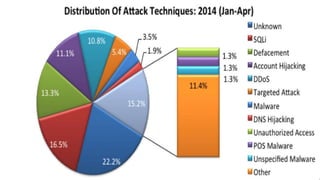
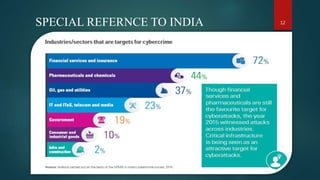
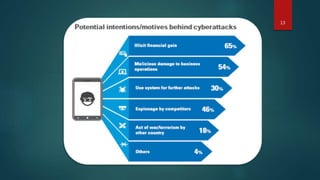
This document discusses cyber security. It defines cyber security as technologies and processes designed to protect computers, networks, and data from unauthorized access and attacks over the internet. The three core principles of cyber security are confidentiality, integrity, and availability. Several types of cyber attacks are described such as malware, phishing, and denial of service attacks. Major historical cyber attacks are outlined including the Morris Worm in 1988 and the Anthem hack in 2015 that breached 80 million records. Common attack patterns and measures to prevent cyber attacks like using complex passwords and encryption are also summarized.