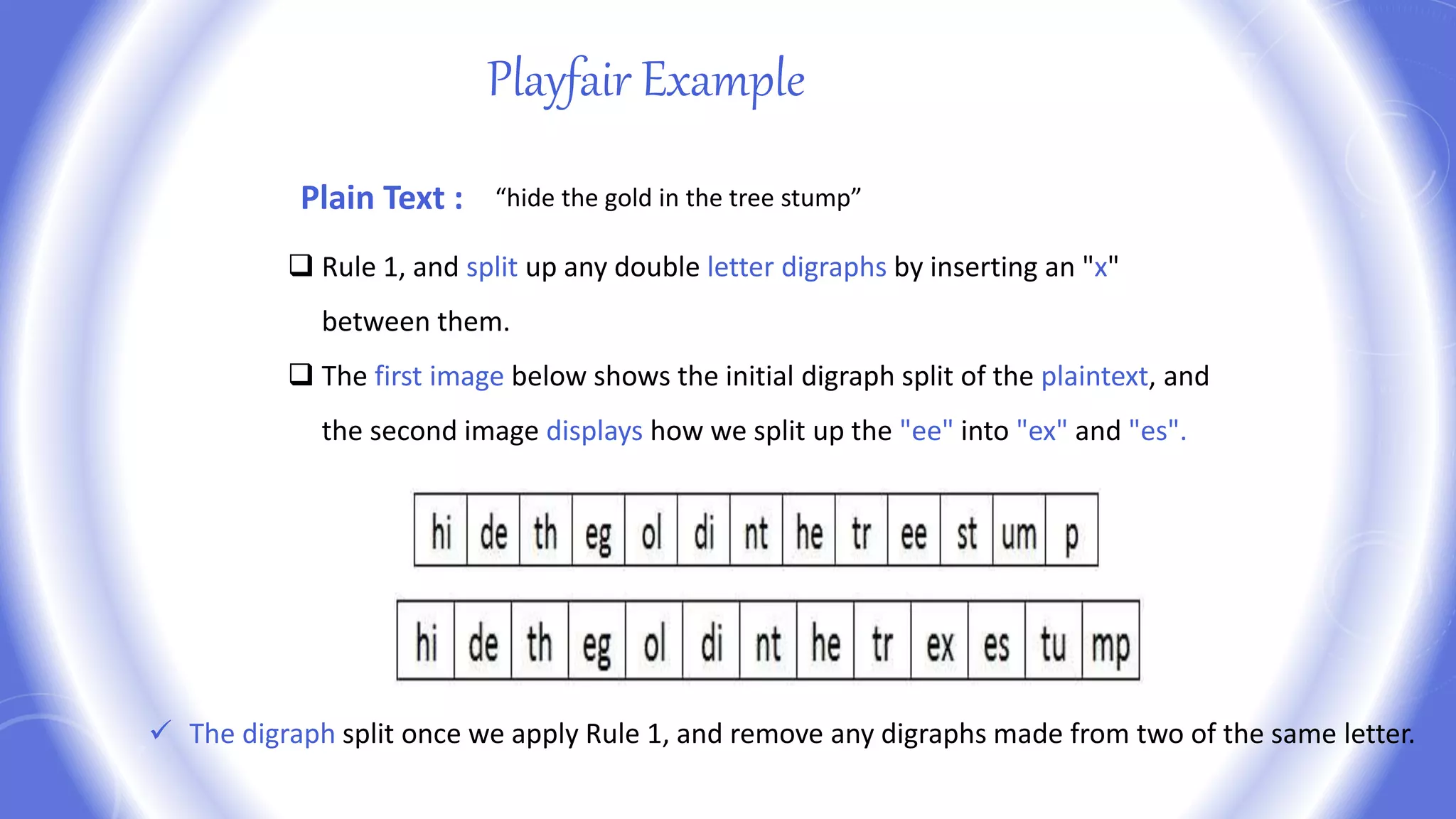
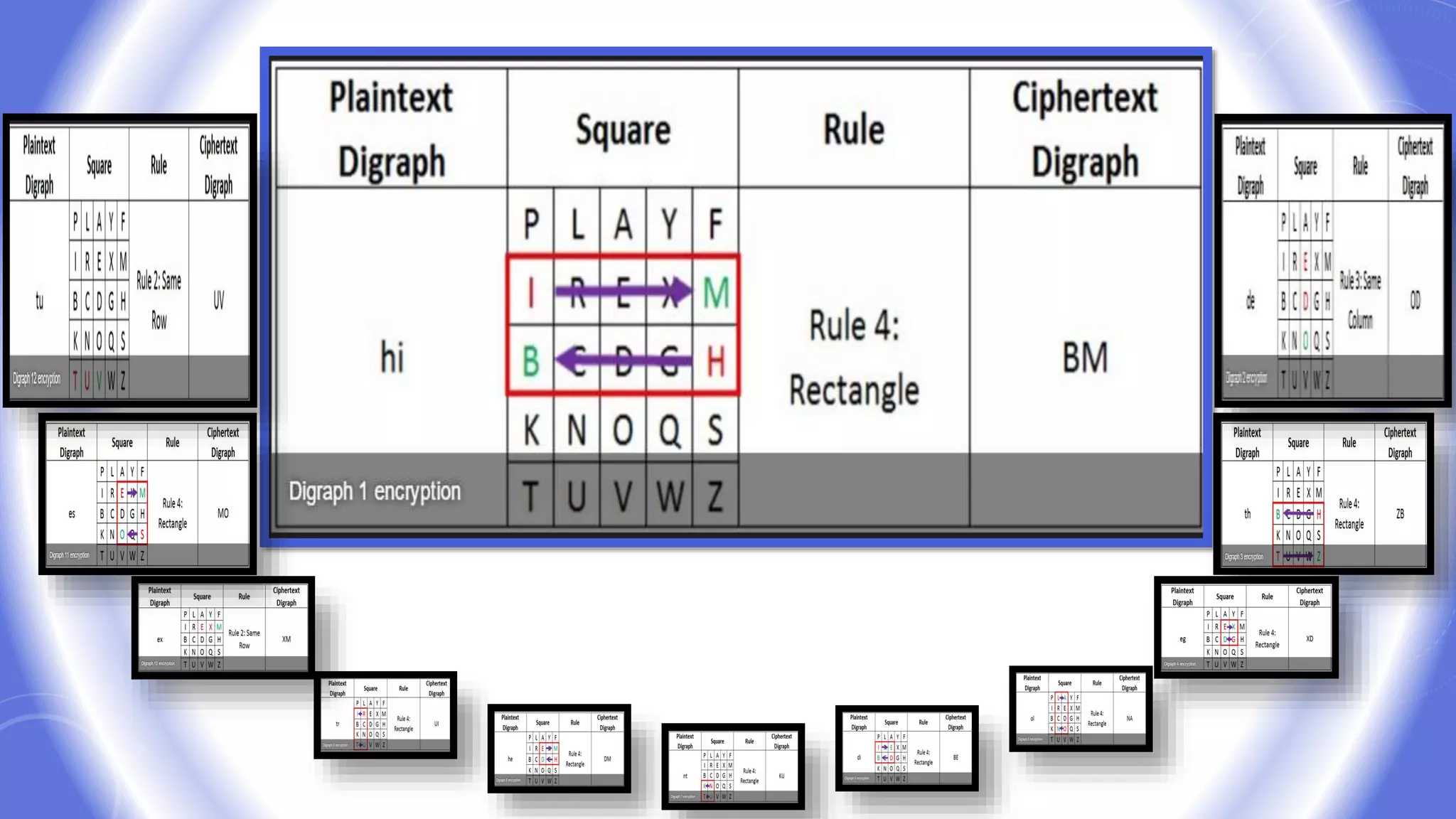
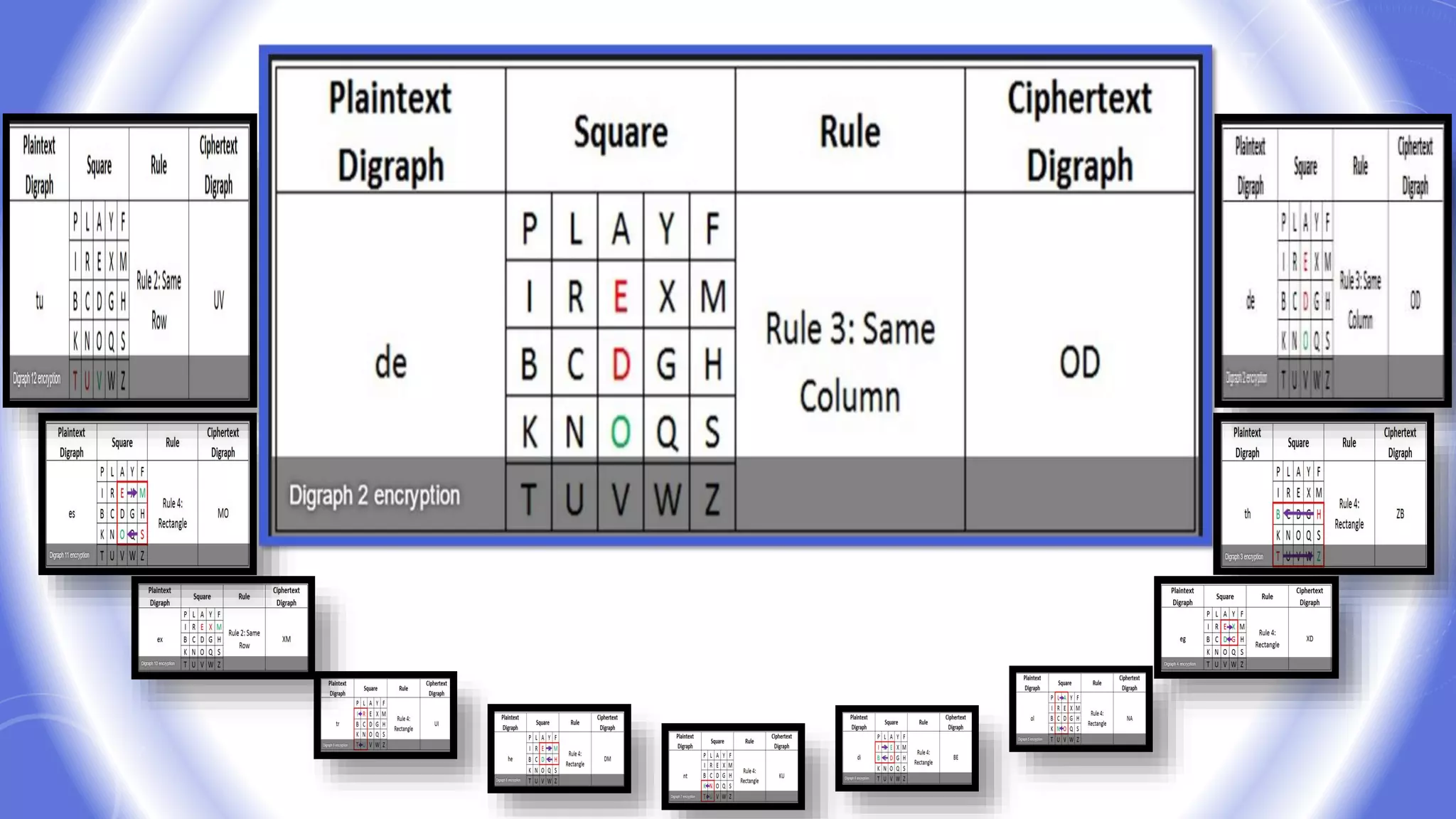
