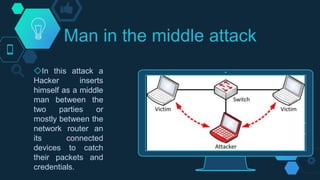
This document provides an overview of topics related to cybercrime and security that will be covered. It lists the team members and topics to be discussed including the history of cybercrime, authenticity, security and privacy, database security, social engineering, cyber attacking methods, and security tips. Database security features like digital certificates, encryption, firewalls, and proxy servers will be explained. Responsibilities of database administrators and built-in database protections will also be covered. Specific cyber attacks such as Trojan horse attacks, backdoors, keyloggers, DDoS attacks, and man-in-the-middle attacks will be described. The document concludes with safety tips and references.