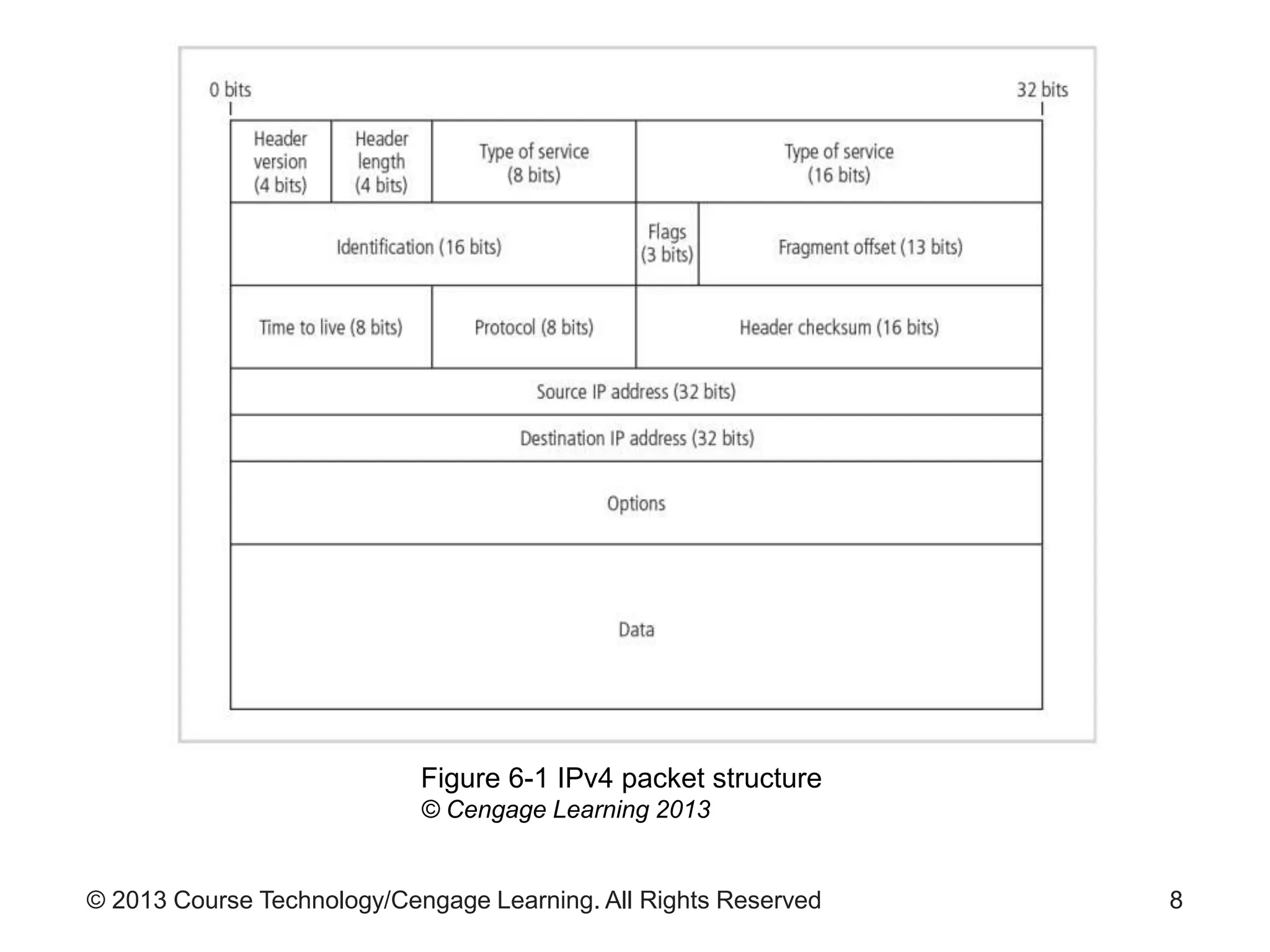
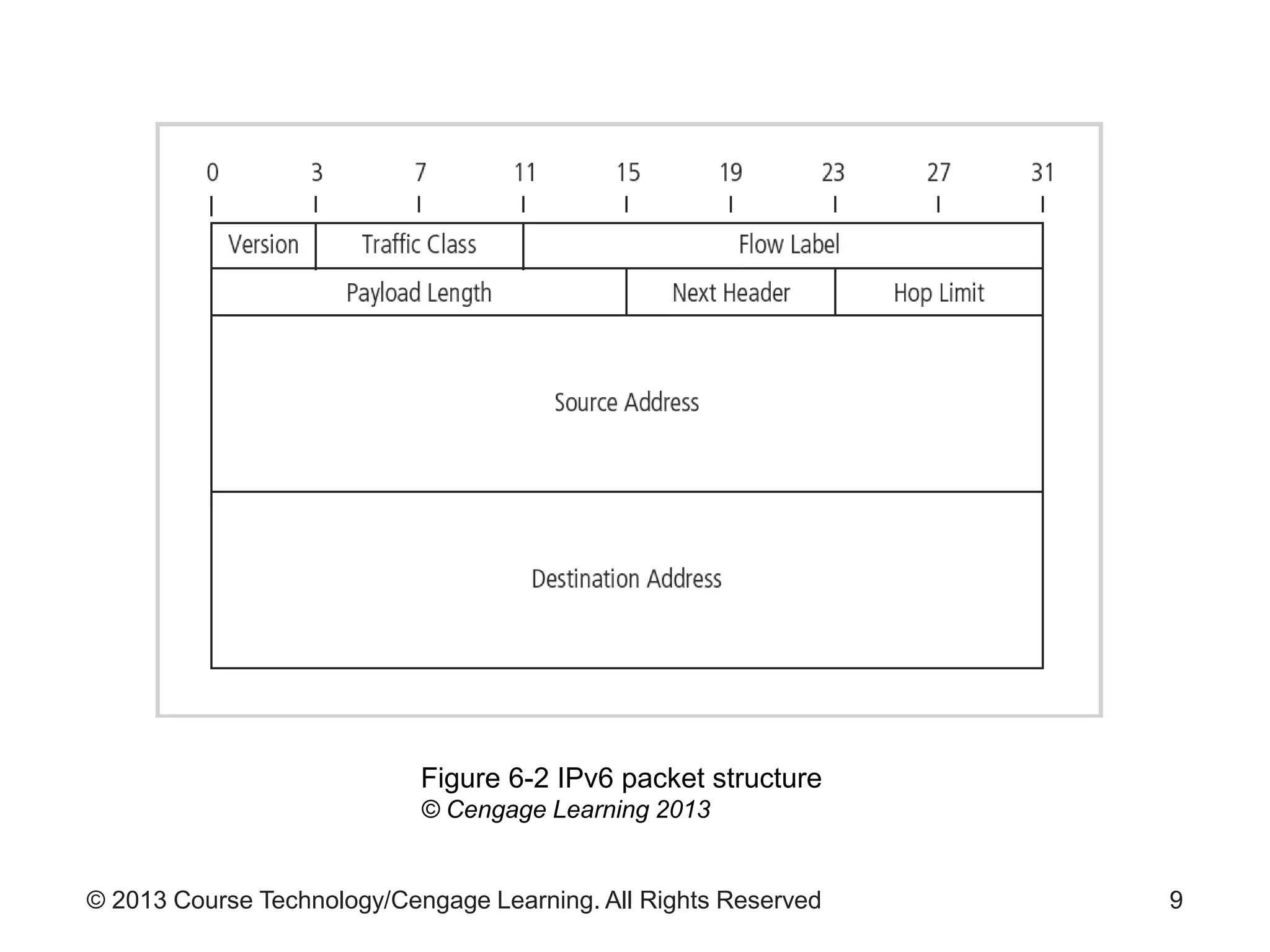
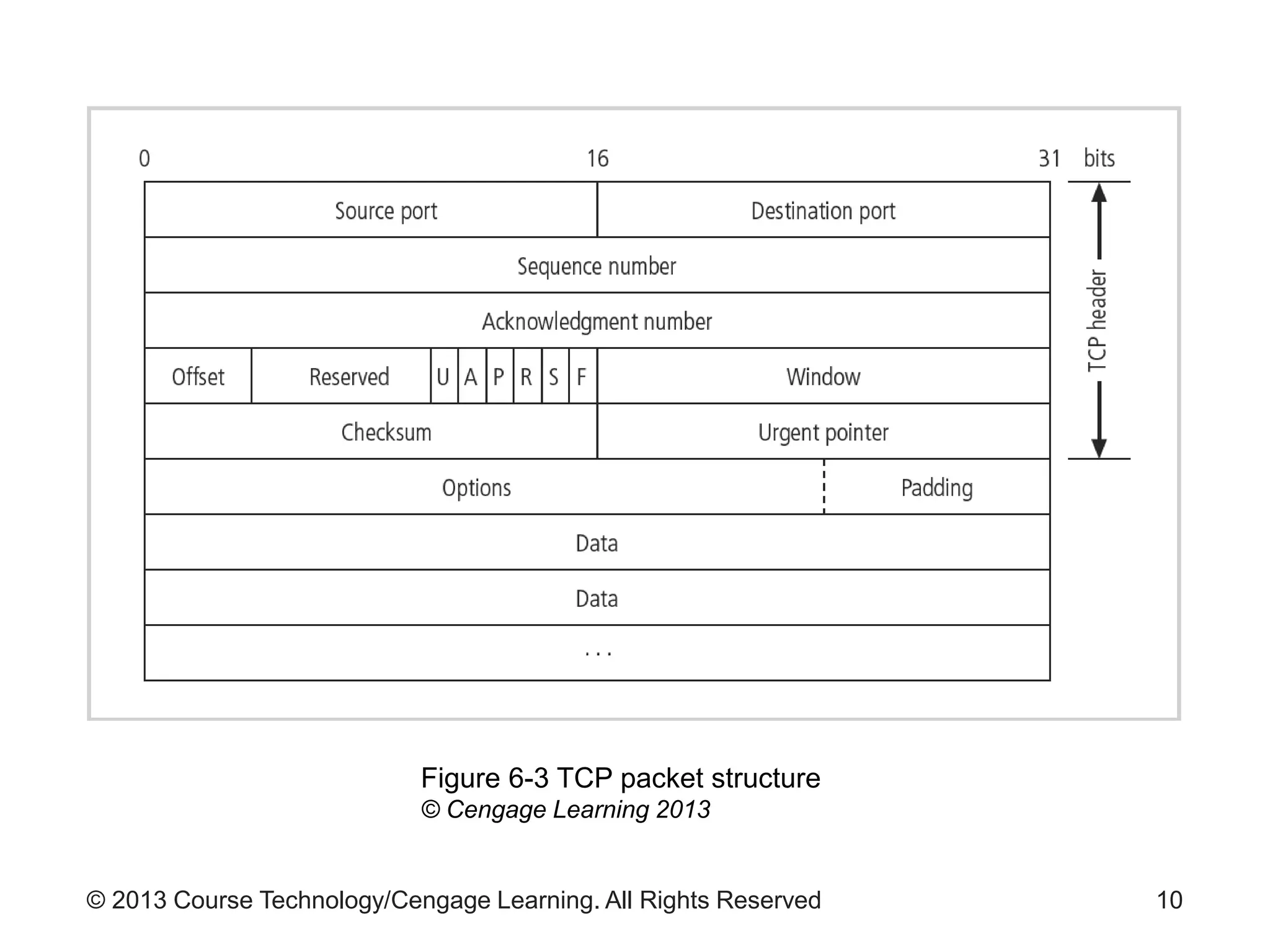
