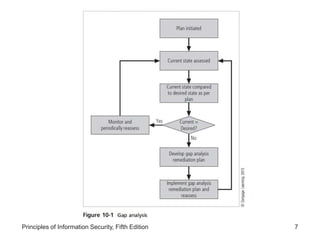
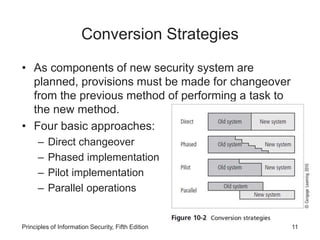
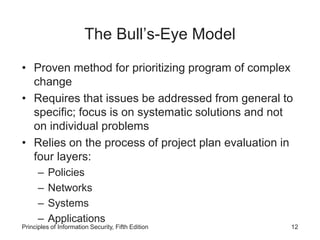
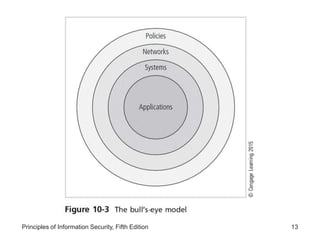
This document discusses the need for project management in information security projects. It explains that most information security projects require a trained project manager or skilled IT manager to oversee implementation. The project manager's role is crucial to the success of complex security projects. The document also outlines technical and non-technical considerations for implementing a project plan, such as conversion strategies, change management processes, and organizational readiness for change.