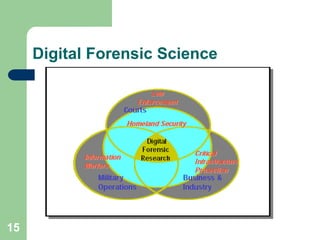
This document discusses the fundamentals of computer forensics and digital forensics. It defines digital forensics science and explains that it has three main communities - law enforcement, military, and private sector. The document outlines the investigative process in digital forensics and categorizes the different types of analysis. It also discusses challenges in the field like the lack of standards and it being a new science.