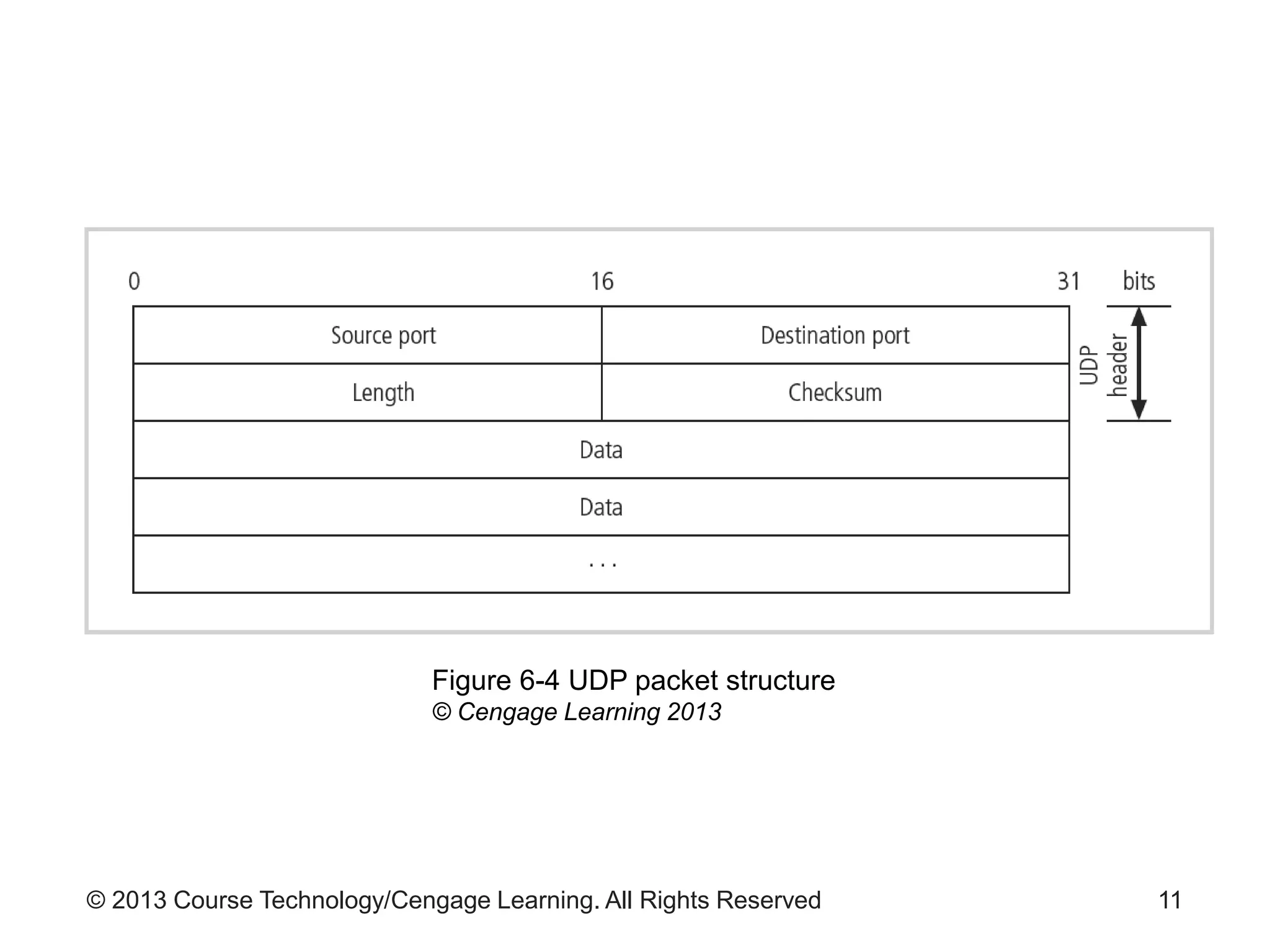
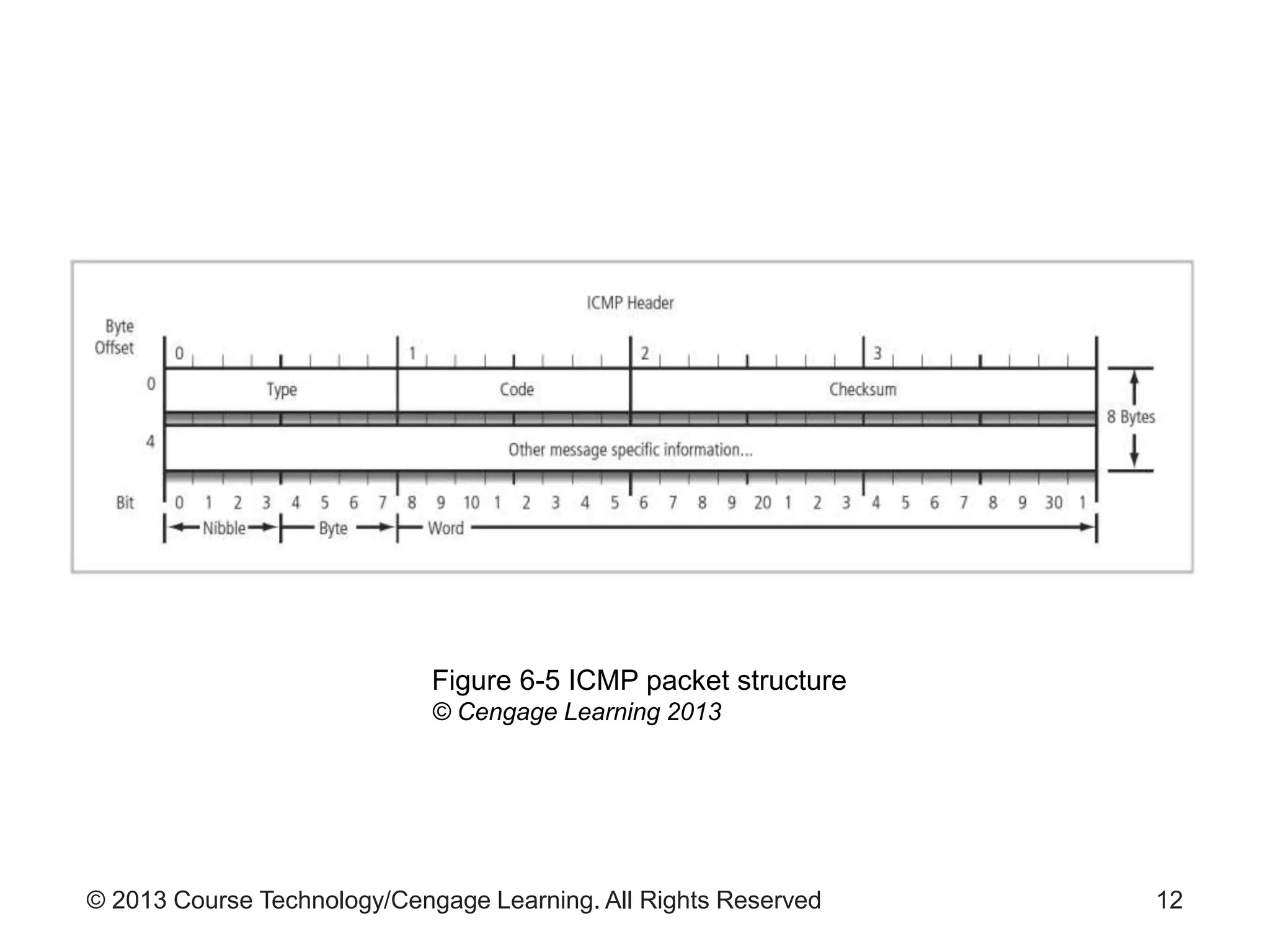
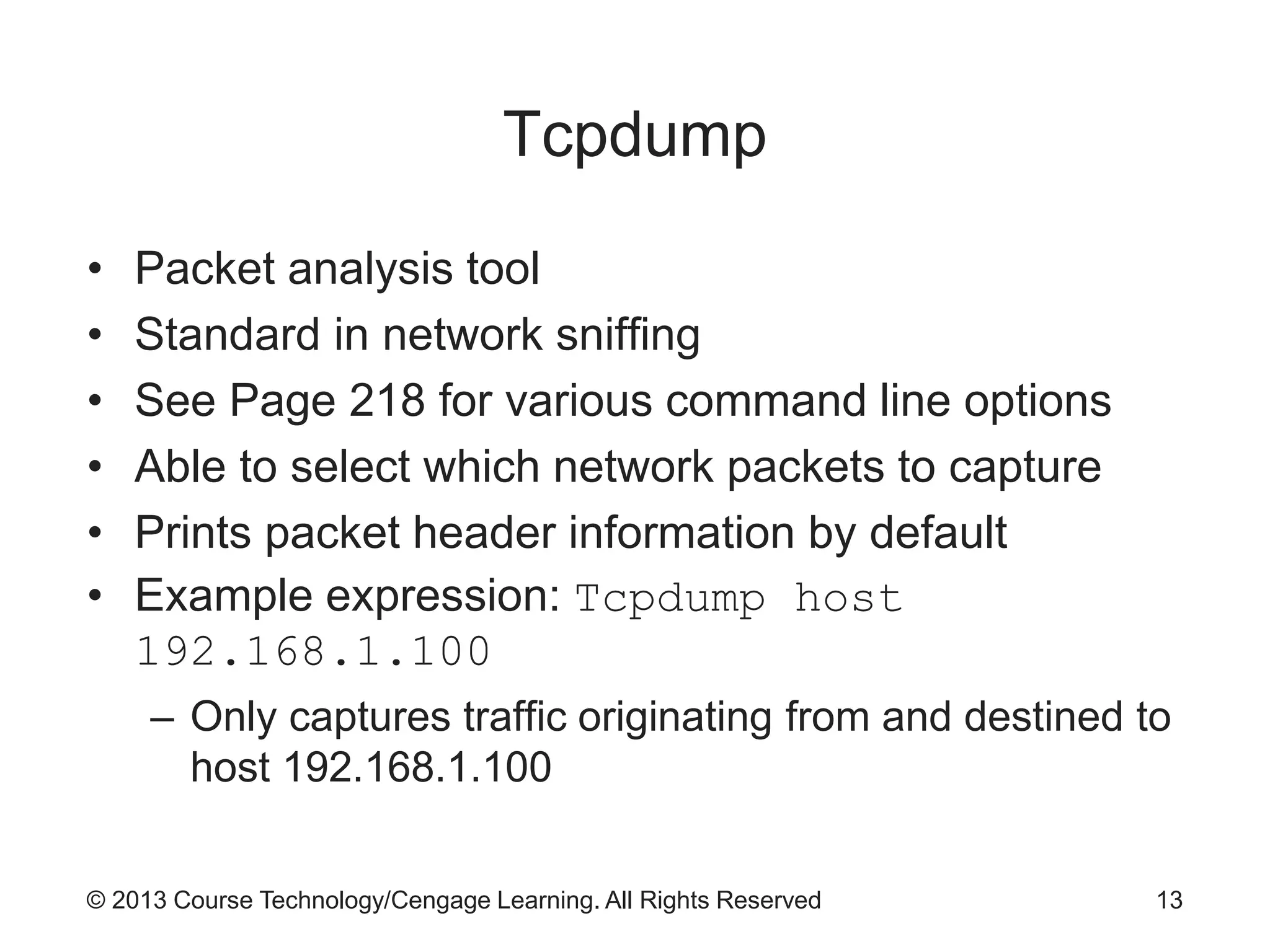
