1. The document summarizes the Playfair cipher and Vigenere cipher. The Playfair cipher encrypts text as digraphs (pairs of letters) using a 5x5 grid, while the Vigenere cipher uses a polyalphabetic substitution cipher where the alphabet is shifted according to a repeating keyword.
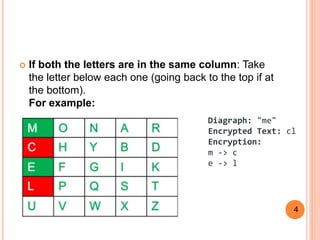
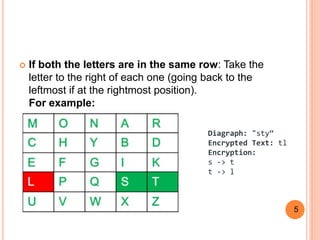
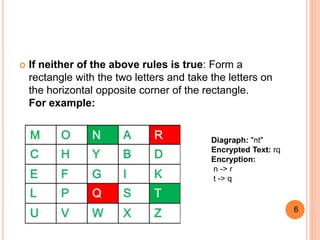
2. The Playfair cipher encryption involves splitting the plaintext into pairs, and then looking at the letters' positions in the grid to determine which letters to substitute. If both letters are in the same row/column, letters are taken from that row/column. Otherwise, a rectangle is formed to find the substitution.
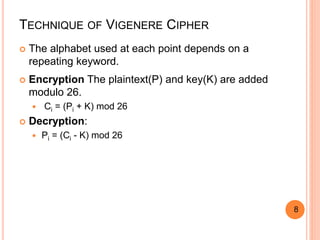
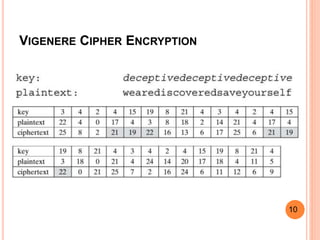
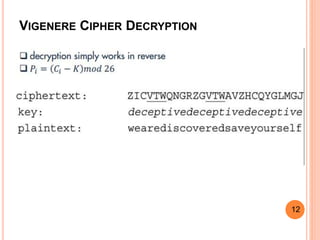
3. The Vigenere cipher adds the letters of the plaintext and keyword modulo 26