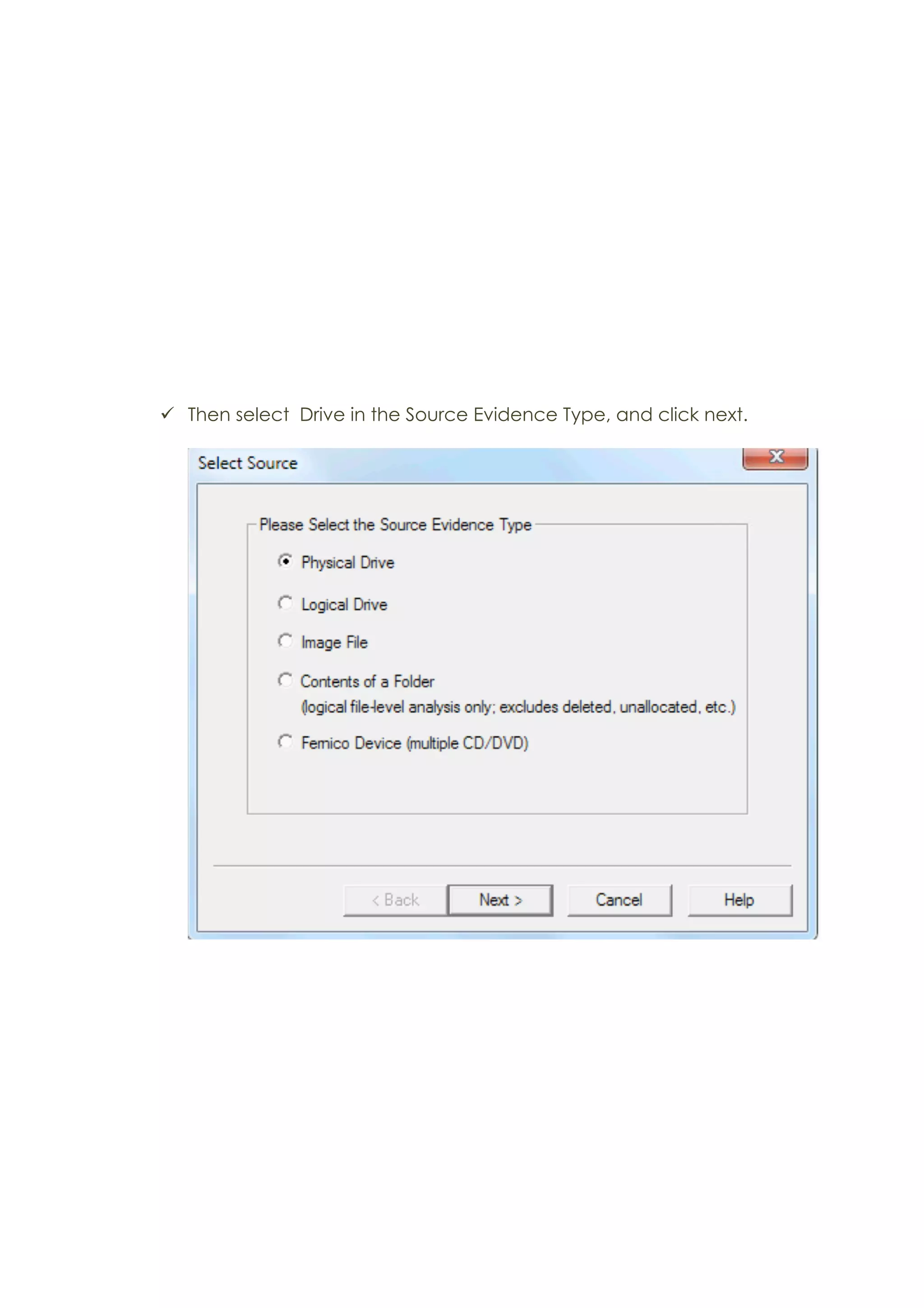
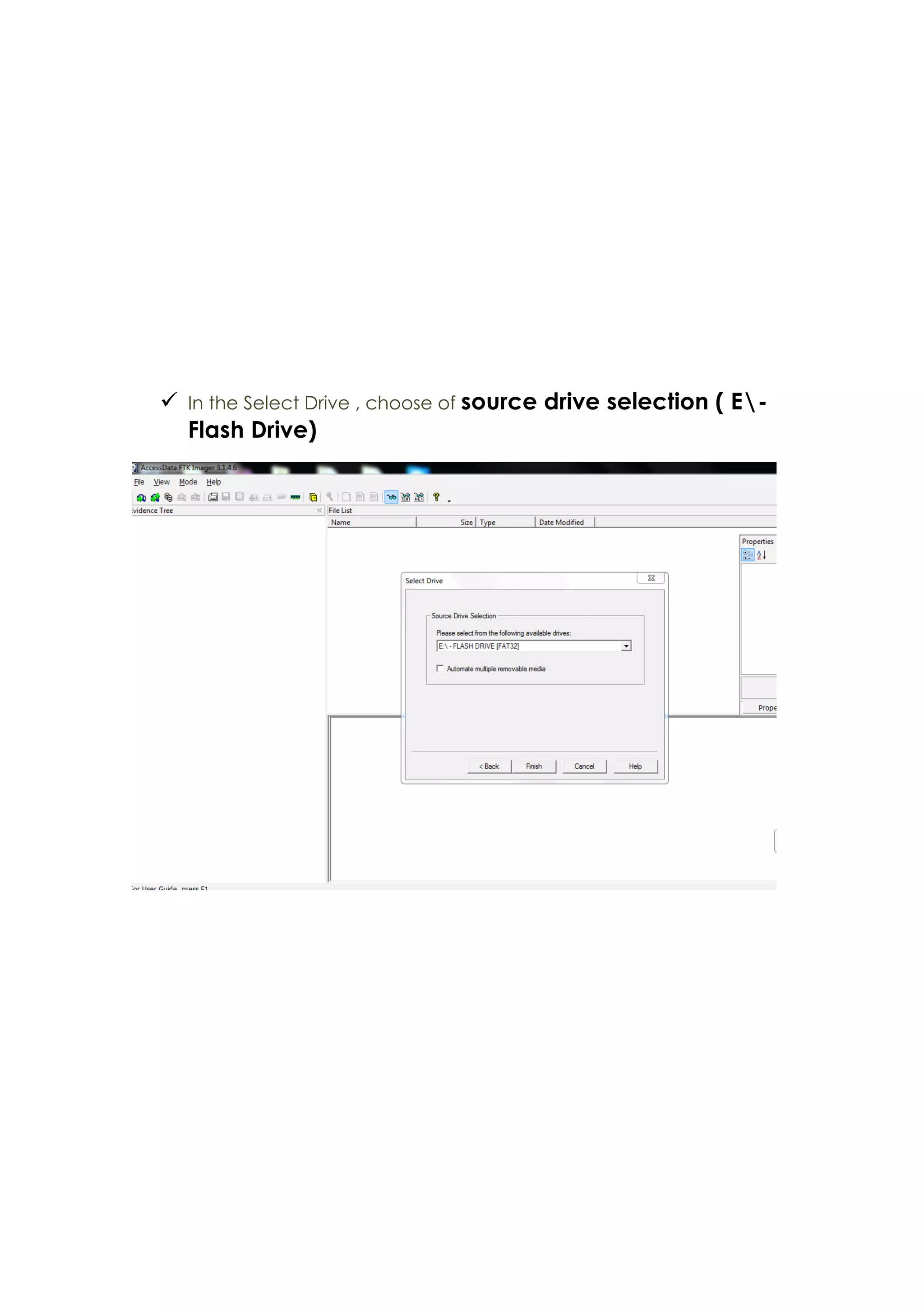
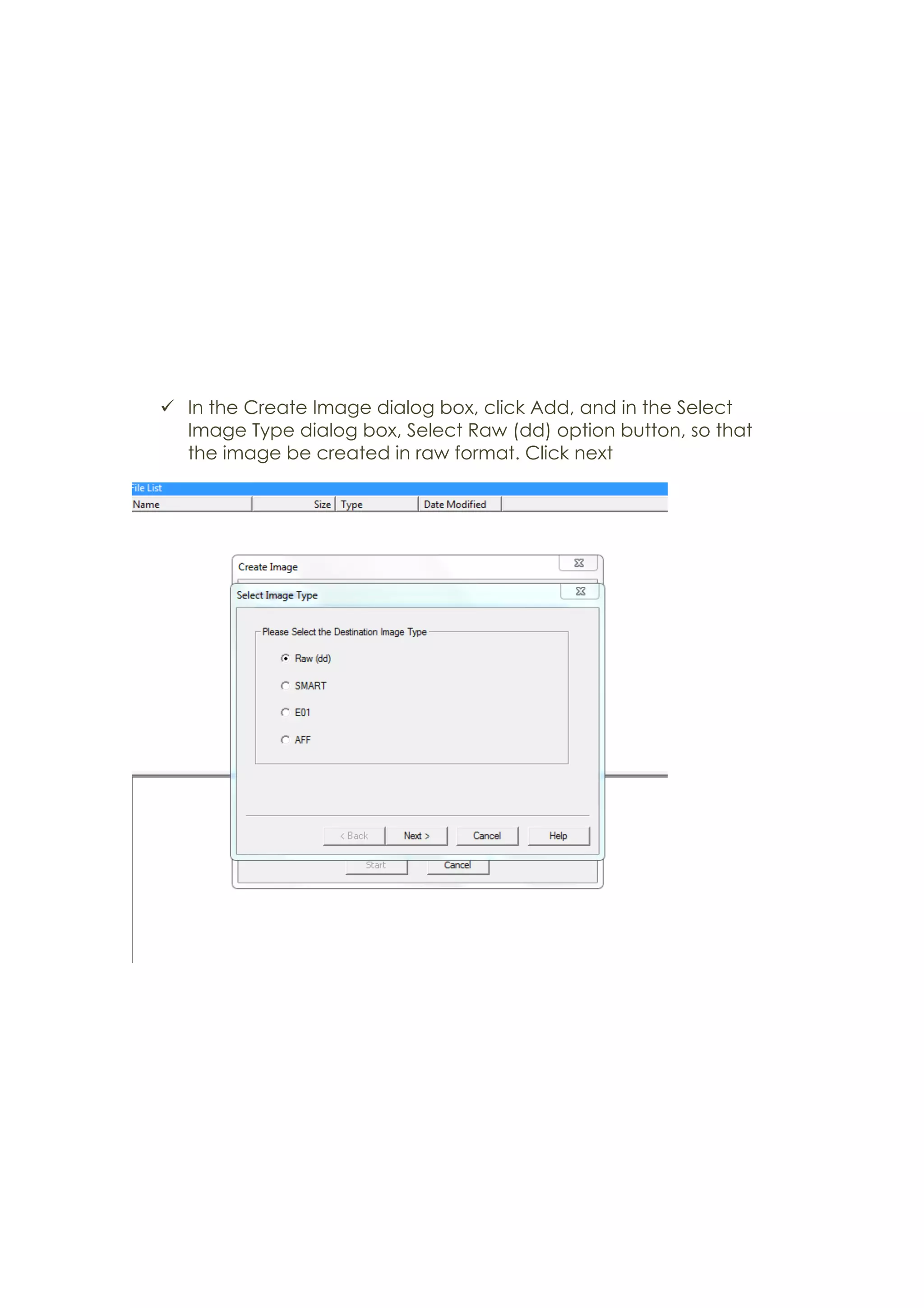
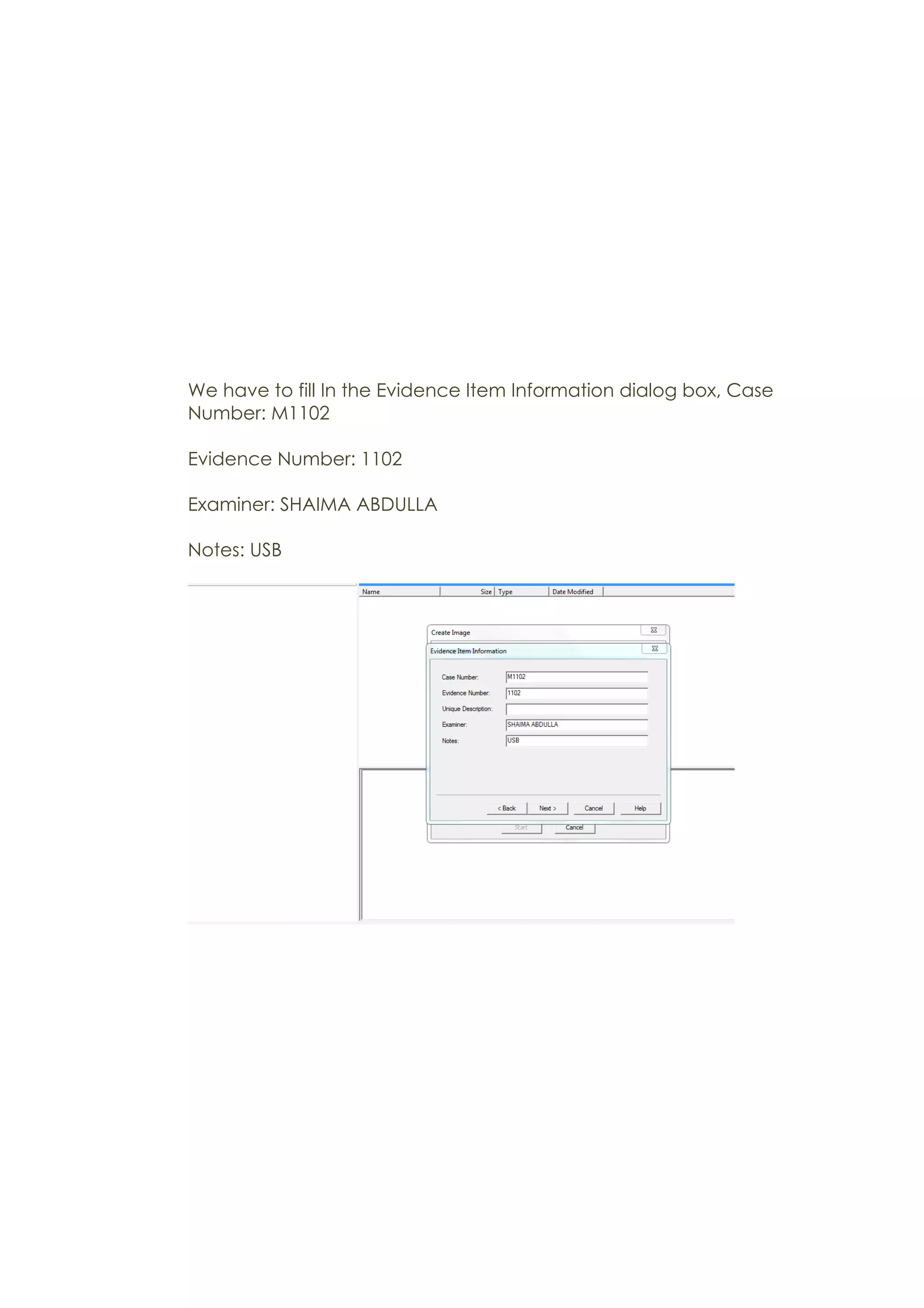
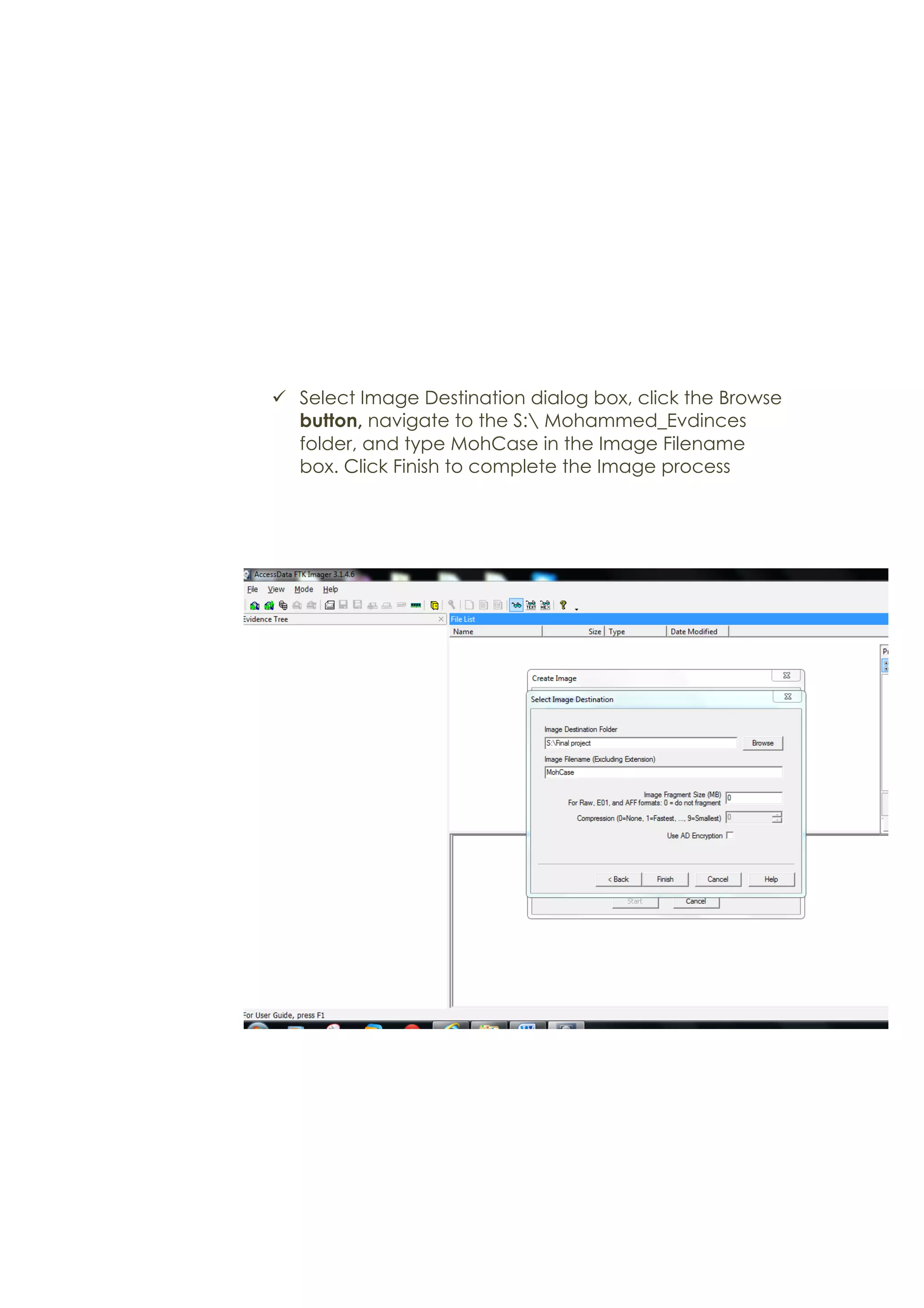
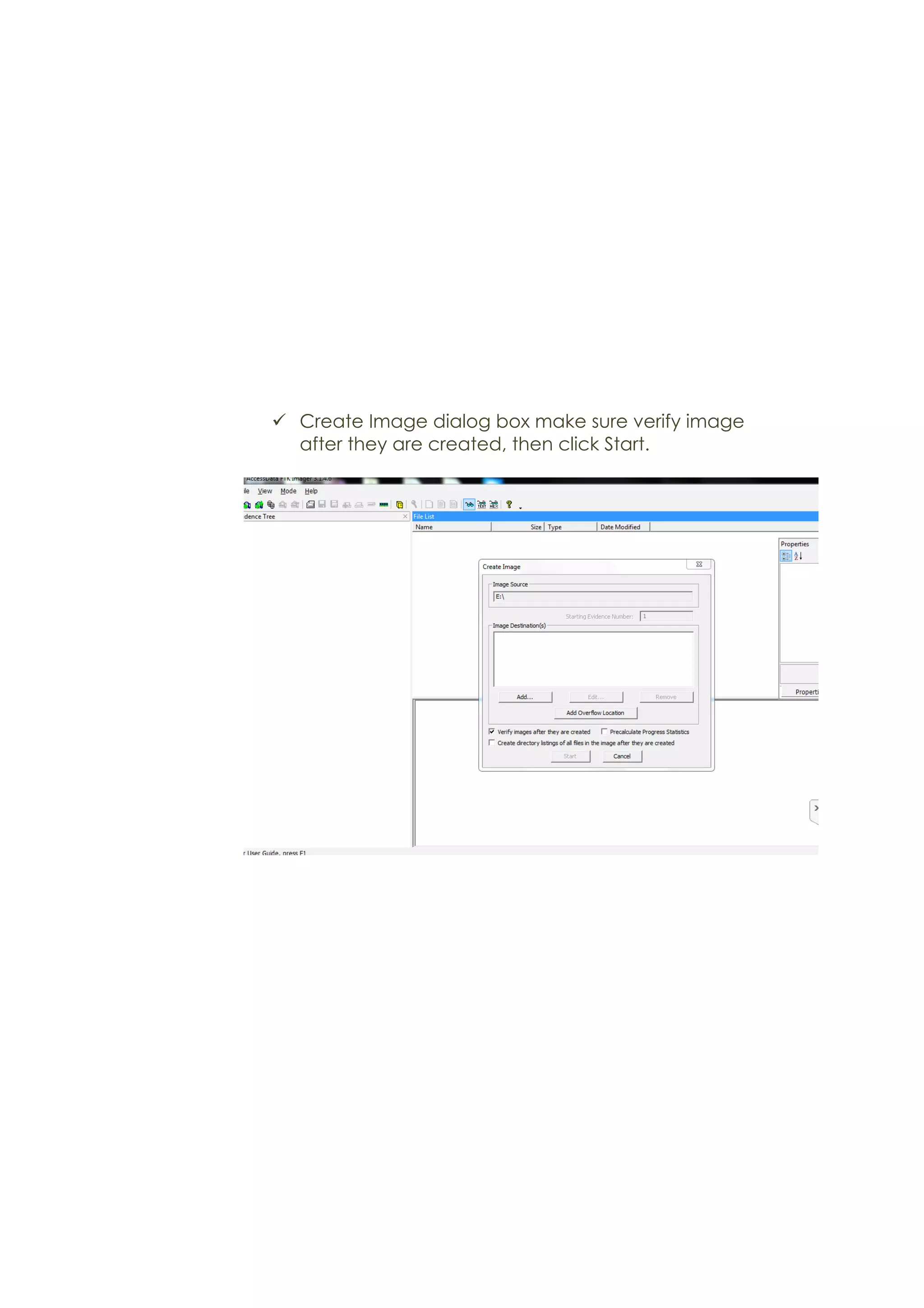
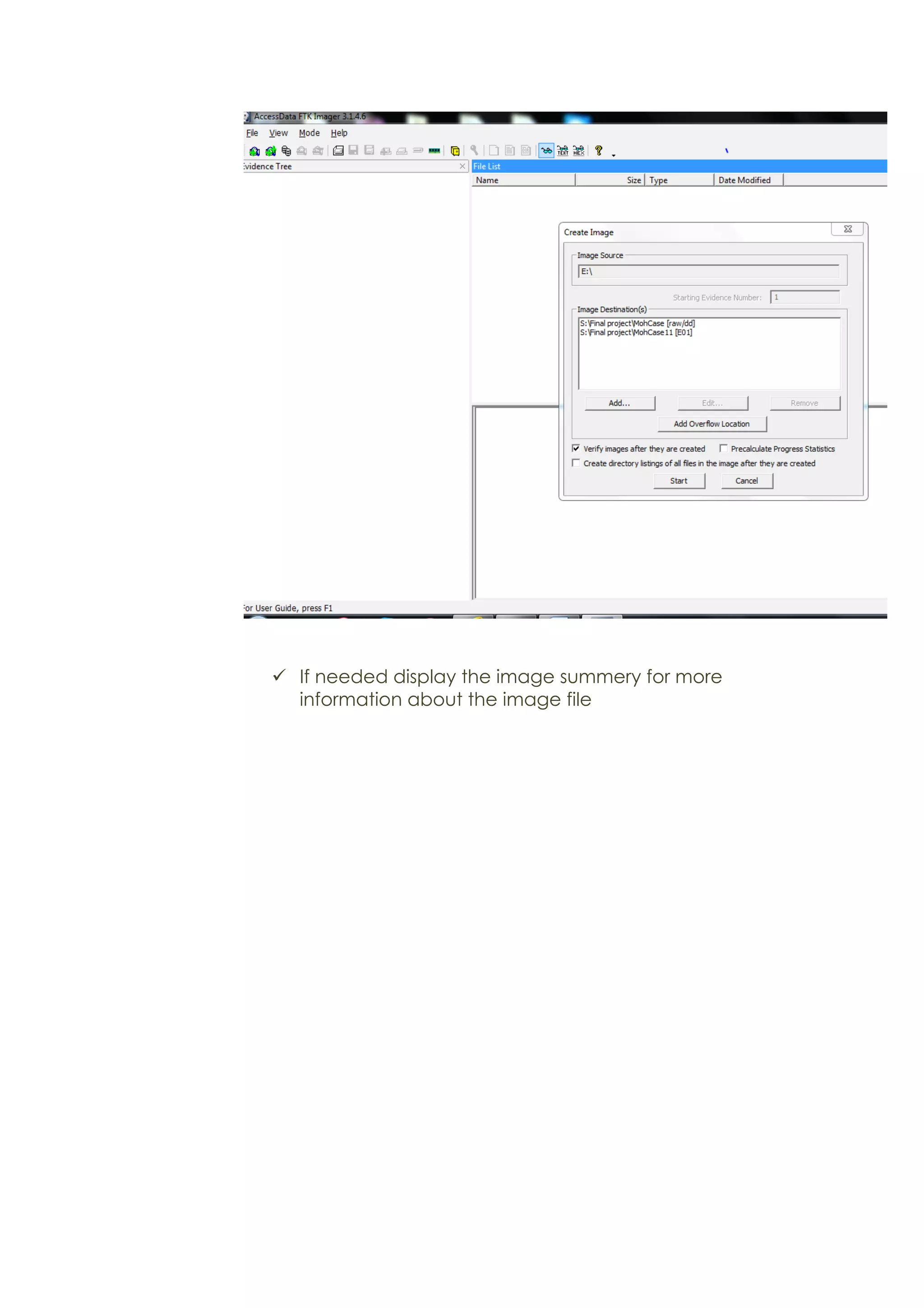
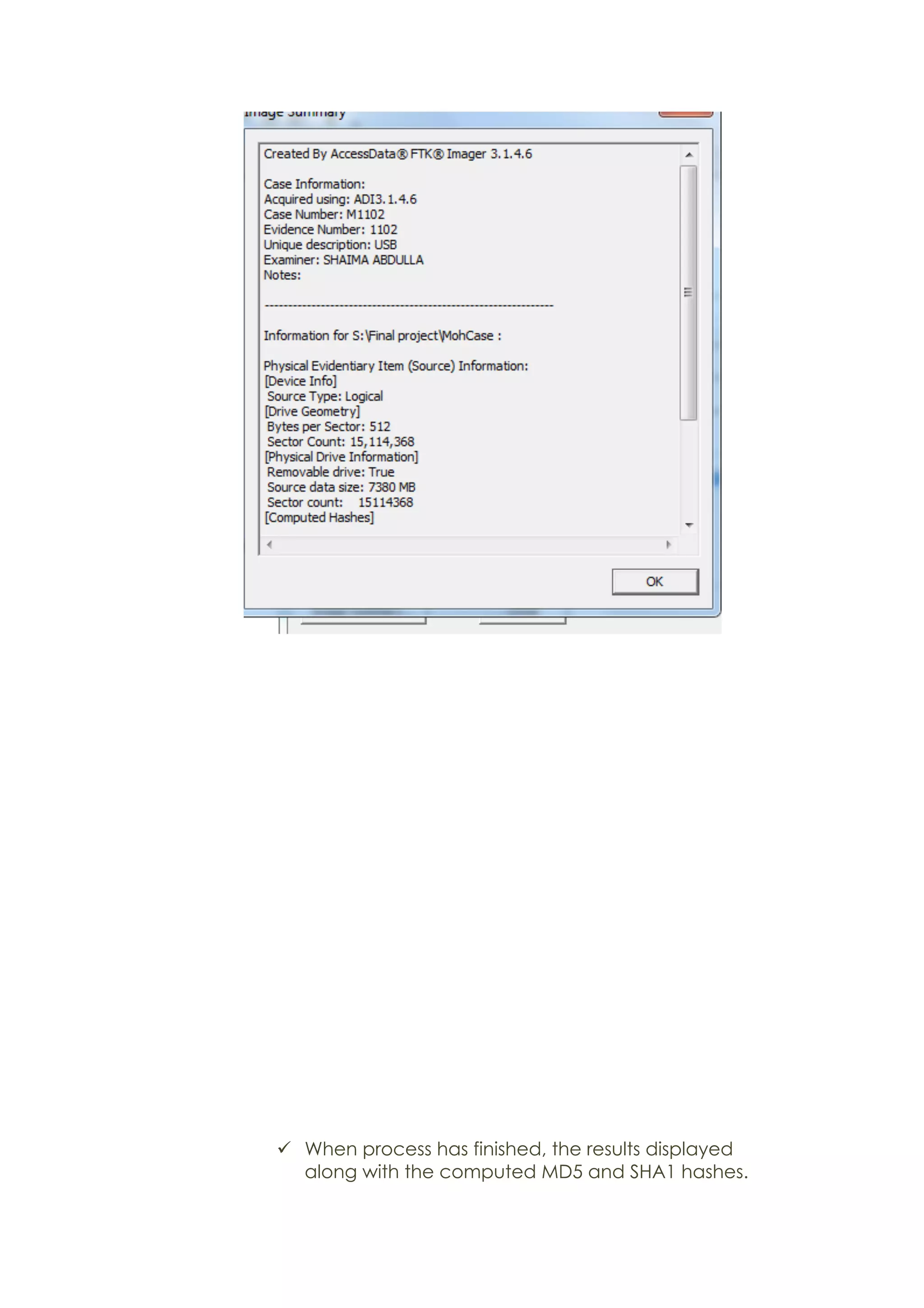
