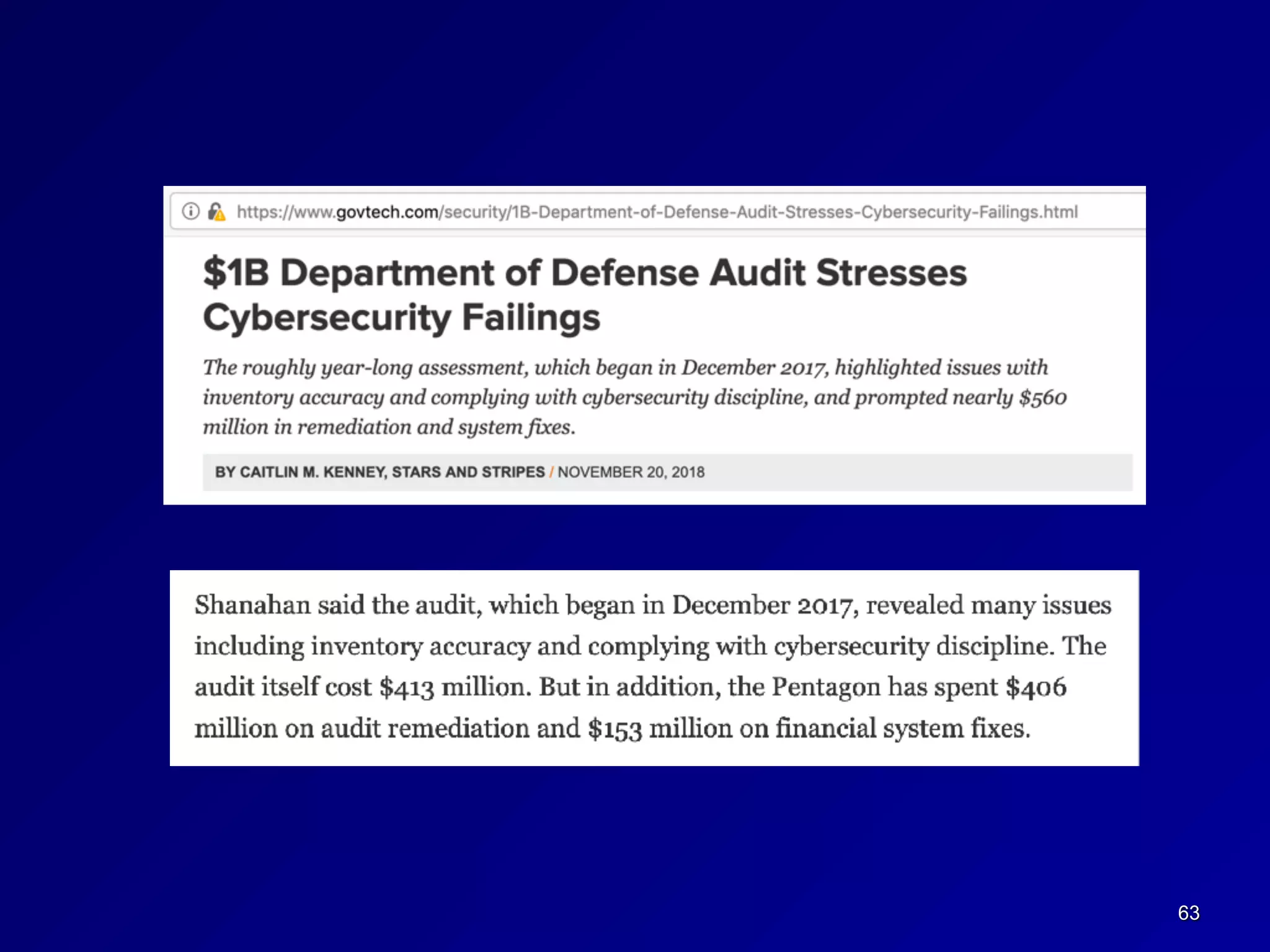
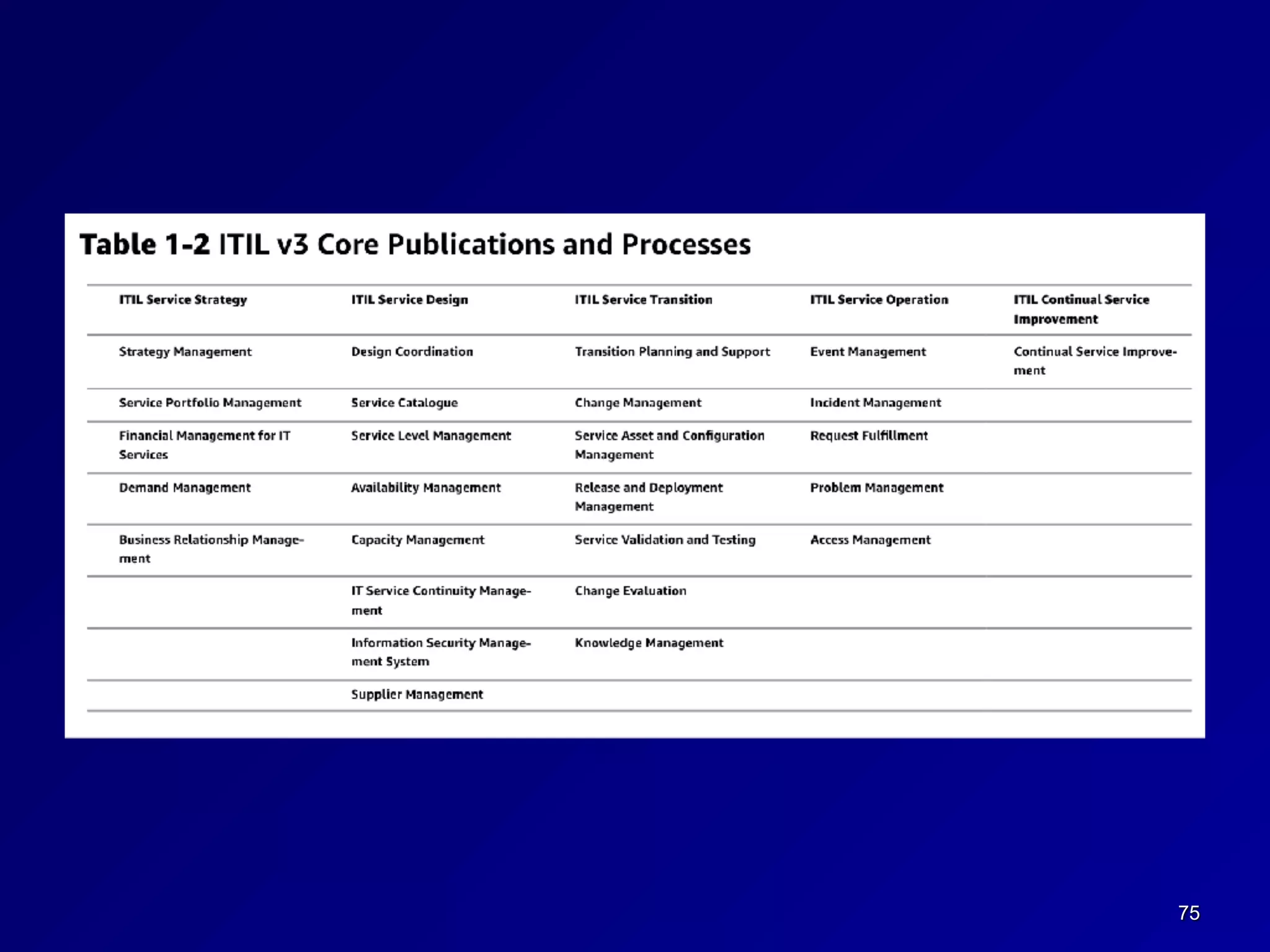
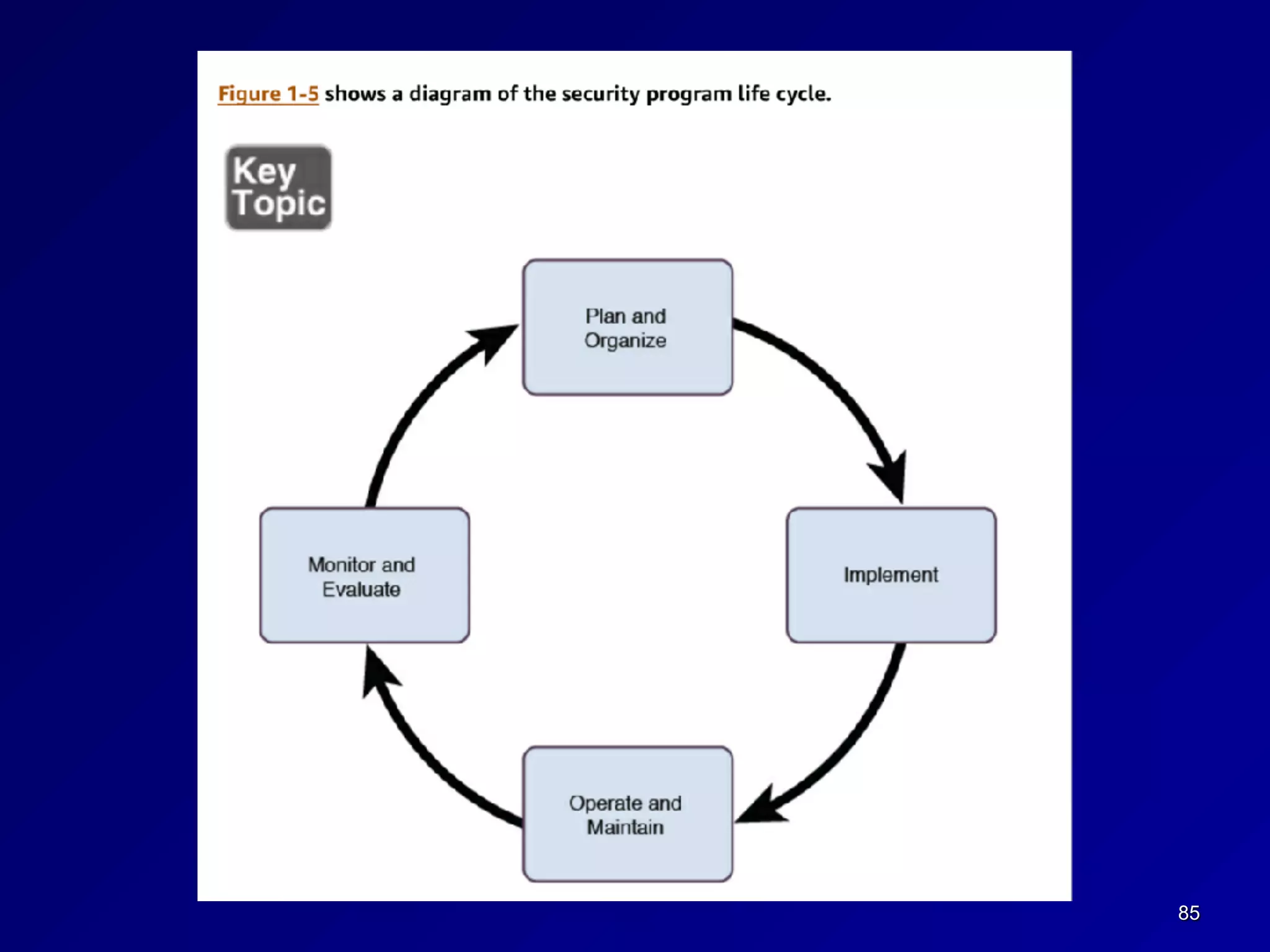
