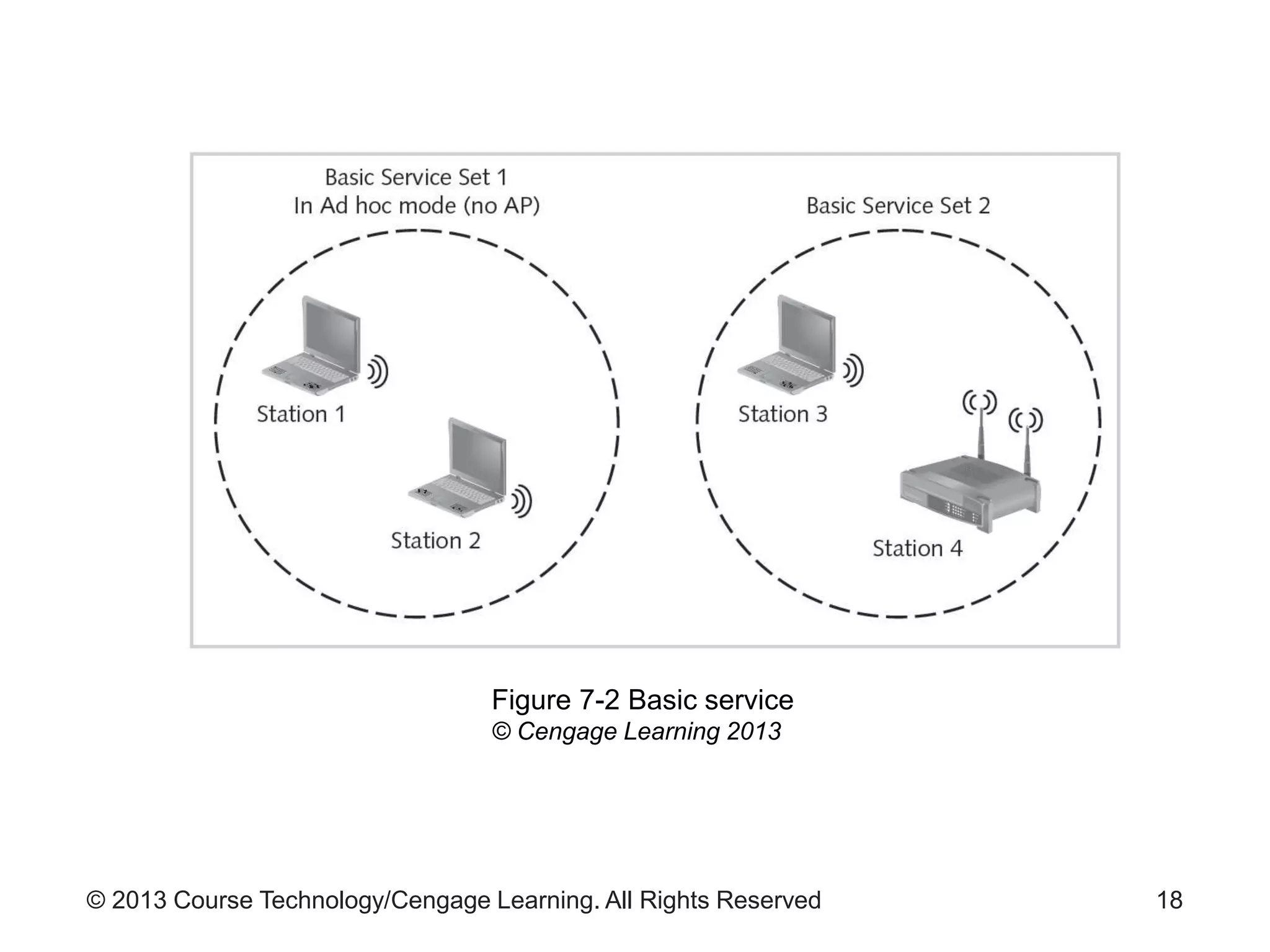
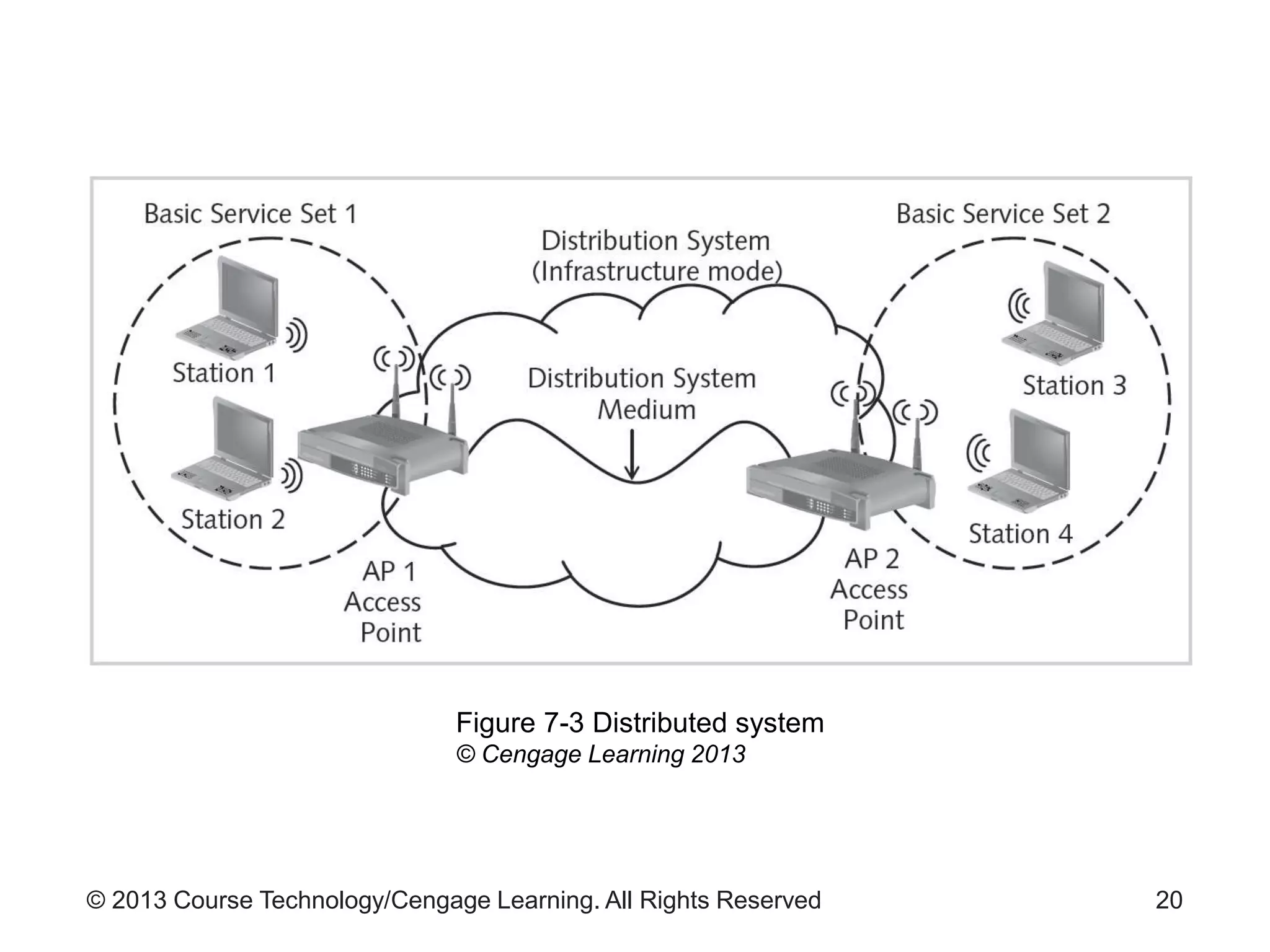
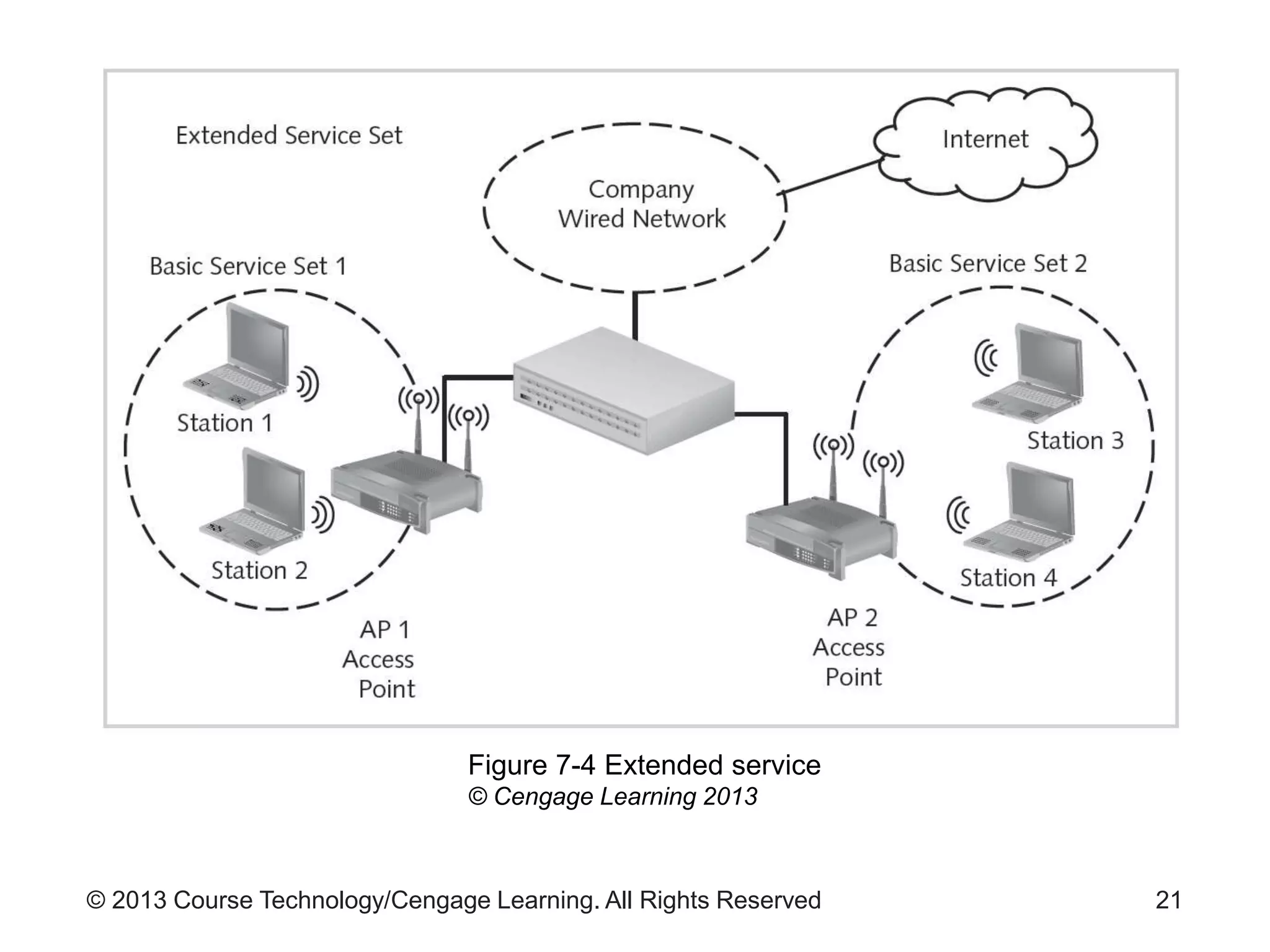