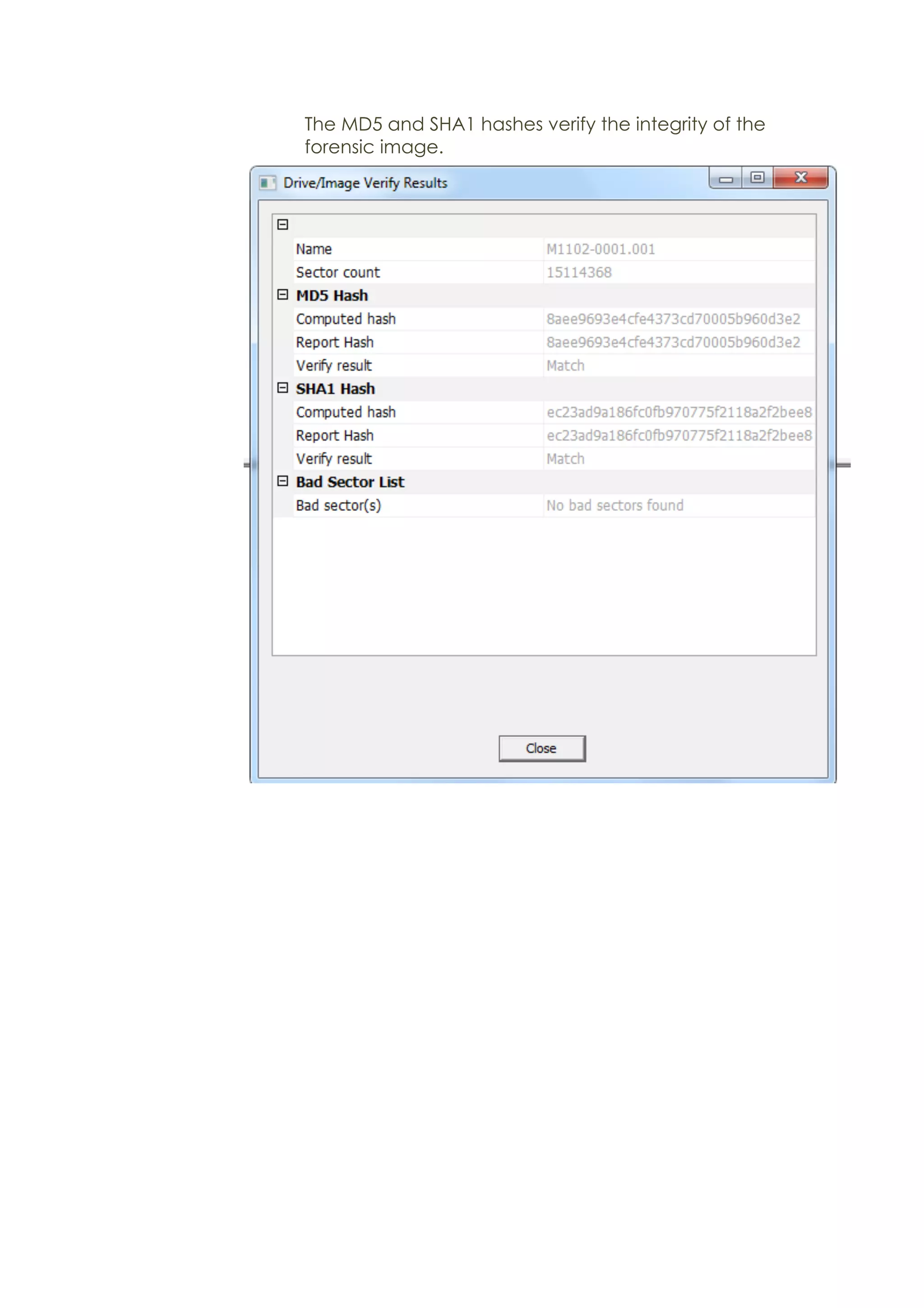
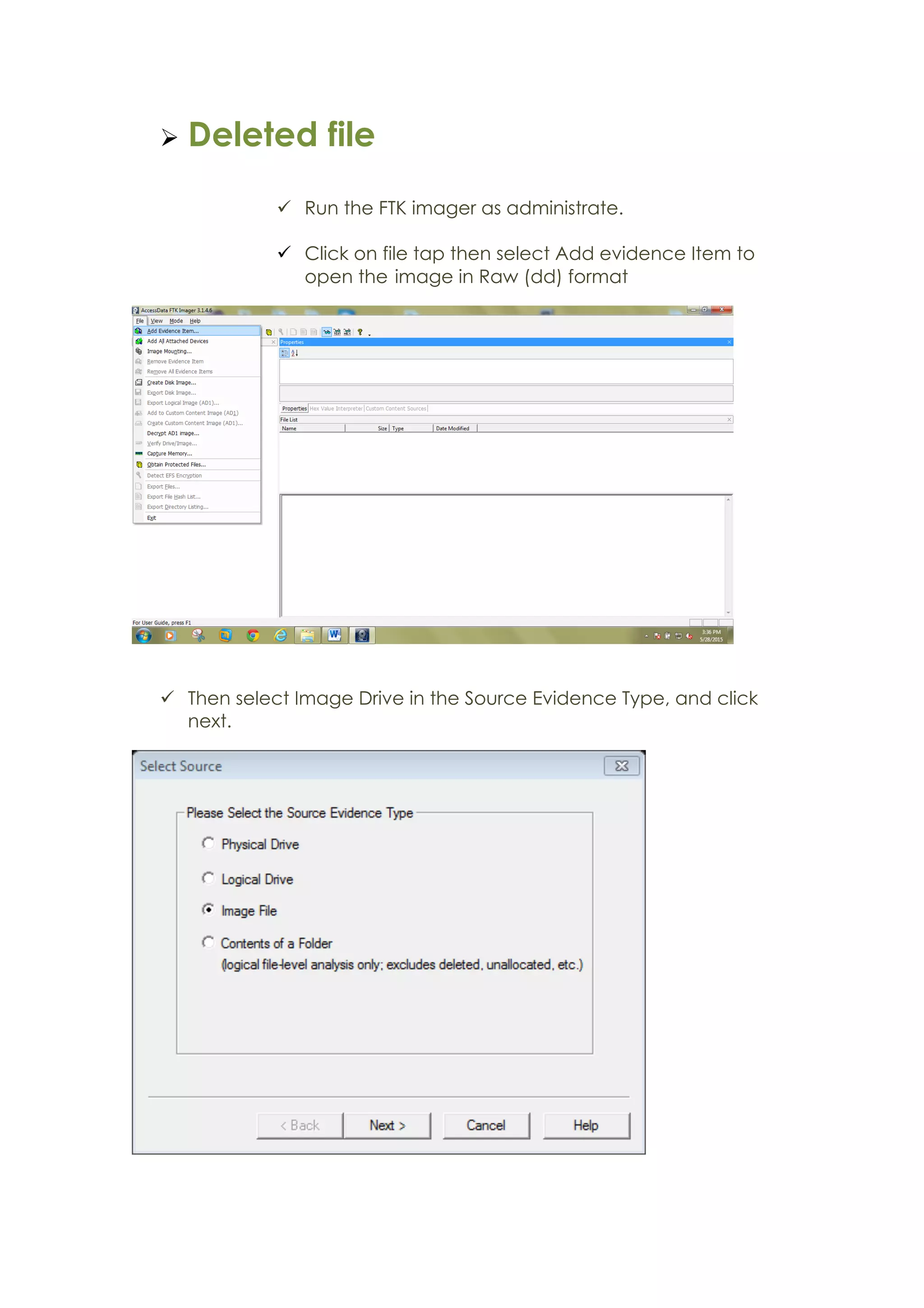
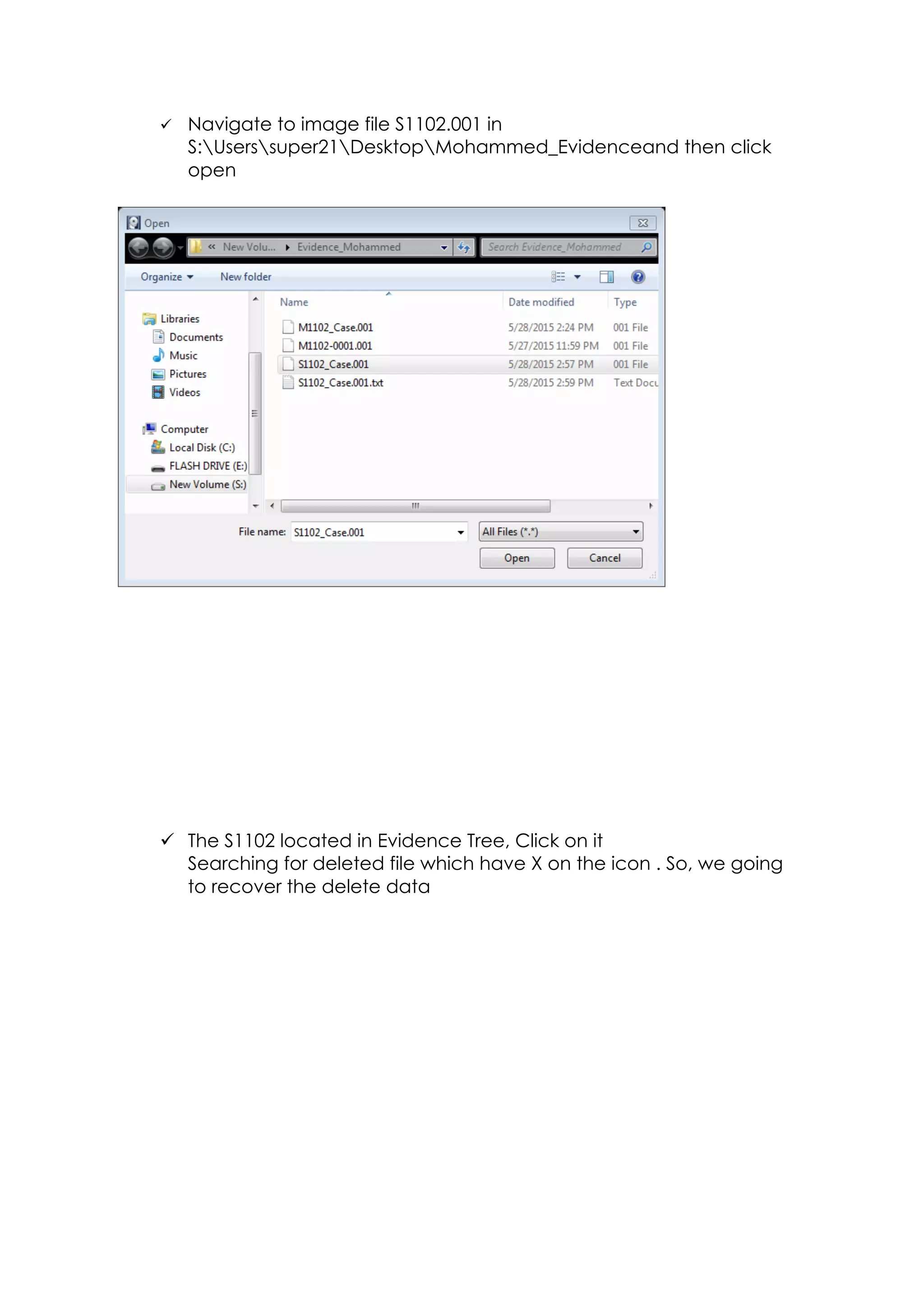
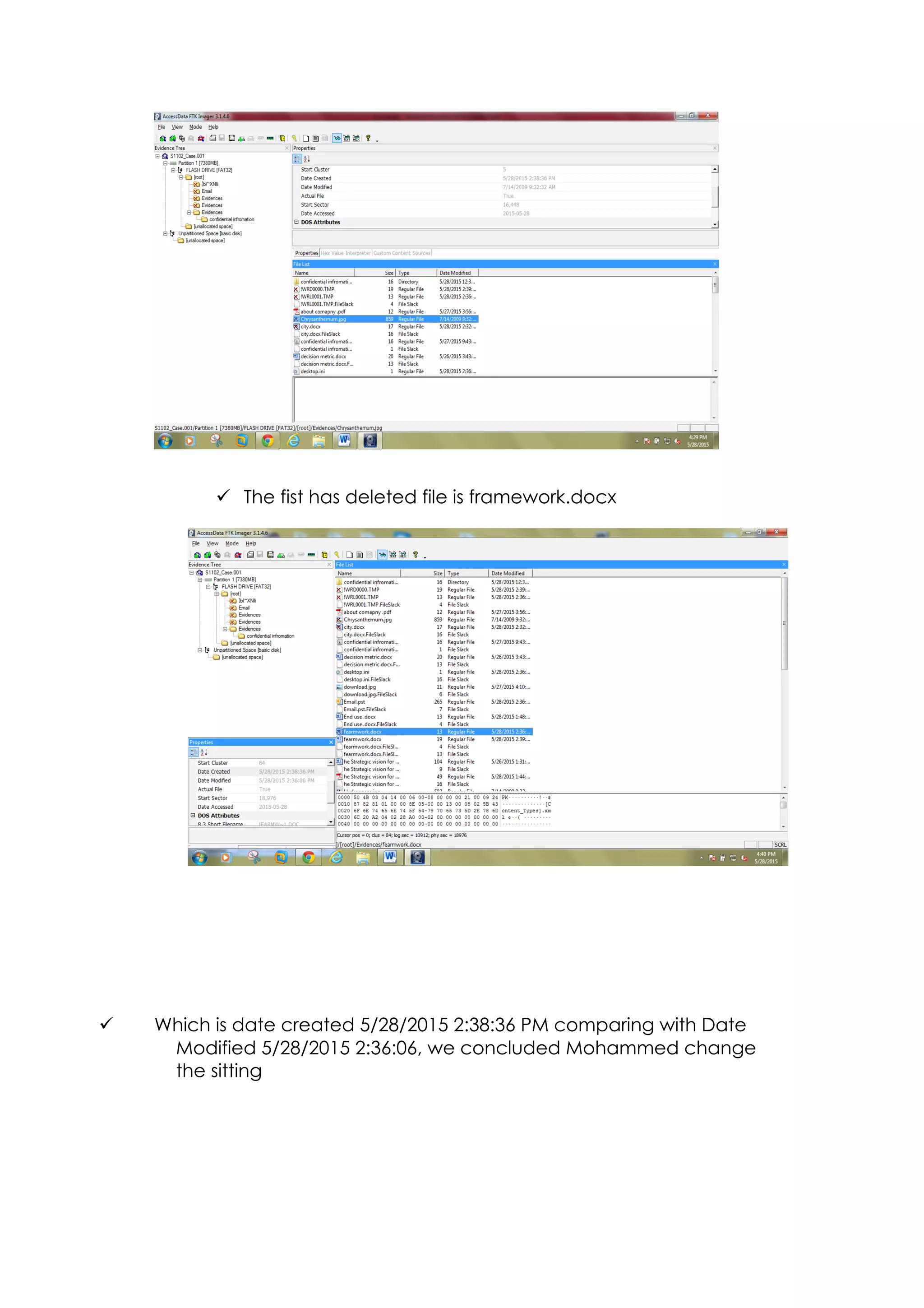
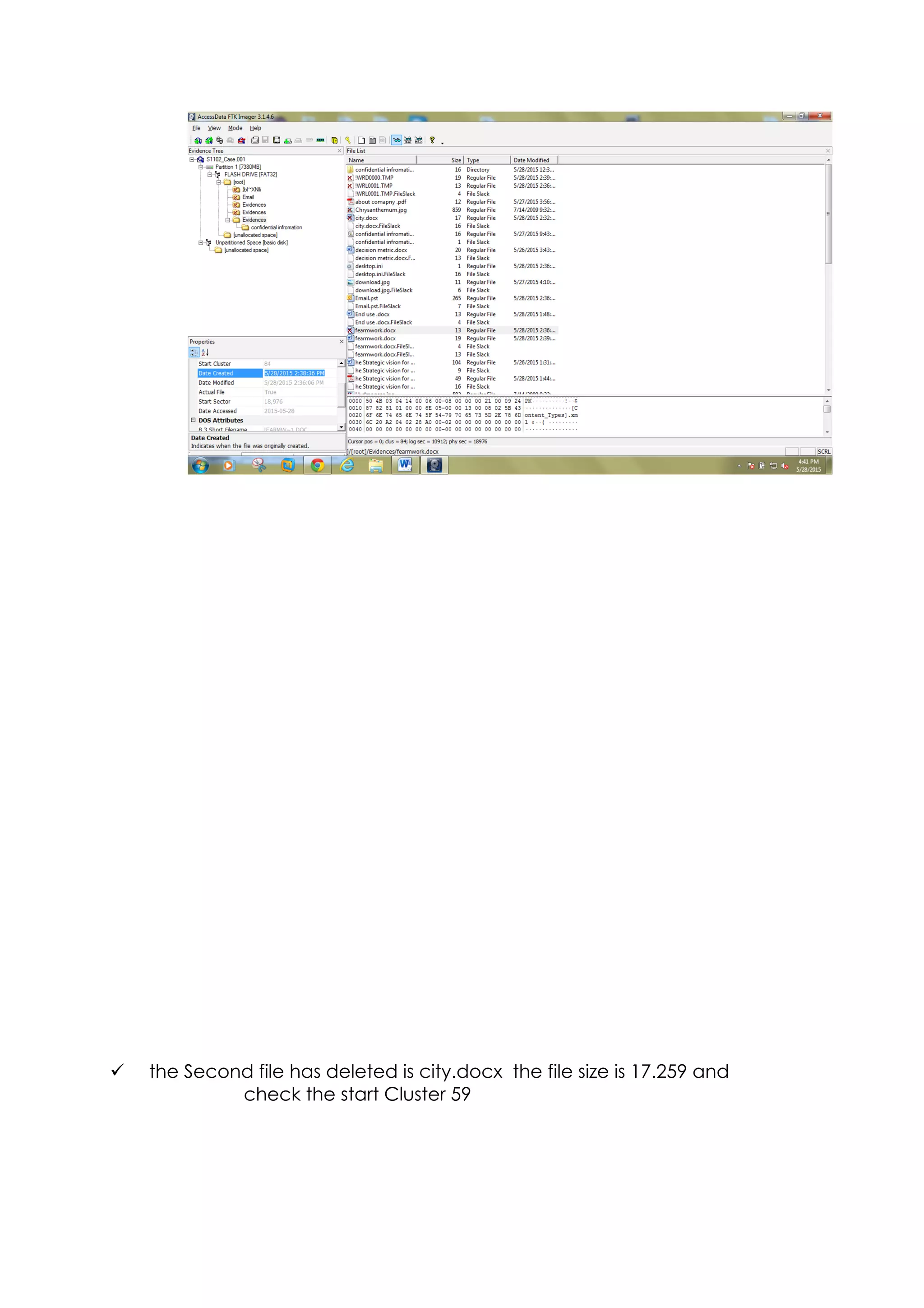
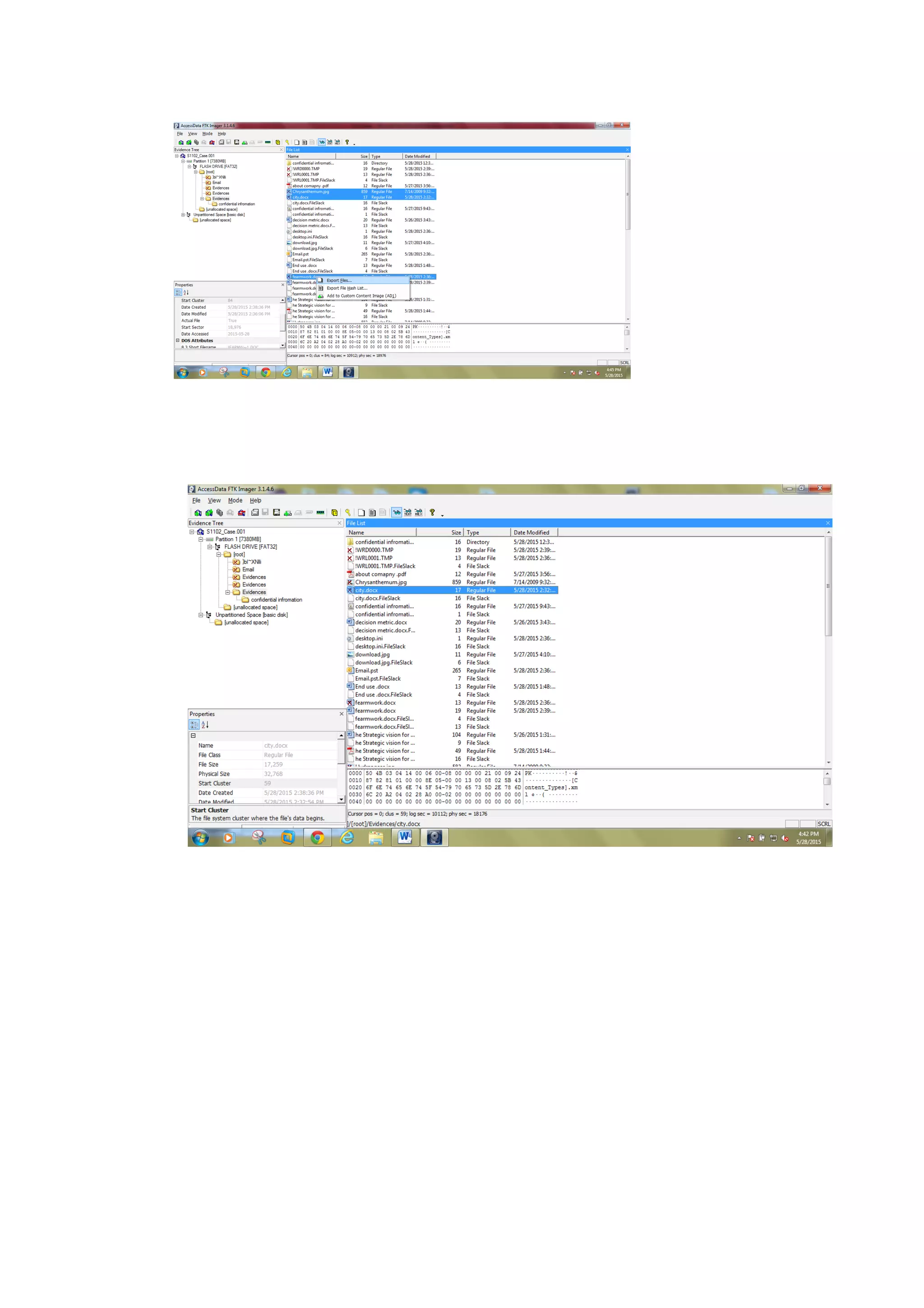
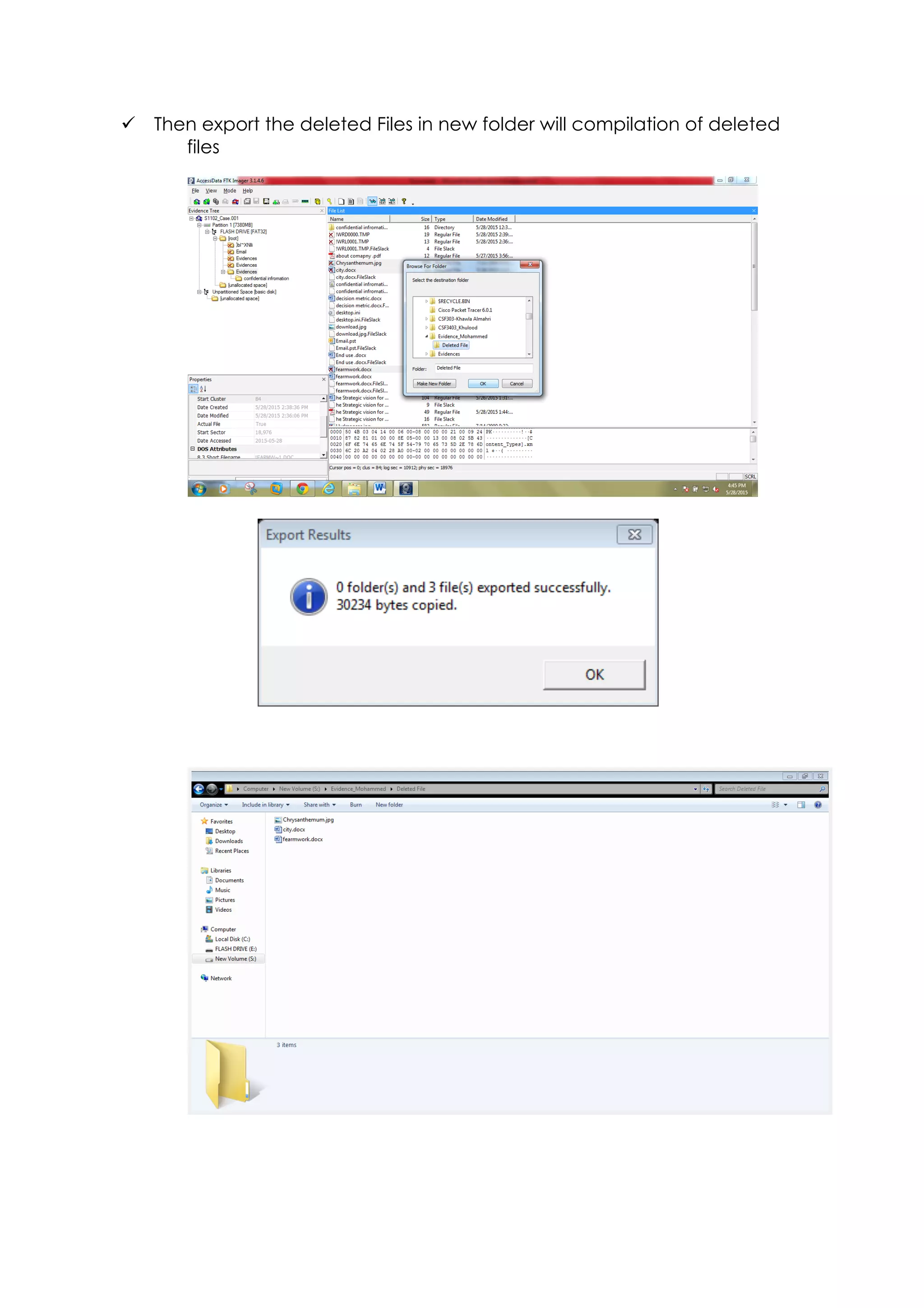
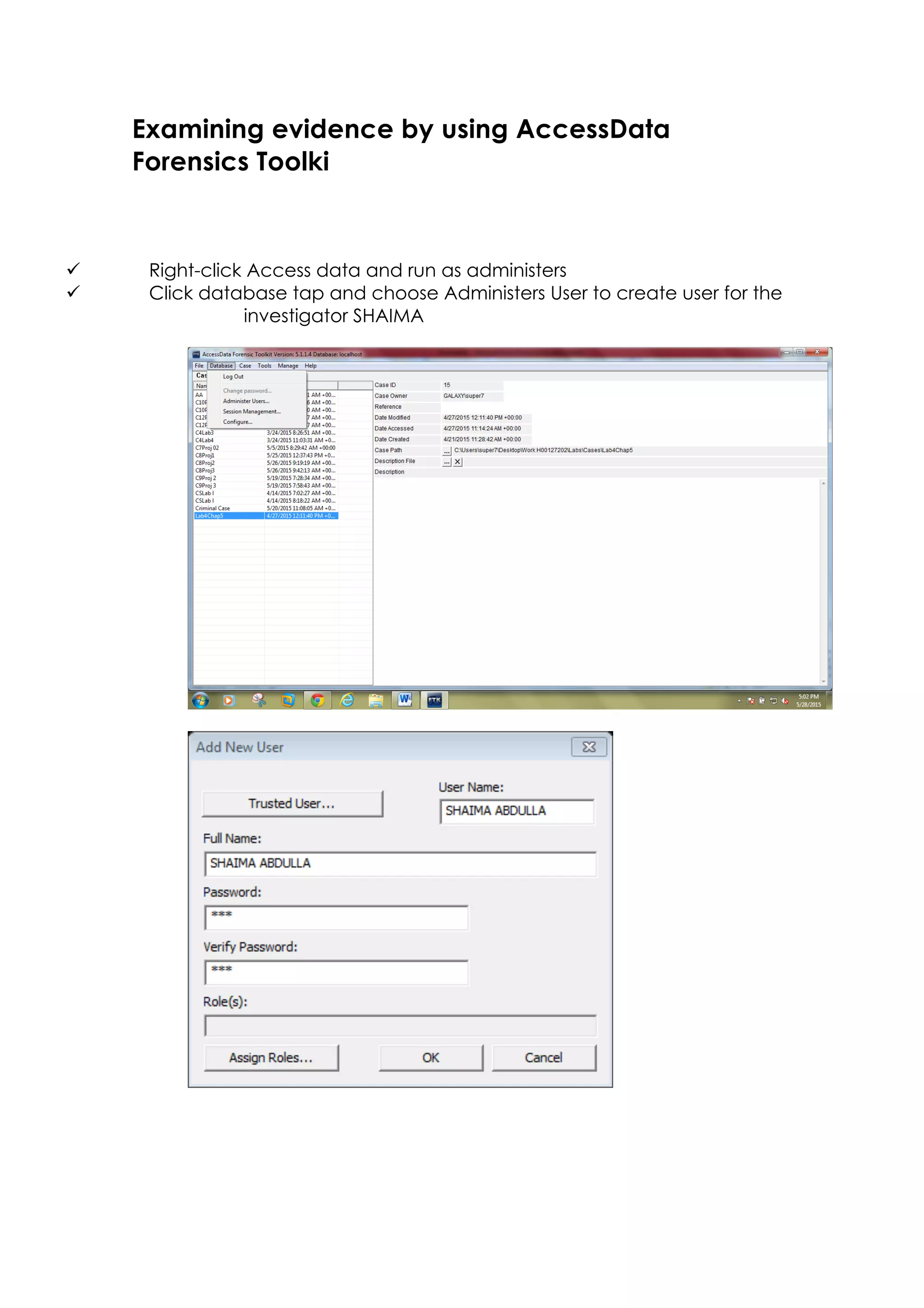
