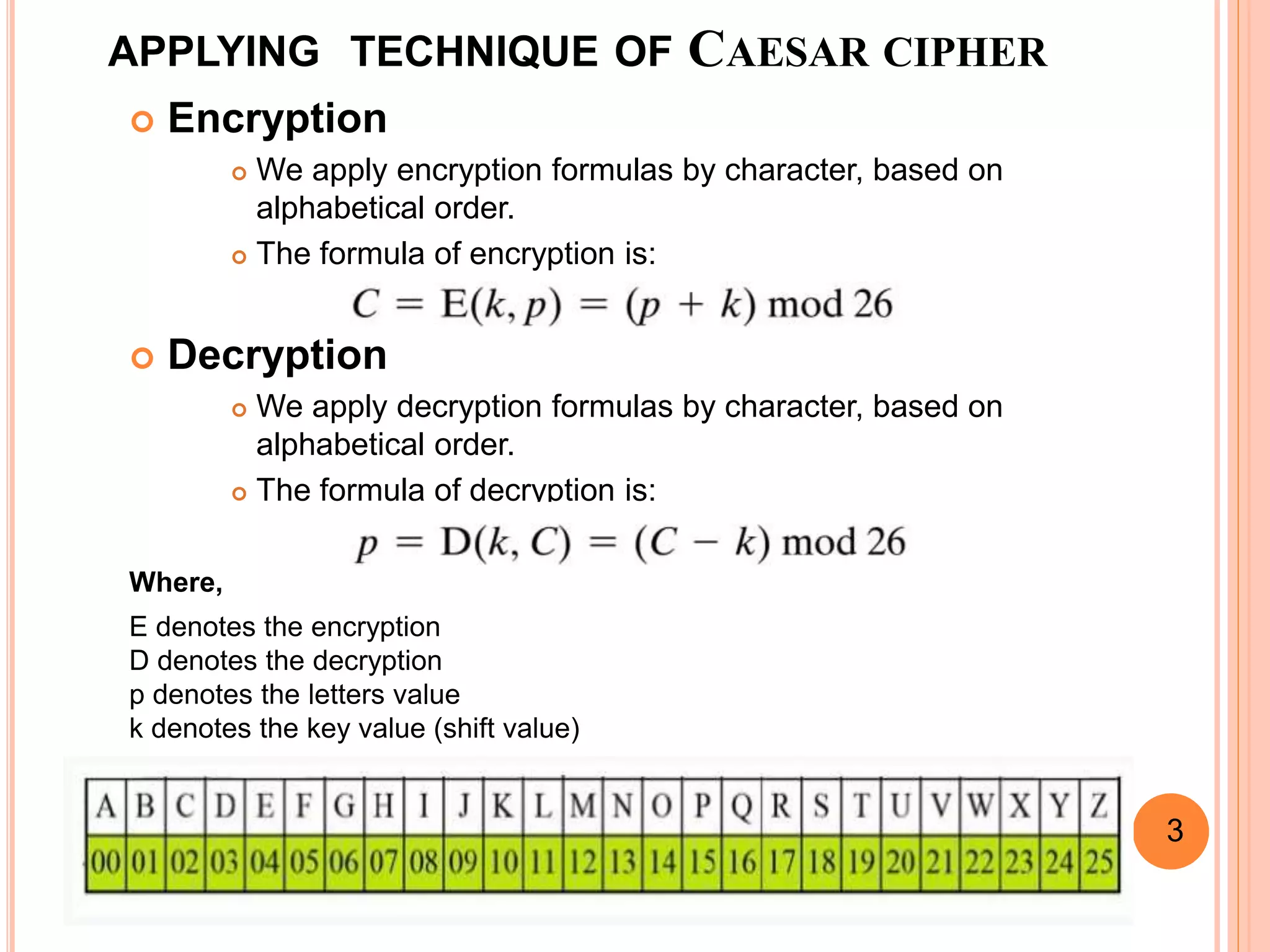
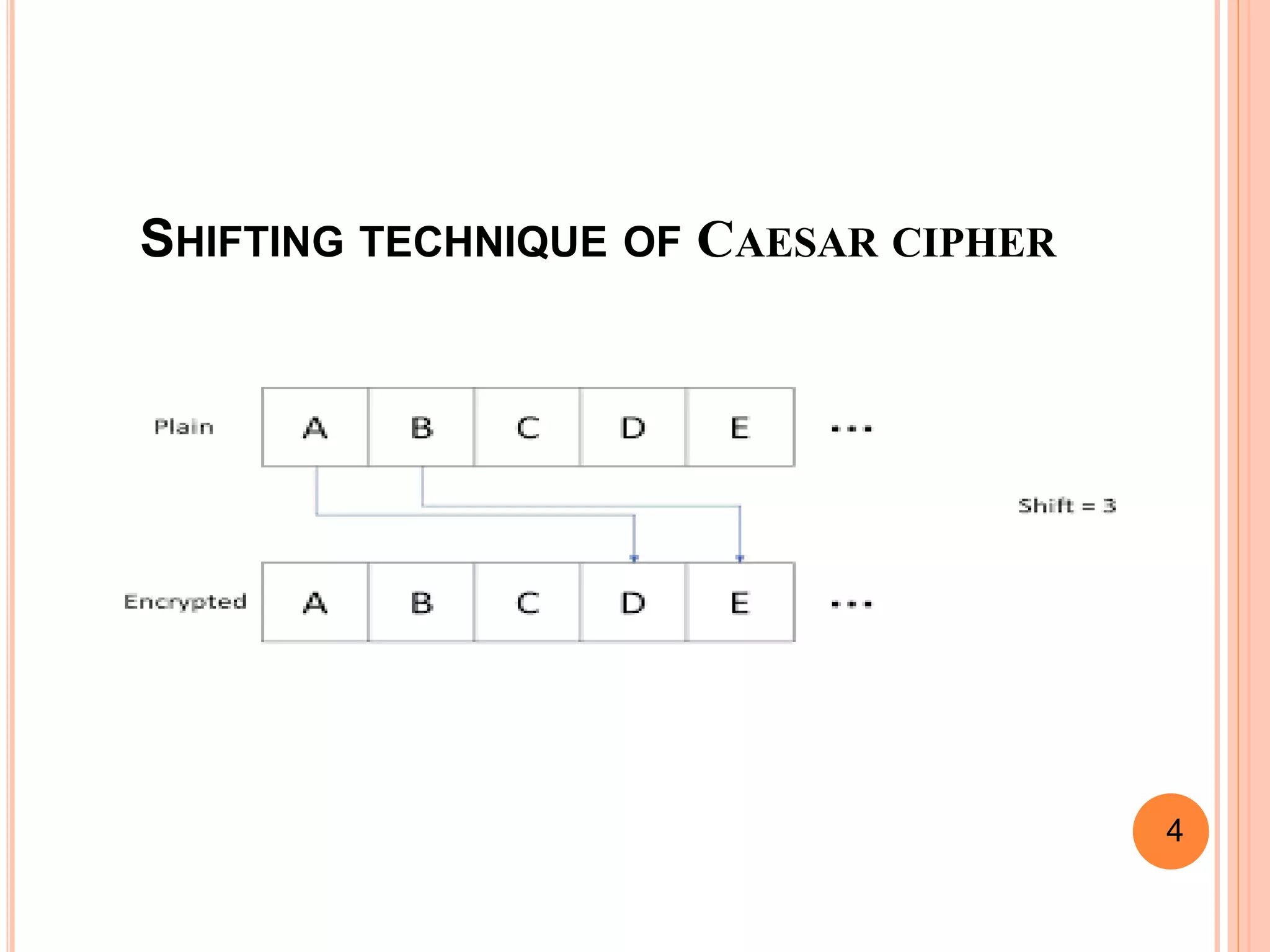
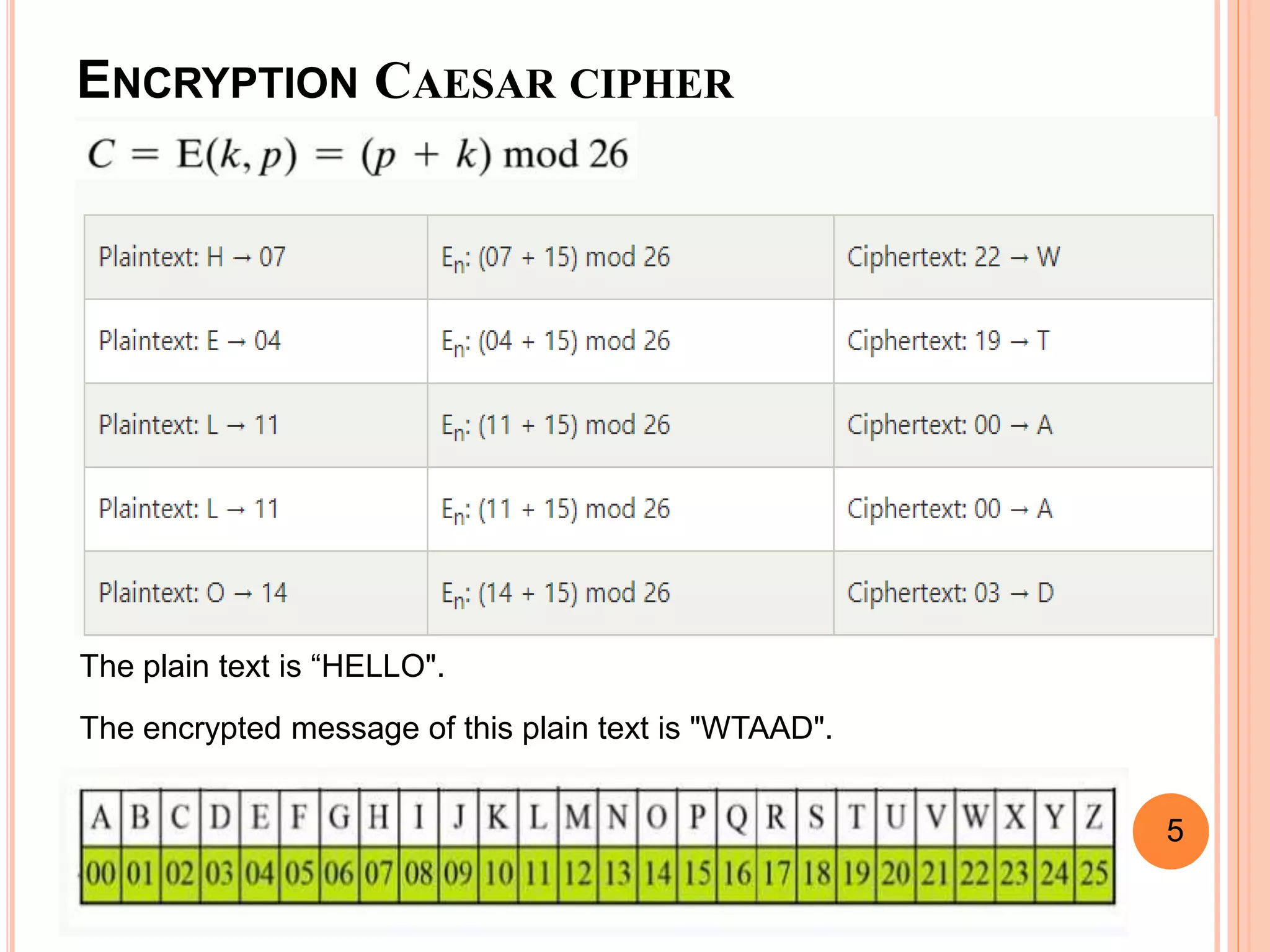
