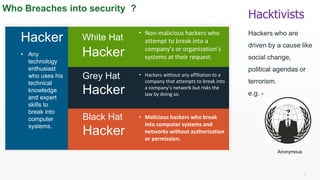
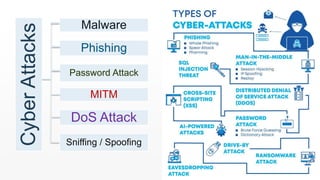
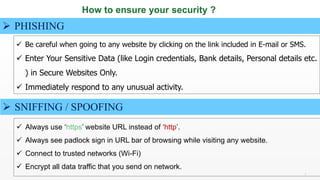
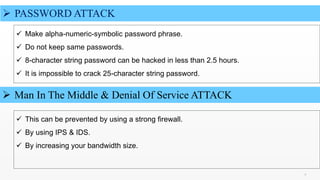
Elizabeth Denham argues that we will all need to change how we think about data protection. The internet has become highly globally connected, making systems vulnerable to viruses, worms, and cyber attacks that can access, alter, or destroy sensitive data. To ensure security, individuals and organizations should use precautions like strong passwords, encryption, firewalls, and anti-malware software to protect against common cyberattack types such as phishing, spoofing, malware, and denial of service attacks.