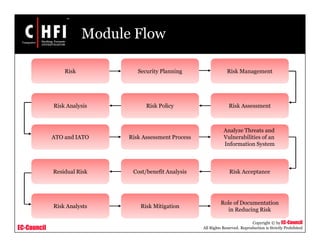
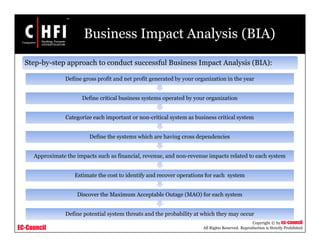
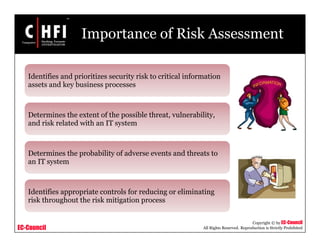
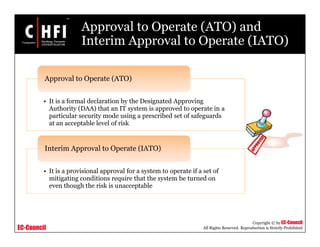
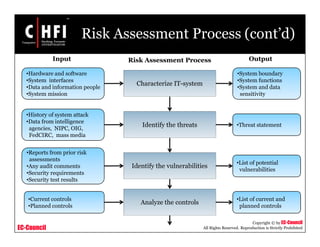
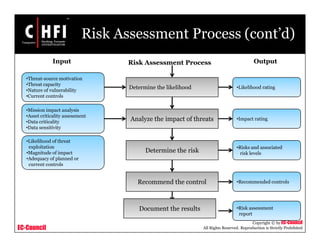
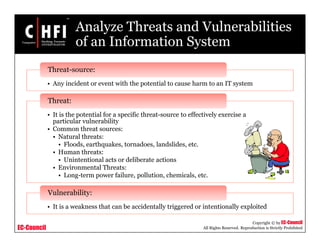
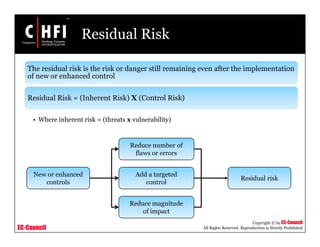
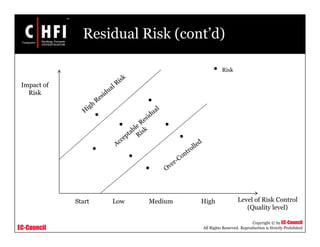
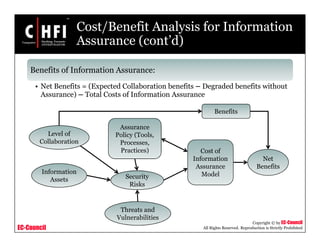
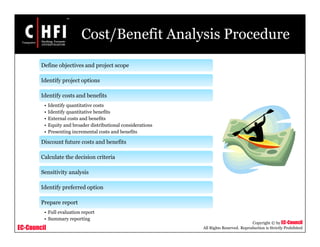
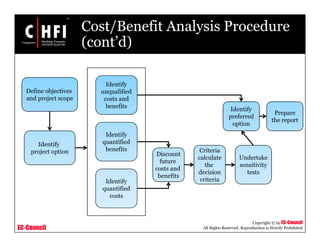
The document discusses the risk assessment process, including characterizing the IT system, identifying threats and vulnerabilities, analyzing controls, determining likelihood and impact, assessing risk level, and recommending controls to mitigate risks; it also covers developing policies and procedures for conducting risk assessments, writing risk assessment reports, and coordinating resources to perform risk assessments.