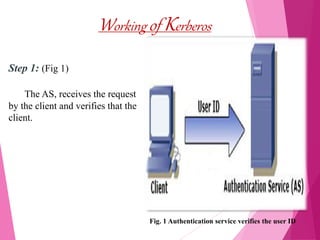
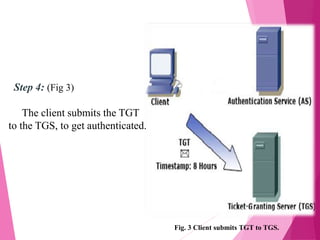
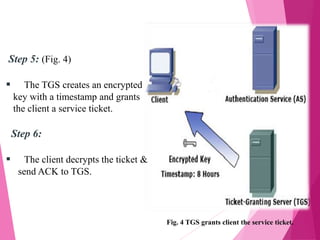
This document discusses the Kerberos authentication protocol. It provides a high-level overview of Kerberos, including its history, terminology, working, environment, database, and administrator. Kerberos provides strong authentication for physically insecure networks using trusted third parties and time-stamped tickets. While it ensures passwords are not sent in the clear, Kerberos is vulnerable if users choose poor passwords and relies on all machines being designed for its authentication.