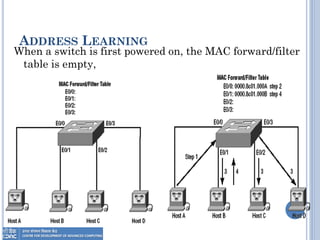
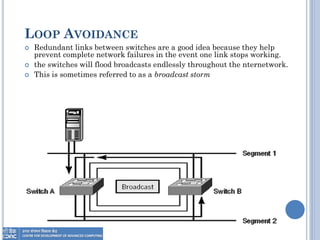
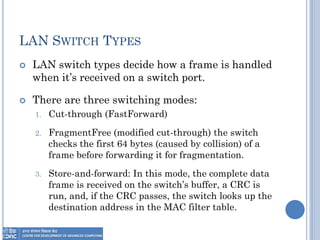
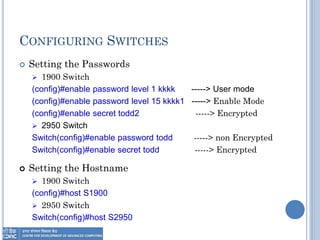
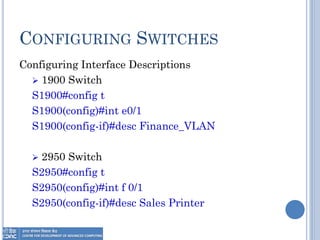
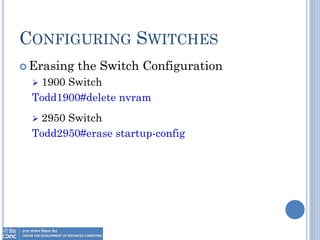
The document provides an overview of Layer 2 switching technology, primarily focusing on the operation and configuration of switches, including the Spanning Tree Protocol (STP) used for loop avoidance. It outlines the functions of switches such as address learning, frame forwarding, and loop prevention, and describes key terms and concepts related to STP. Additionally, it includes instructions for configuring switch settings and interfaces, along with commands for various switch types.