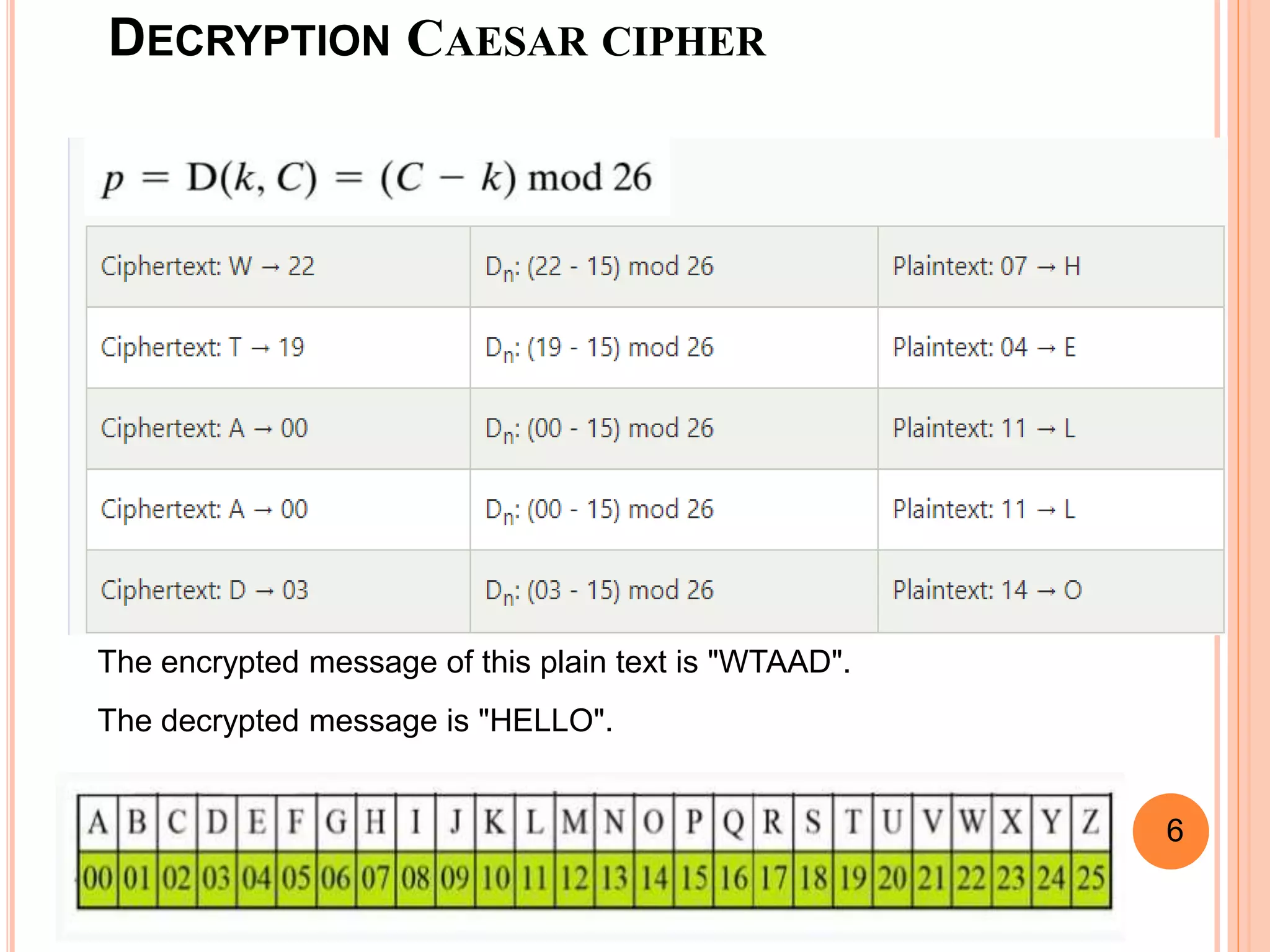
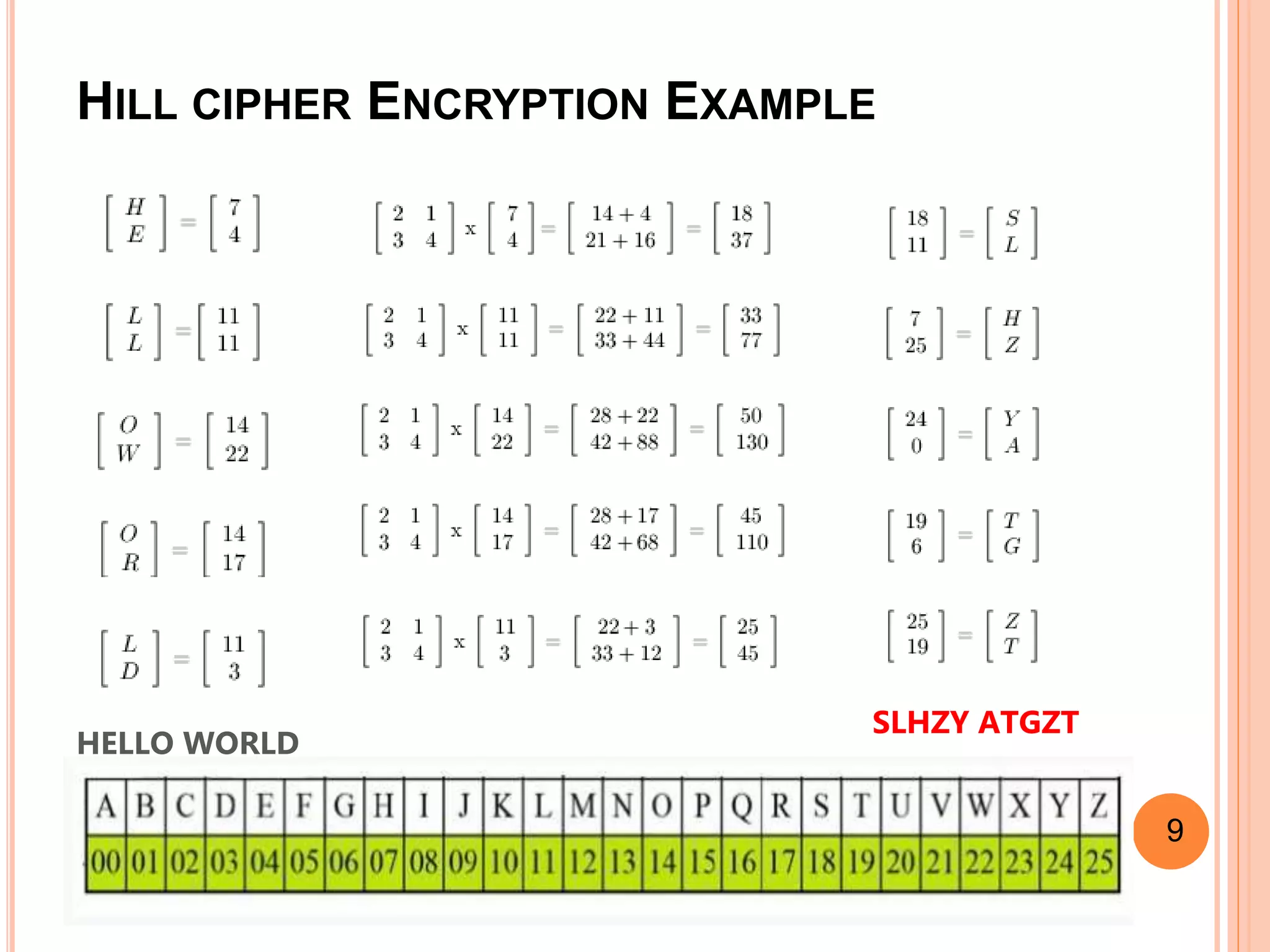
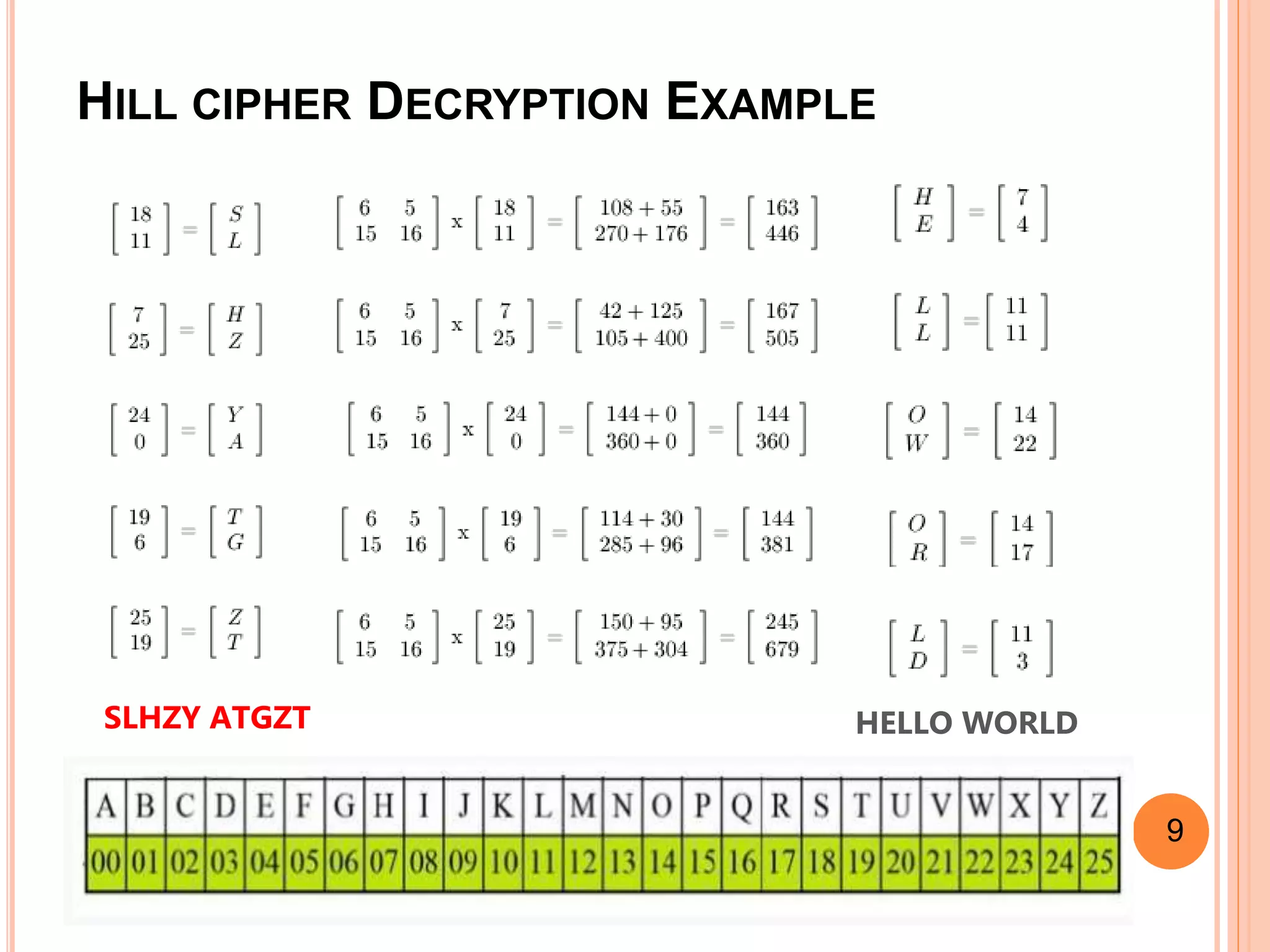
This document discusses the Caesar cipher and Hill cipher methods of encryption. It provides an introduction to each cipher, including how the Caesar cipher works by shifting letters of the alphabet and how the Hill cipher uses a matrix to encrypt blocks of text. The key advantages and disadvantages of each cipher are outlined, such as the Caesar cipher being very easy to implement but also easy to hack, while the Hill cipher provides more security but encrypted text cannot be decrypted if the key matrix is noninvertible. Examples of encrypting and decrypting text using each cipher are also included.