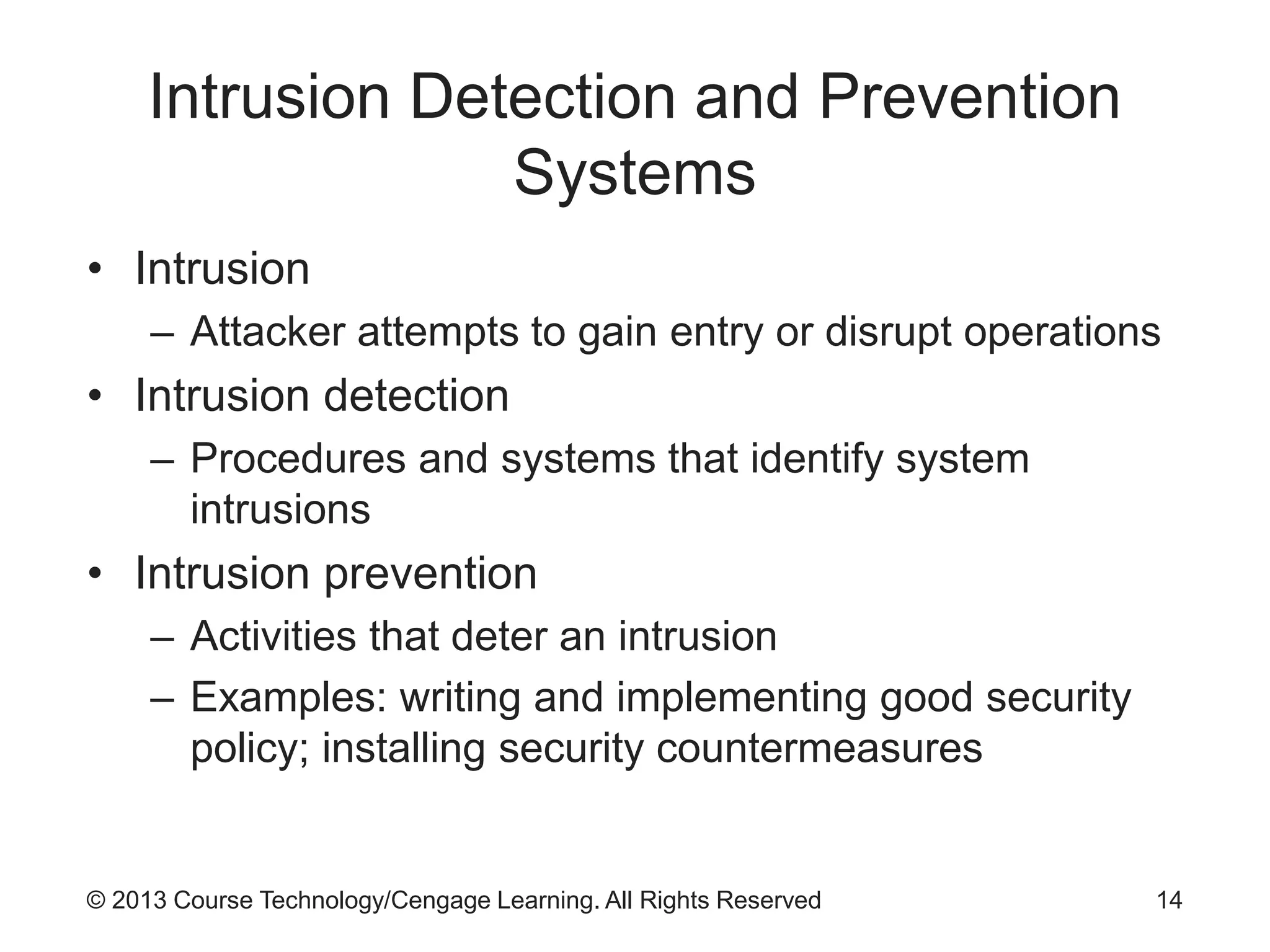
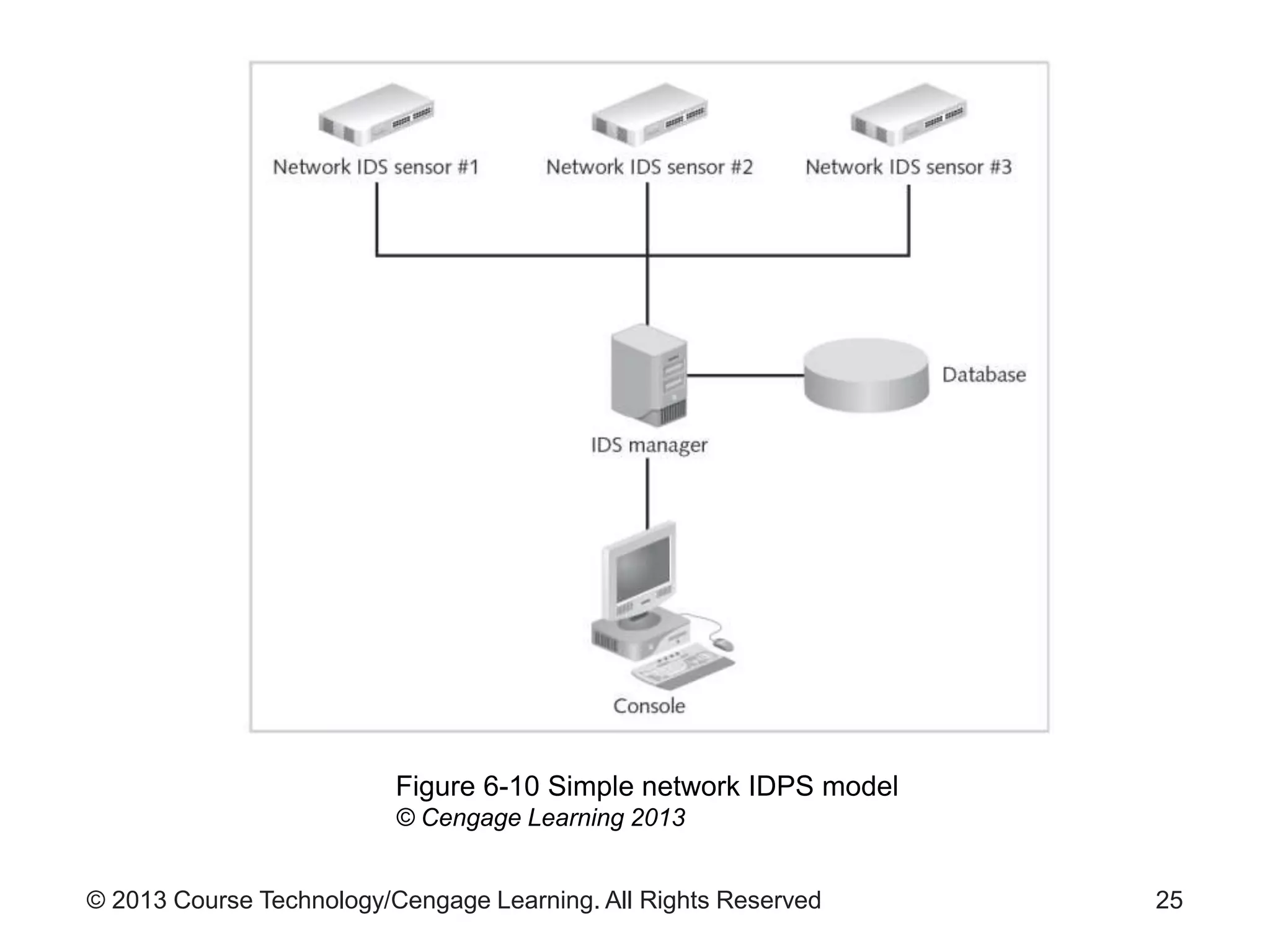
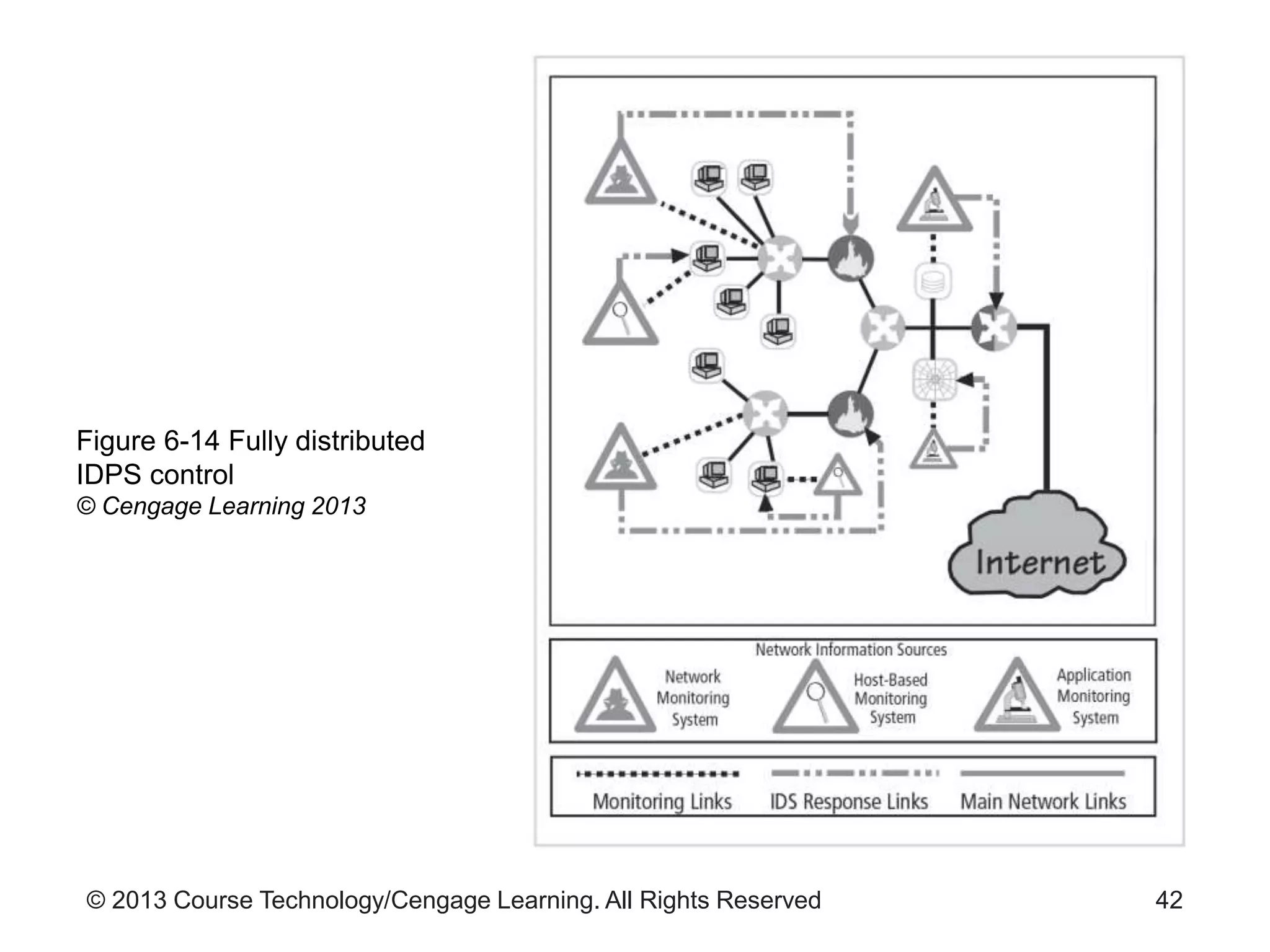
