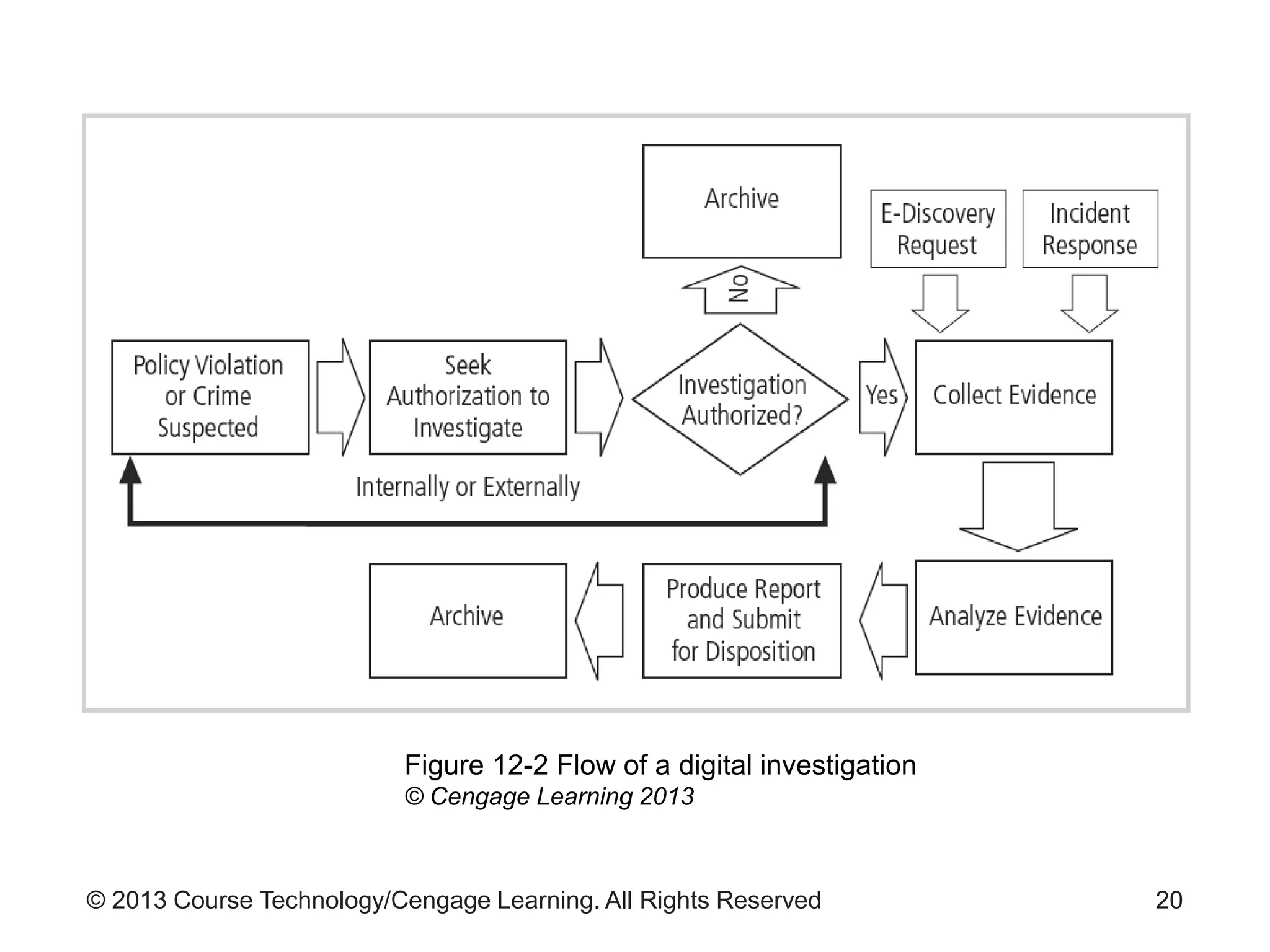
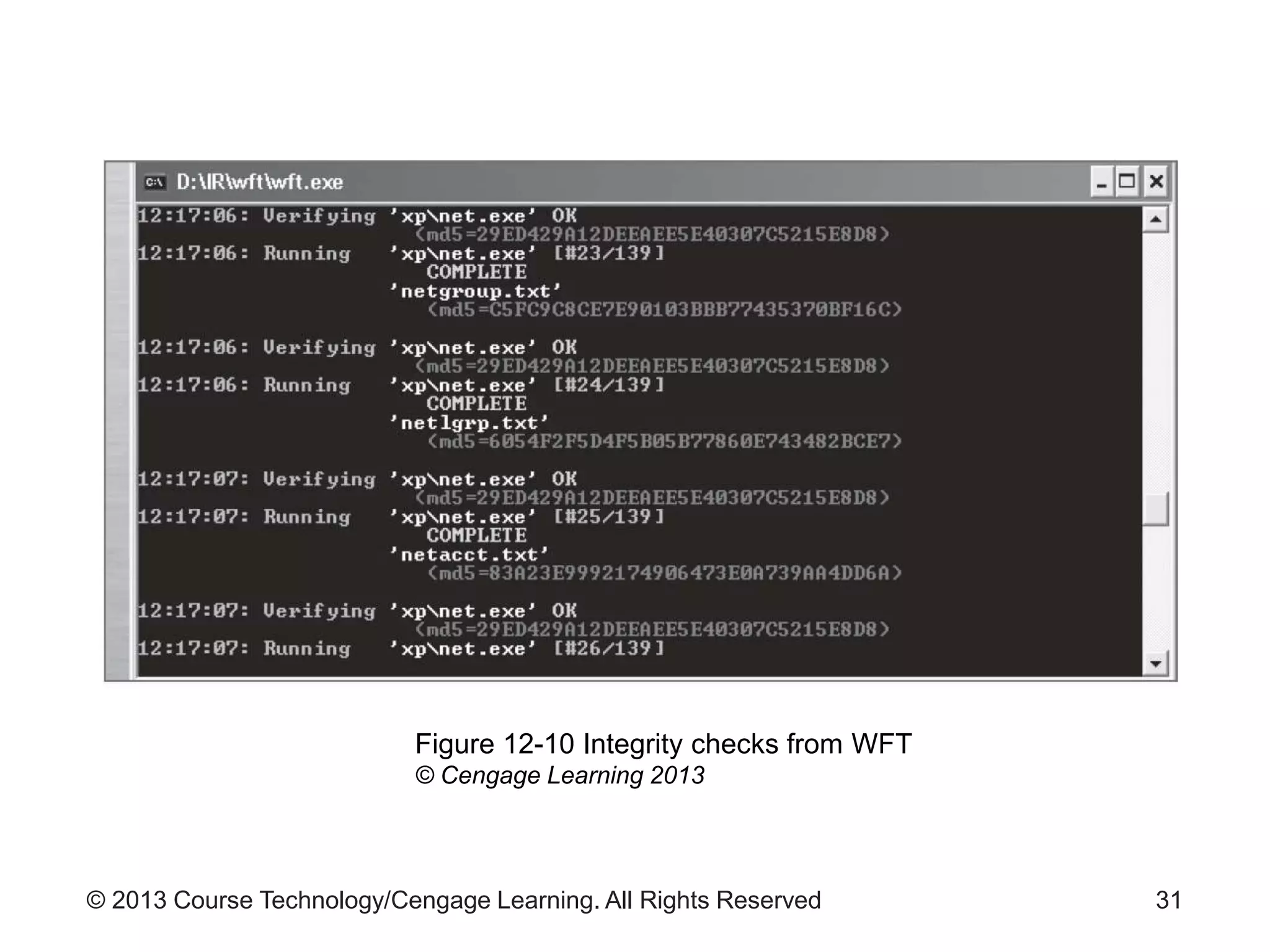
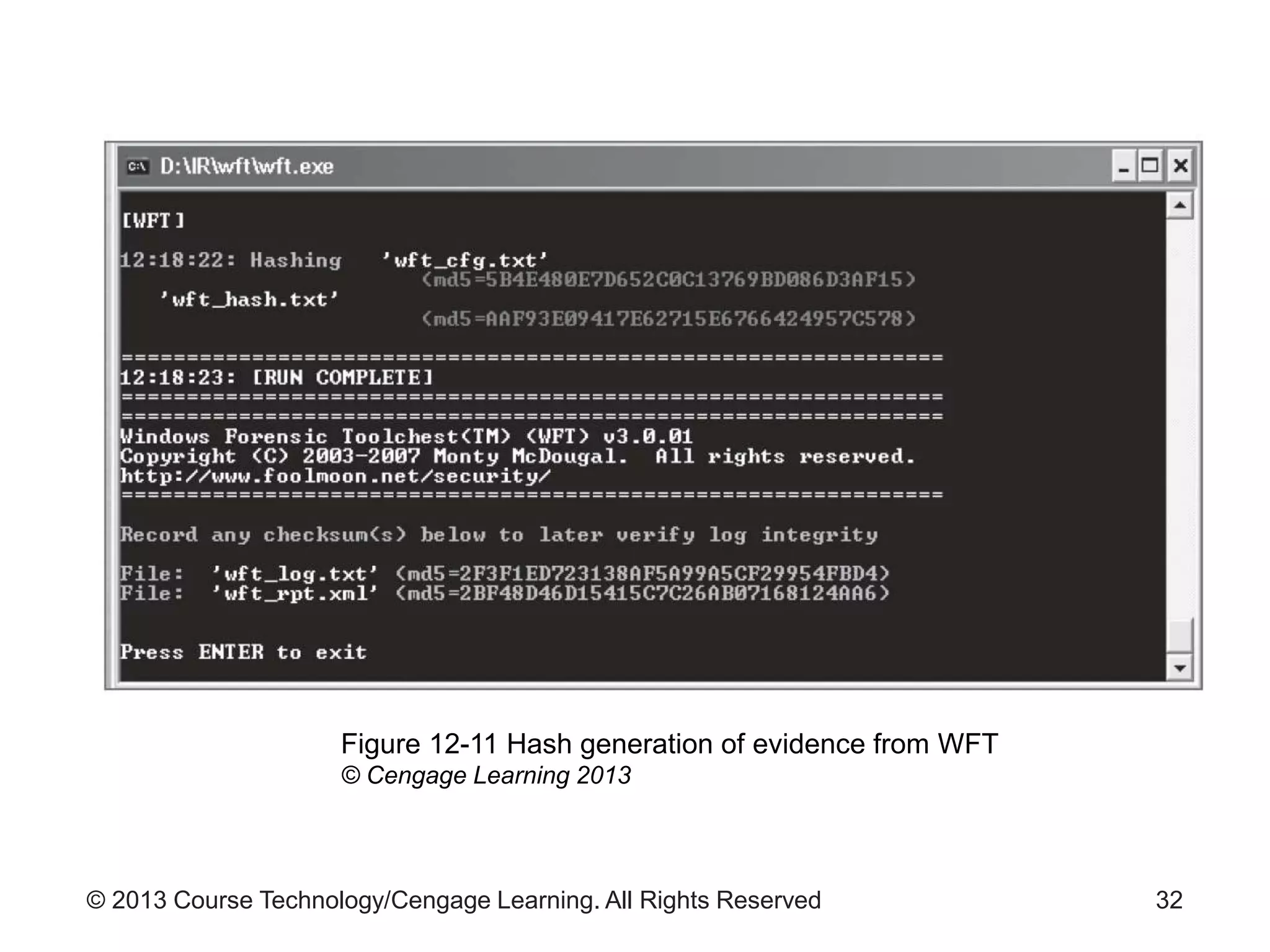
