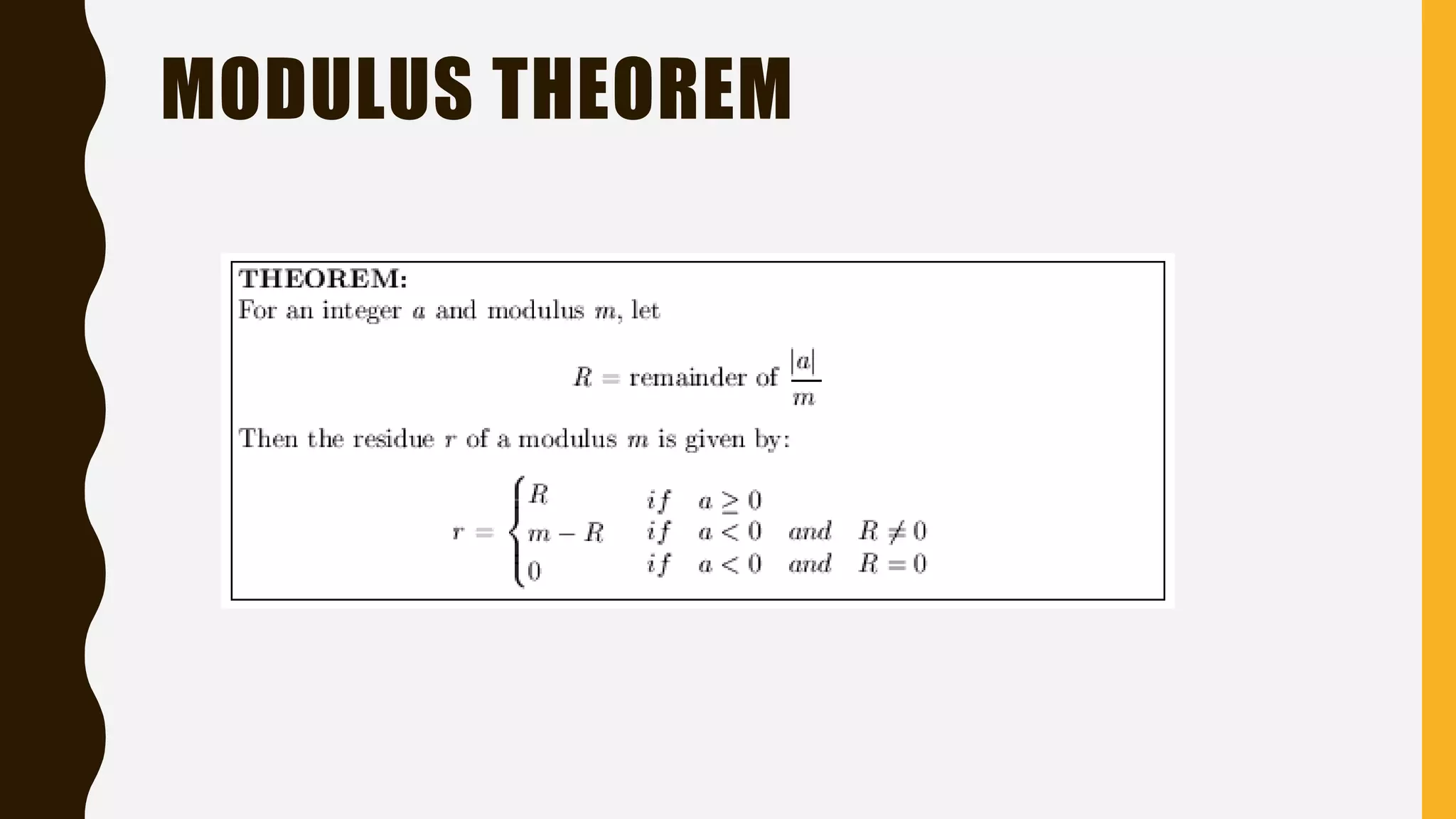
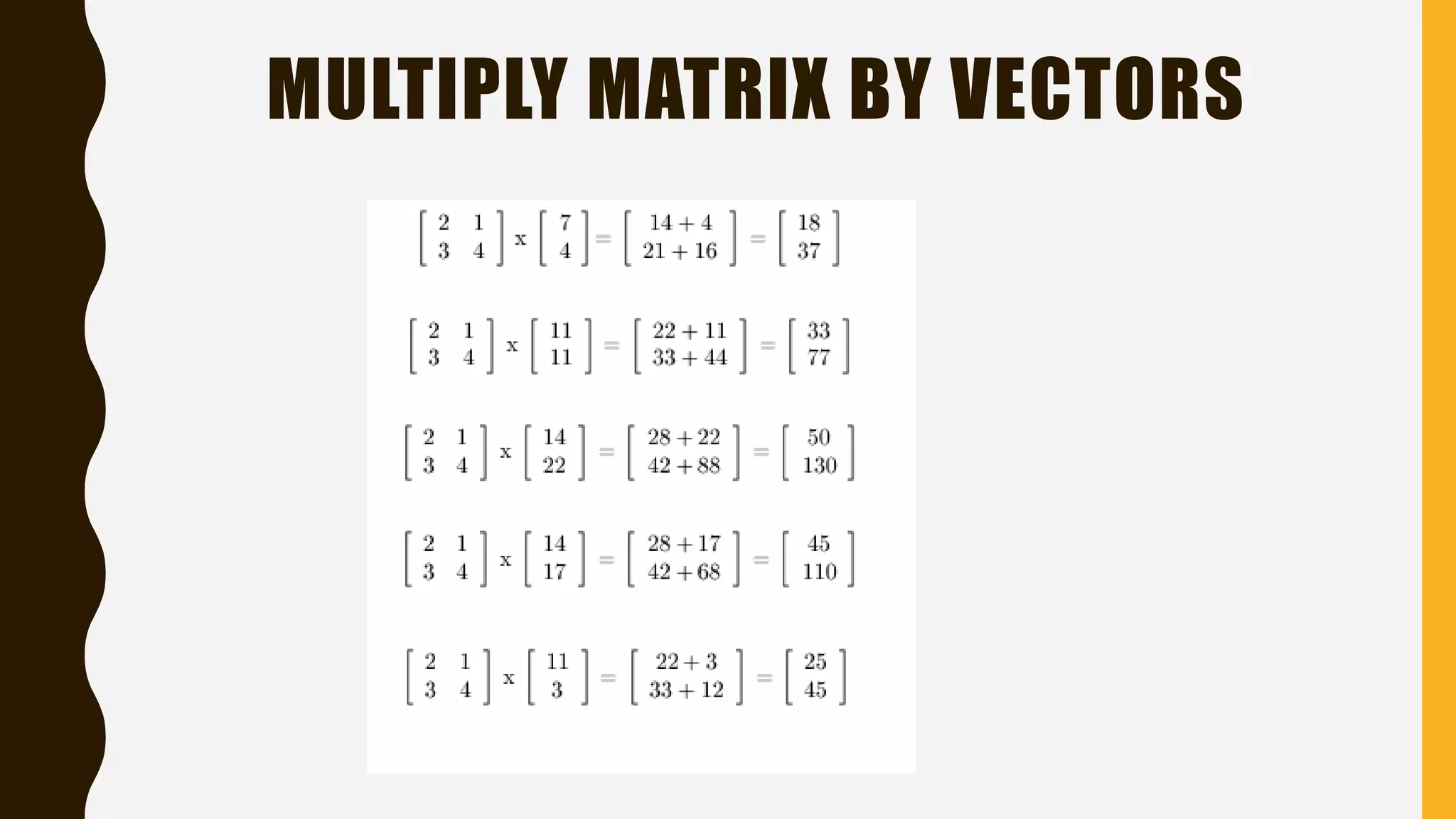
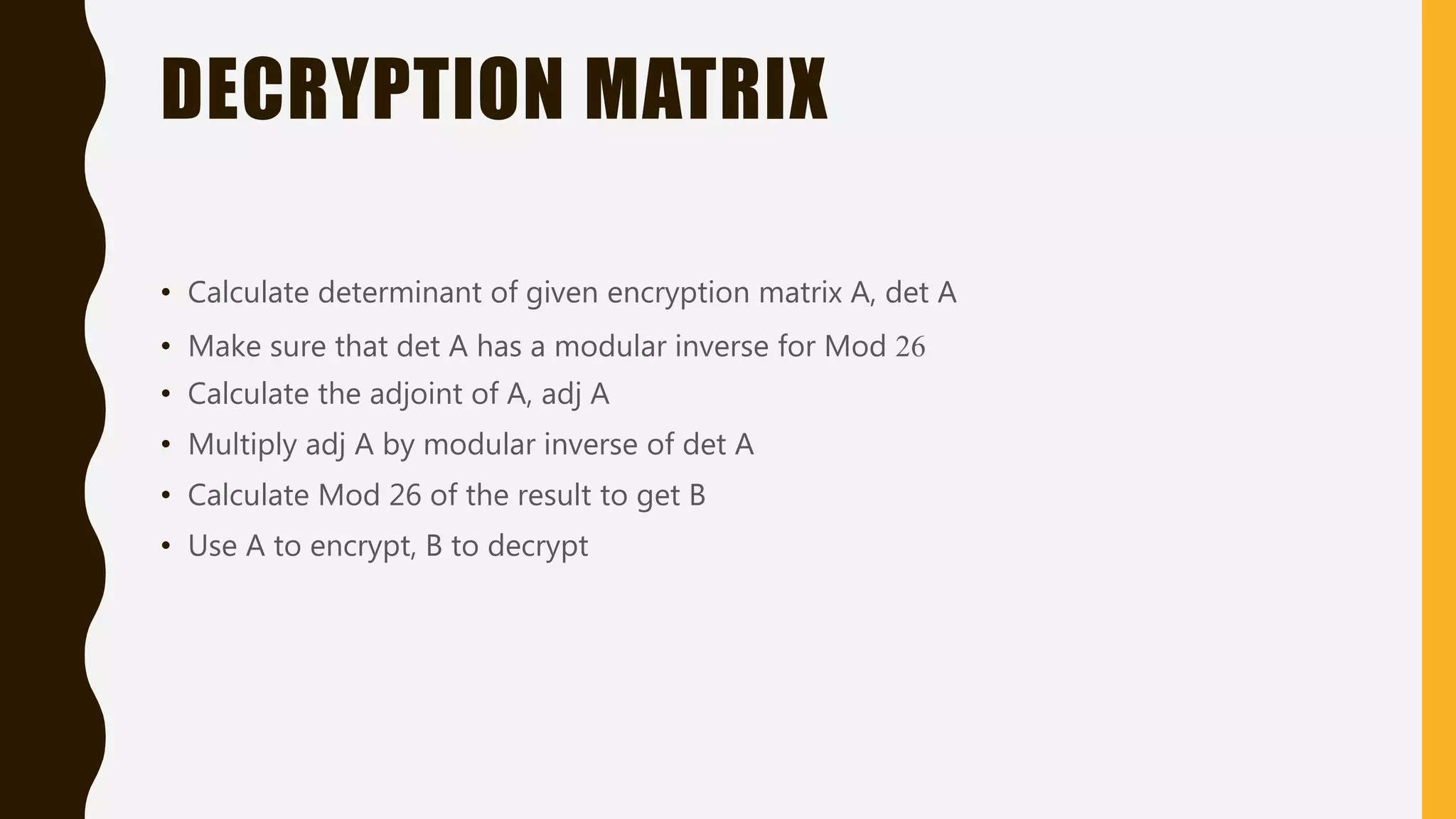
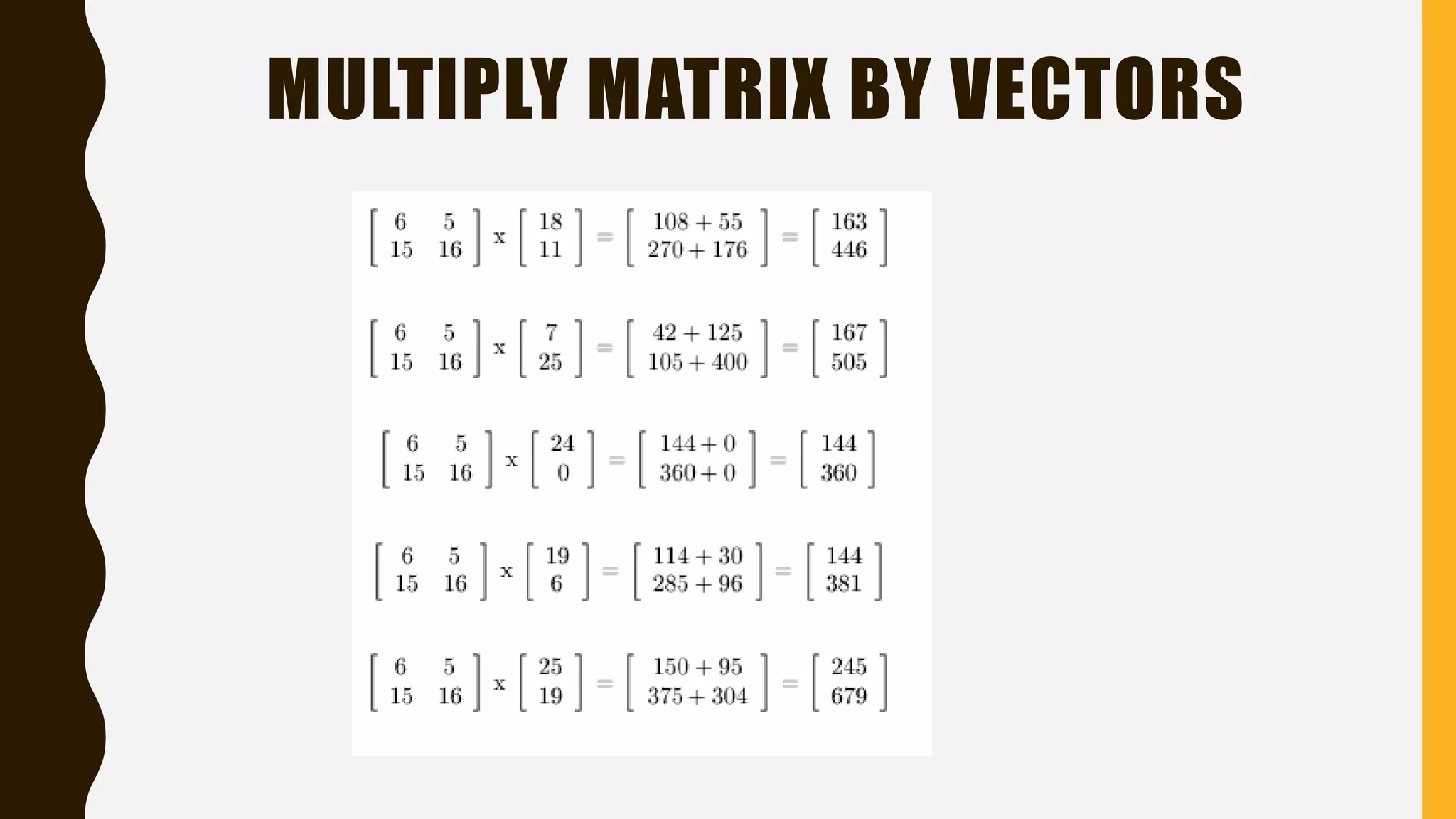