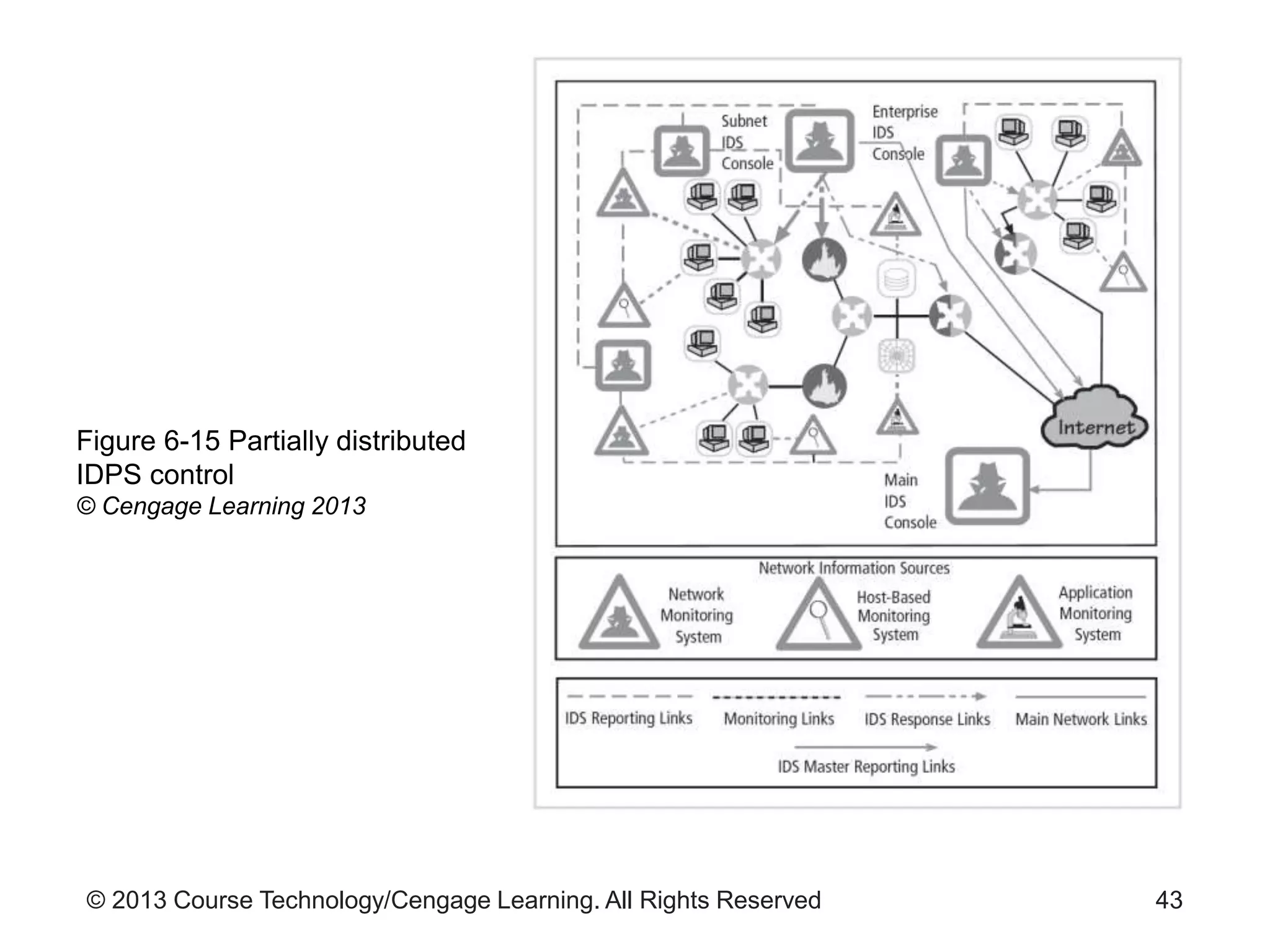
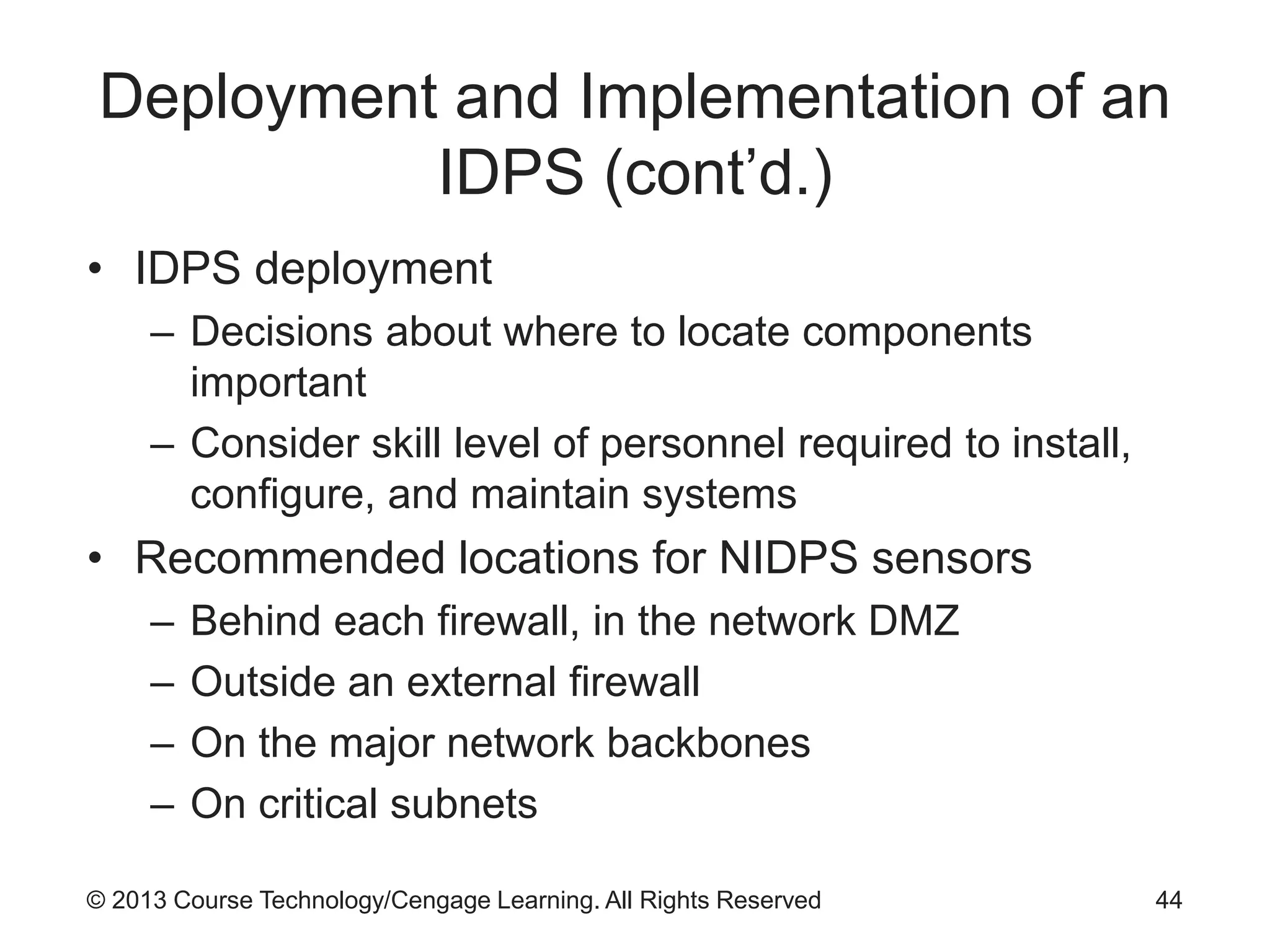
