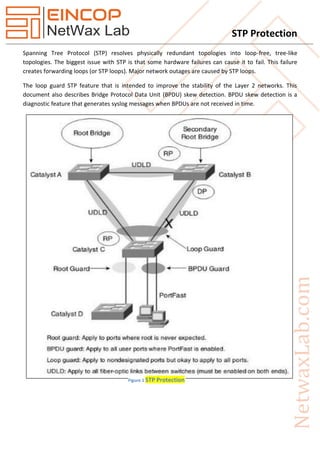
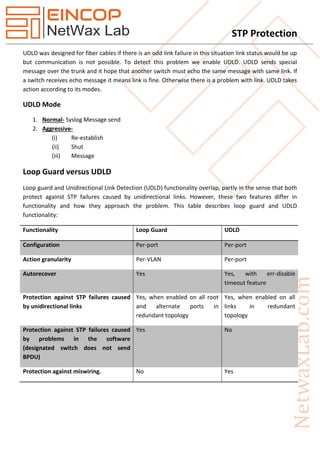
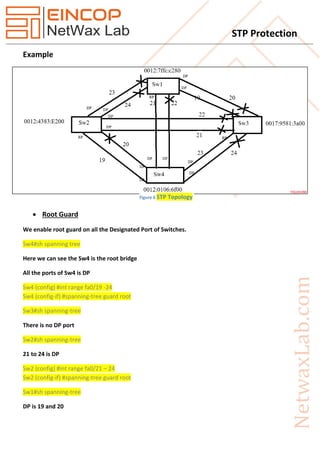
The document discusses the Spanning Tree Protocol (STP) and its features designed to ensure loop-free network topologies, such as loop guard and BPDU skew detection. It outlines how these mechanisms help prevent major network outages caused by hardware failures and loops. Additionally, the document details how to implement STP protection features like root guard, loop guard, BPDU guard, and UDLD to enhance network stability and security.