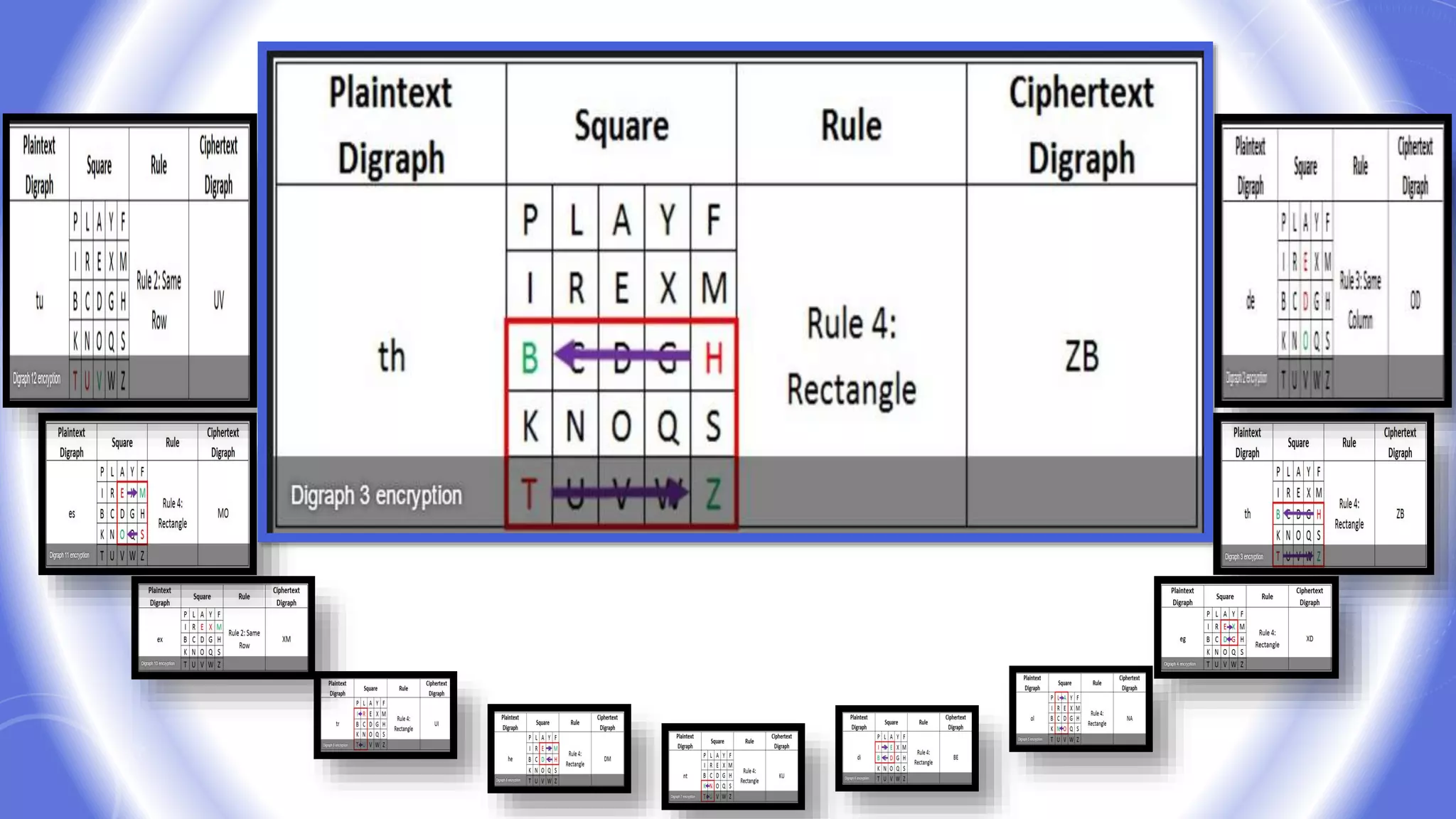
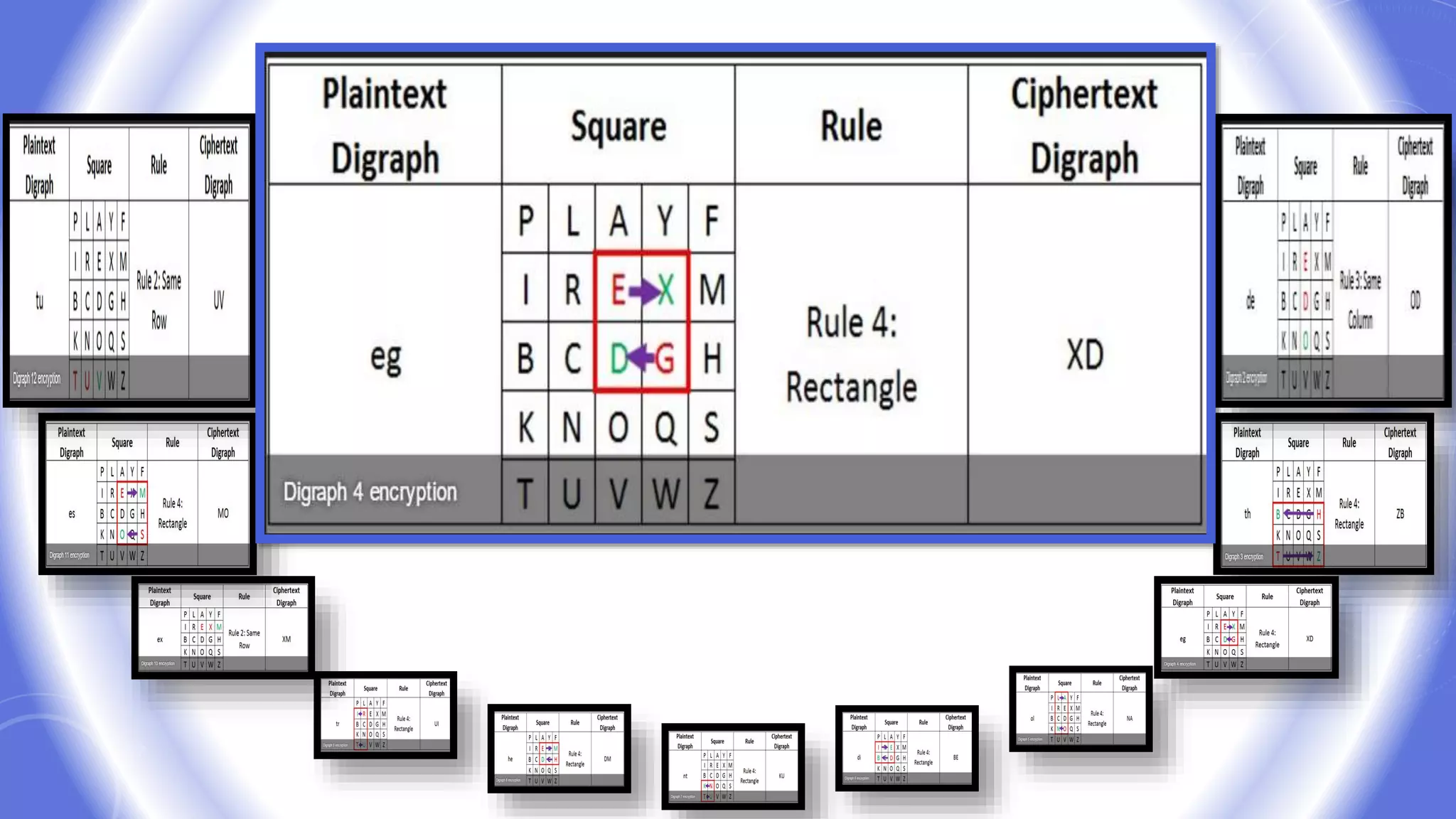
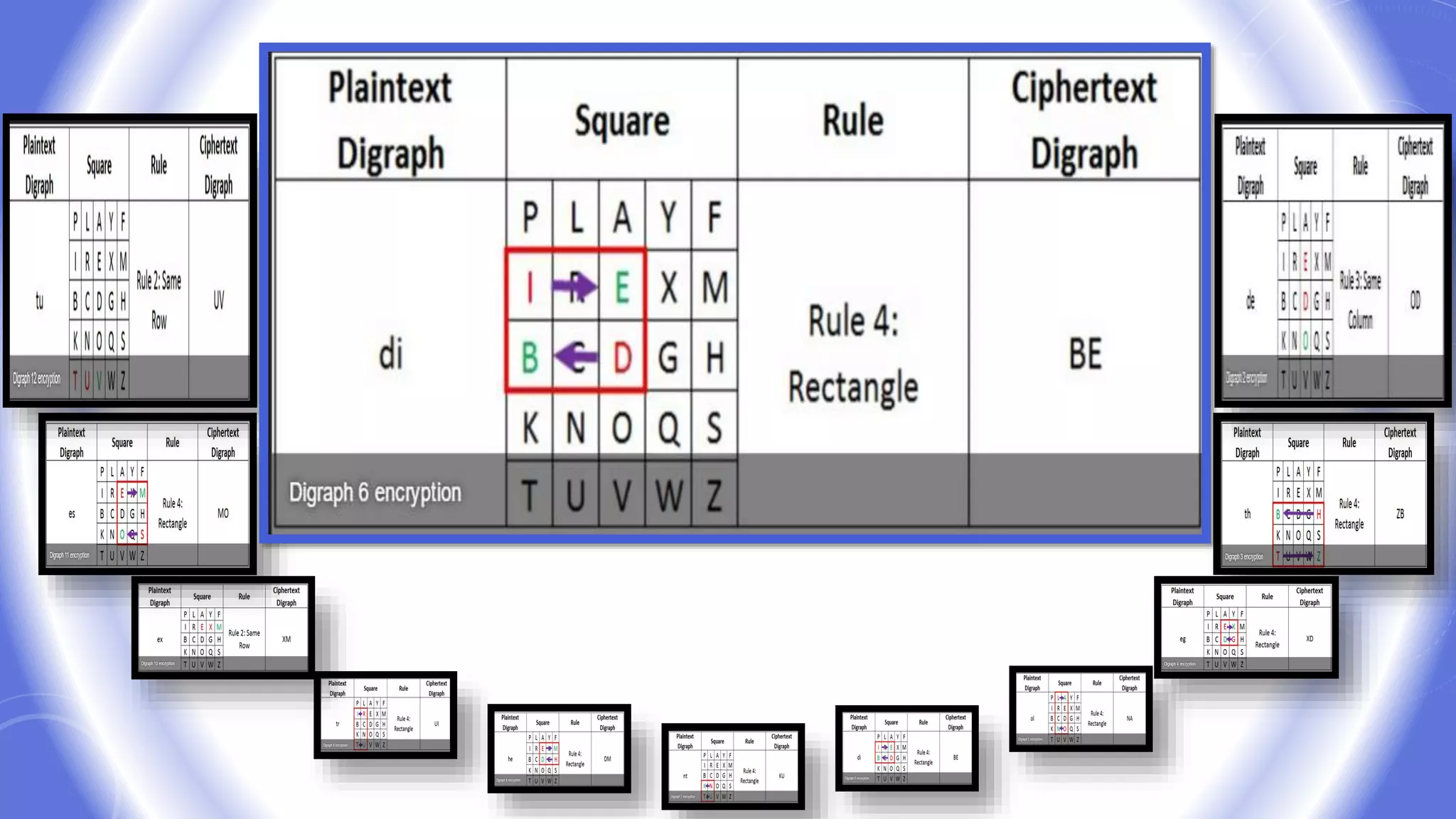
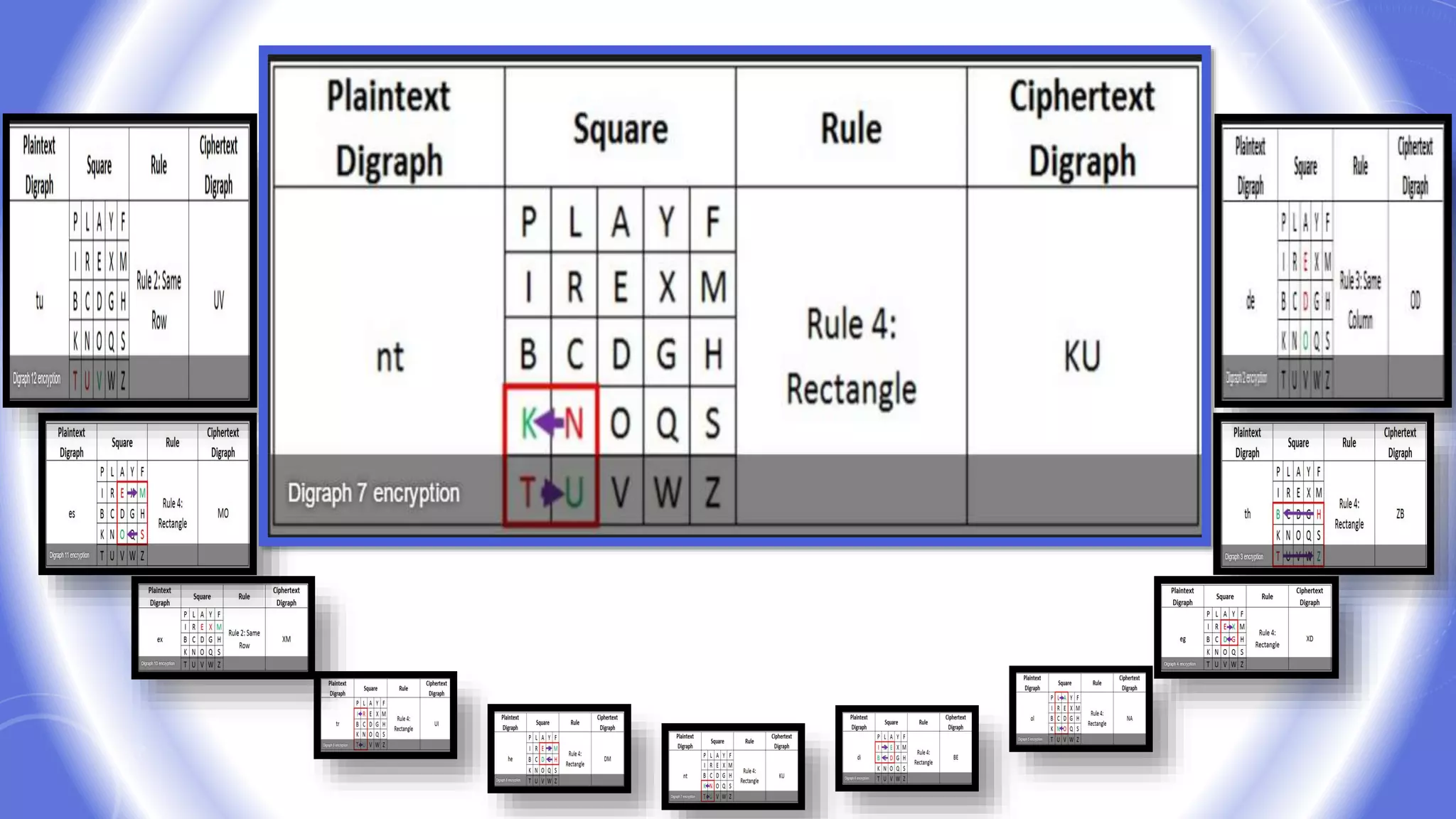