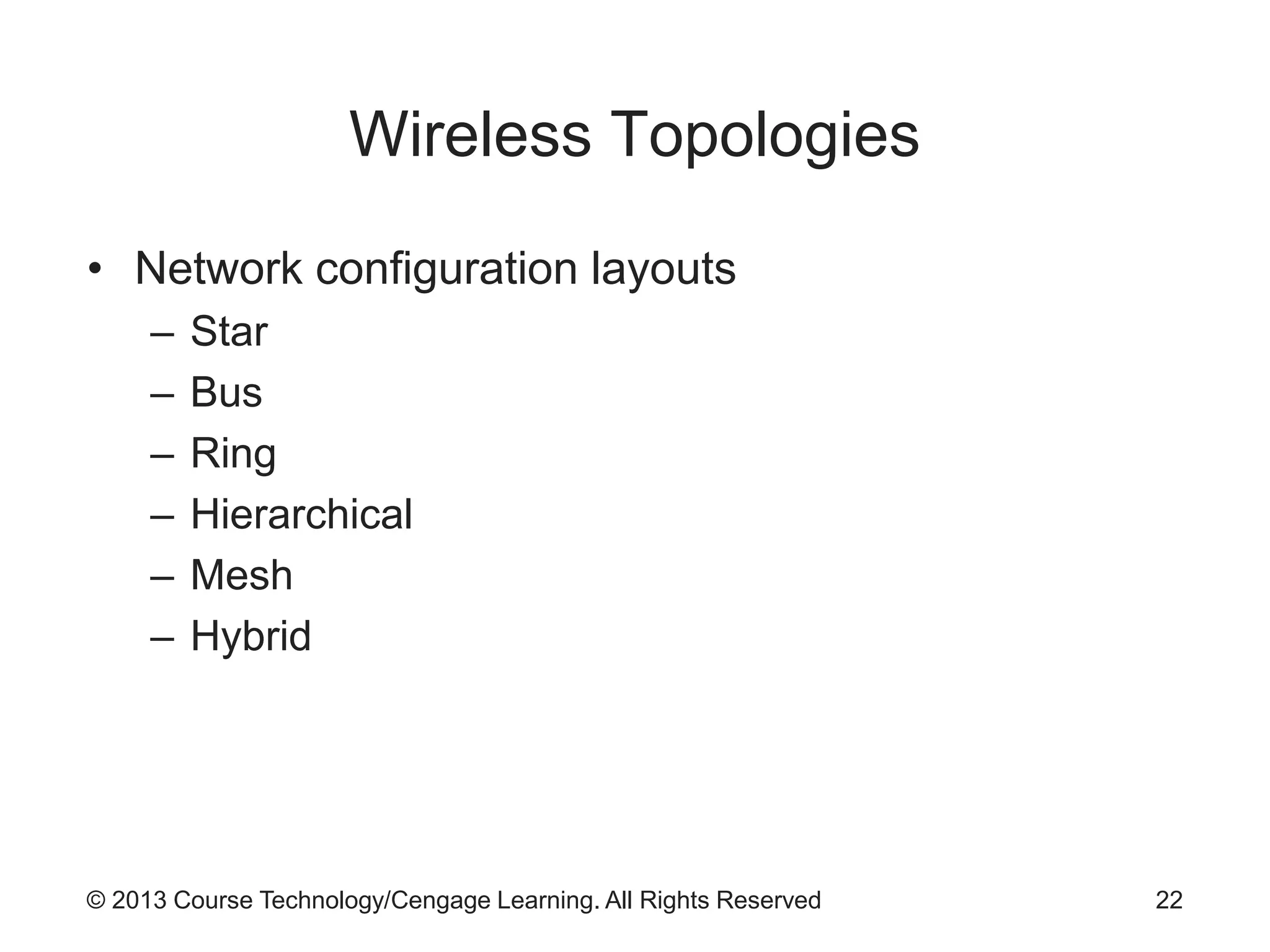
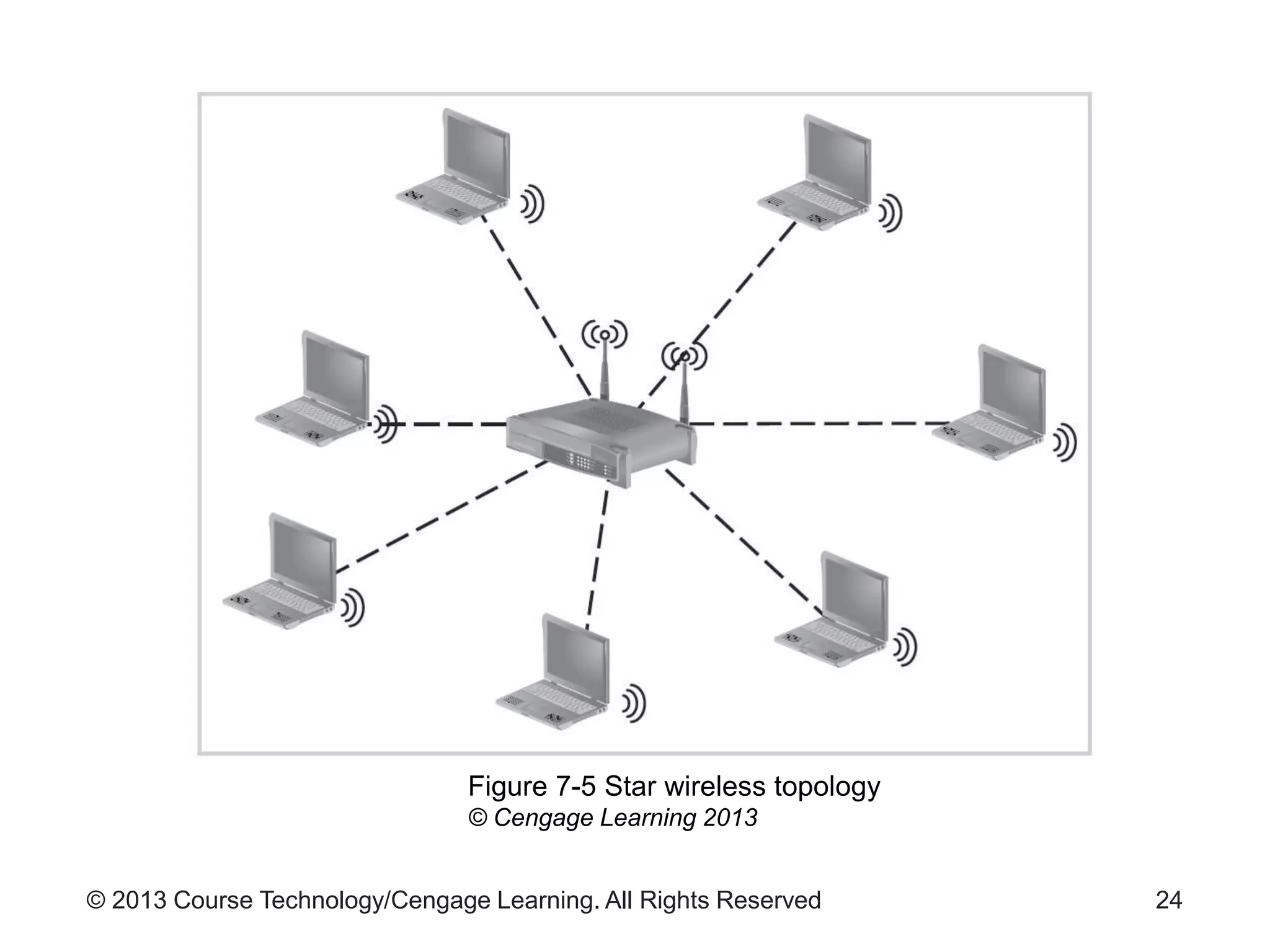