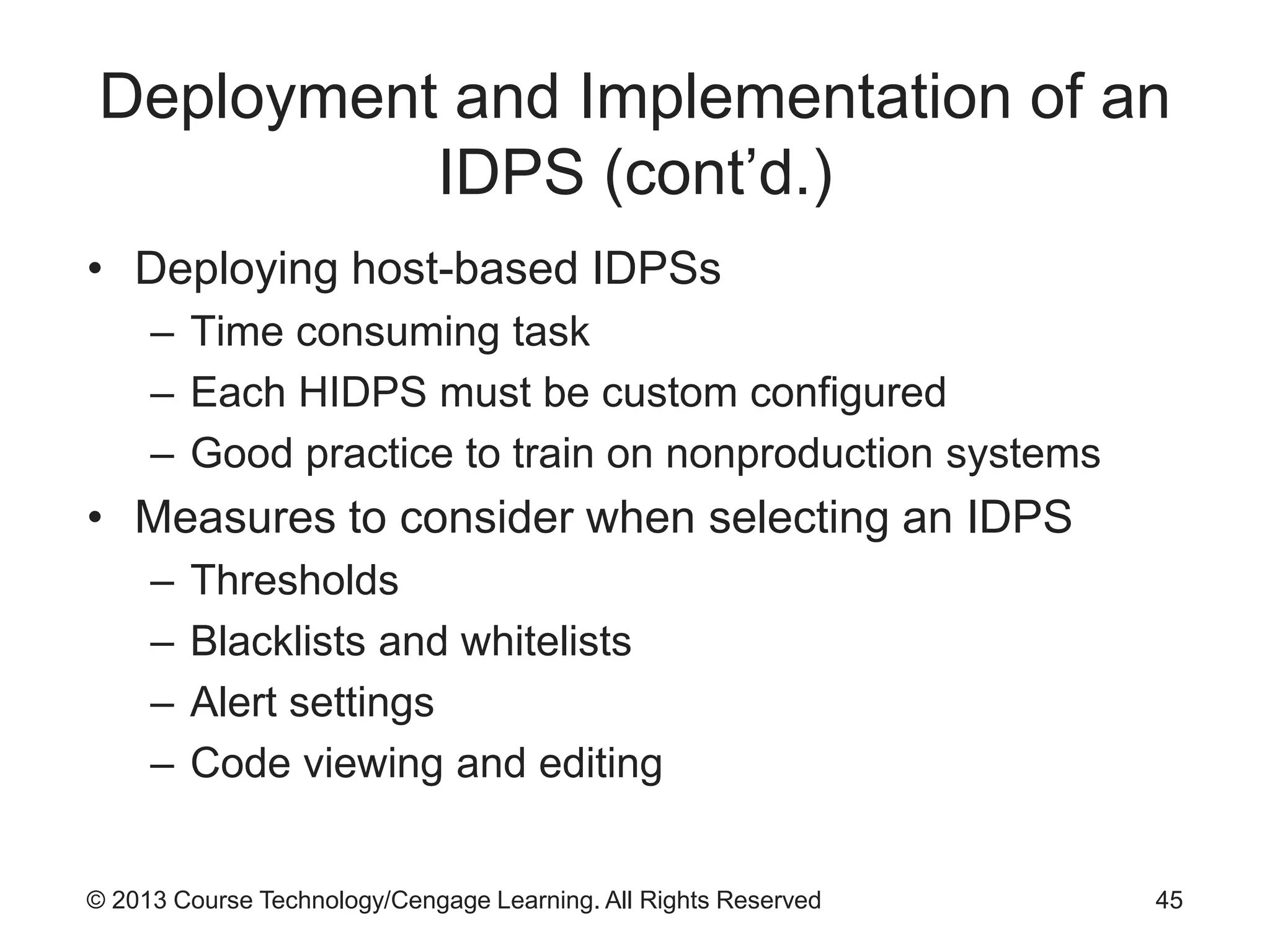
This chapter discusses network monitoring and intrusion detection and prevention systems (IDPS). It defines key concepts like packet analysis and different types of network packet formats. The chapter describes how packet analysis forms the basis for intrusion detection and the various types of intrusion detection systems. It explains common intrusion detection and prevention deployments, response strategies, and technologies like honeypots.