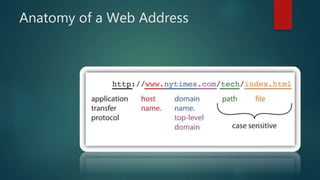
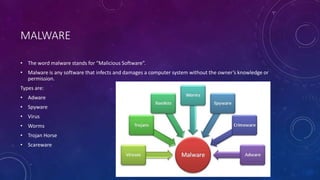
The document discusses an introduction to cyber security presented by Himansh Bhandari. It defines cyber security as the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. It discusses the history and evolution of the internet. It also covers types of malware like viruses, worms, Trojan horses and spyware. It discusses types of hackers like white hat, grey hat and black hat hackers. It provides information on implementing cyber security for mobile phones, banking and in India. It highlights major cyber security problems like viruses, hackers, malware and password cracking and discusses solutions to prevent them.