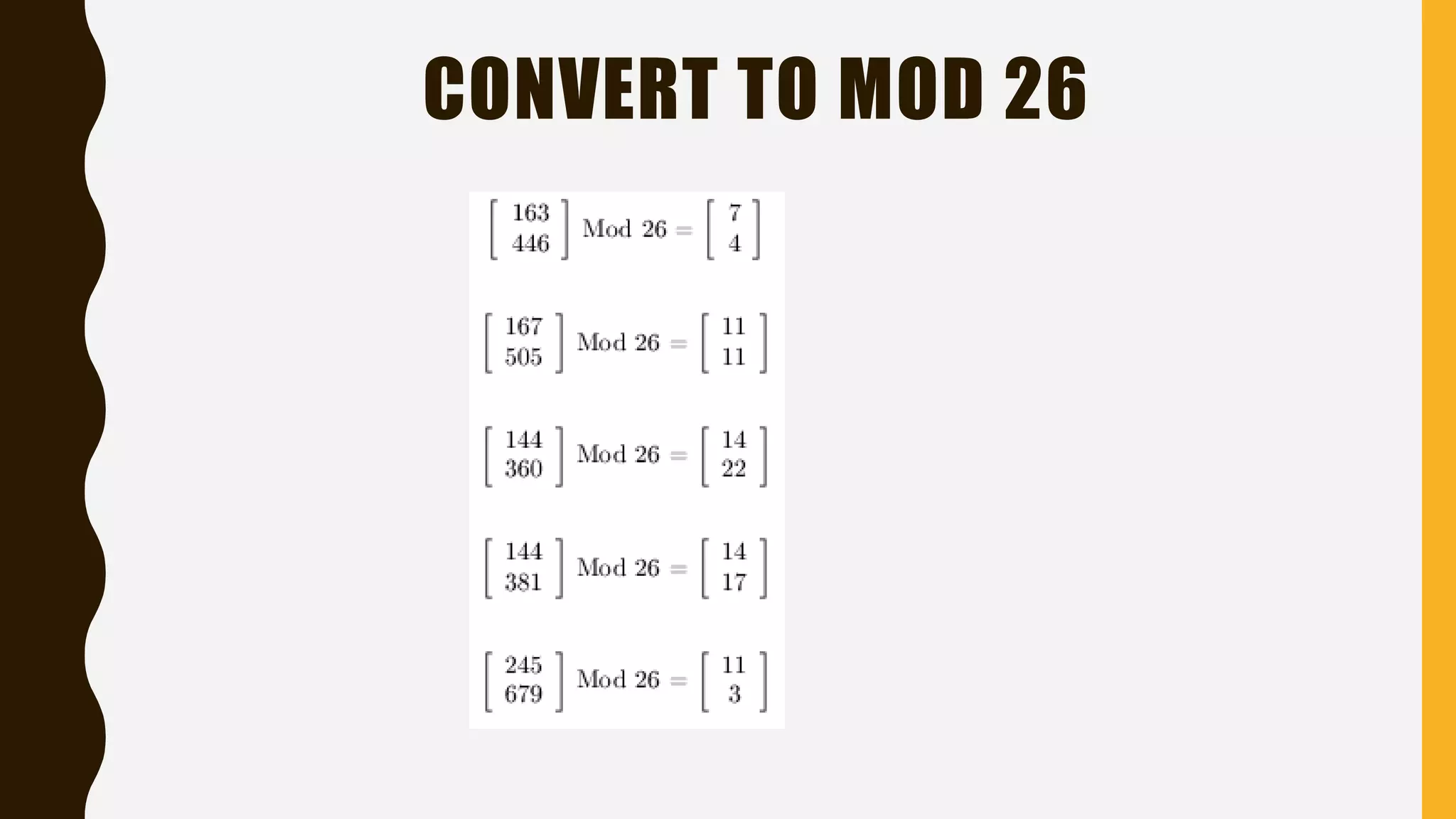
The document discusses the Hill cipher, a polygraphic cipher technique based on linear algebra. The Hill cipher operates on blocks of letters, using a secret key matrix to encrypt plaintext letters into ciphertext. It encrypts by multiplying blocks of plaintext letters by the key matrix, taking the result modulo 26. The corresponding decryption matrix is calculated from the encryption matrix and is used to decrypt by reversing the process. An example demonstrates encrypting and then decrypting the message "HELLO WORLD" using a 2x2 matrix.