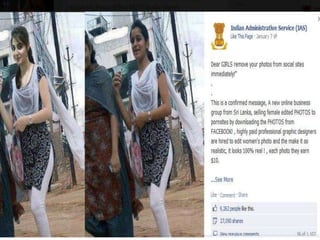
The document discusses the history of cyber crimes from the first recorded incident in 1820 to modern times. It outlines some of the earliest cyber crimes and hackers from the 1980s onward. It then provides details on different types of cyber crimes including hacking, denial of service attacks, virus dissemination, software piracy, and more. For each crime type, it gives examples and explanations. The document is an informative overview of the evolution of cyber crimes and the various forms they can take.



















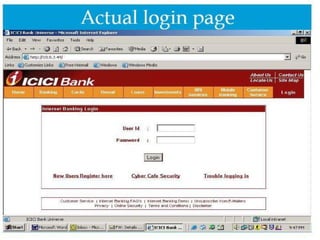
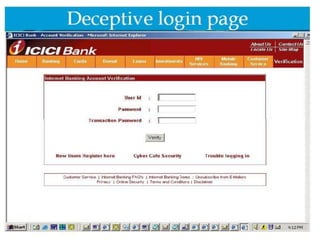
![Phishing E-mail
From : ICICI Bank
[mailto:support@icici.com]
Sent : 08 June 2004 03:25
To : India
Subject : Official information from ICICIBank
Dear valued ICICI Bank Customer !
For security purposes your account has been randomly chosen for verification. To
verify your account information we are asking you to provide us with all the data we are
requesting.Otherwise we will not be able to verify your identity and access to your
account will be denied. Please click on the link below to get to the ICICI secure page and
verify your account details.
Thank you.
https://infinity.icicibank.co.in/Verify.jsp
ICICI Bank Limited](https://image.slidesharecdn.com/cybercrimeandcybersecurity-130408200531-phpapp02/85/Cyber-crime-and-cyber-security-23-320.jpg)