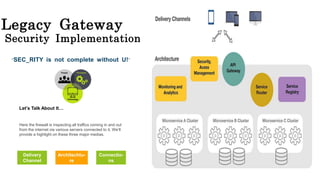
The document provides an overview of cybersecurity, defining it as the practice of protecting systems and data from digital attacks, including cyber crimes that threaten individual and national security. It emphasizes the need for multi-layered protection encompassing technology, processes, and people, and outlines common cyber threats such as identity theft, phishing, and malware. Furthermore, it discusses the importance of reporting cyber crimes and implementing advanced security measures to mitigate risks.