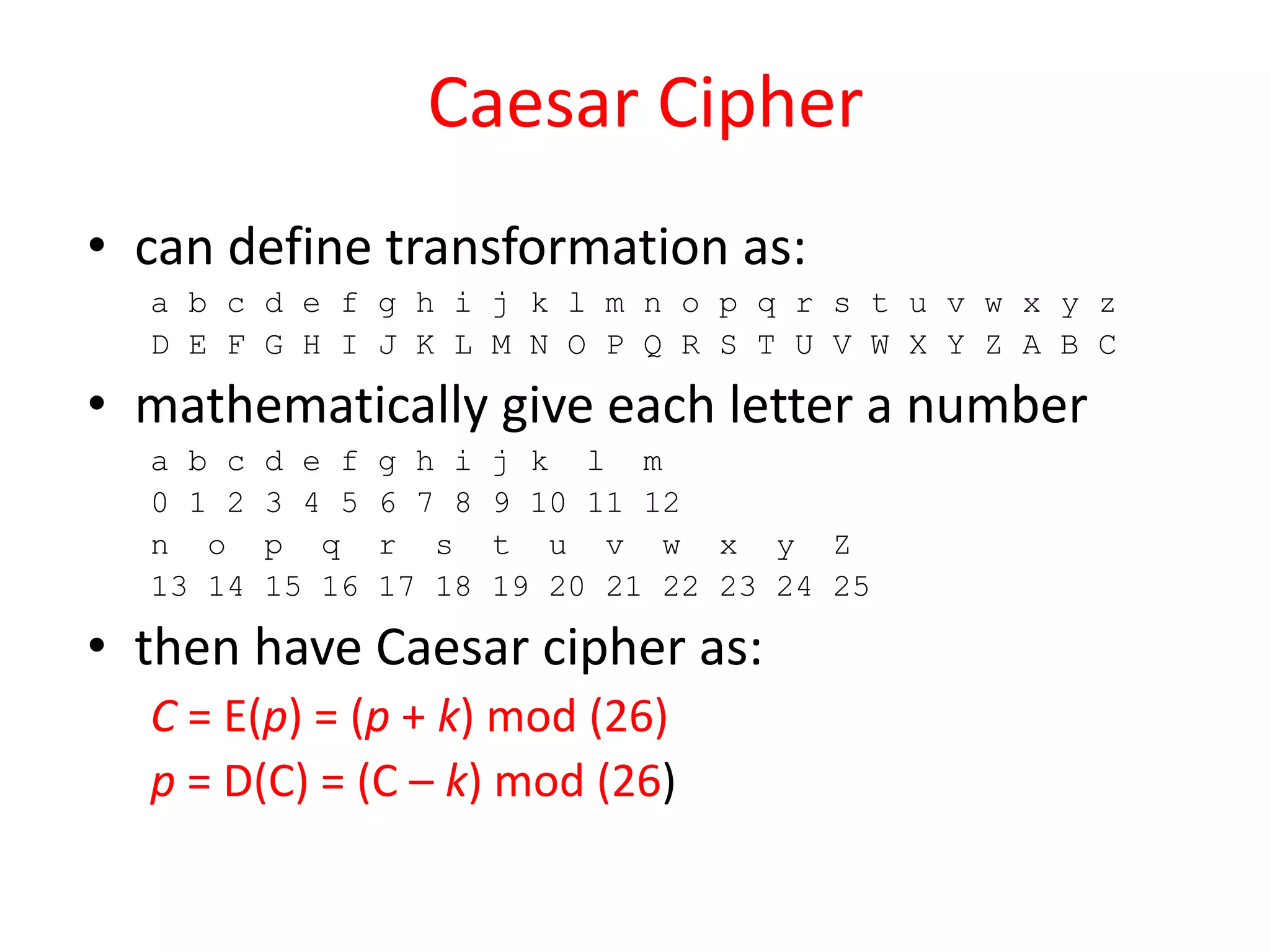
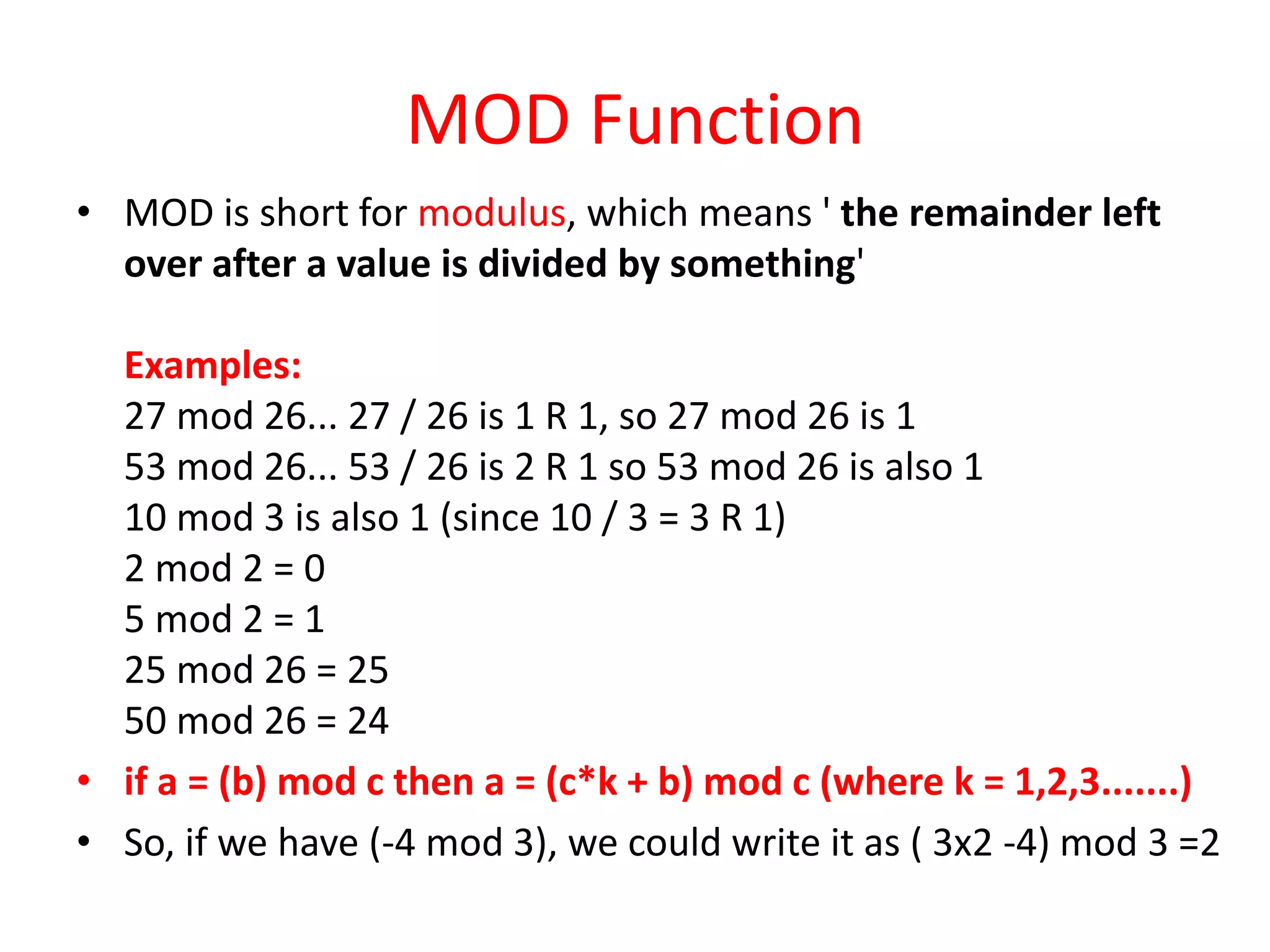
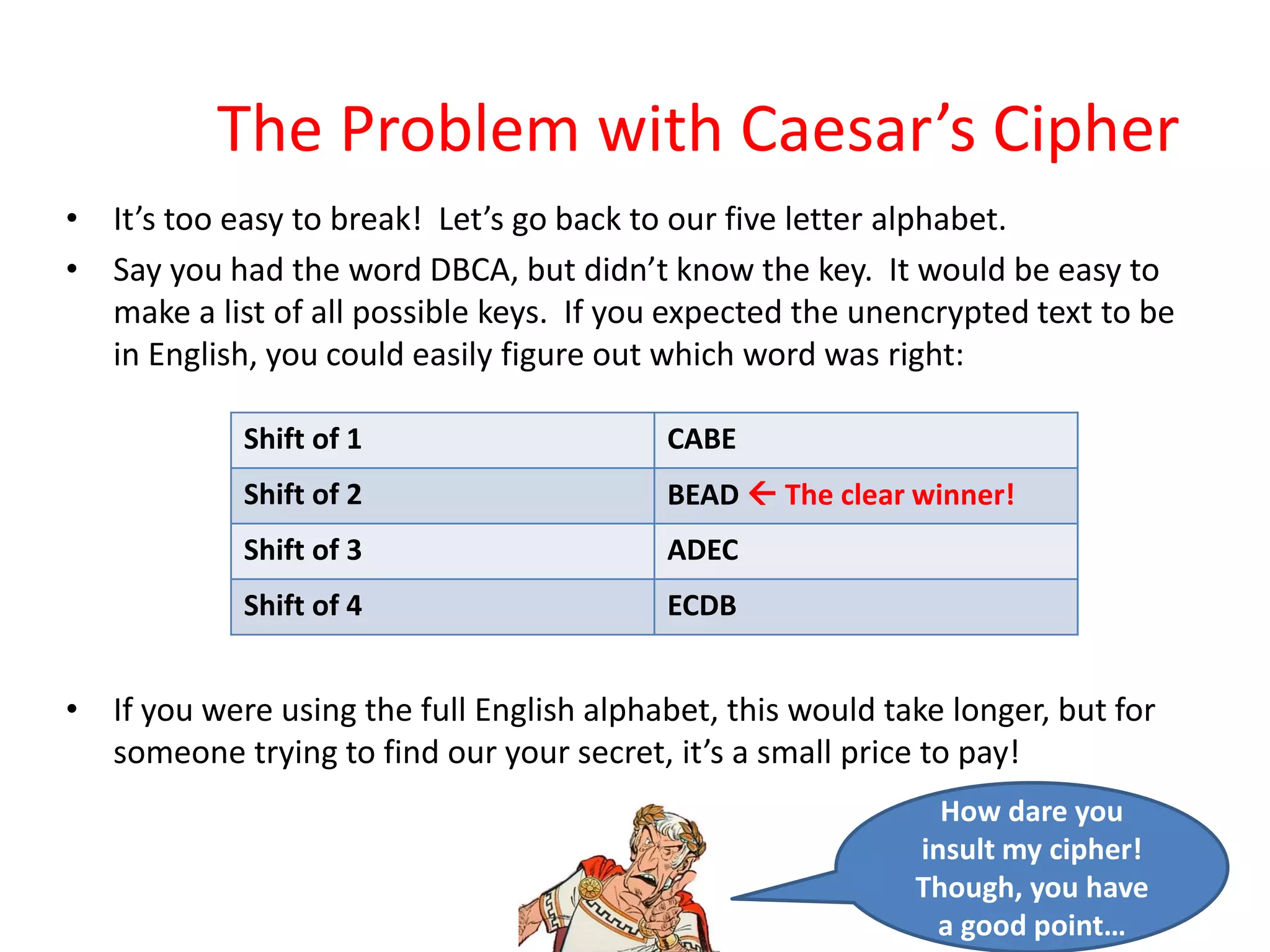