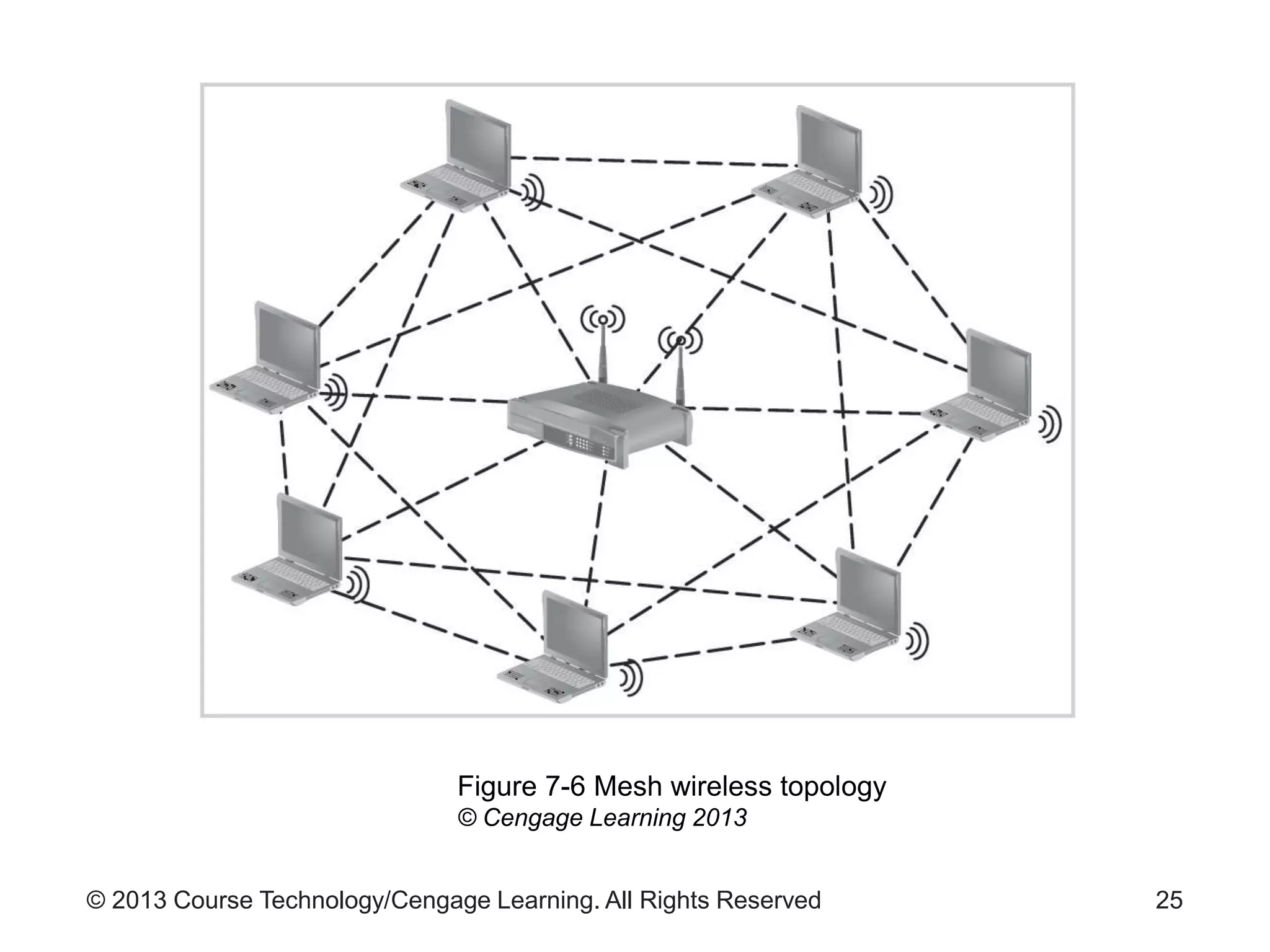
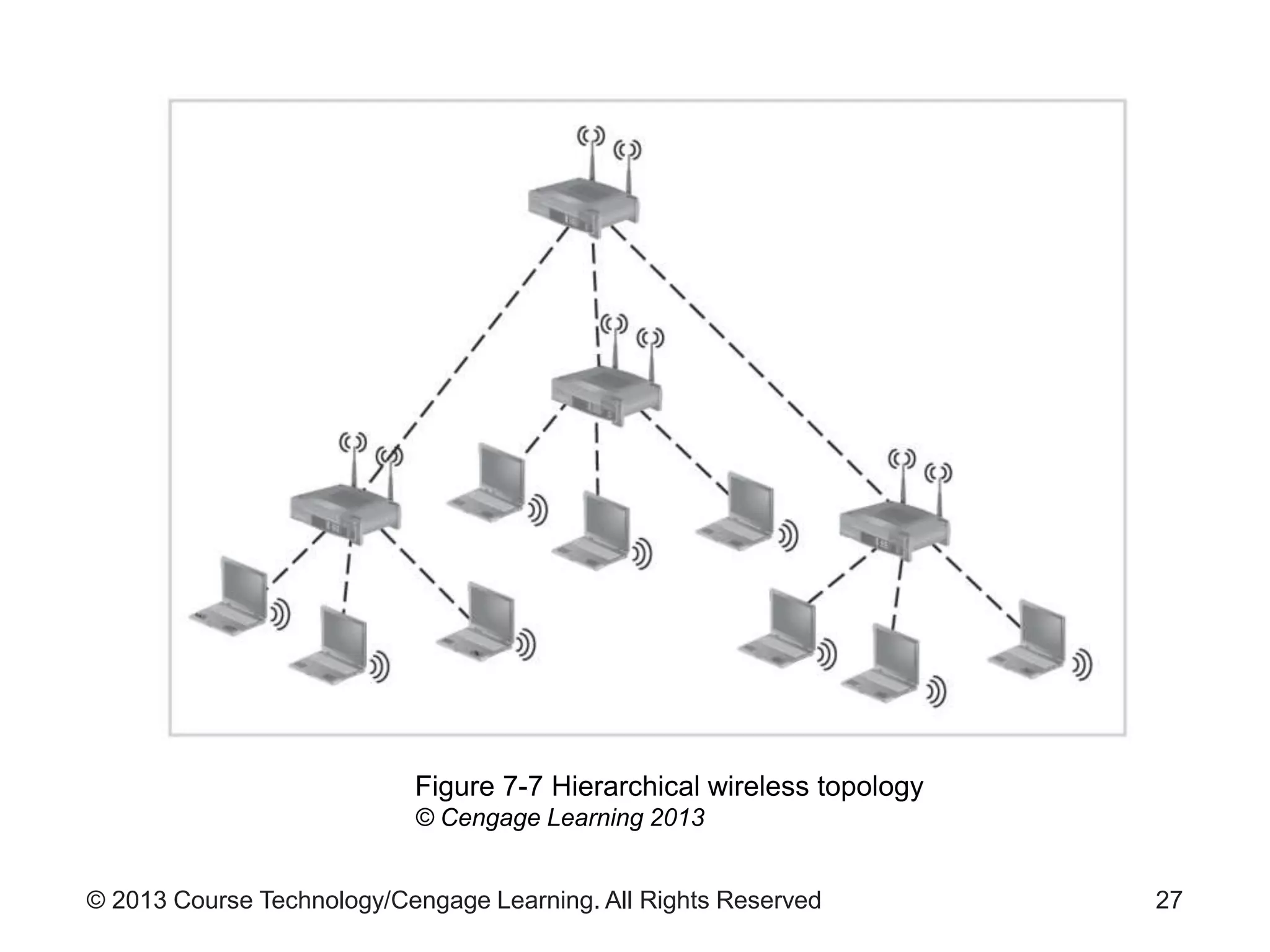
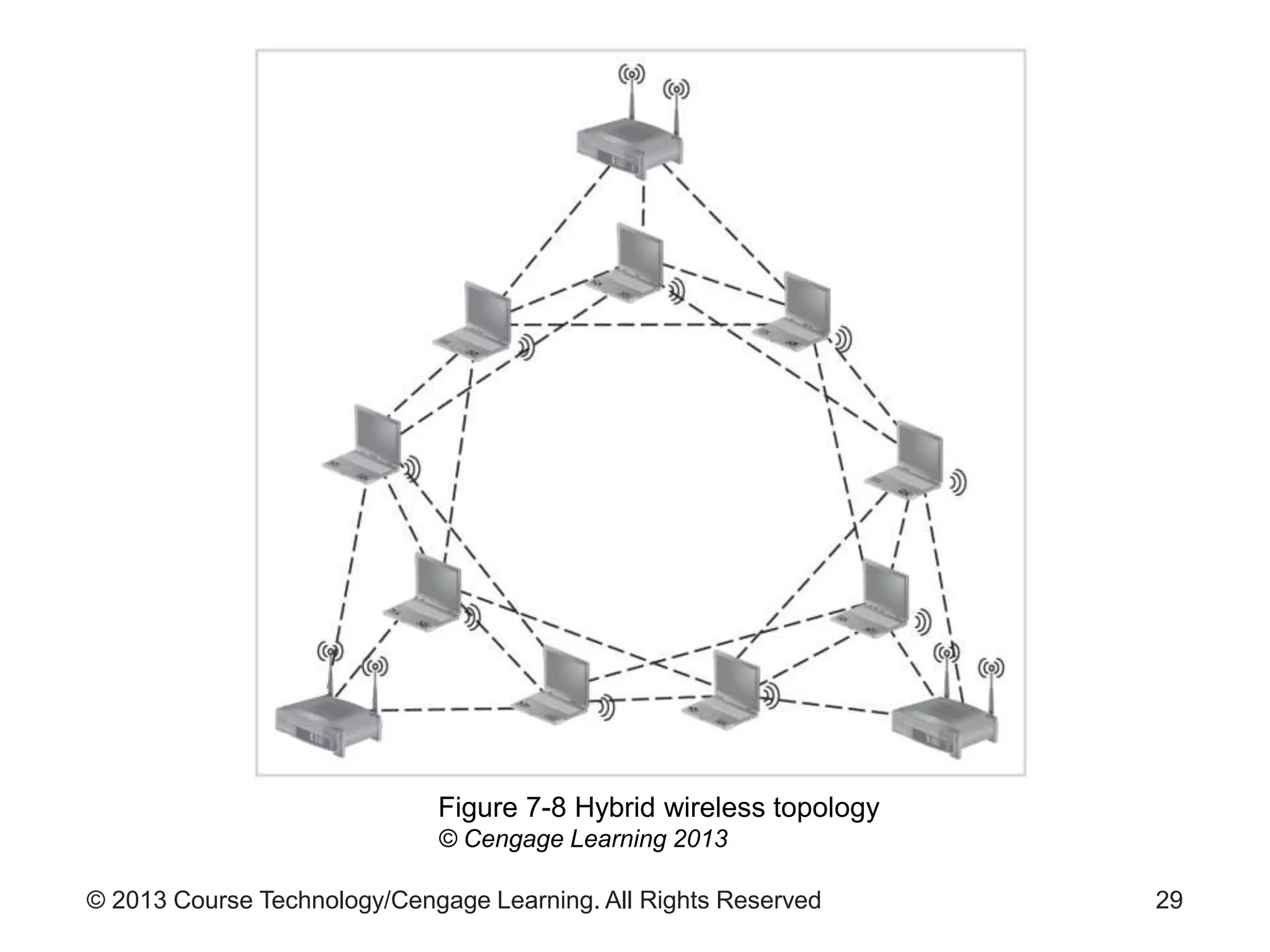