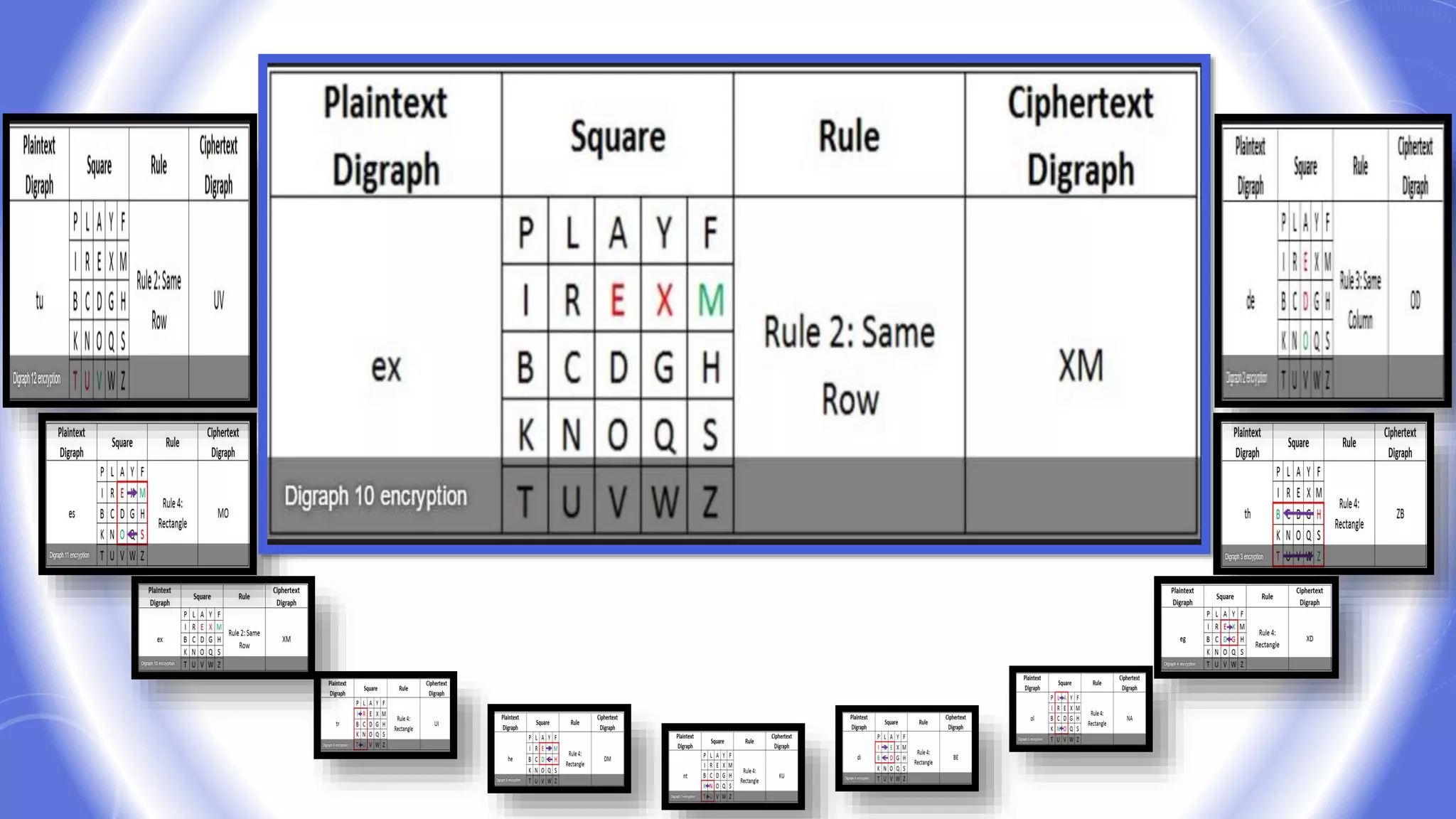
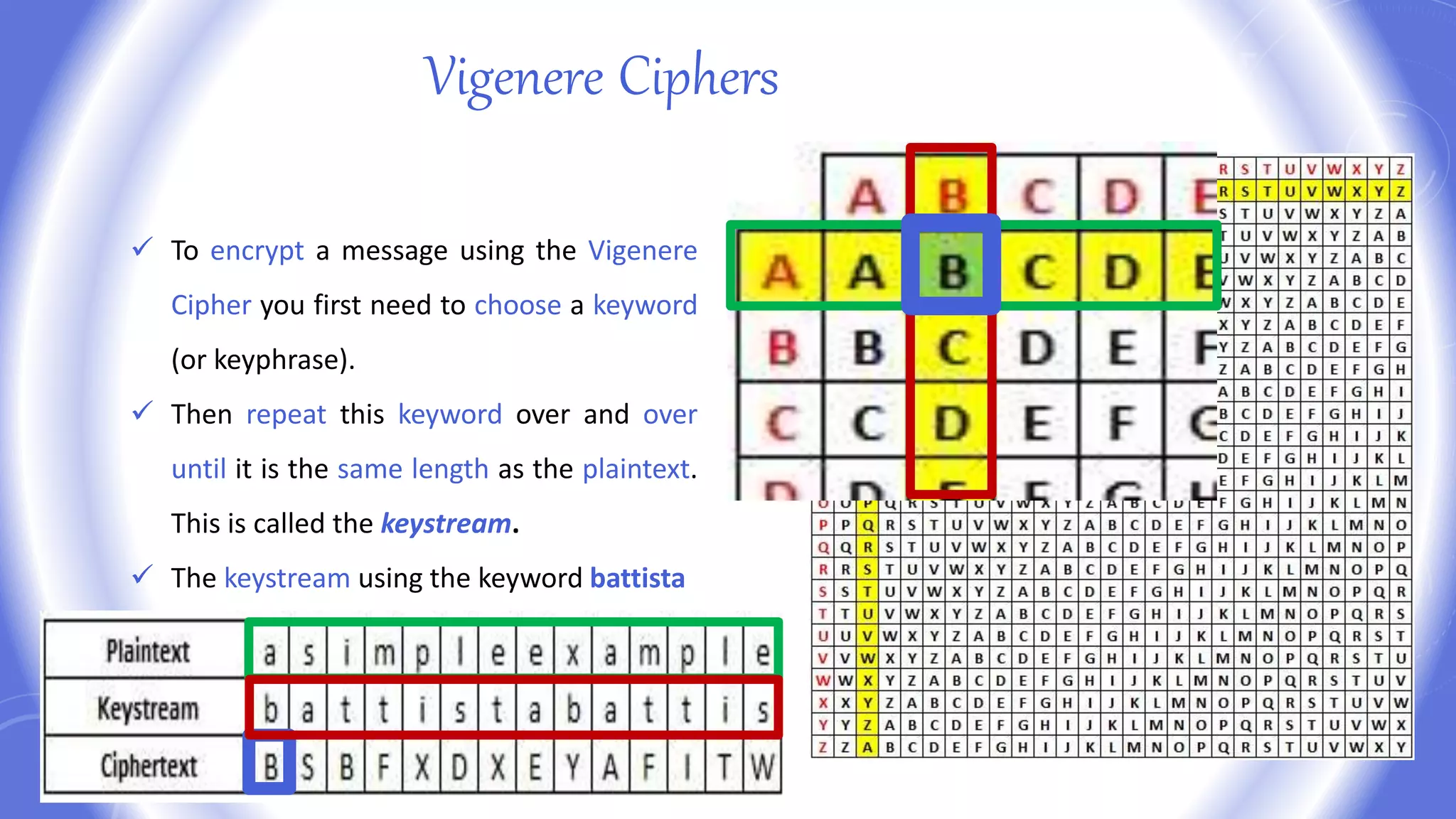
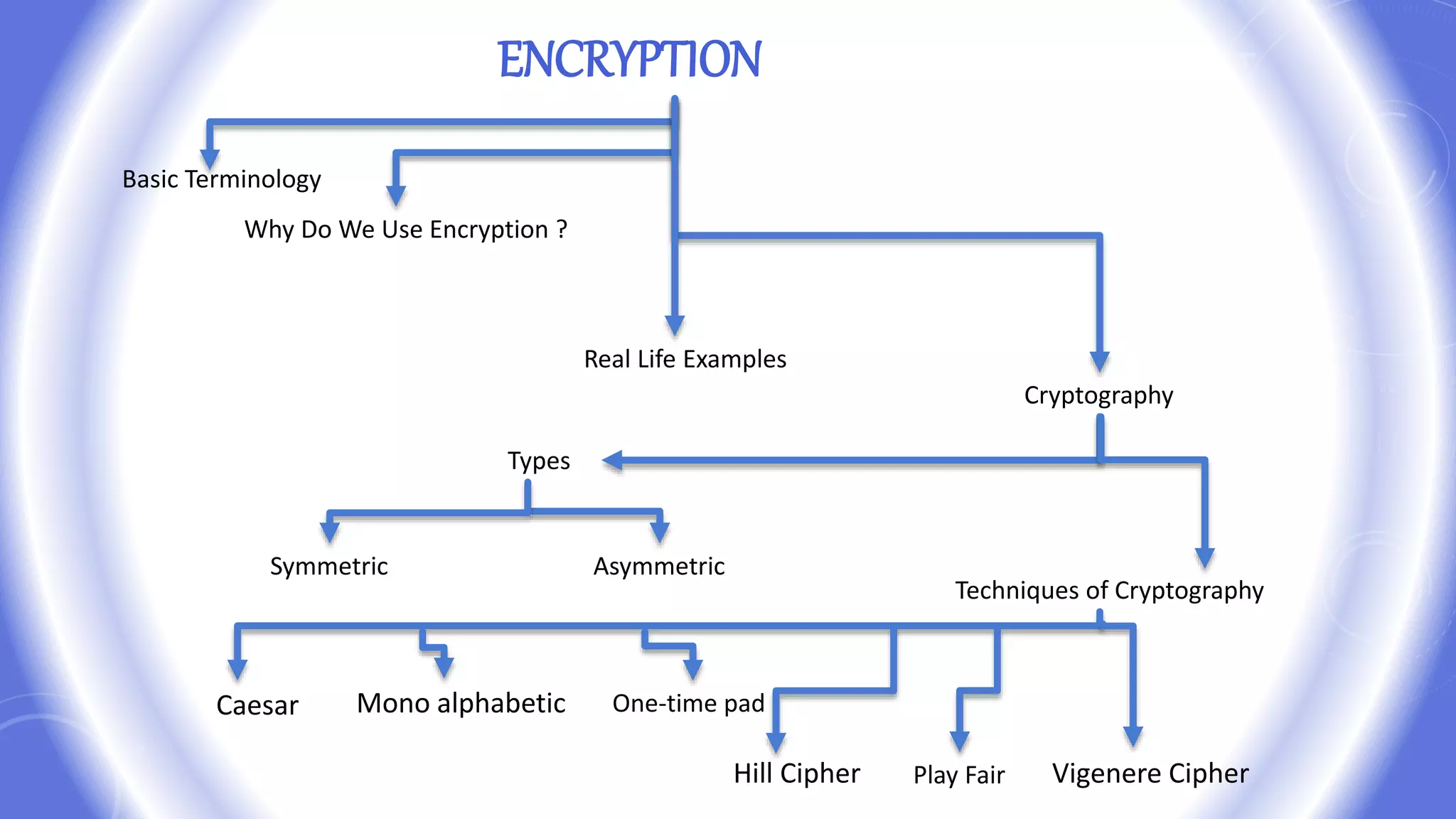
This document provides an overview of encryption techniques. It begins with basic terminology used in cryptography such as plaintext, ciphertext, cipher, key, enciphering, deciphering, and cryptanalysis. It then discusses why encryption is used and provides real-life examples of encryption applications. The document outlines symmetric and asymmetric cryptography and describes several classical ciphers such as the Caesar cipher, monoalphabetic ciphers, the one-time pad, Hill cipher, Playfair cipher, and Vigenere cipher.









