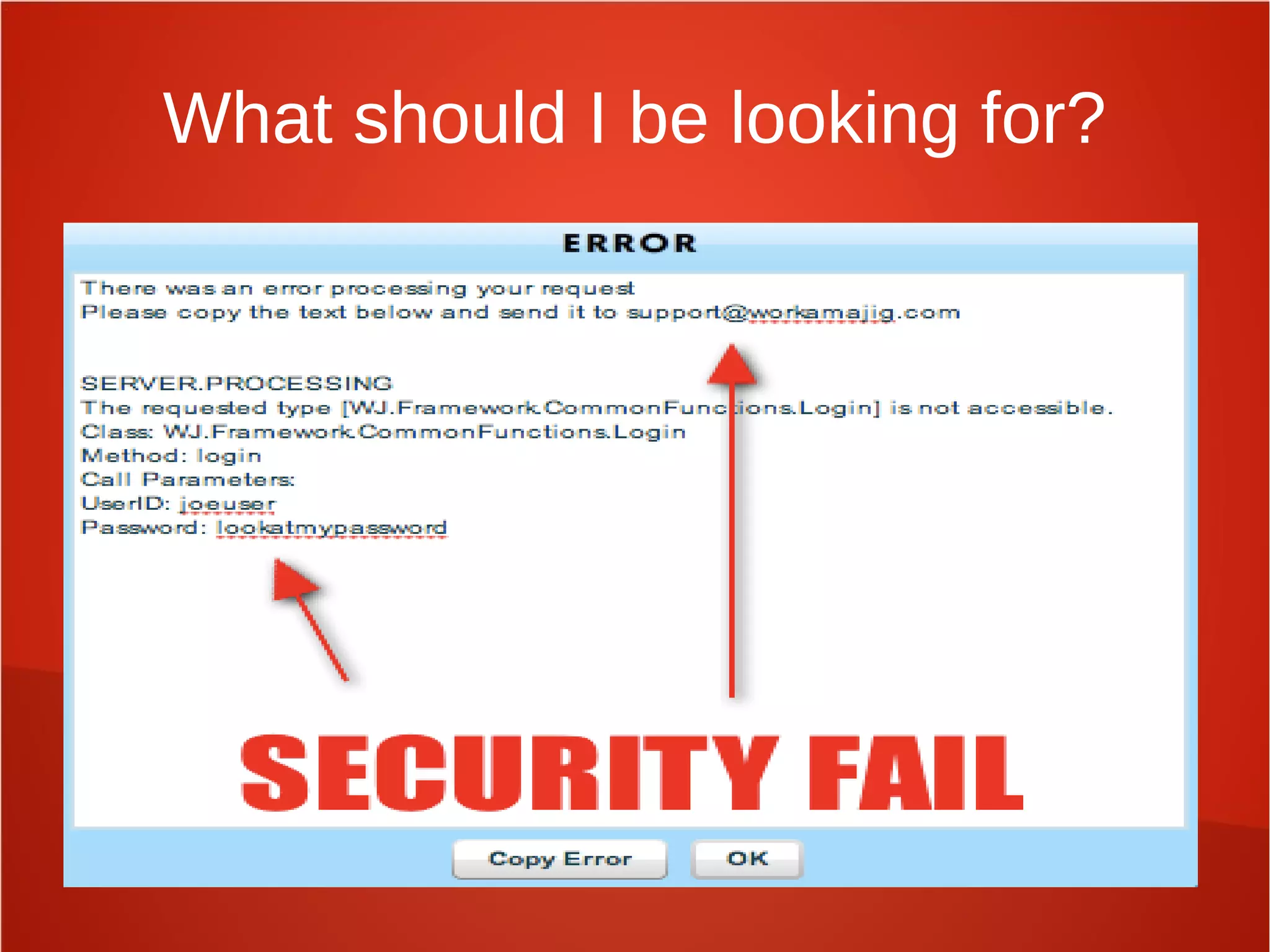
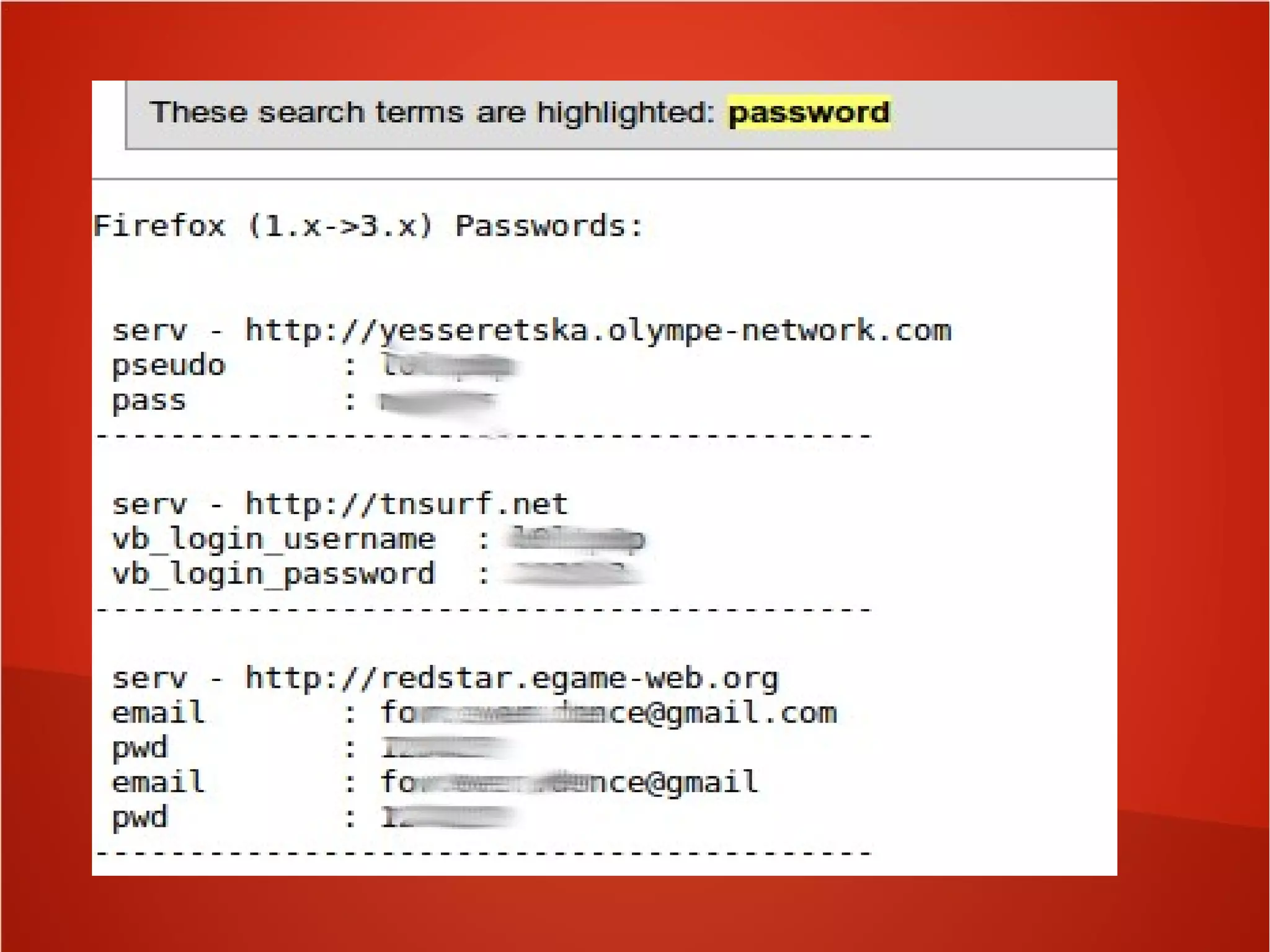
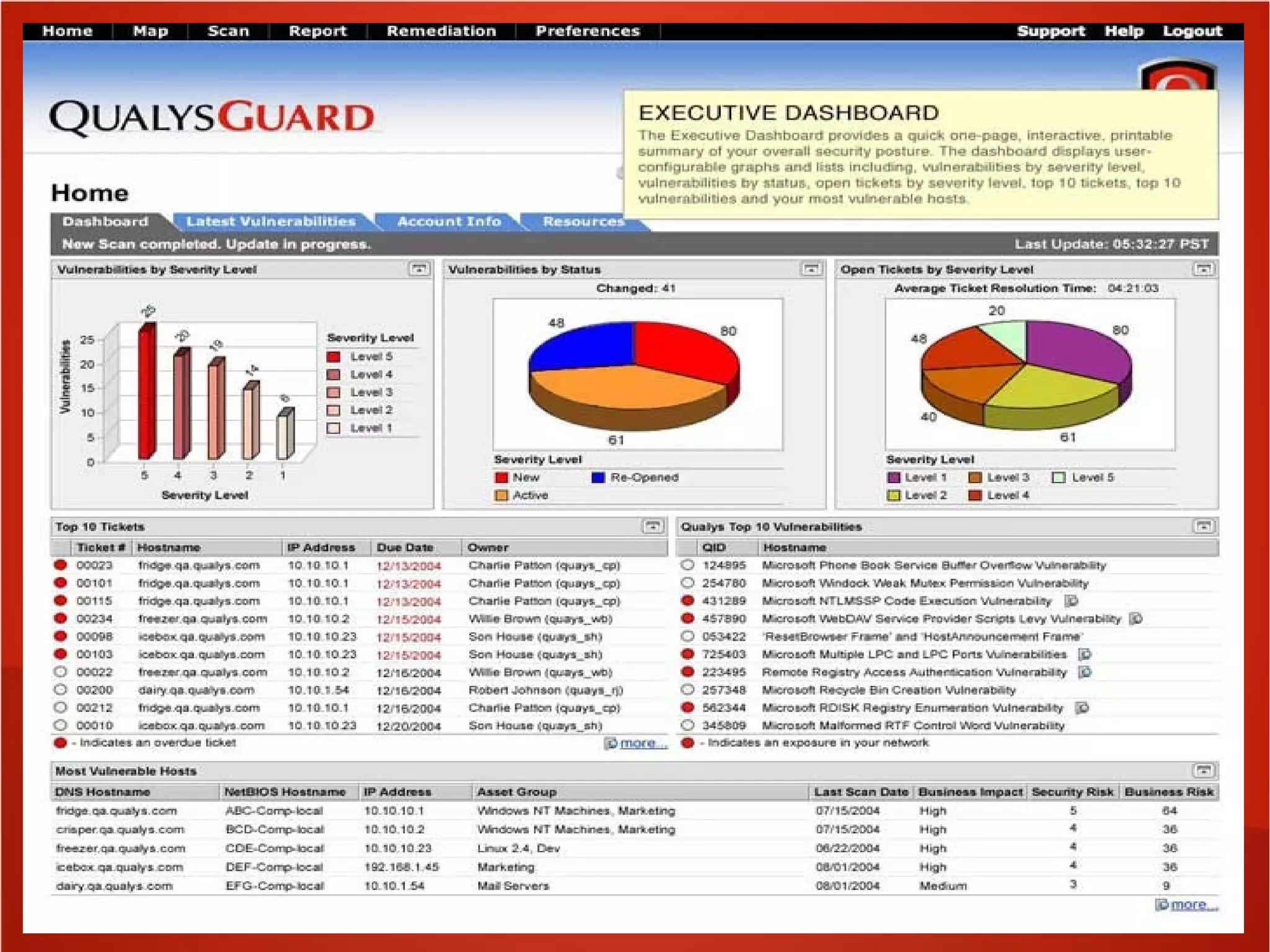
This document provides an overview of security awareness training topics and best practices. It discusses designing training to explain security policies, show practical threats, and empower employees to act as security sensors. Topics covered include corporate policies, regulatory compliance, social engineering, business continuity, emergency response, data handling, personnel security, and physical security. It also provides guidance on teaching policy importance, addressing employee questions, and identifying security risks. Suggested awareness activities include formal training, posters, walkthroughs, and security recognition events. The document emphasizes consistent security metrics, bridging technical and executive perspectives, strategic planning, and annual program reviews.