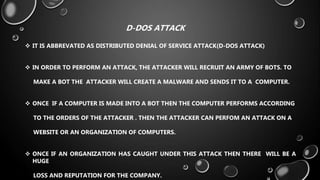
This document discusses cyber security and cyber crimes. It defines cyber security as technologies and practices to protect networks and data from unauthorized access and cyber crimes as criminal activities carried out using computers or networks. The document describes common cyber attacks like man-in-the-middle attacks, DDoS attacks, SQL injection, and phishing. It also discusses preventive security measures and advantages of cyber security like protecting against viruses and data theft. The conclusion is that cyber crimes cannot be fully stopped but cyber security can help prevent them.