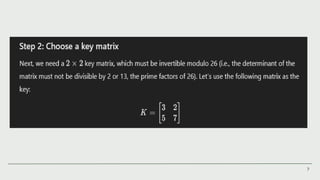
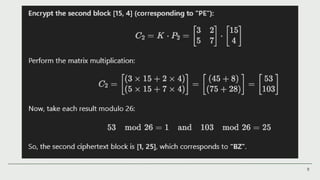
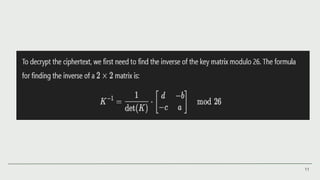
The Hill cipher is a polygraphic substitution cipher that employs linear algebra for encryption and decryption, invented by Lester S. Hill in 1929. It requires a square key matrix and involves processes like assigning numerical values to letters and performing matrix operations. While it has strengths against frequency analysis, it also has weaknesses, such as key distribution challenges and vulnerabilities to known plaintext attacks.





![6
Step 1: Assign Numerical Values
to the Letters
● Convert the letters of the word 'Hope' into their numerical equivalents:
● H = 7, O = 14, P = 15, E = 4
● Plaintext: [7, 14, 15, 4]
● Split into pairs:
● (H, O) → [7, 14]
● (P, E) → [15, 4]](https://image.slidesharecdn.com/hillcipher-241215144710-43c388aa/85/Understanding-the-Hill-Cipher-with-Matrix-6-320.jpg)