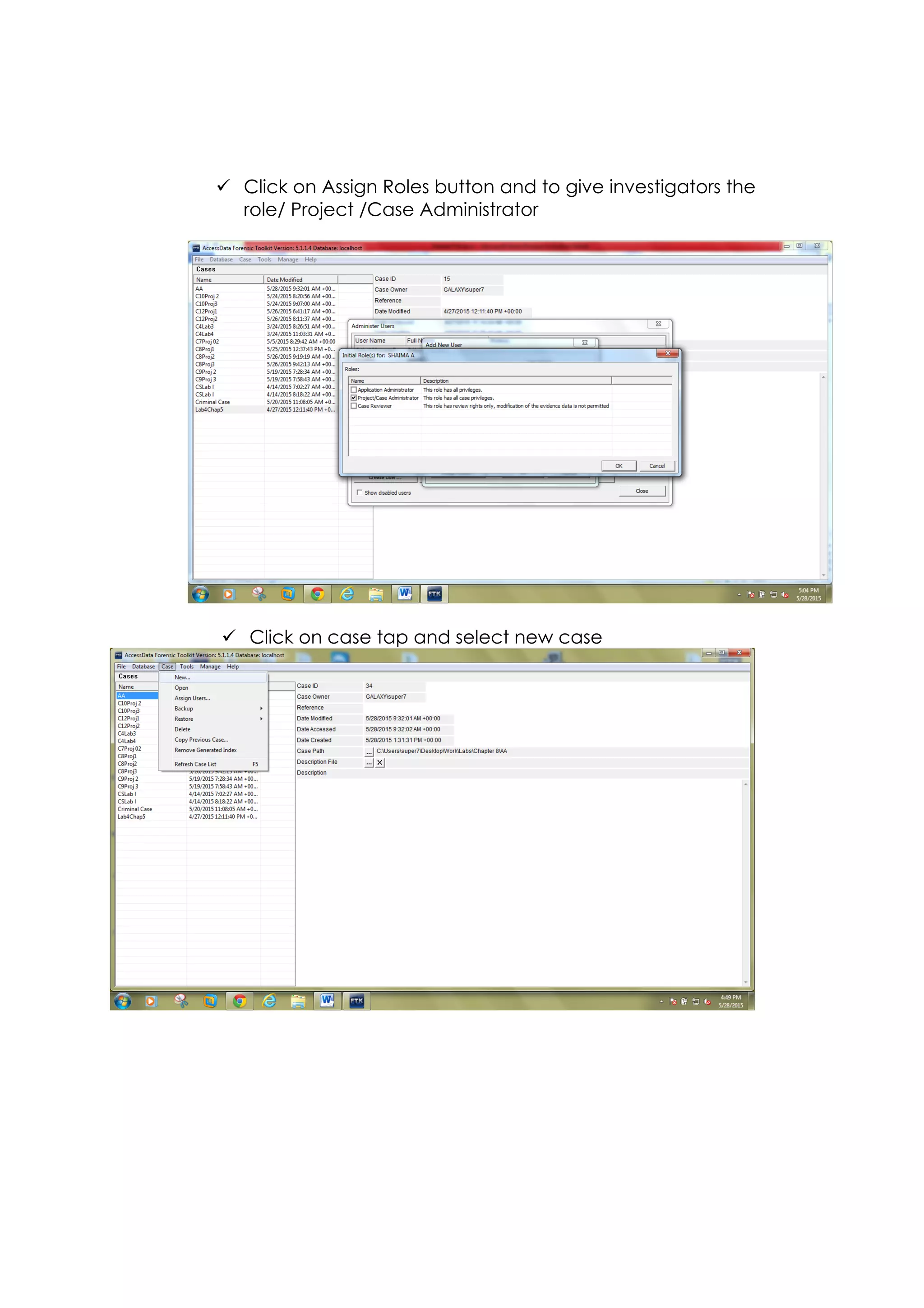
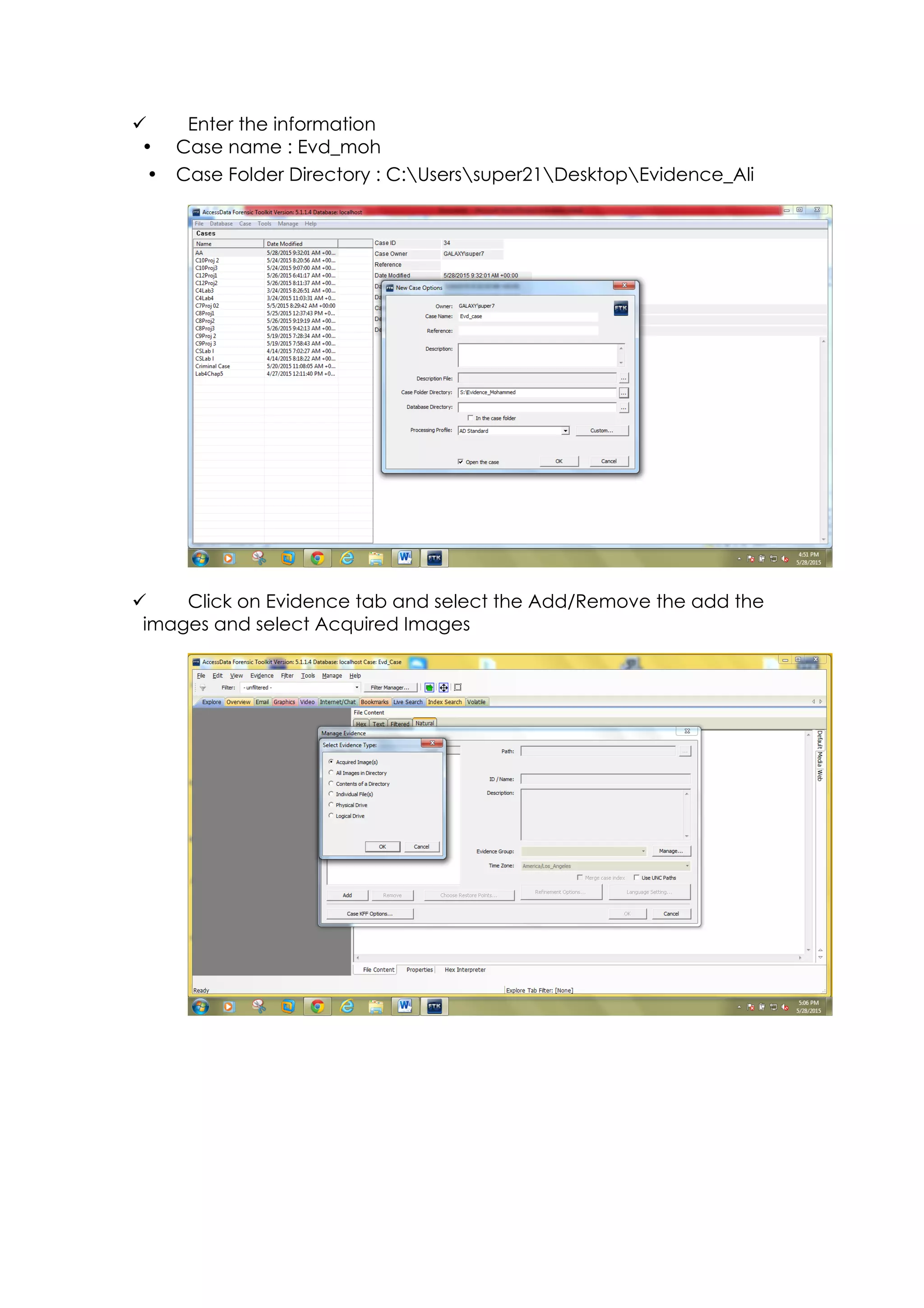
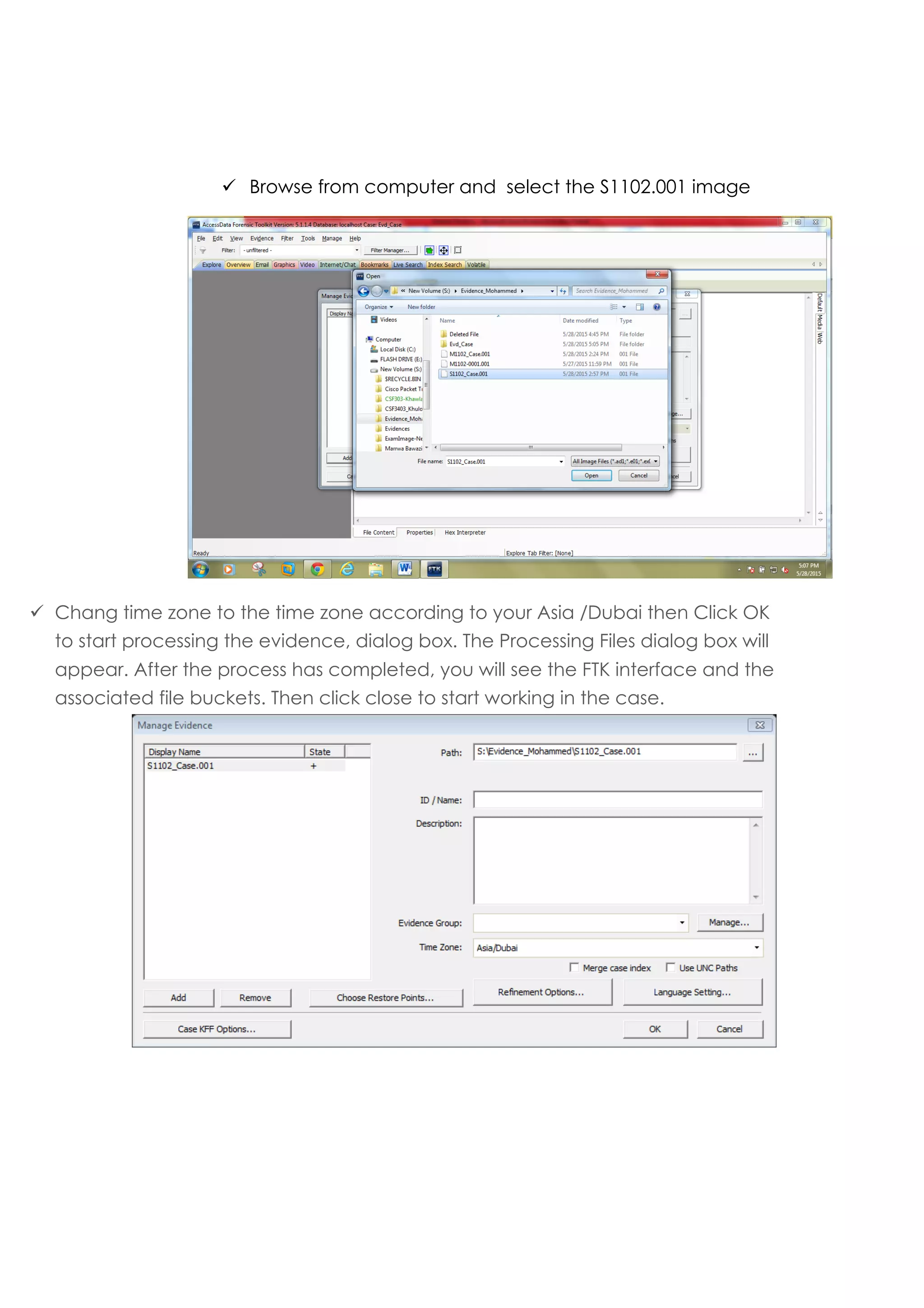
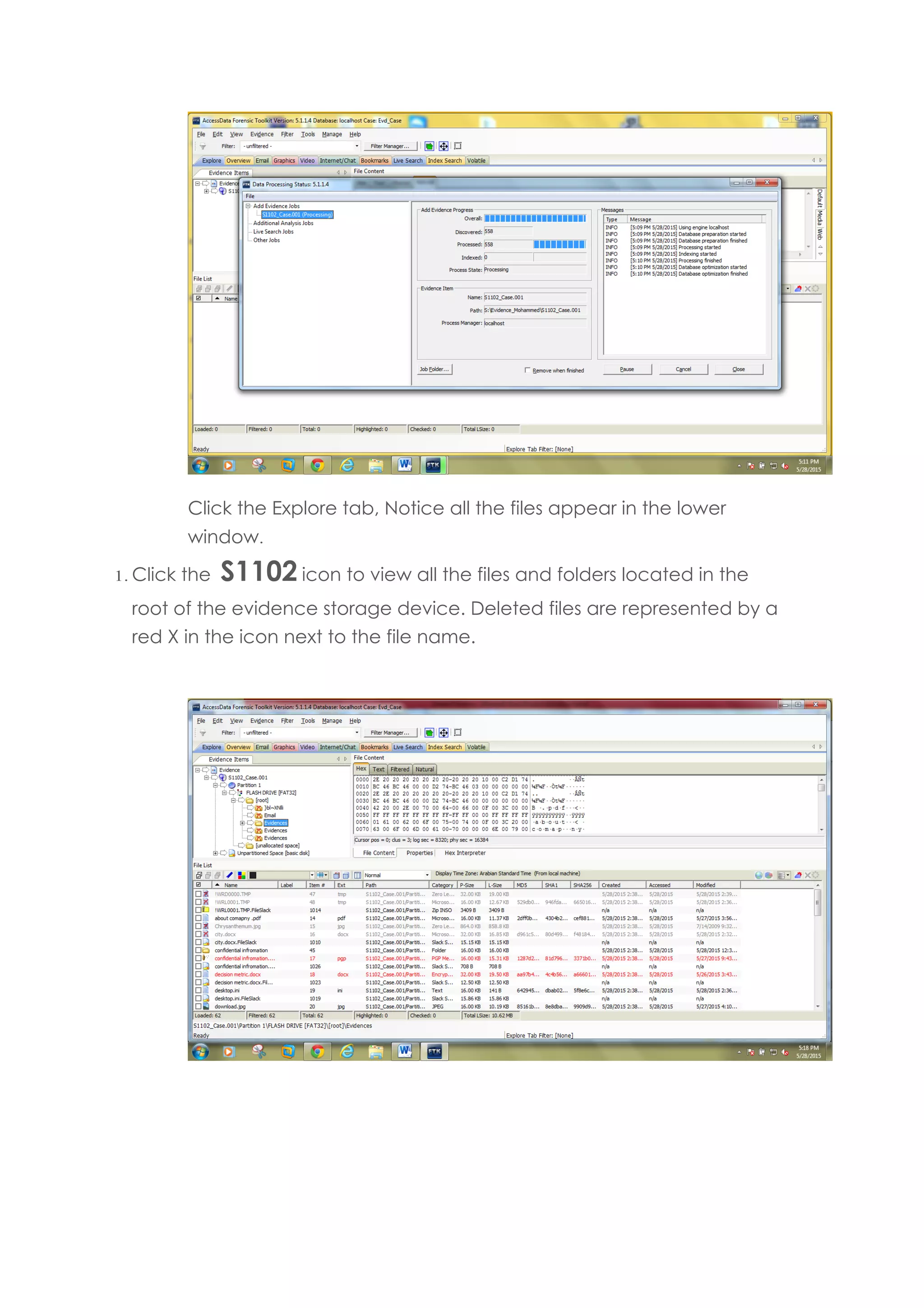
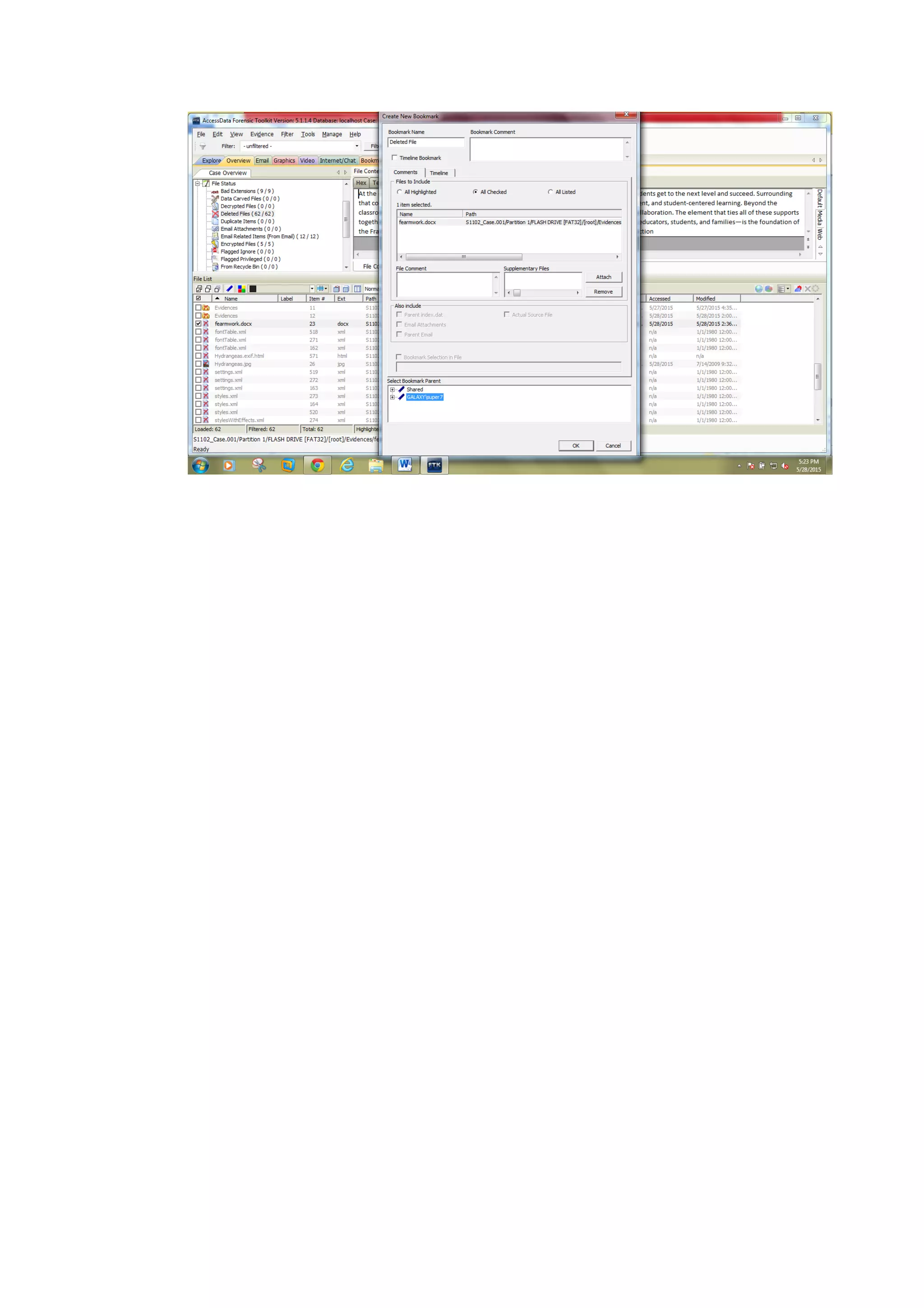
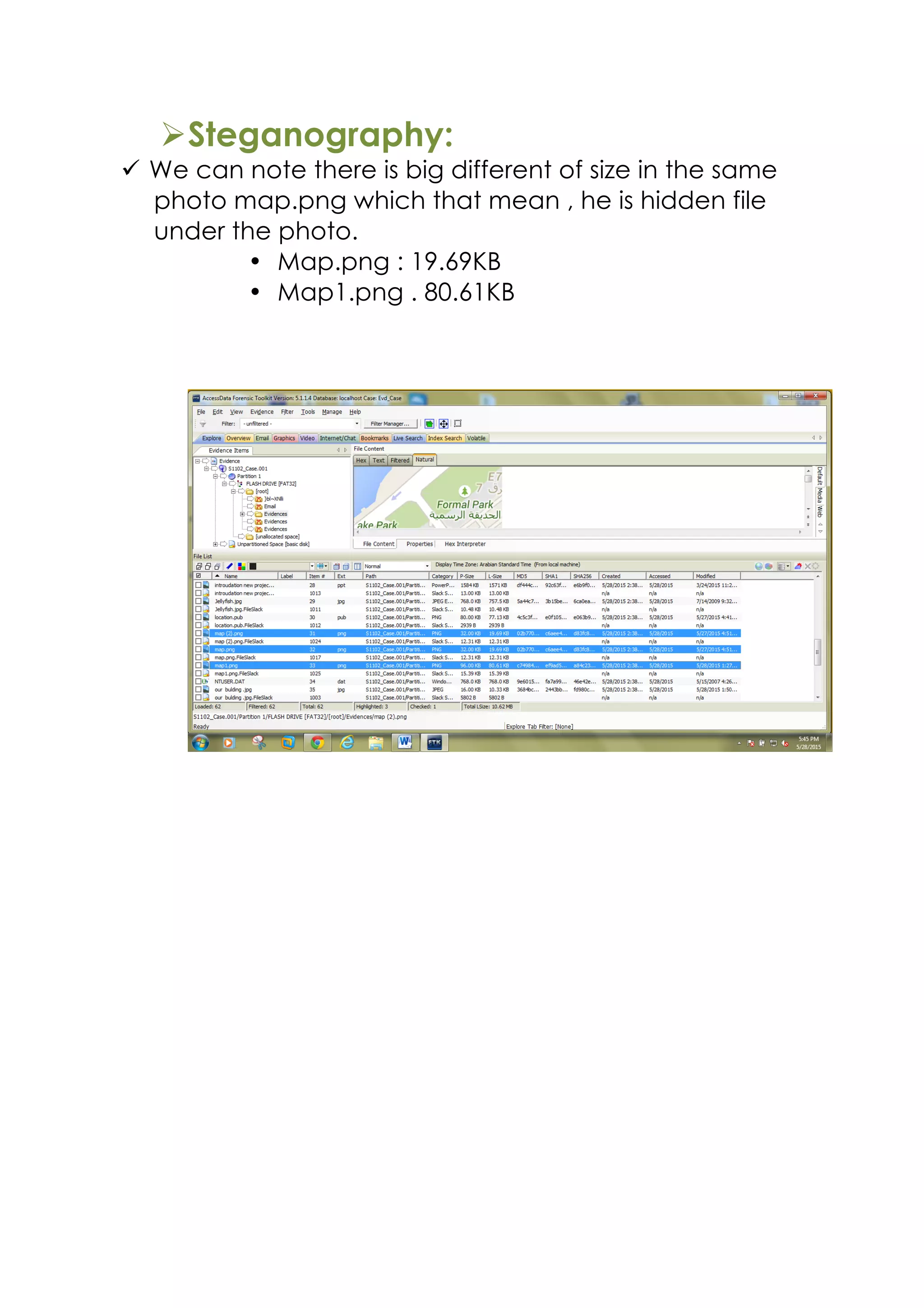
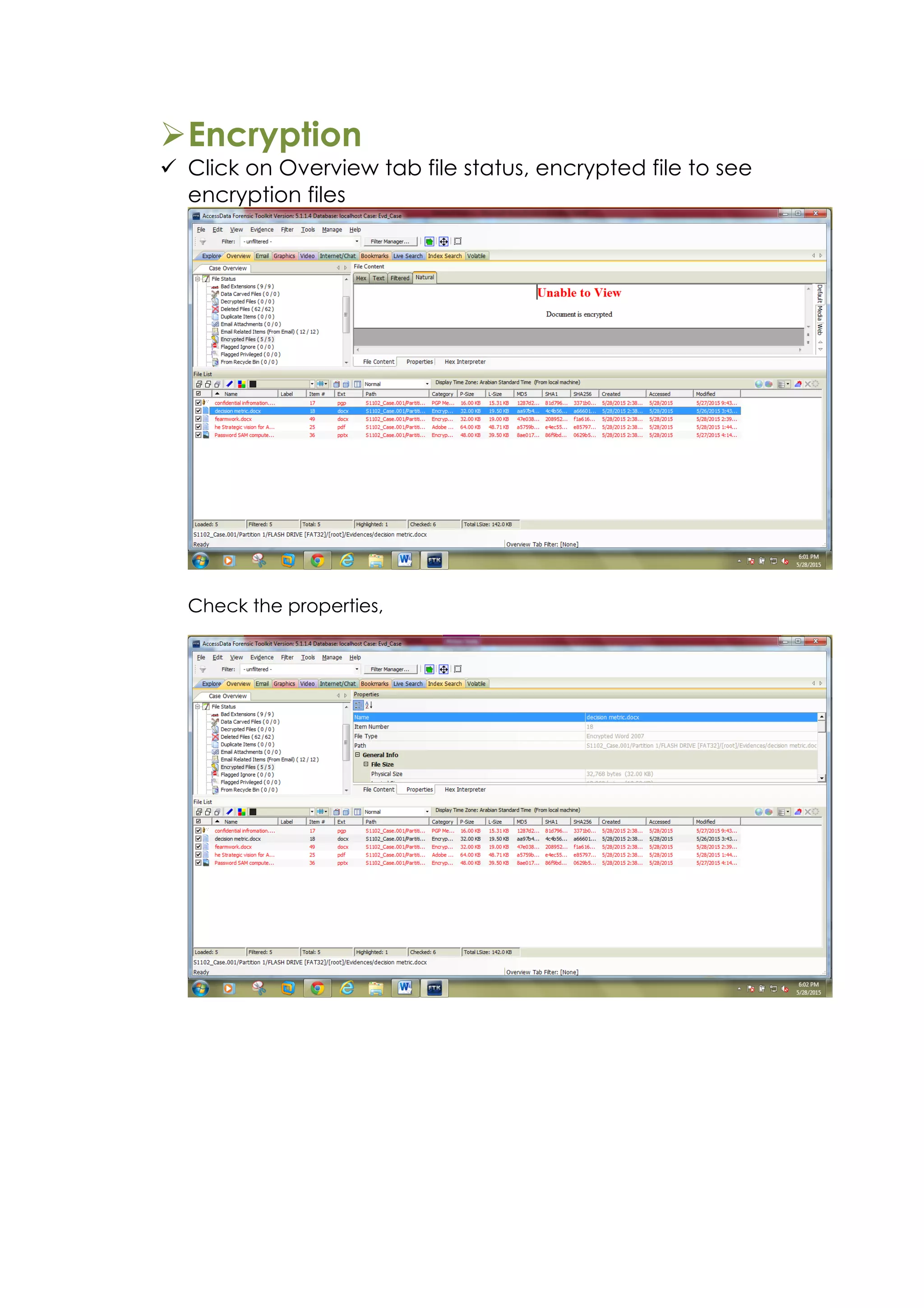
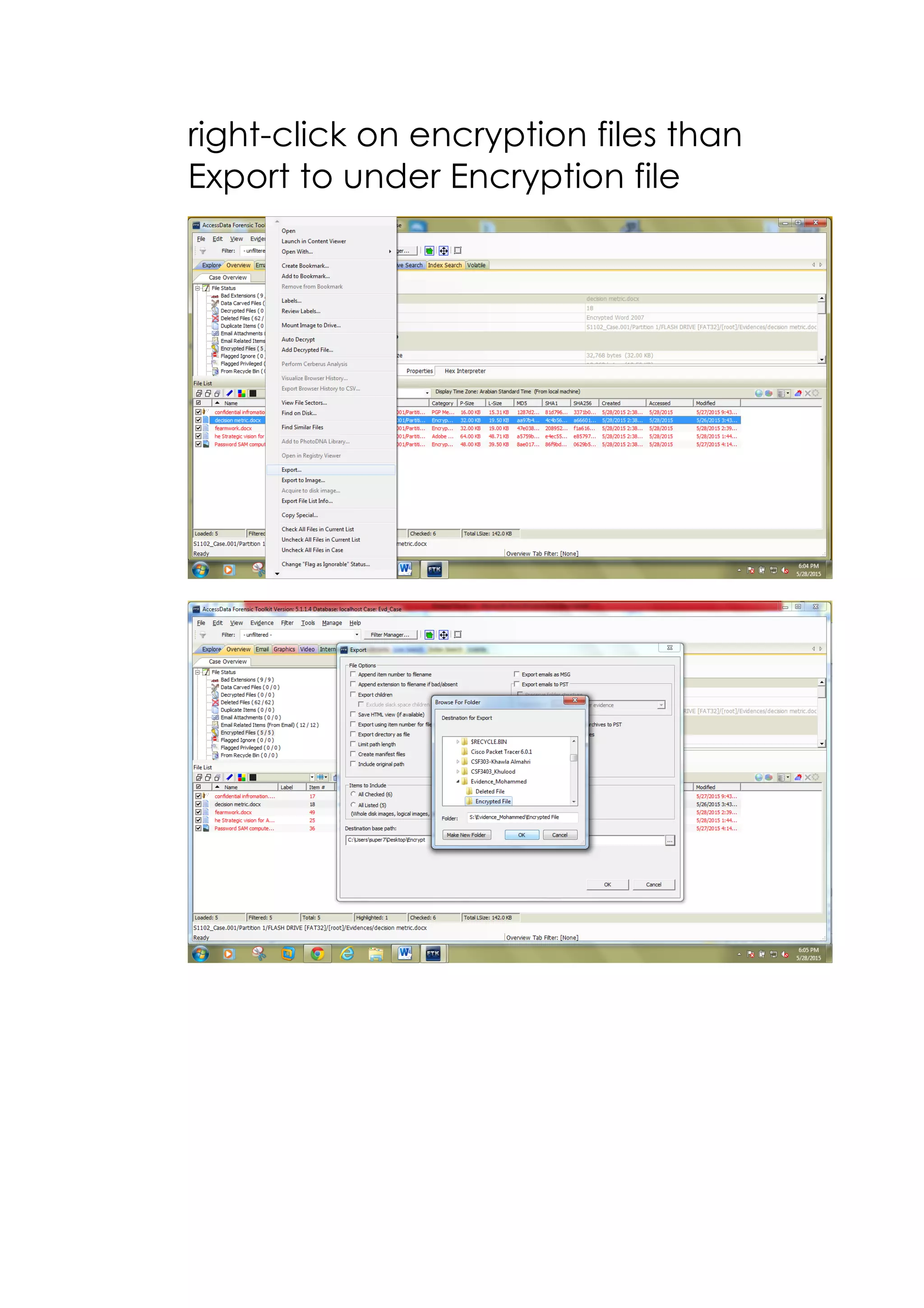