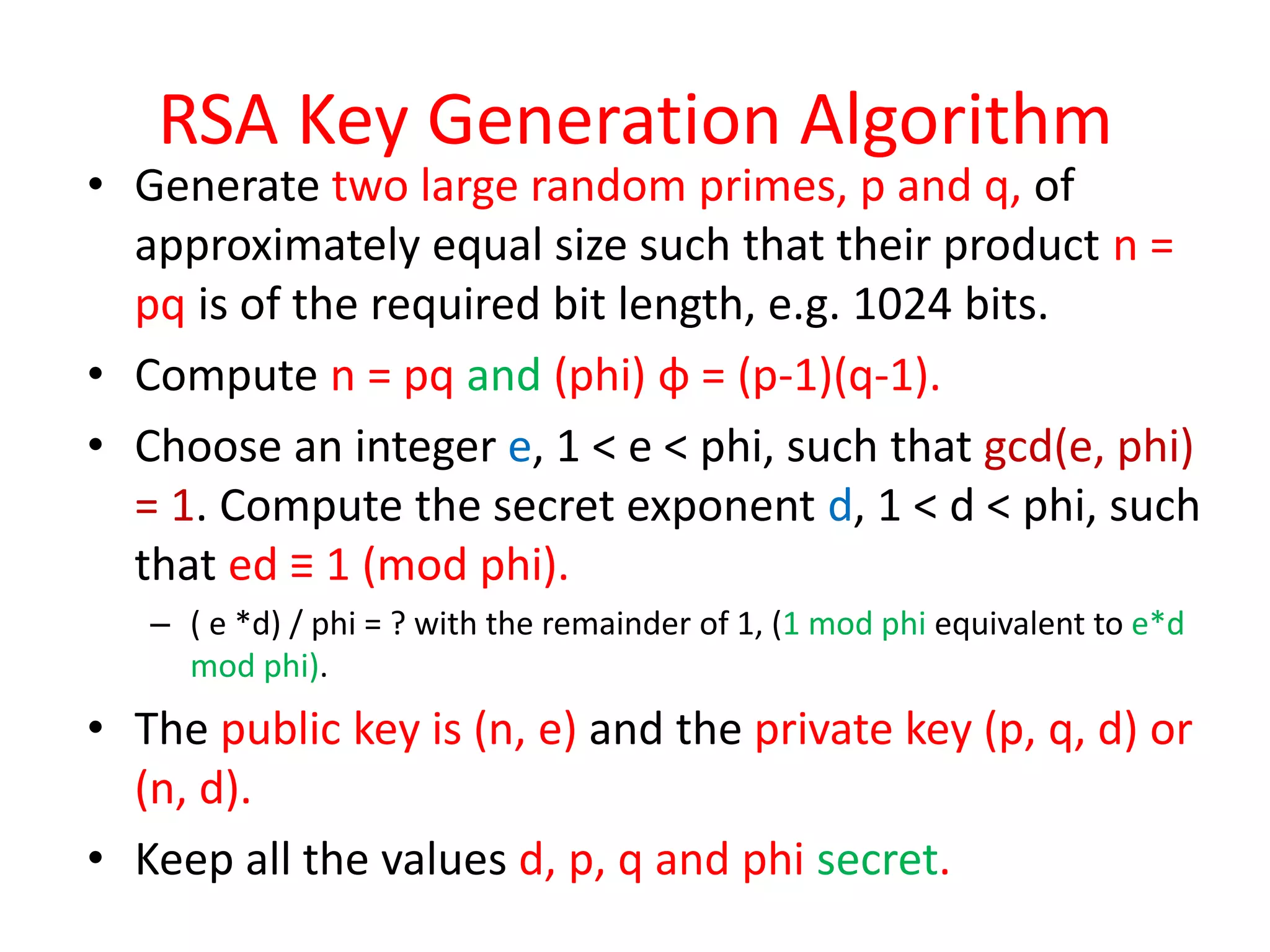
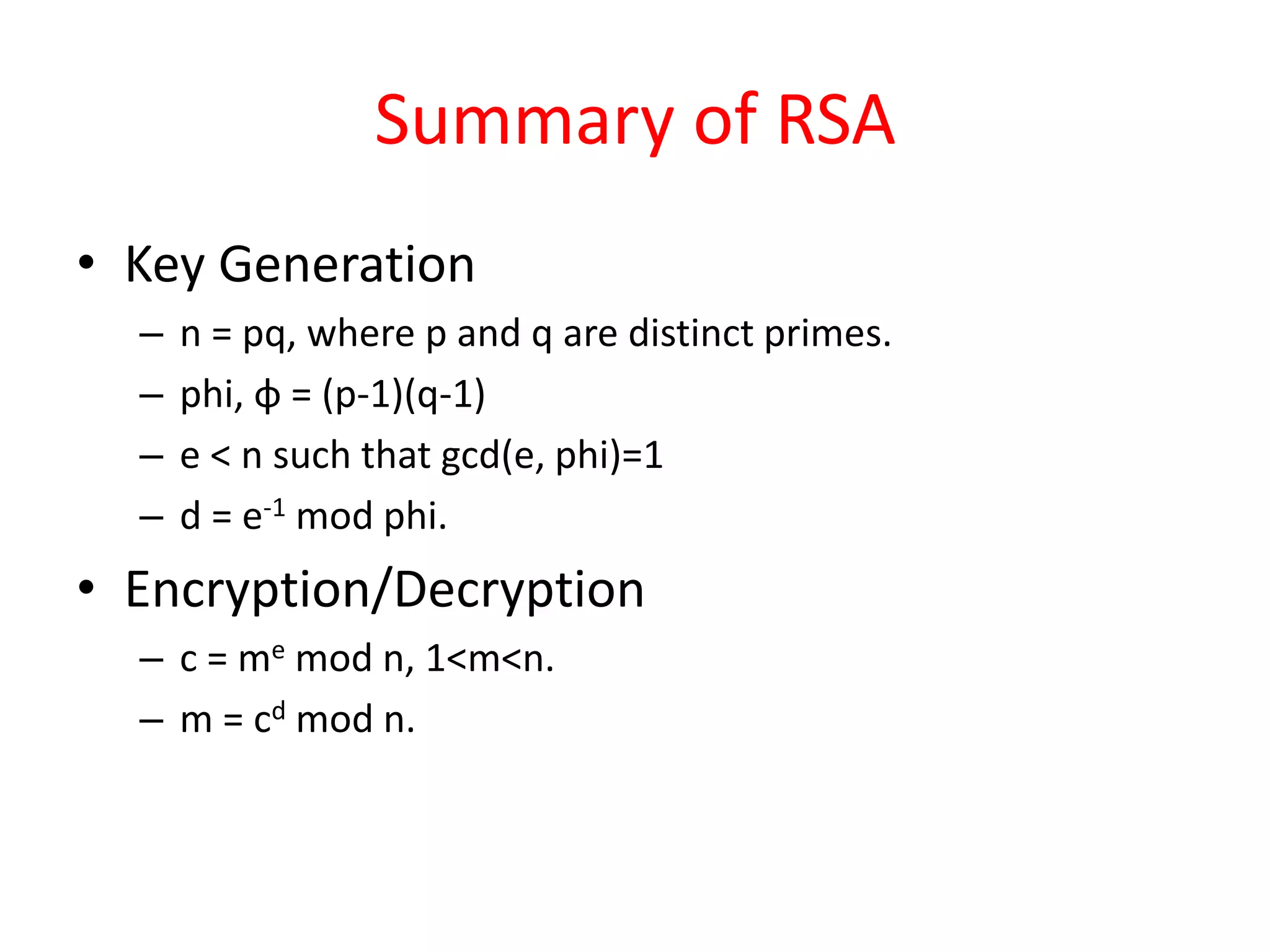
The document outlines a lecture on network security focusing on symmetric and asymmetric encryption techniques, specifically the Caesar cipher and RSA algorithm. It explains the mechanics of the Caesar cipher, its vulnerabilities, and provides a detailed overview of the RSA algorithm, including key generation, encryption, and decryption processes. Additionally, it includes examples and a homework assignment to apply the techniques learned in the lecture.