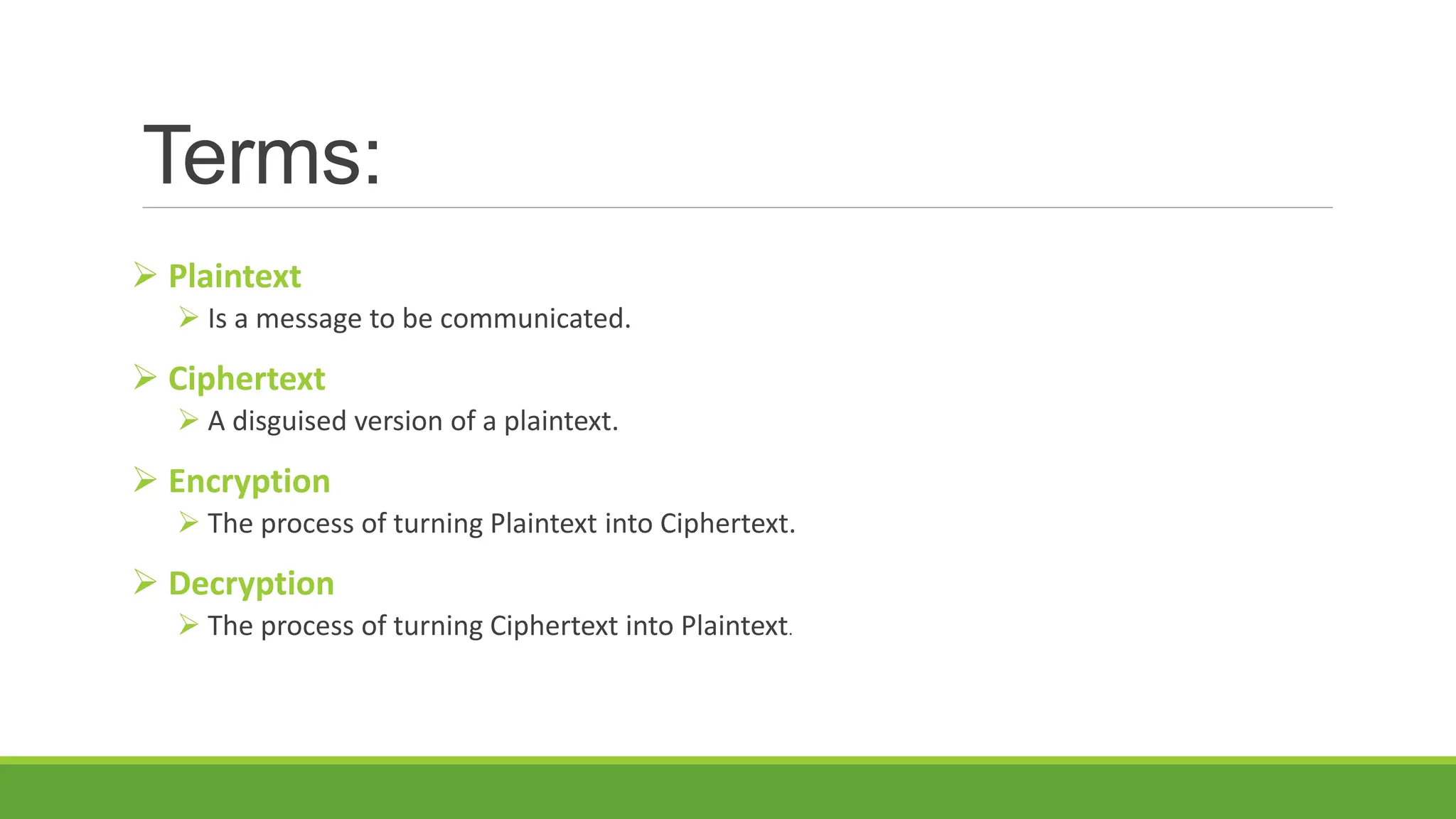
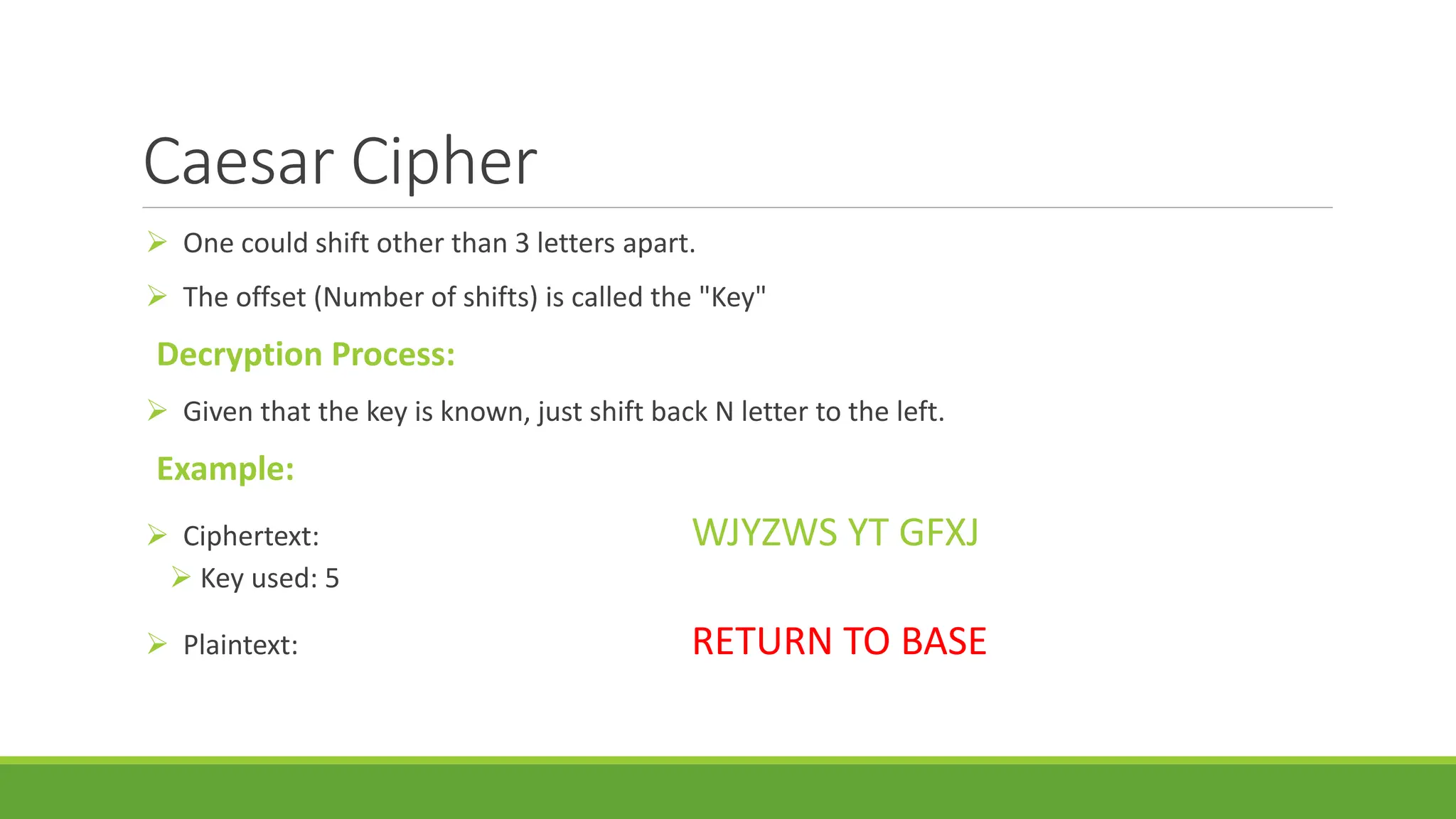
This document provides an overview of the Caesar cipher, one of the earliest known substitution ciphers. It explains that the Caesar cipher involves shifting each letter of a plaintext message by a set number of positions (the key) in the alphabet to encrypt it. For example, with a shift of 3, A would become D, B would become E, etc. The document includes an example of encrypting the plaintext "ATTACK AT DAWN" with a shift of 3. It also describes how the cipher can be represented mathematically using modular arithmetic.