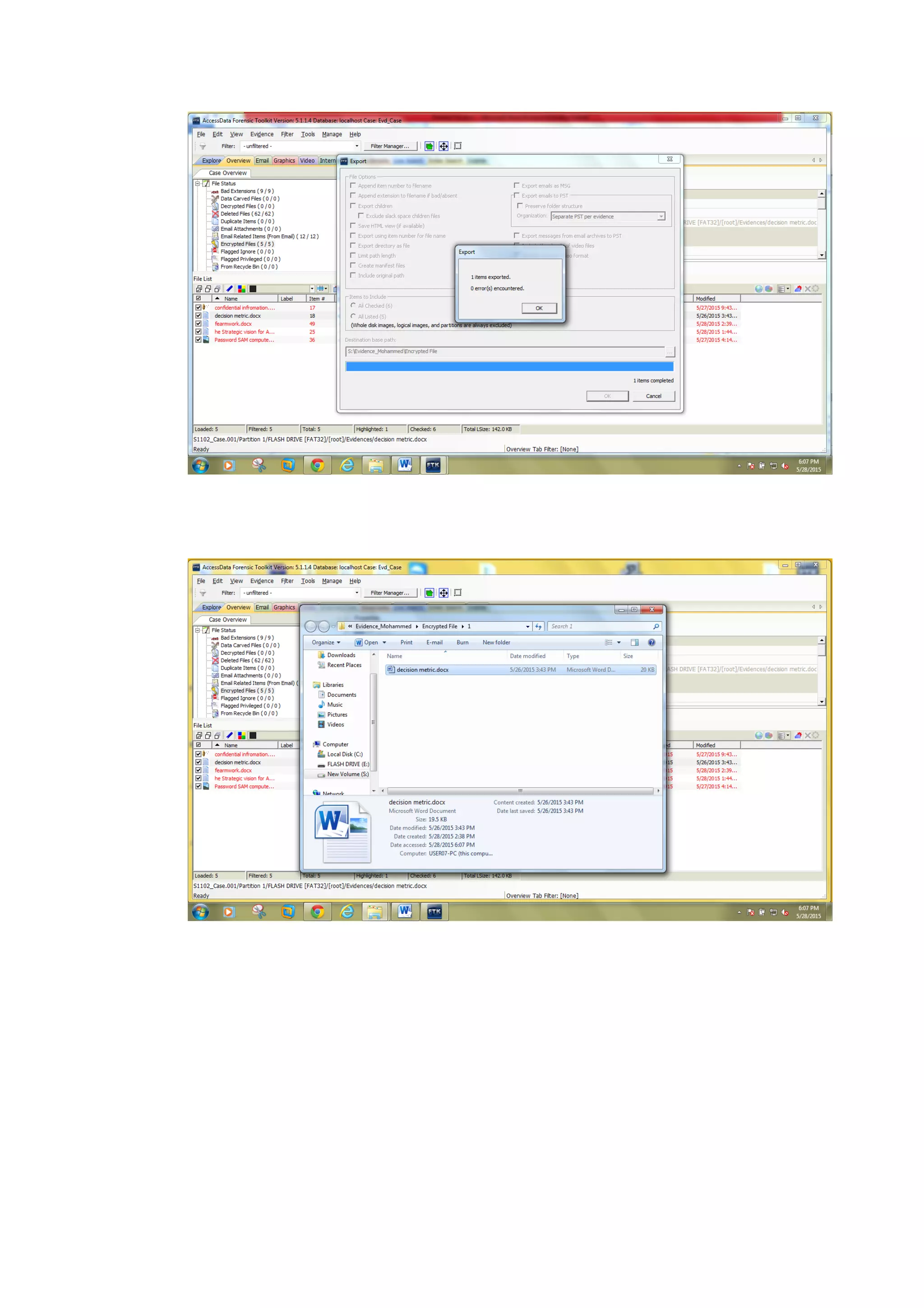
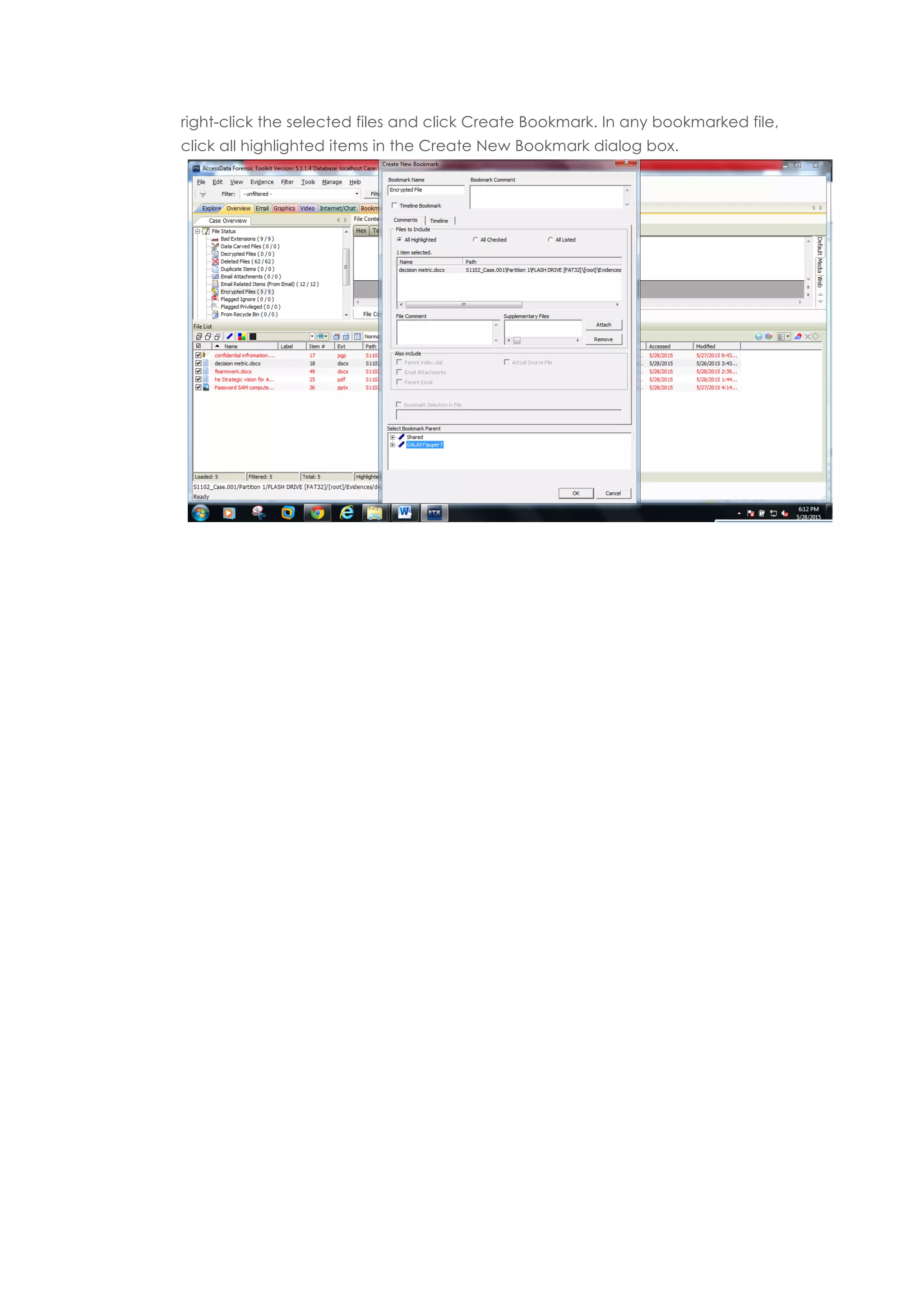
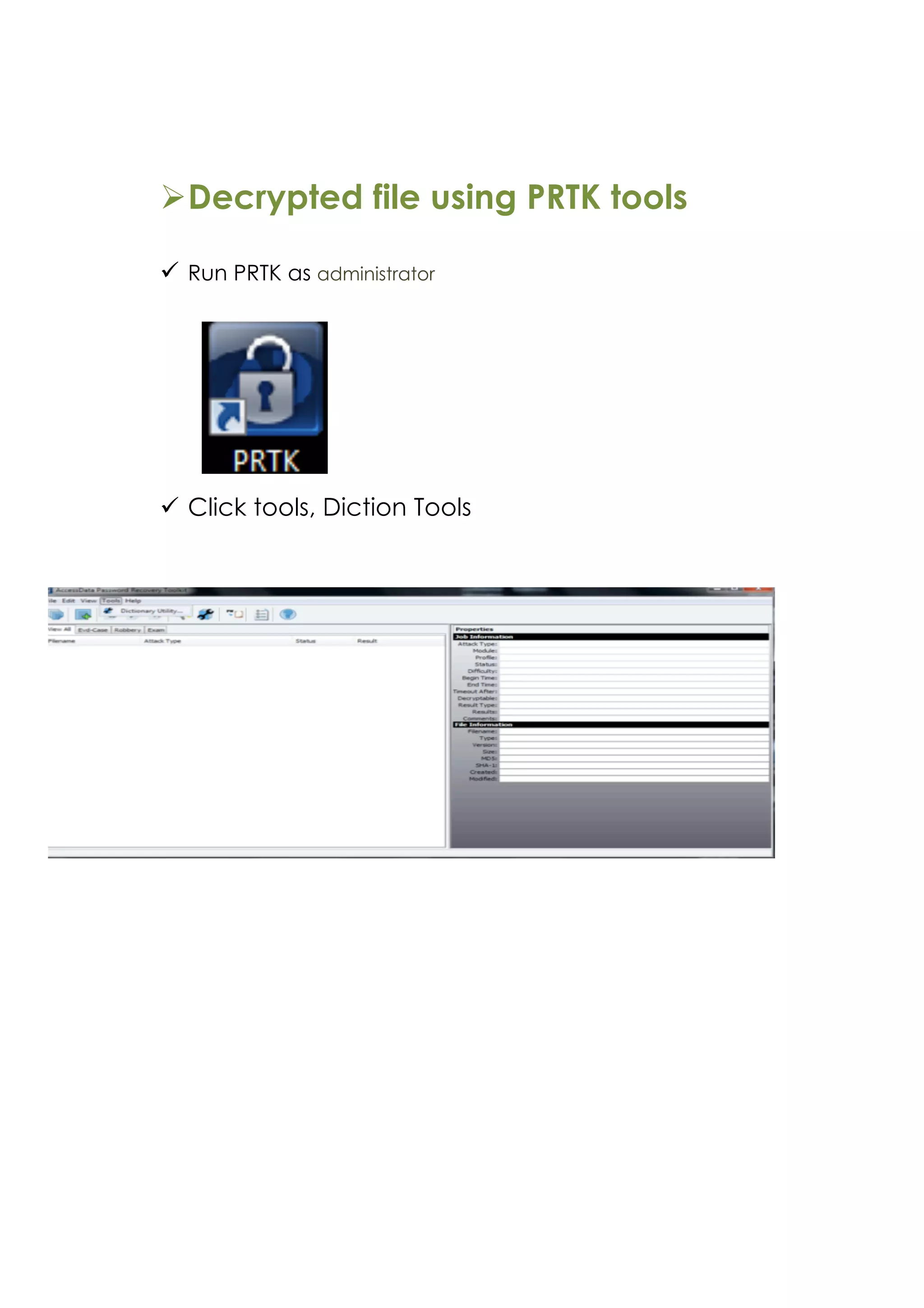
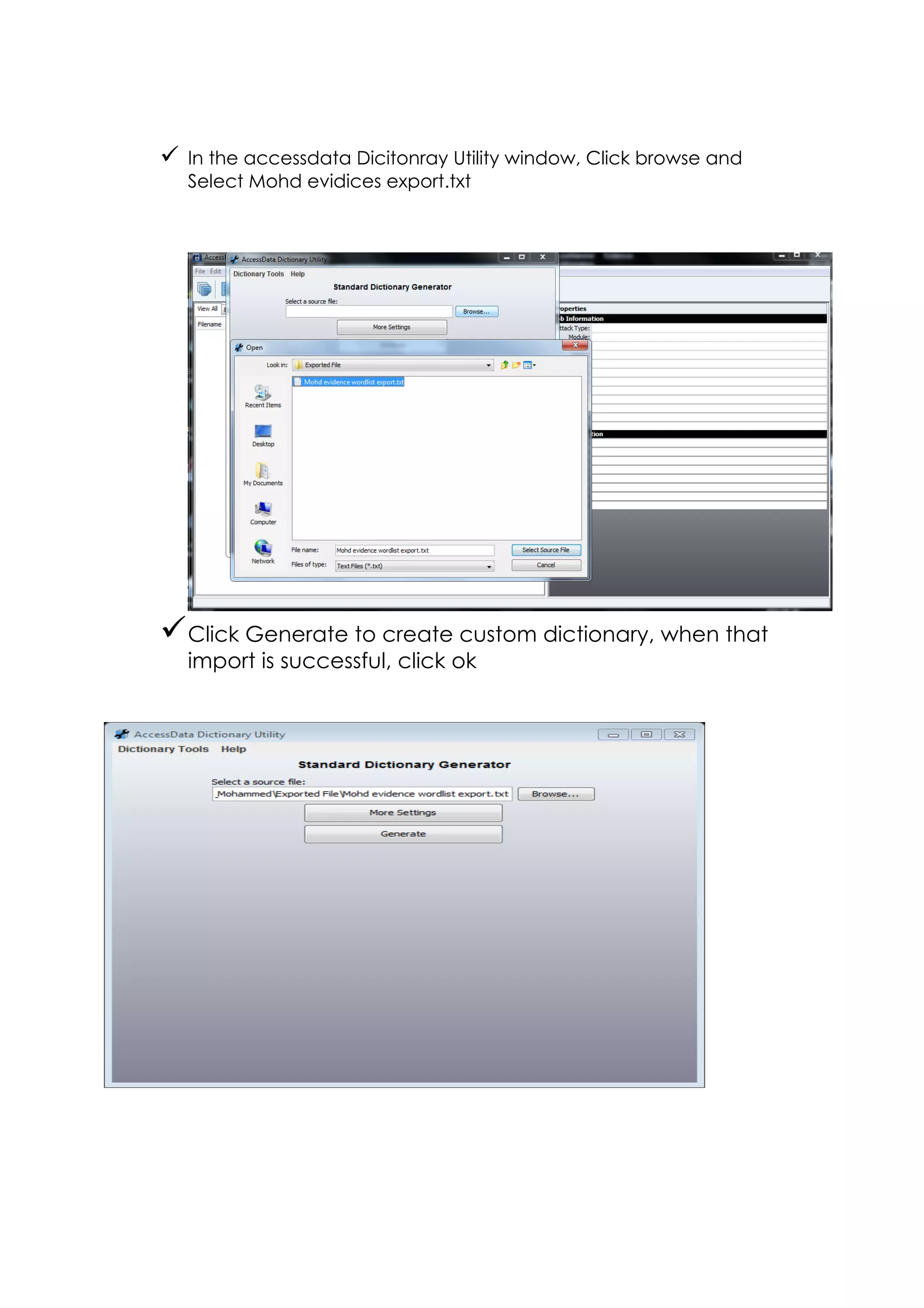
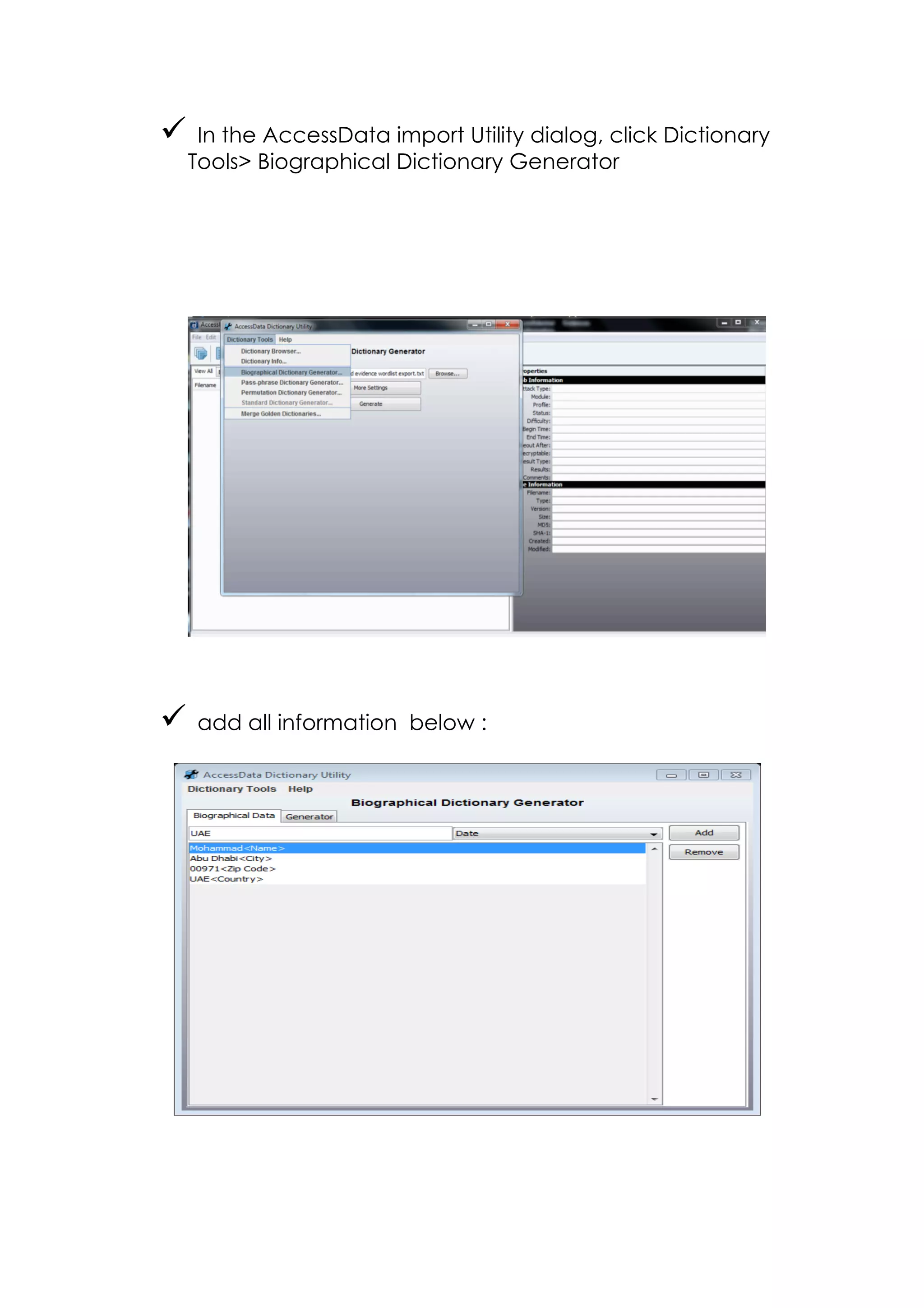
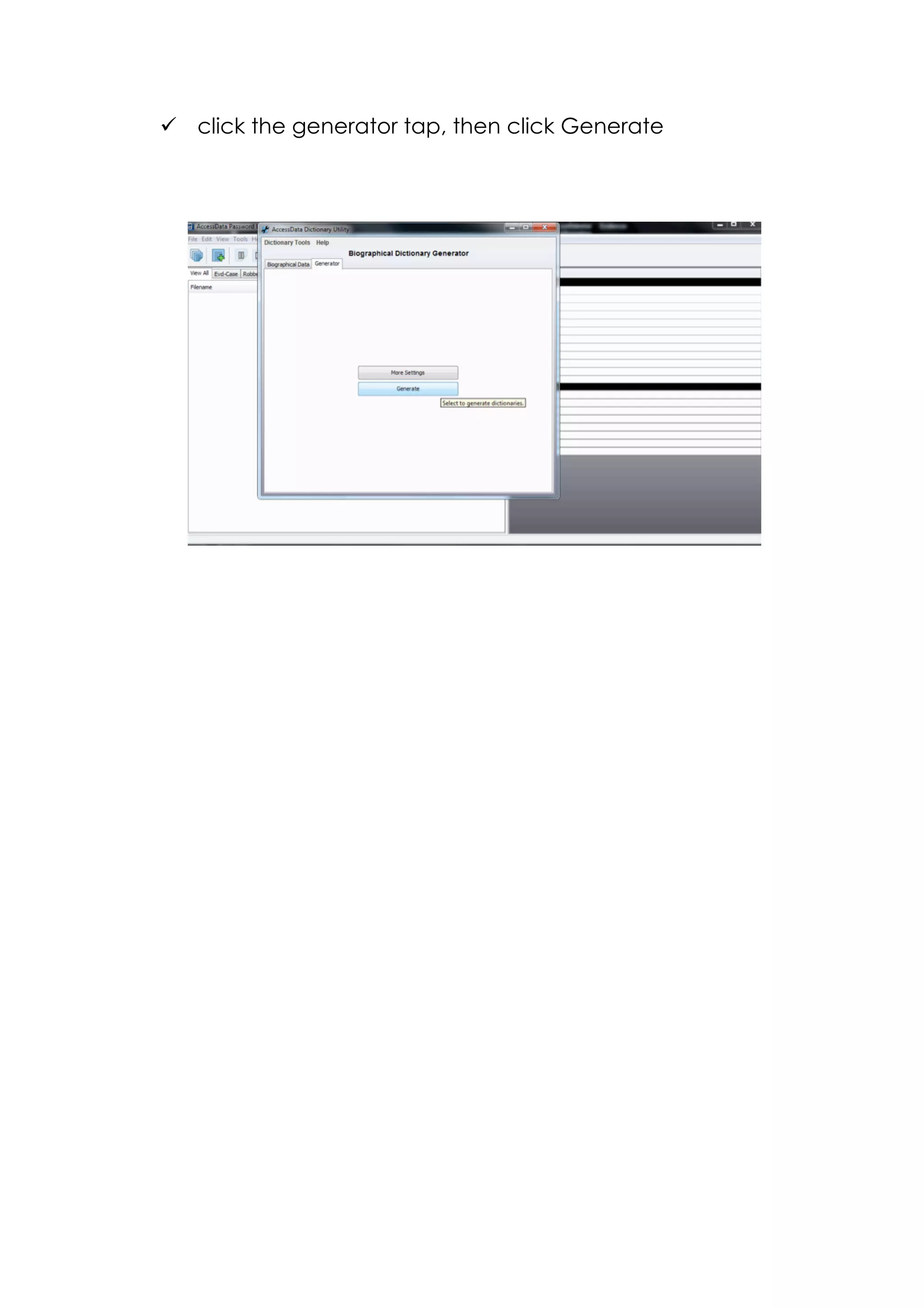
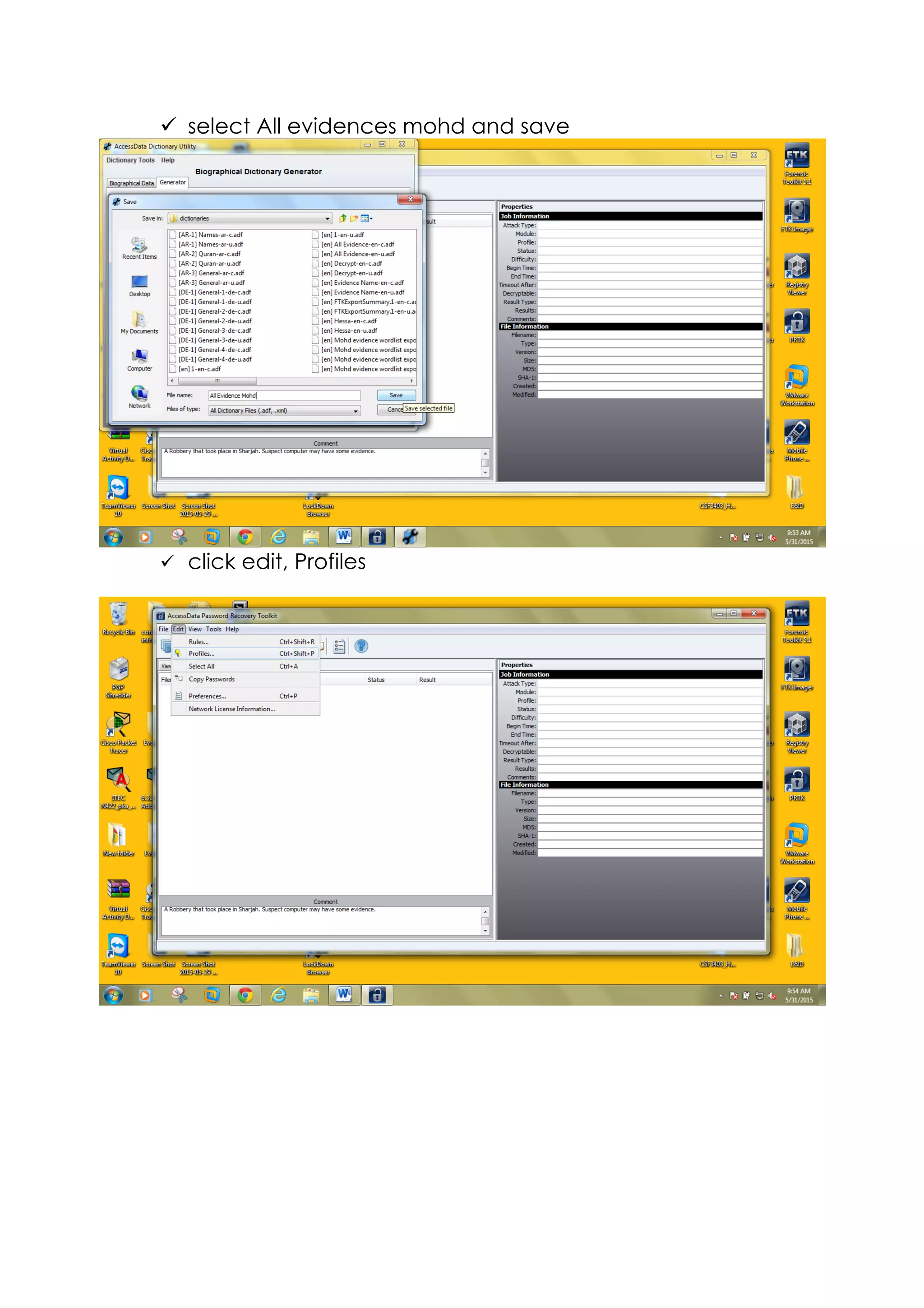
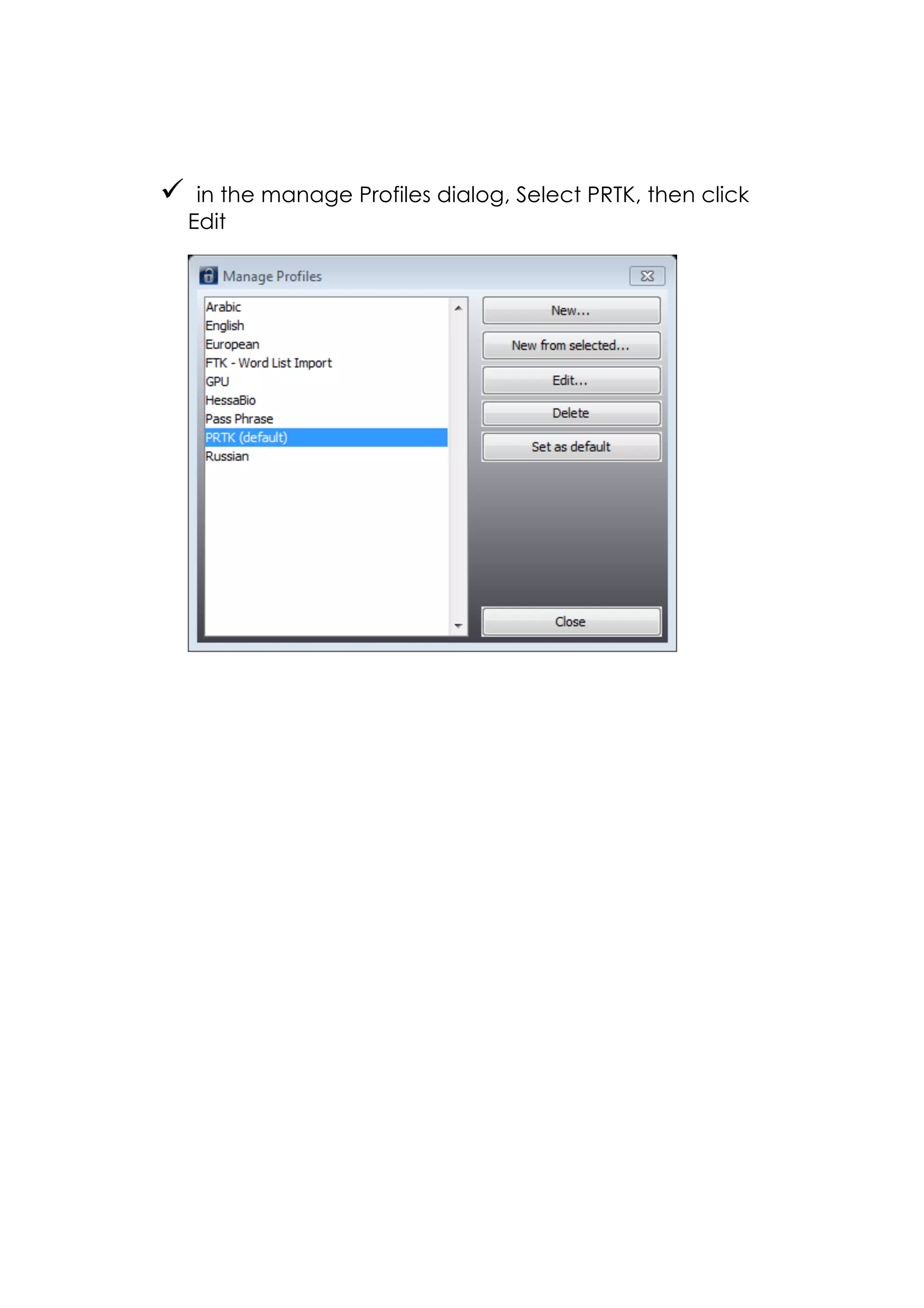