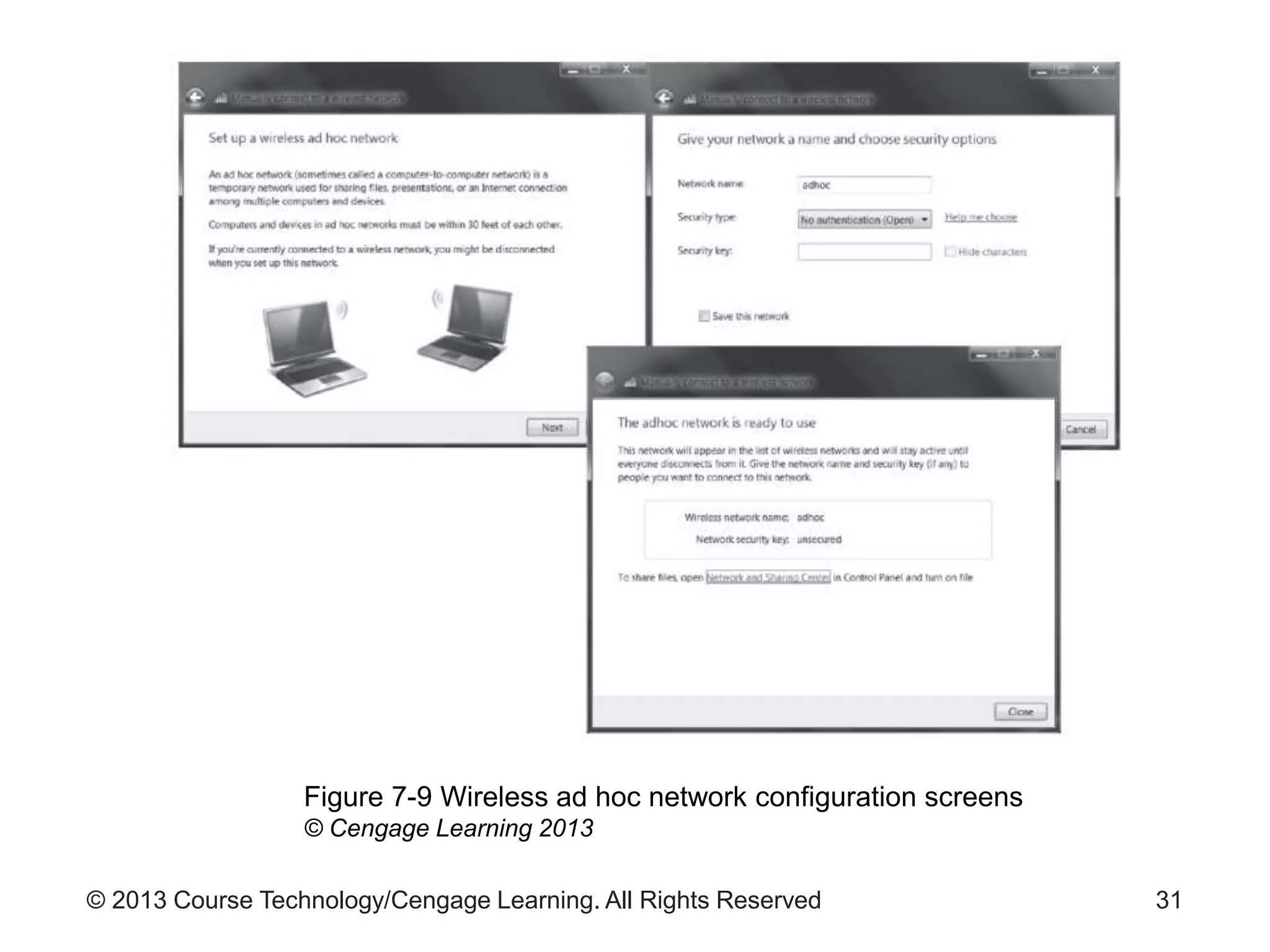
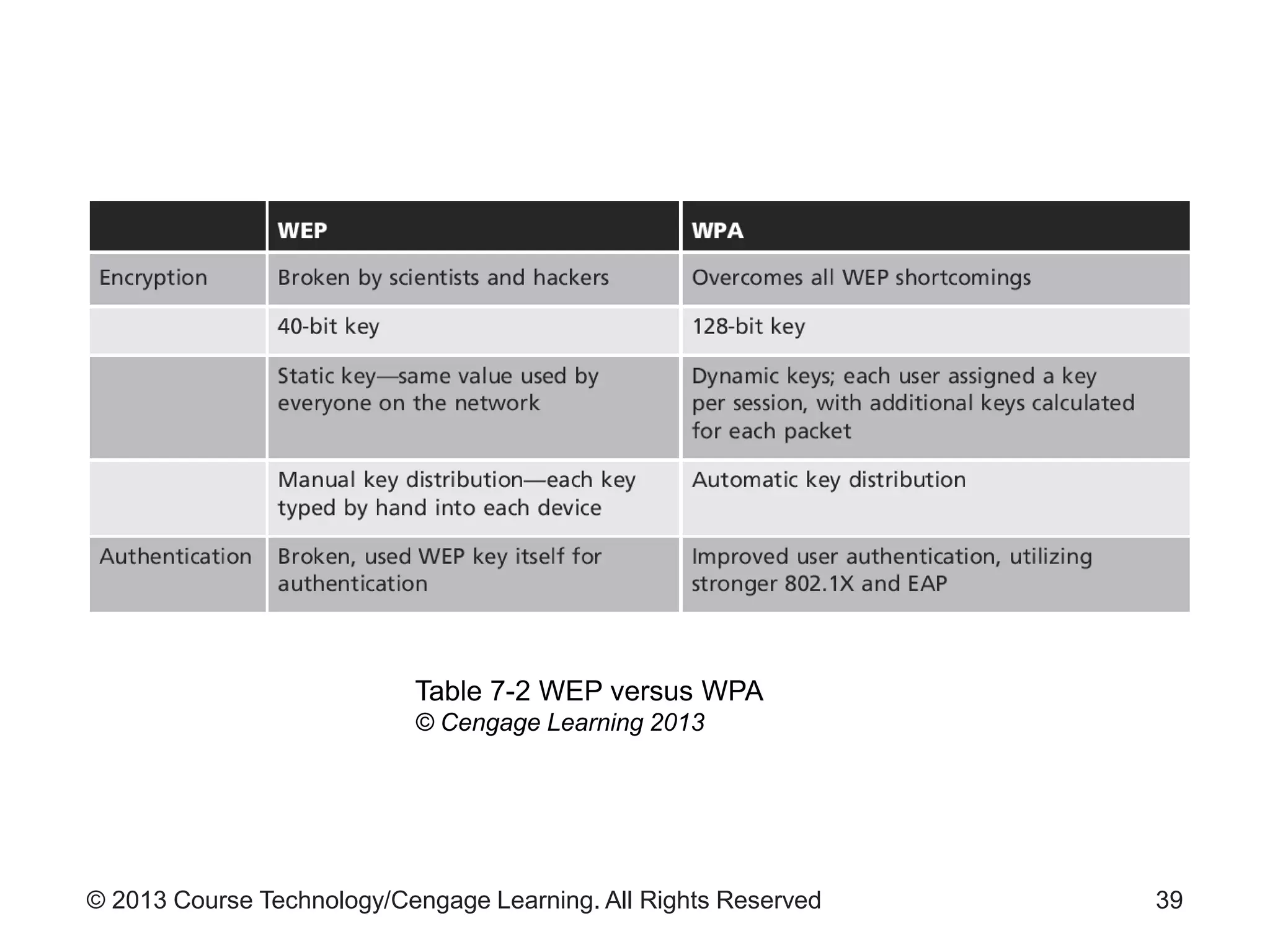
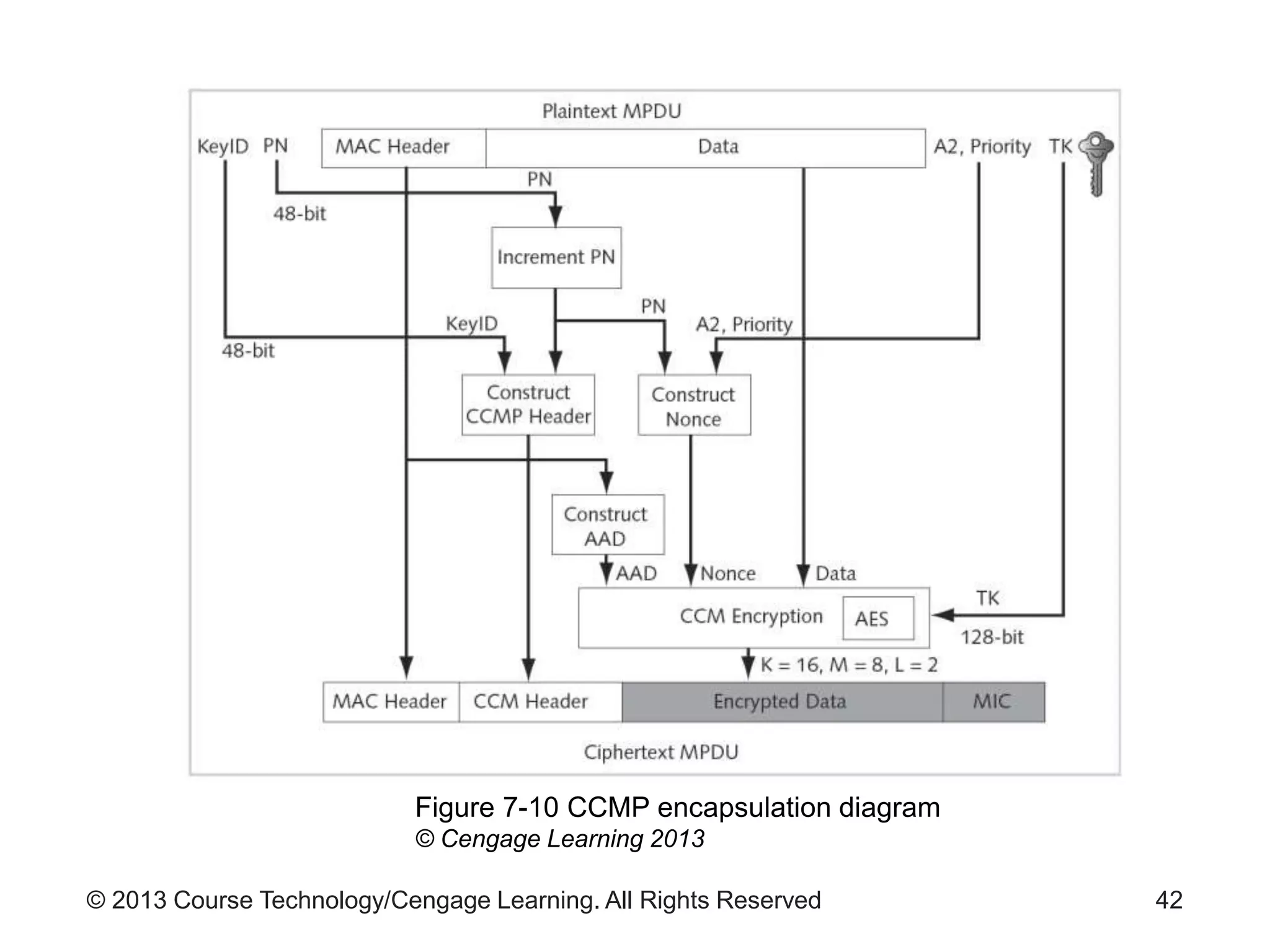
This chapter discusses wireless network security. It defines key wireless technologies like Wi-Fi and Bluetooth. It describes wireless network architectures including basic service sets, distributed systems, and extended service sets. It also covers wireless topologies such as star, mesh, and hybrid configurations. Finally, it discusses wireless security protocols and concerns regarding securing wireless transmissions from interception.