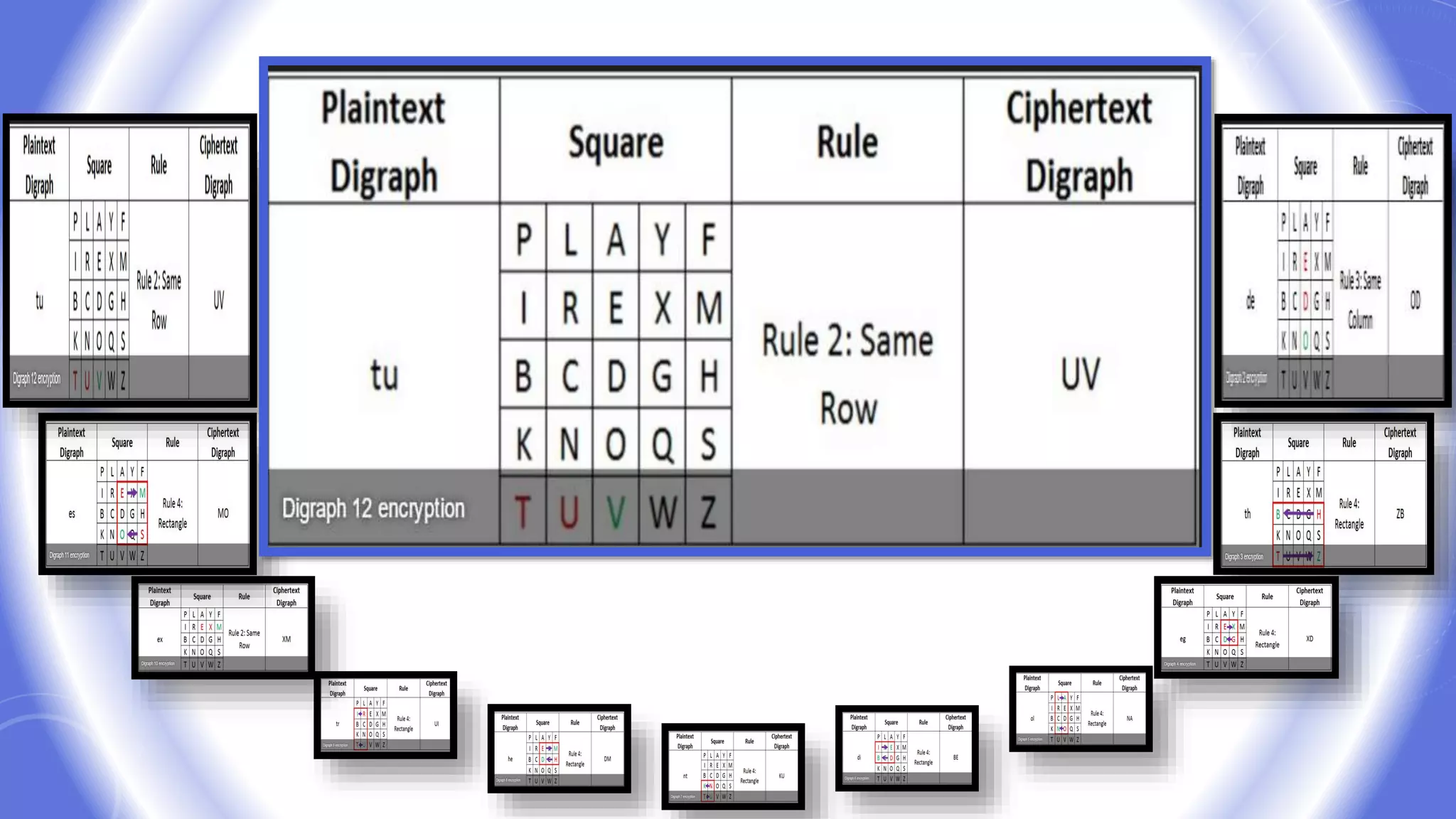
![Hill Cipher Example
The key for a hill cipher is a matrix
e.g.
In the above case, we have taken the size to be 3×3
Assume we want to encipher the message ATTACK AT DAWN.
We now take the first 3 characters from our plaintext, ATT and
create a vector that corresponds to the letters to get: [0 19 19]
Hill Ciphers example](https://image.slidesharecdn.com/cyphertechnique-160601025951/75/Cypher-technique-16-2048.jpg)