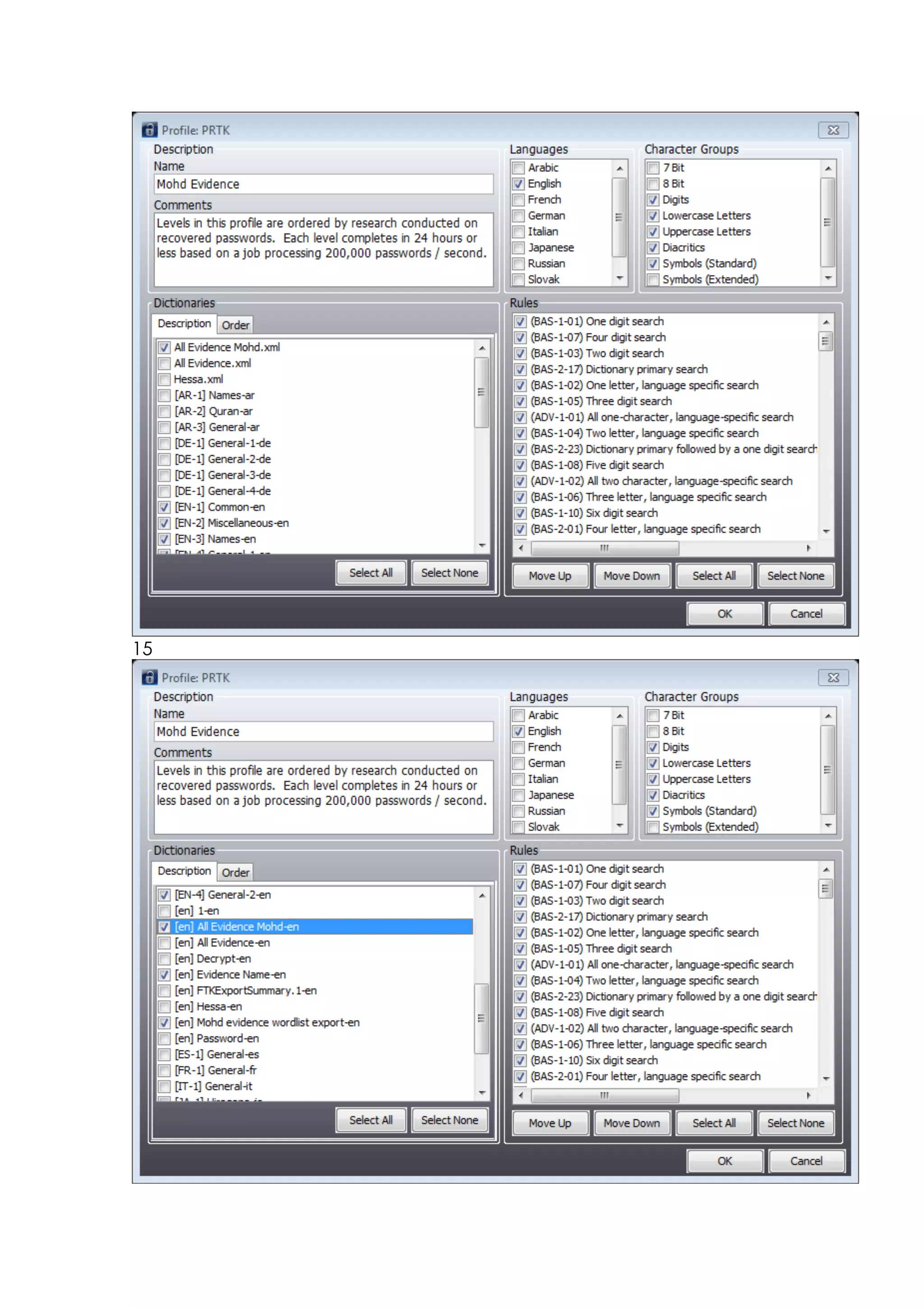
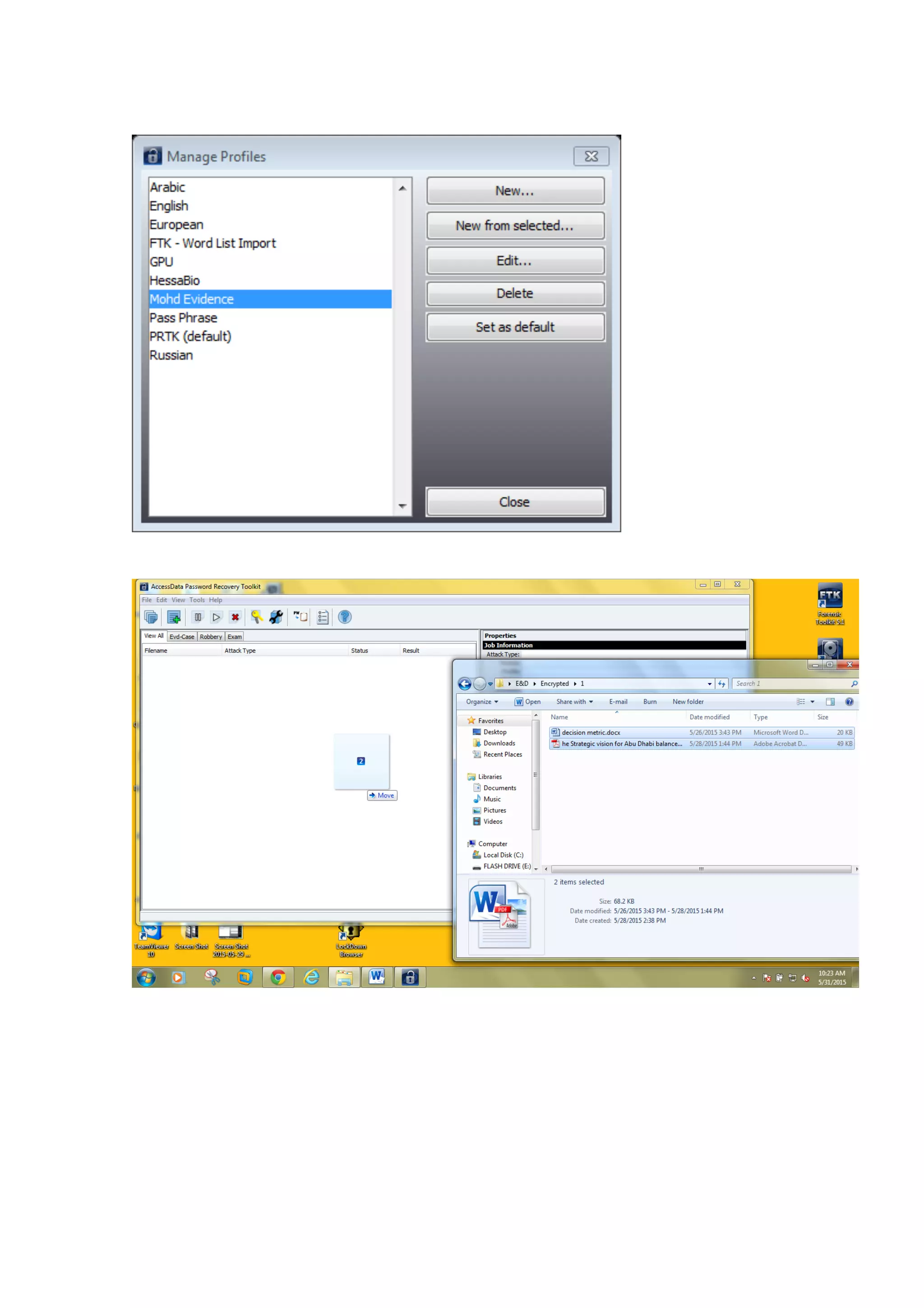
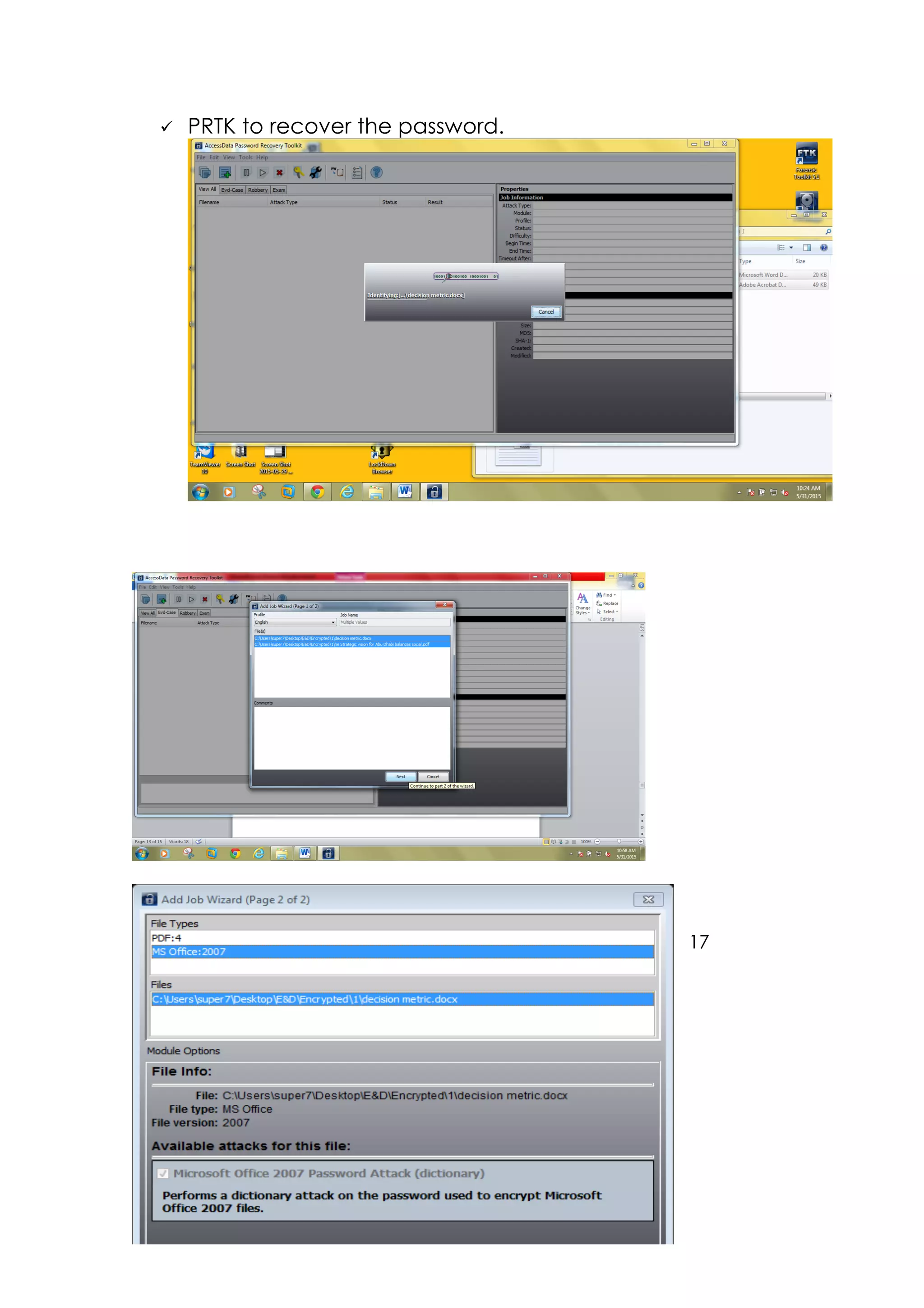
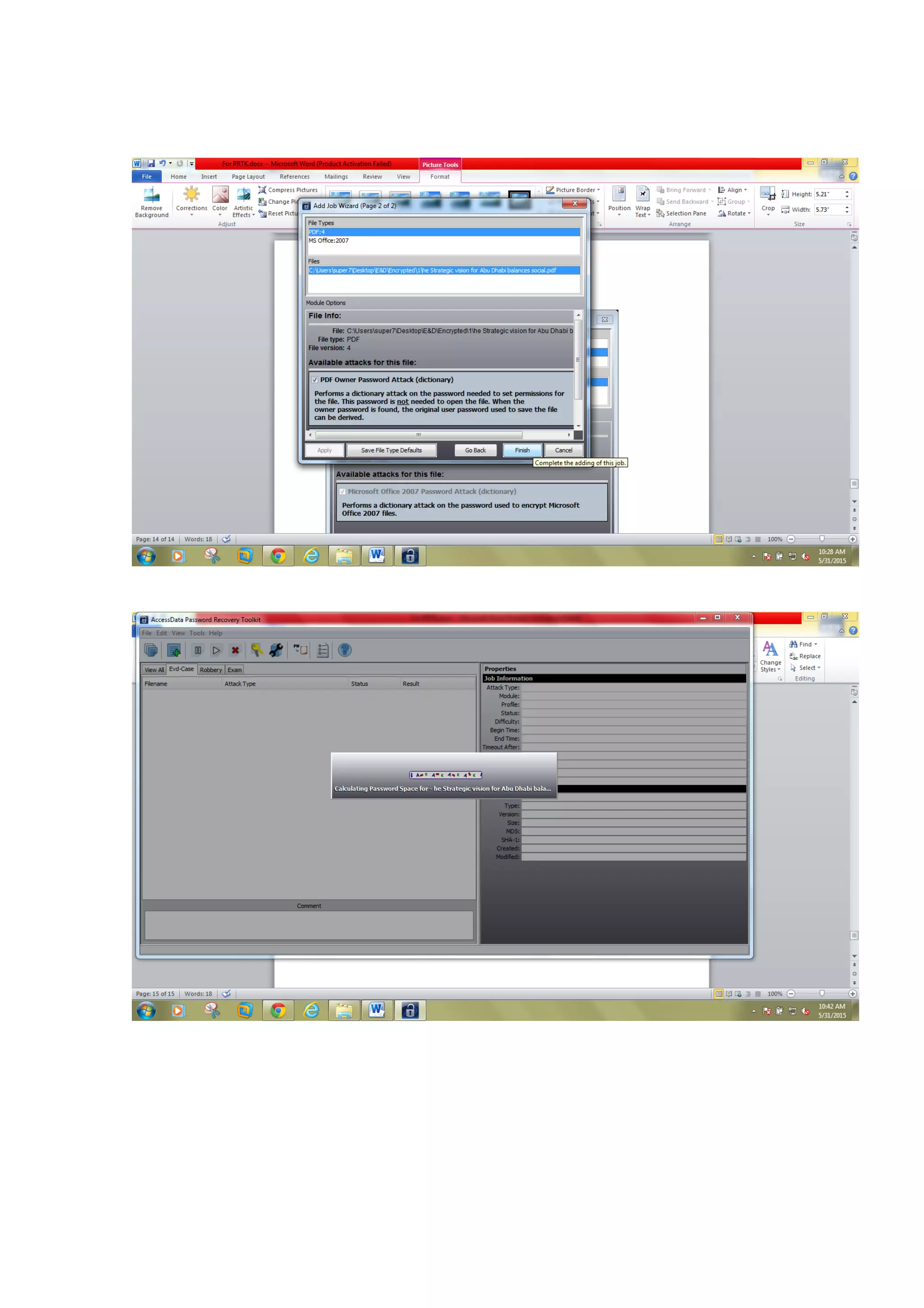
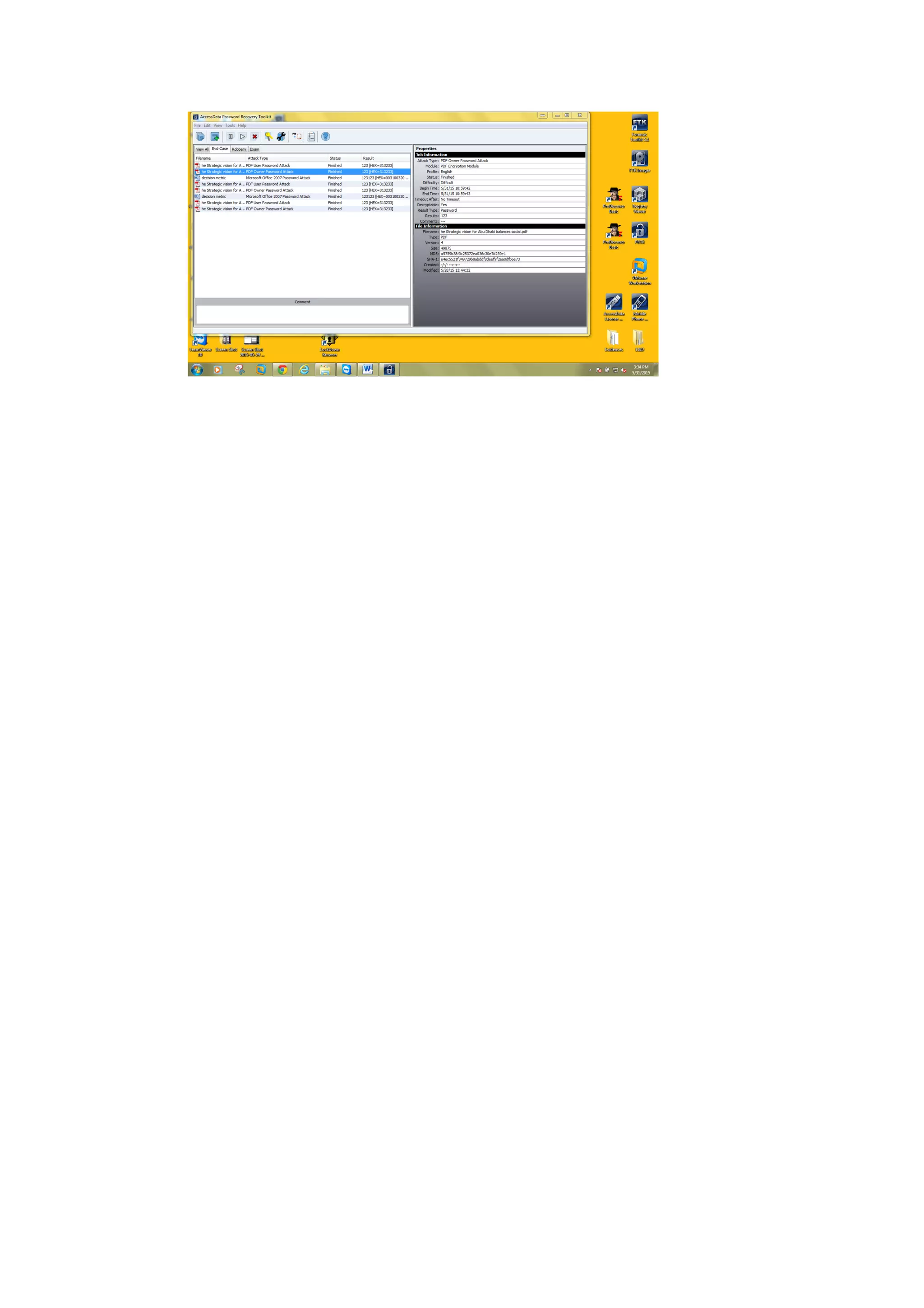
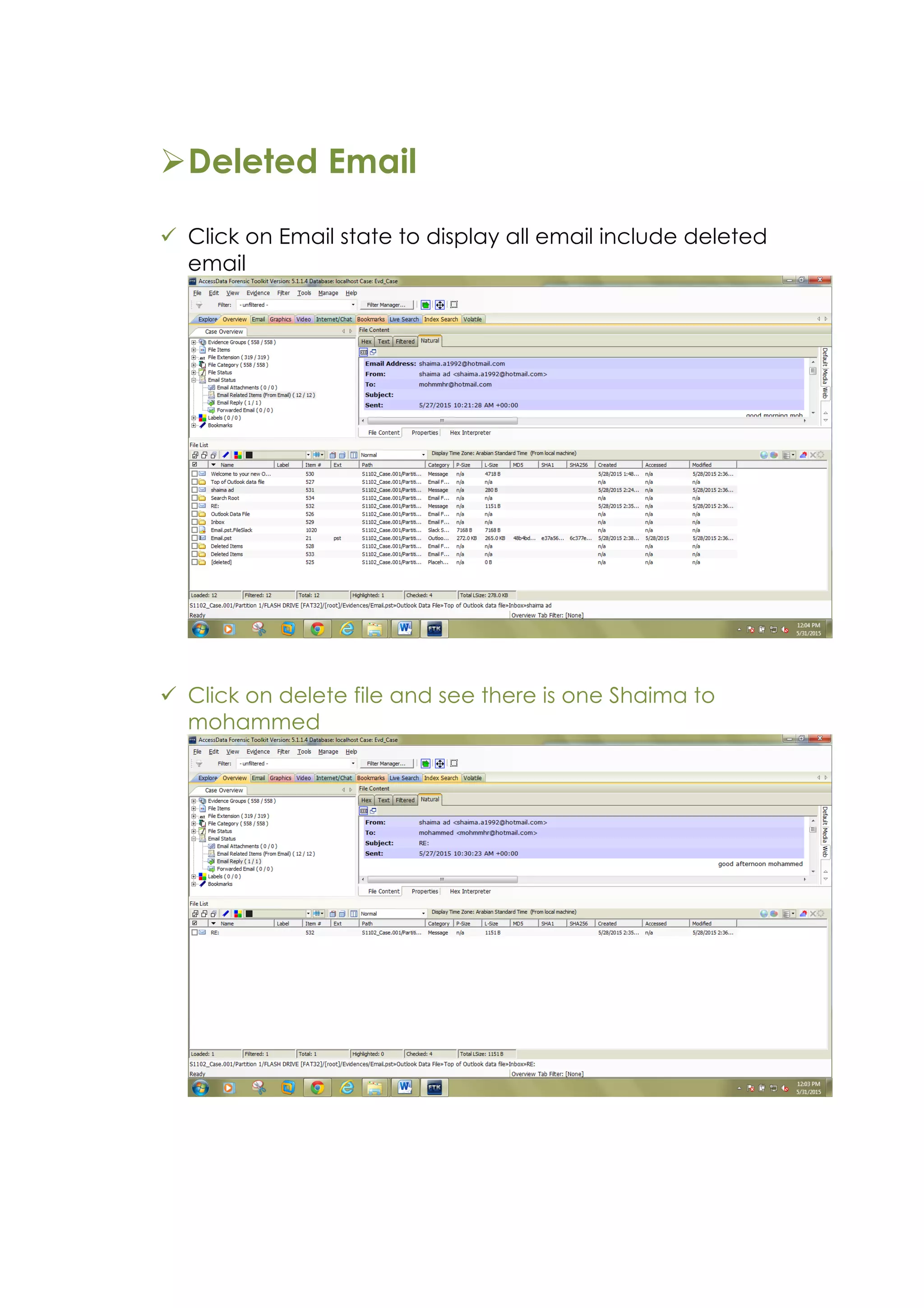
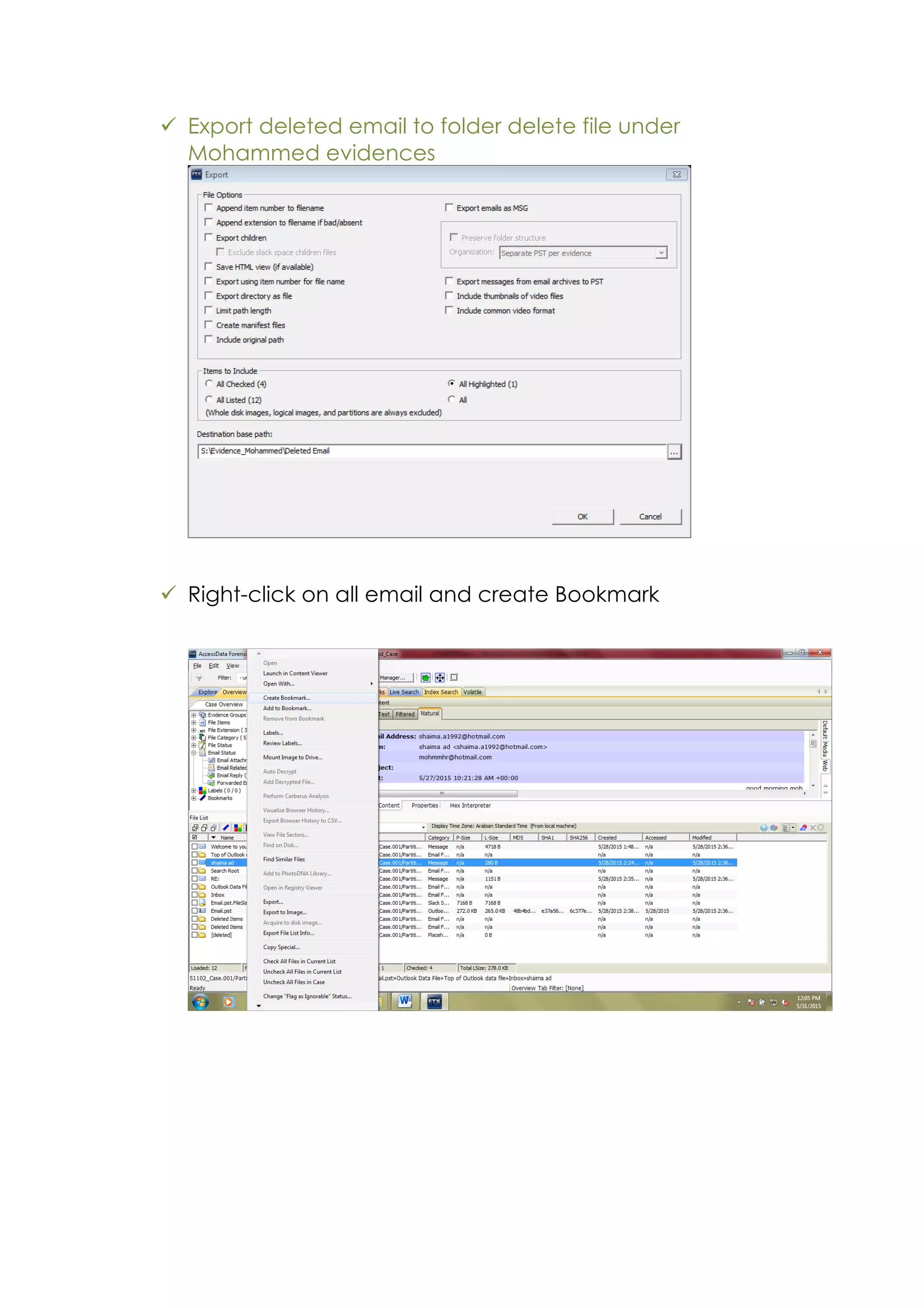
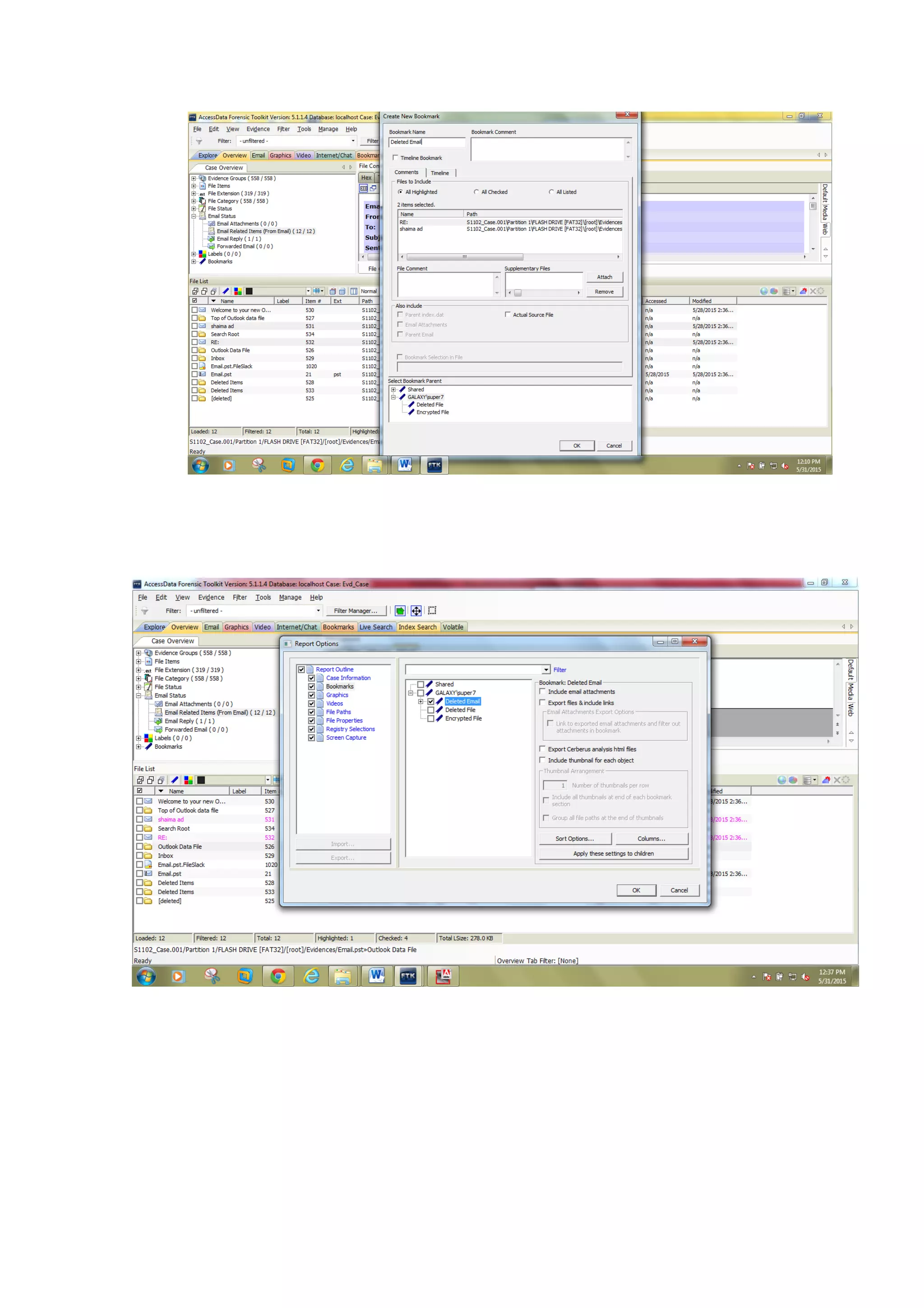