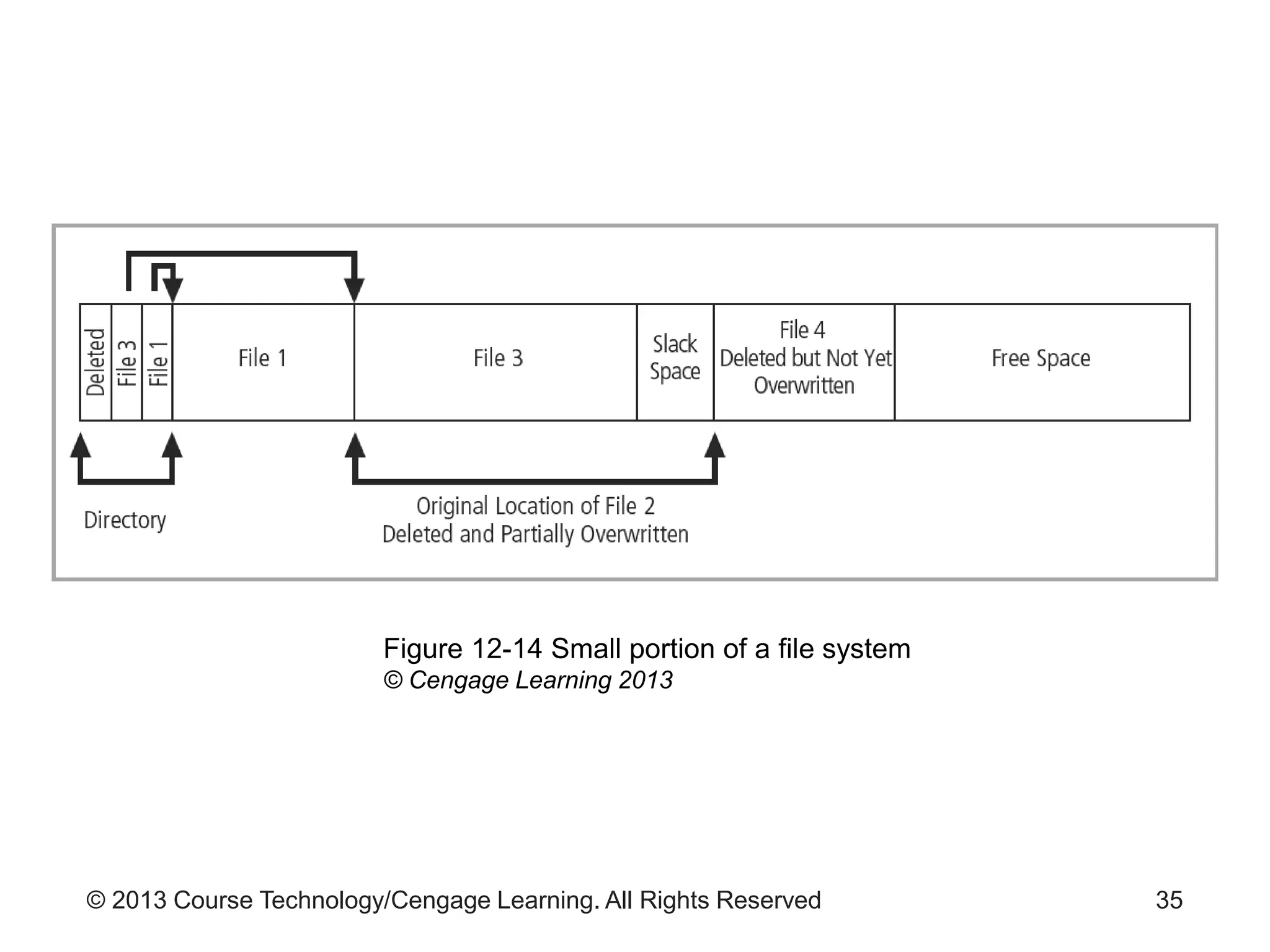
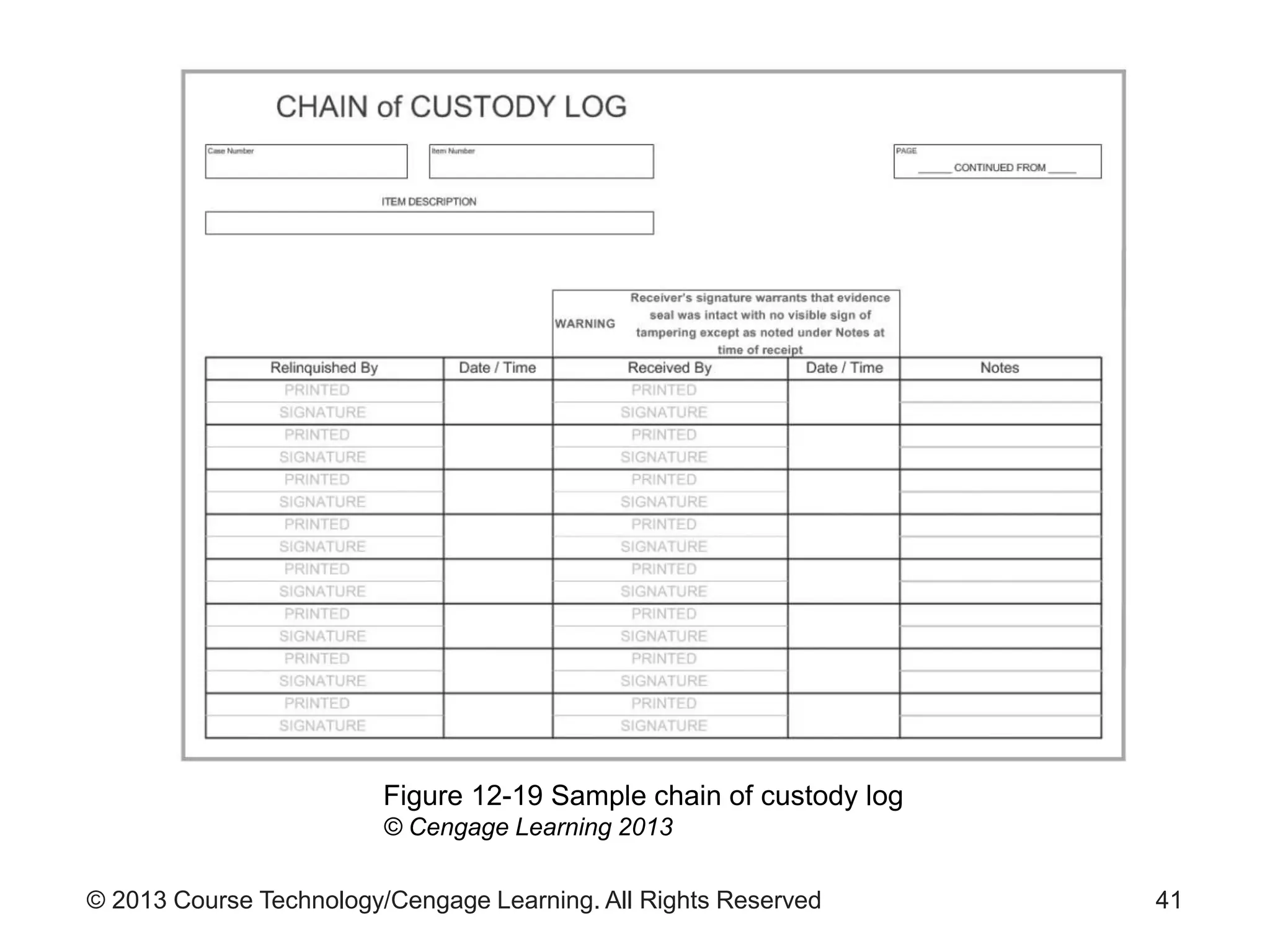
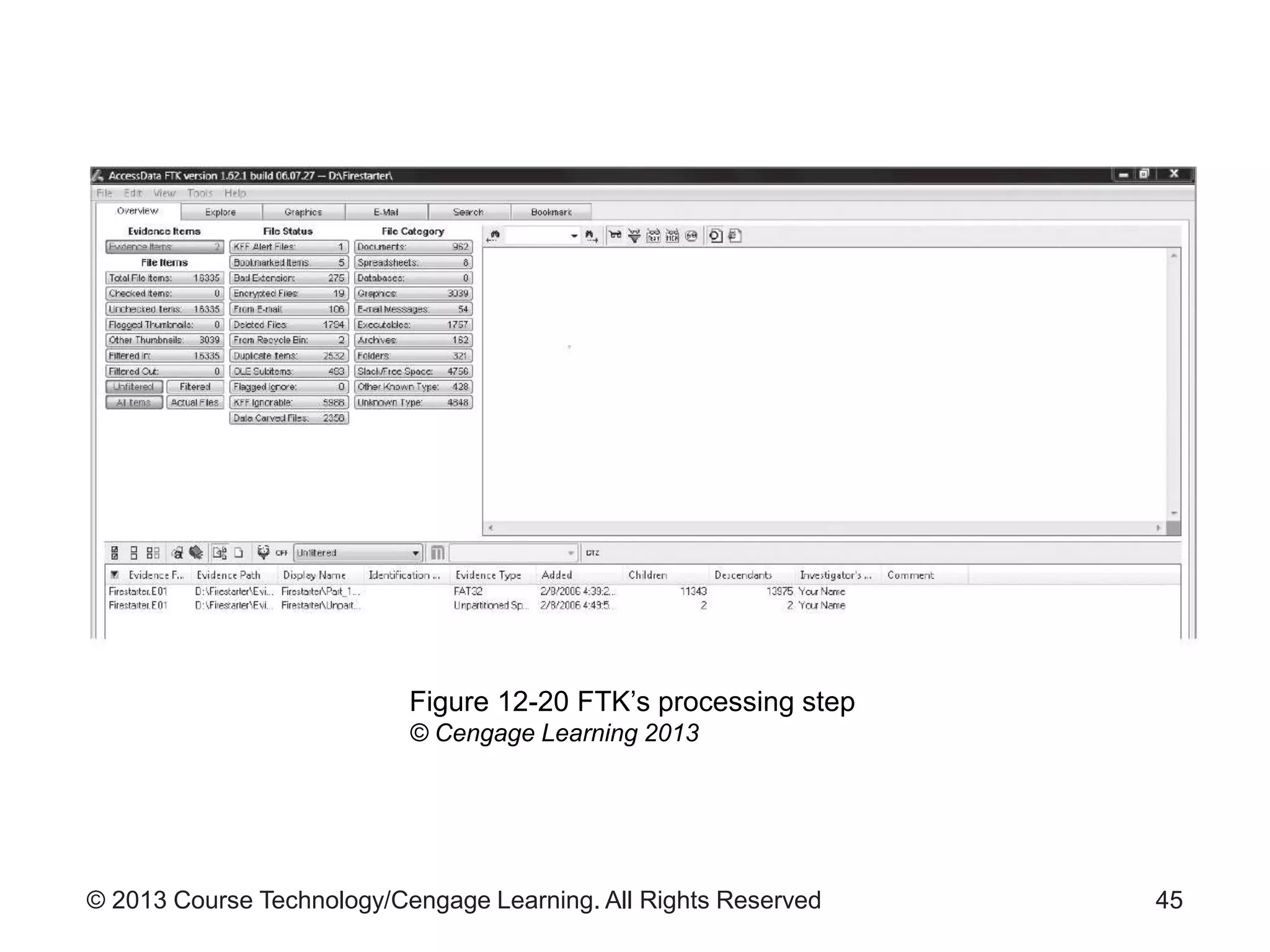
This document provides an overview of digital forensics processes and procedures. It discusses the roles of digital forensics team members in collecting, analyzing, and reporting on digital evidence. The steps involved include assessing the scene, acquiring evidence such as by imaging hard drives, analyzing evidence using specialized tools, and producing a final report of findings. Legal and technical challenges like encryption are also addressed.