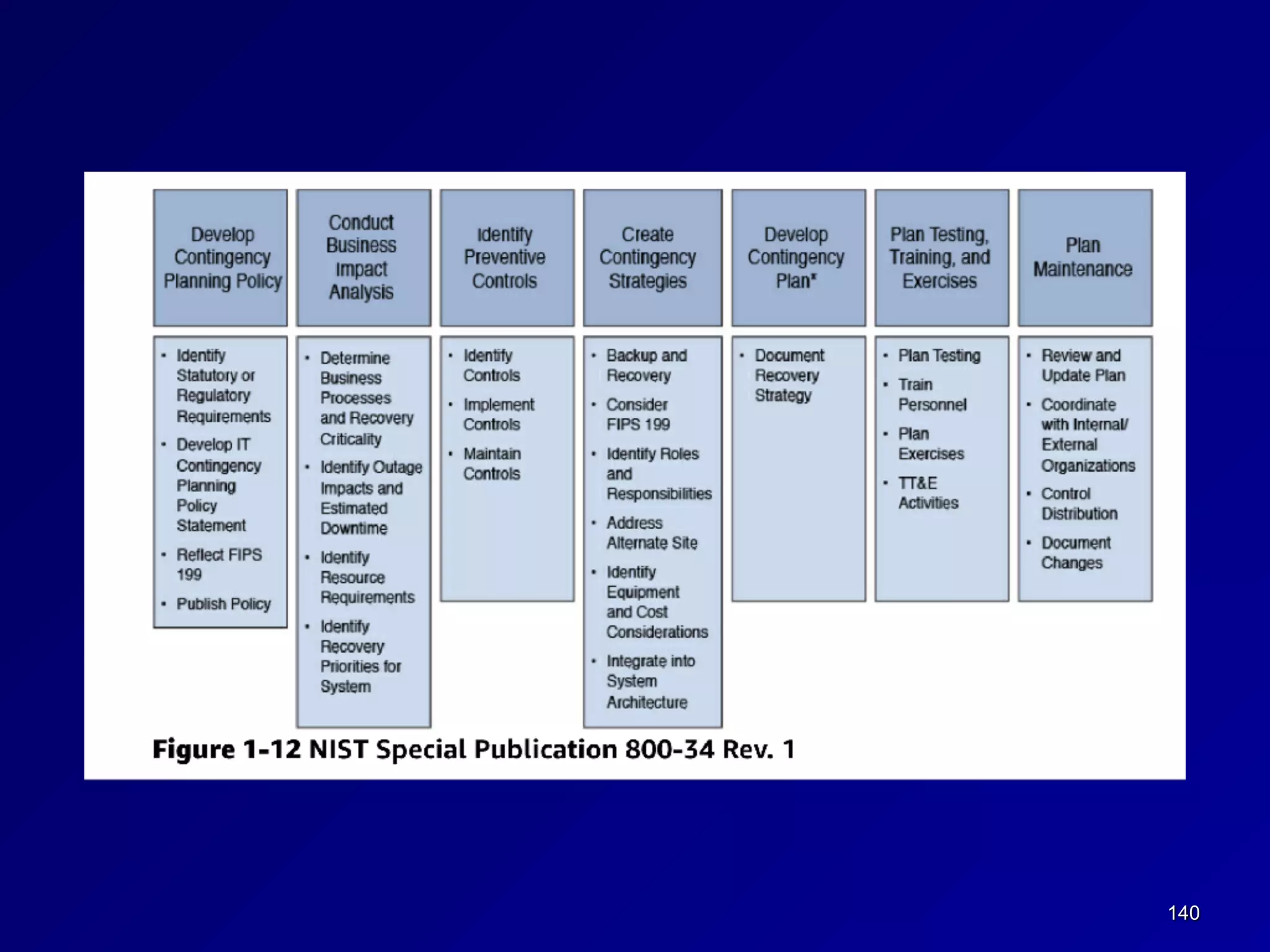
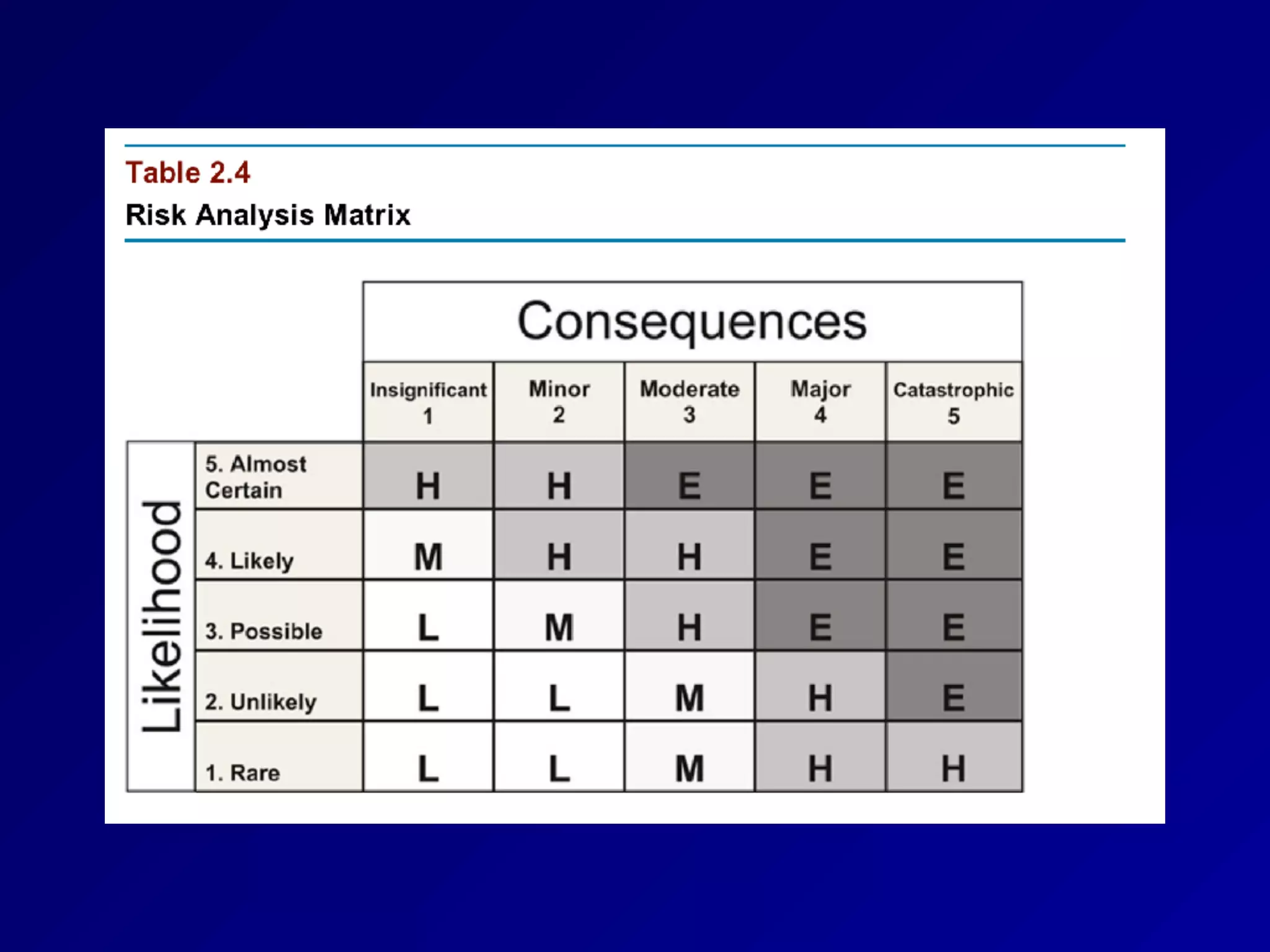
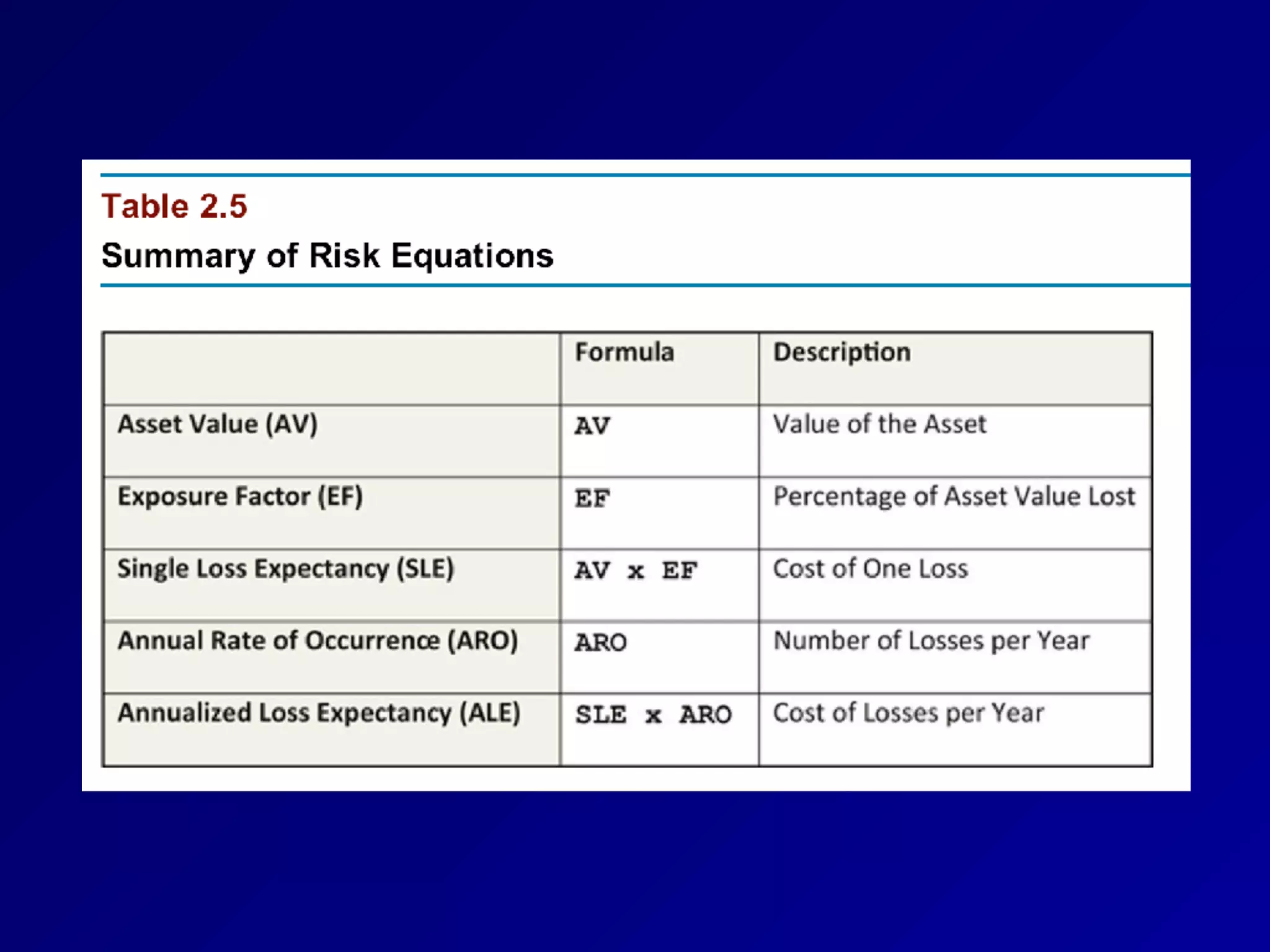