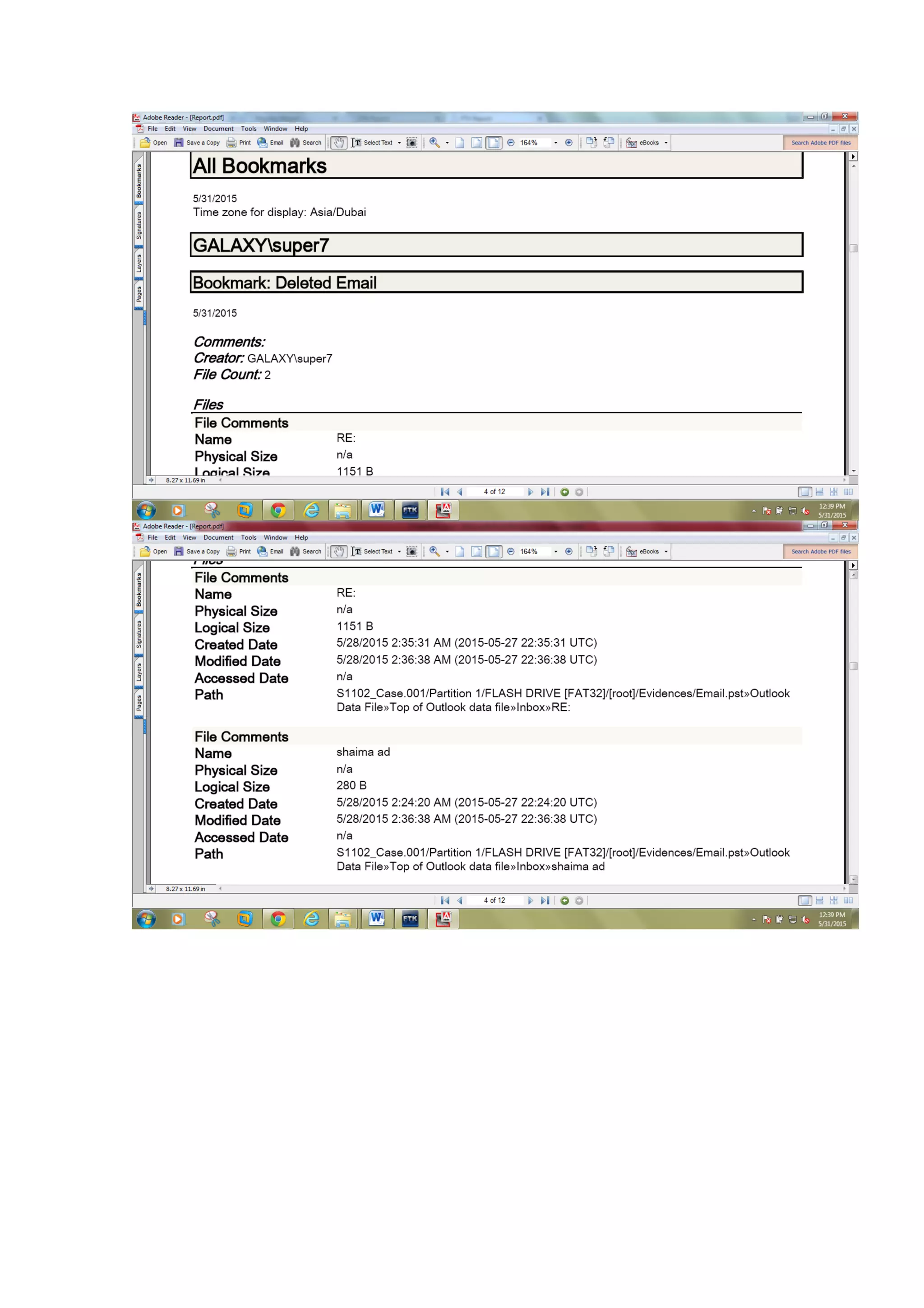
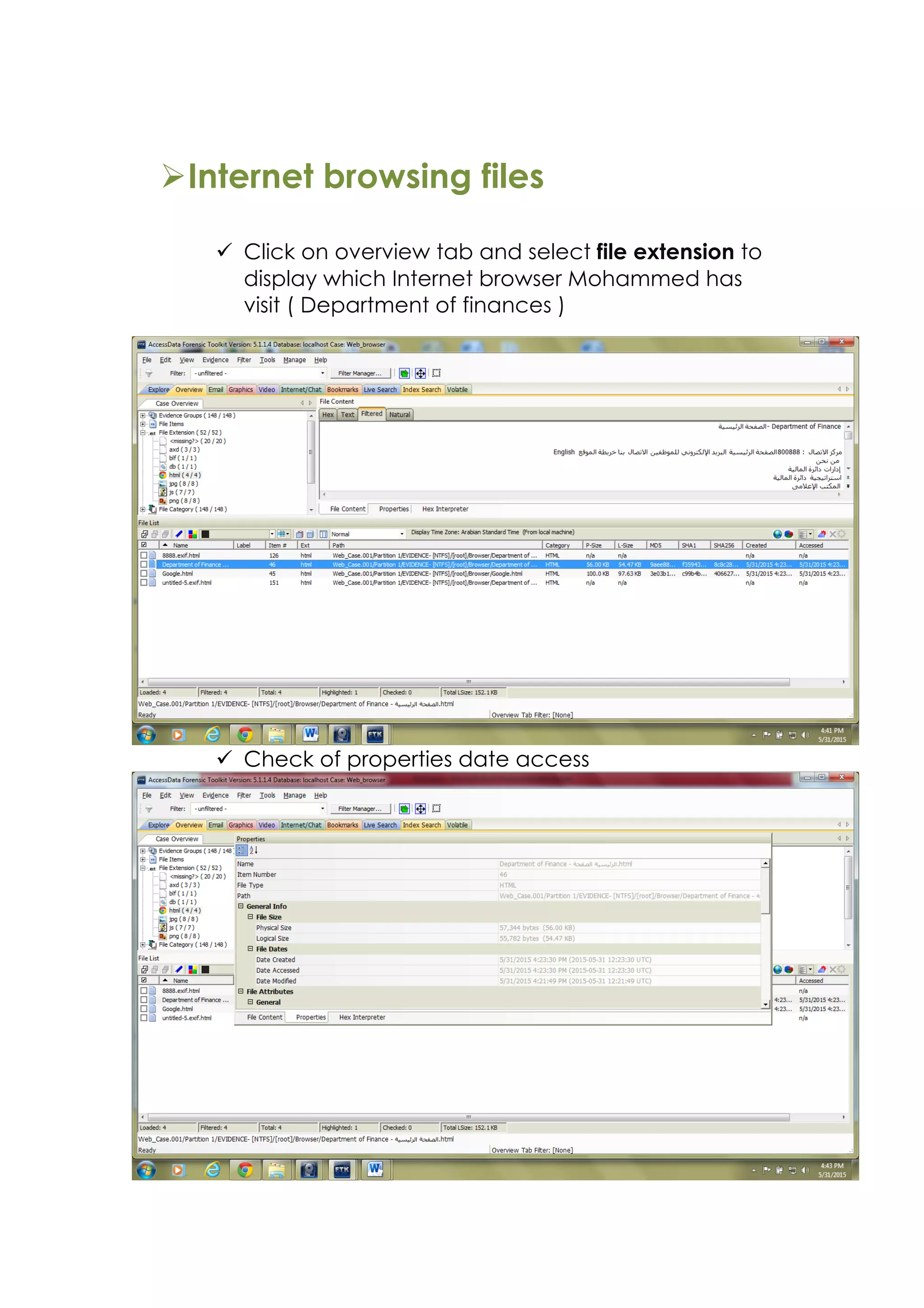
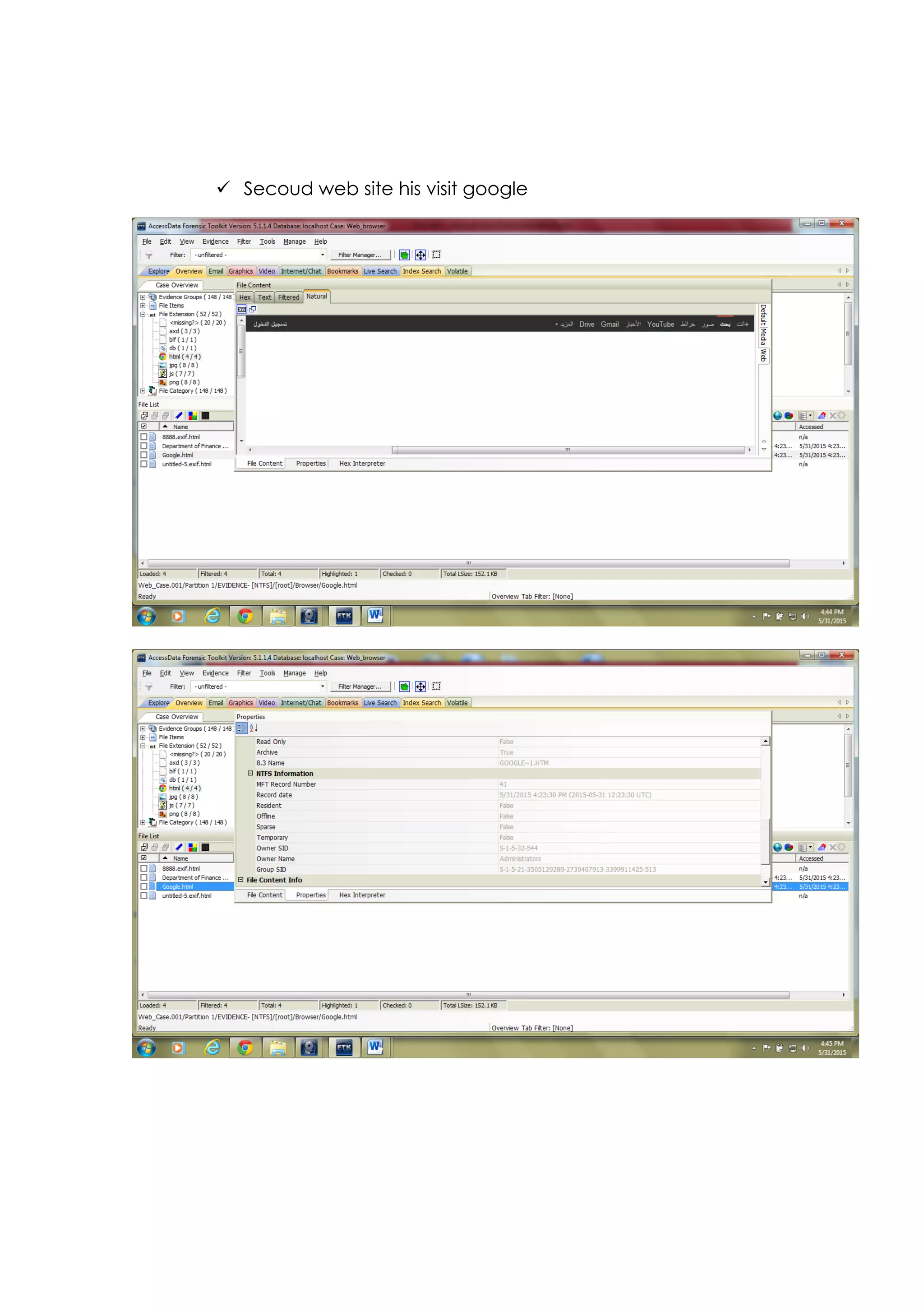
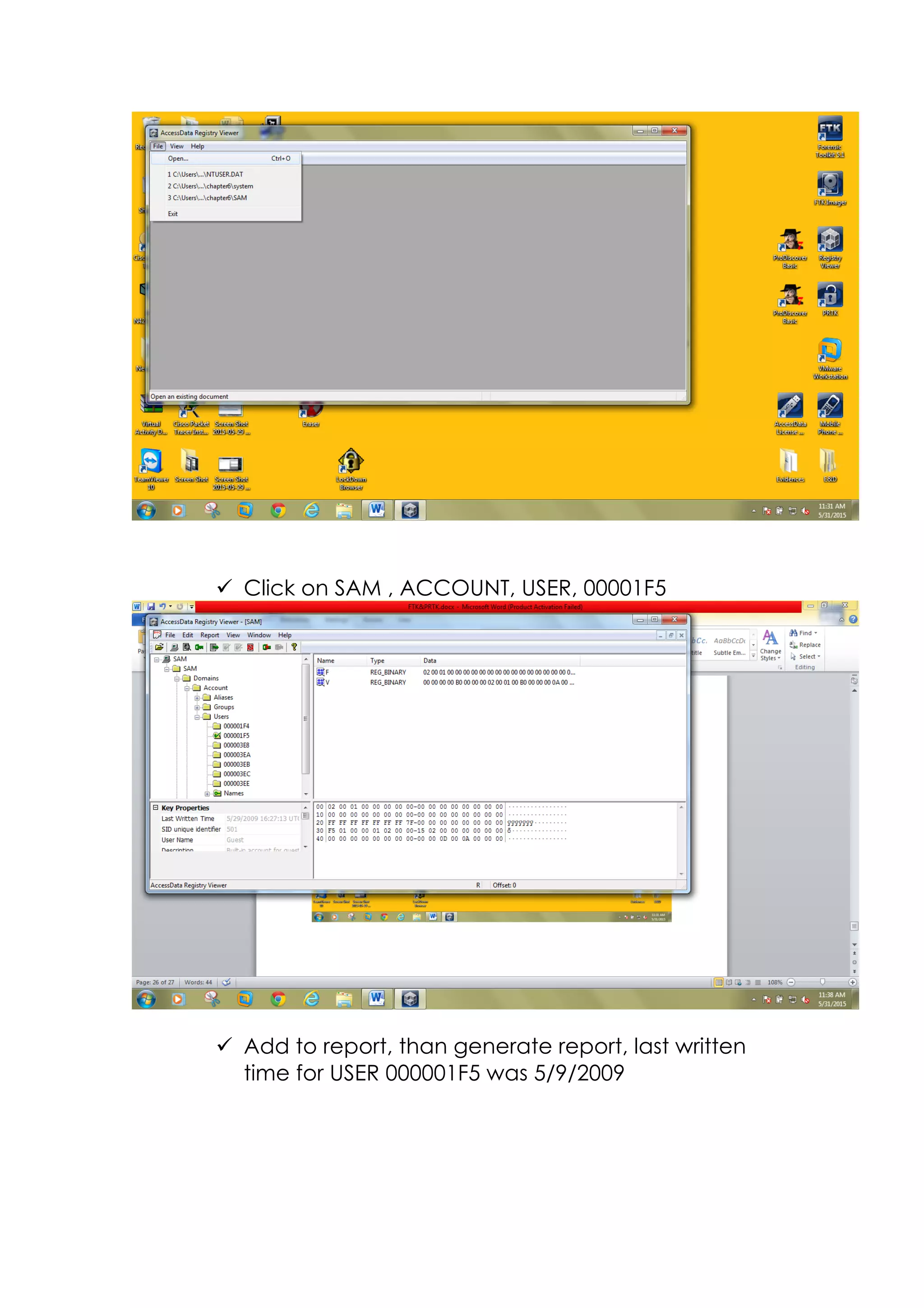
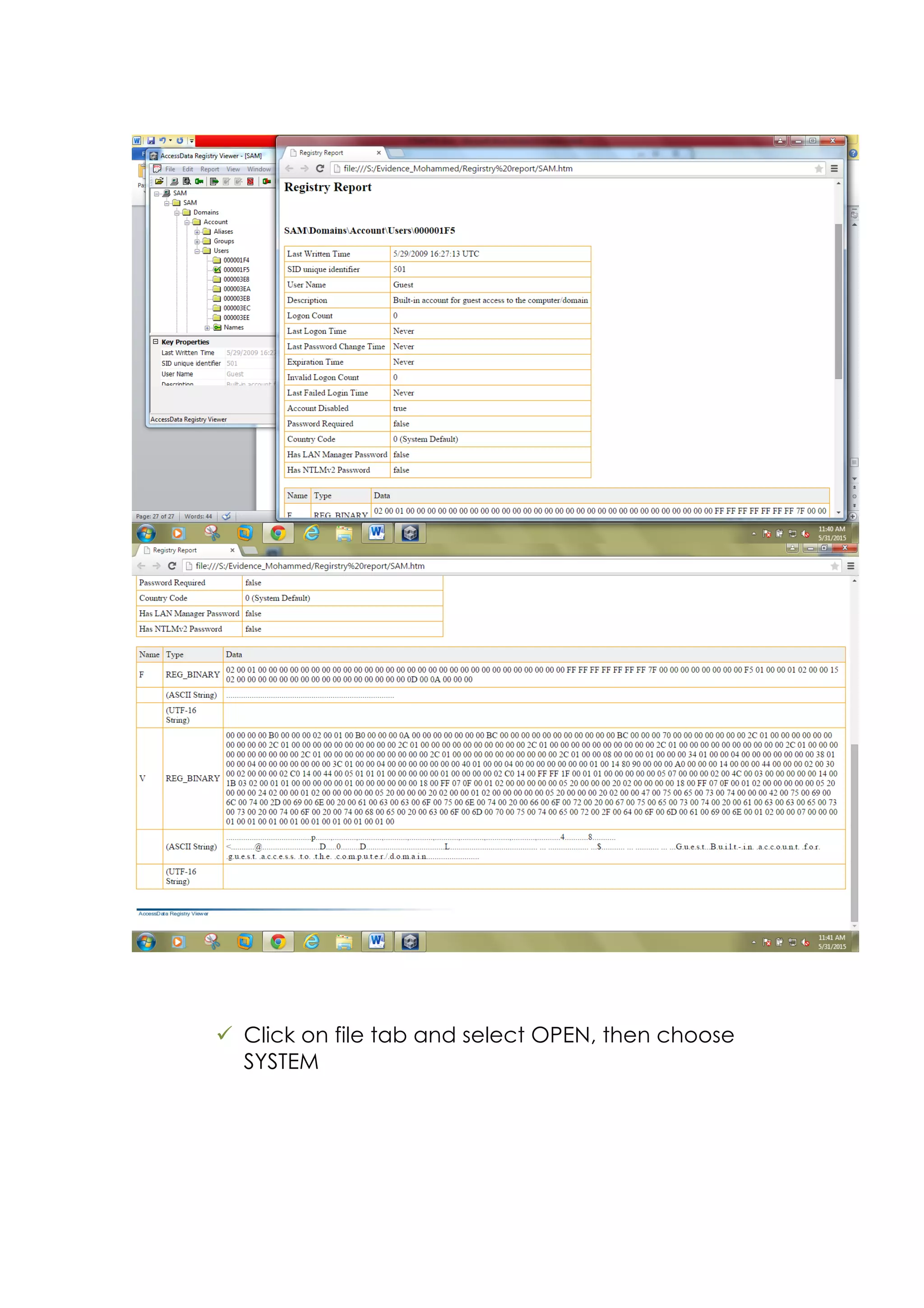
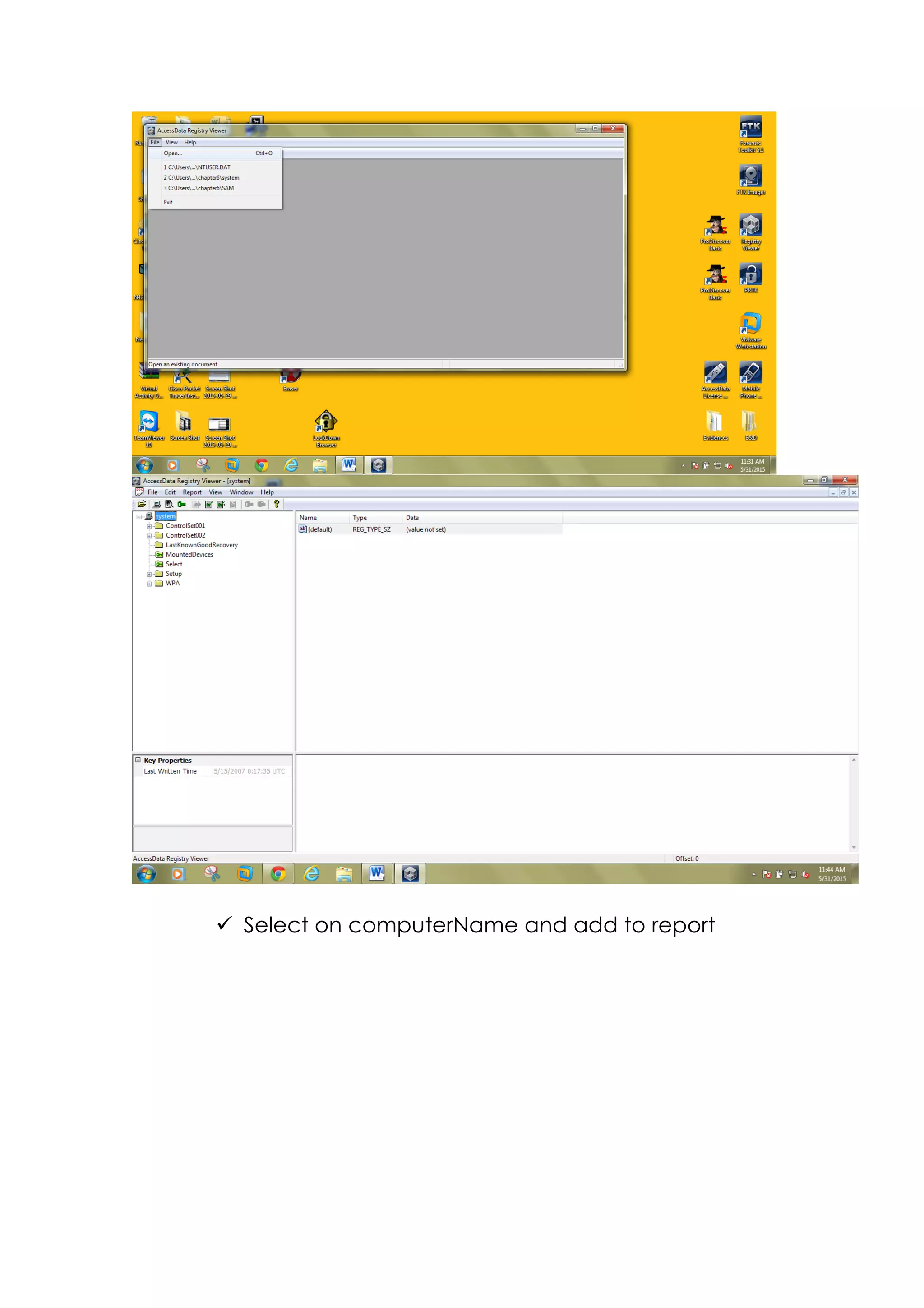
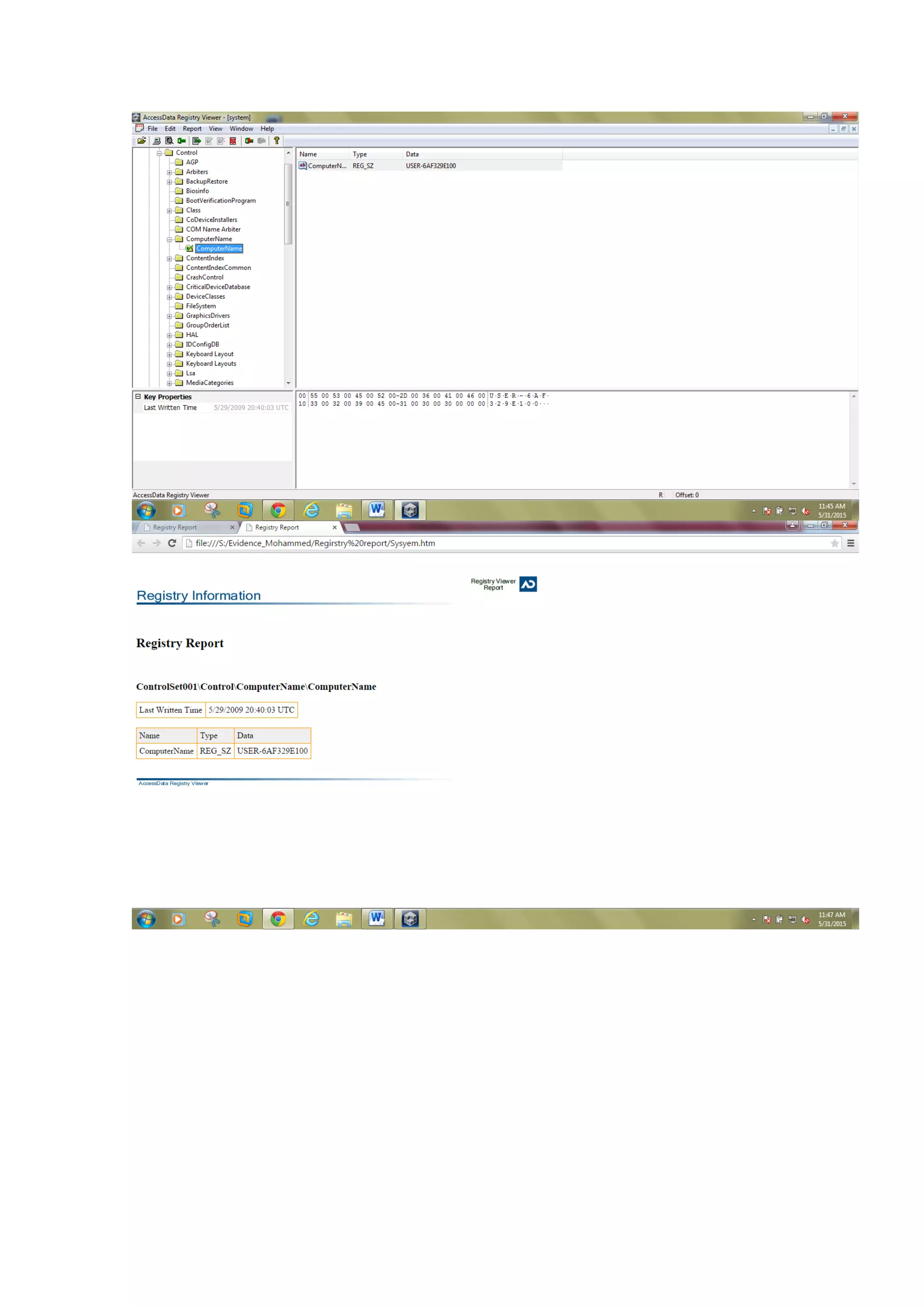
This document outlines a team project on computer forensics and investigations submitted by three students. It begins with an introduction on the importance of computer forensics in investigating civil and criminal cases. It then presents a problem statement describing a situation where confidential company information was leaked to a competitor, possibly via USB flash drive or email. The company wants to investigate by collecting evidence from the suspected employee's computer using forensics tools. The rest of the document includes sections on literature review, methodology, results and analysis of the findings using forensic tools like FTK and AccessData, discussion, and conclusion.