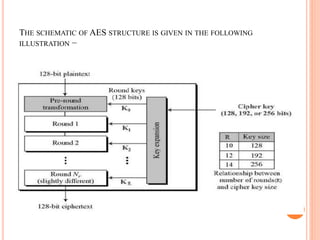
1) The Advanced Encryption Standard (AES) is a symmetric block cipher chosen by the U.S. government to protect classified information. It operates on 128-bit blocks using 128, 192, or 256-bit keys.
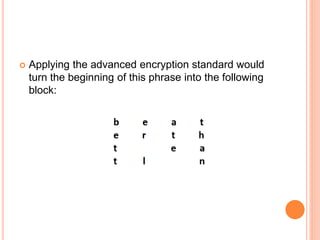
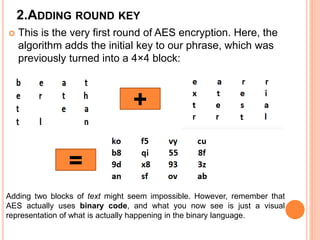
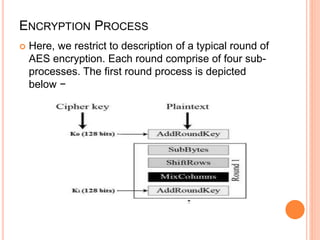
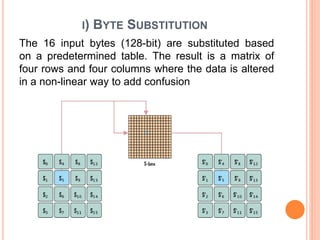
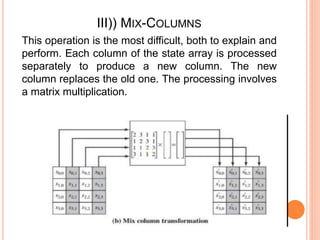
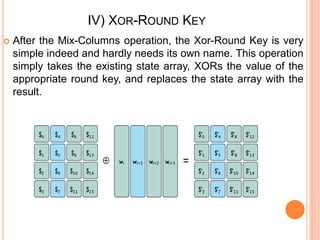
2) AES encryption works by first dividing plaintext into blocks, then adding an initial round key. It undergoes multiple rounds of byte substitution, shift rows, mix columns, and XOR with round keys until ciphertext is produced.
3) Proper implementation and protection of AES encryption keys is important for security, as keys could enable hackers to decrypt ciphertext if accessed without authorization.