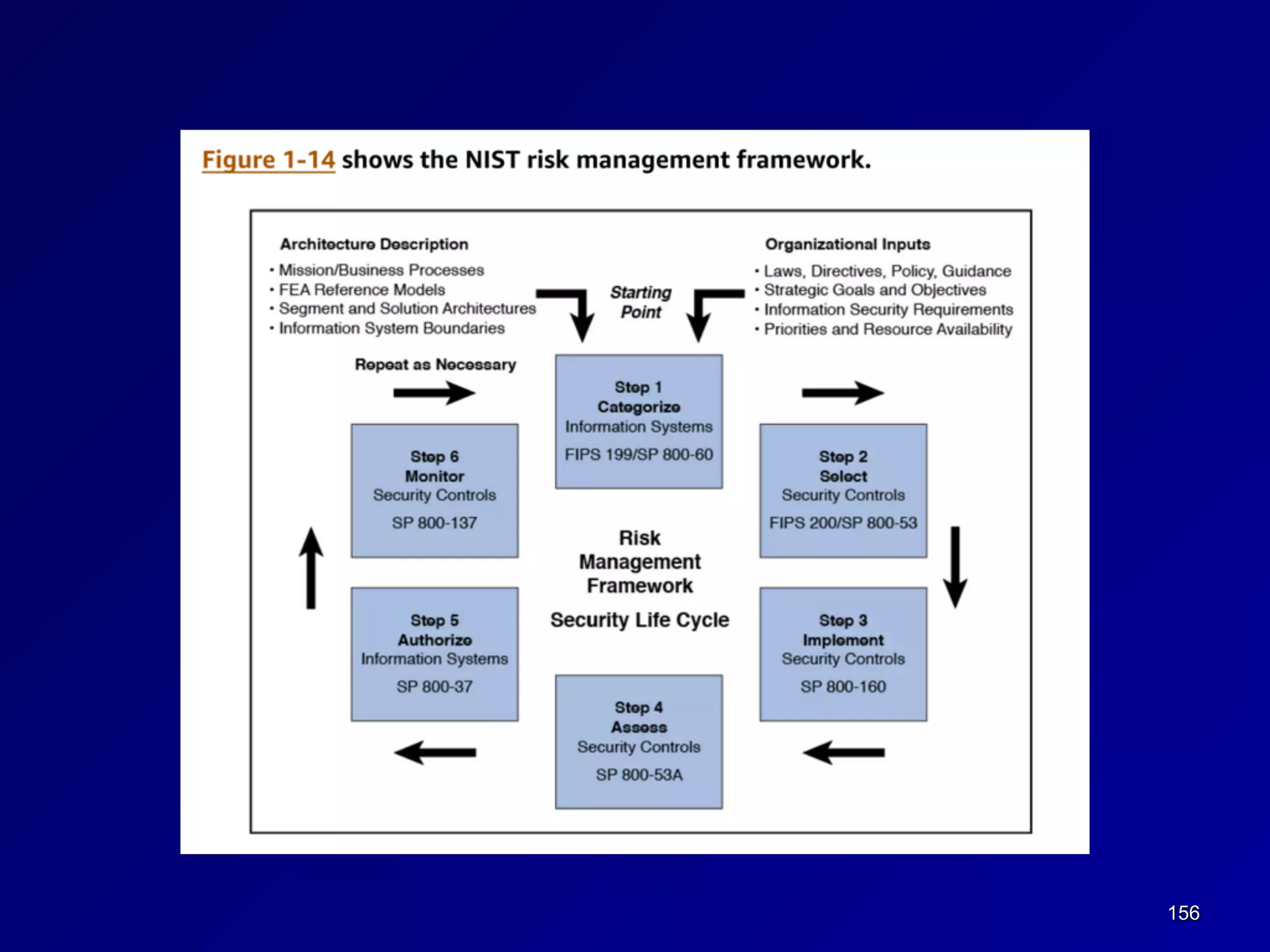
This document provides an overview of chapter 1 of the CNIT 125 course on information security and CISSP preparation. It covers key security terms like confidentiality, integrity, and availability that make up the CIA triad. It also discusses security governance principles such as strategic planning, change management, data classification, and defining security roles and responsibilities. Finally, it introduces several common security control frameworks and standards like ISO 27000, NIST 800 series, and COSO that are used to implement controls and ensure compliance.