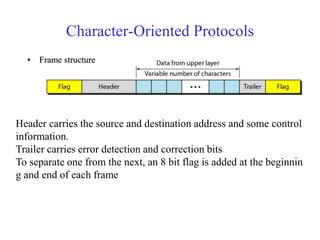
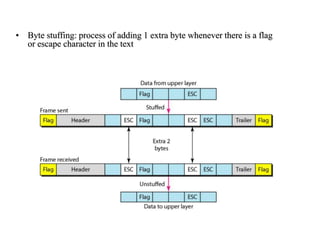
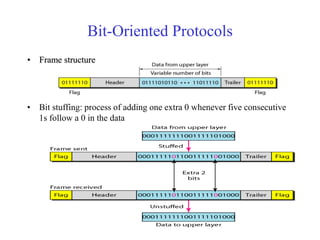
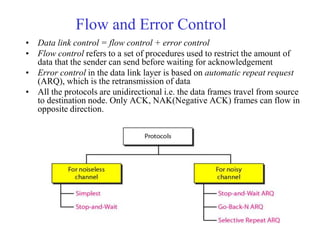
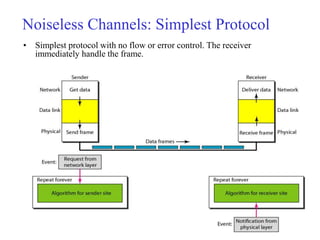
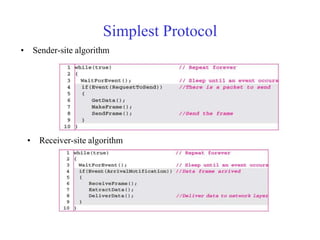
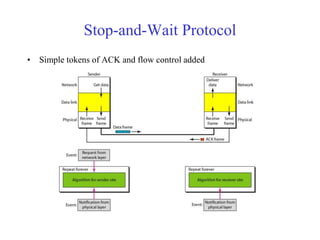
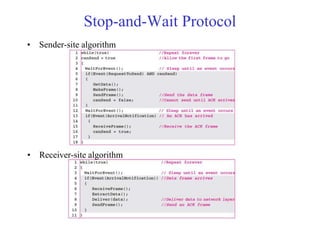
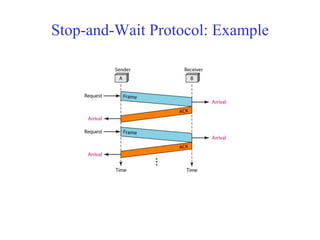
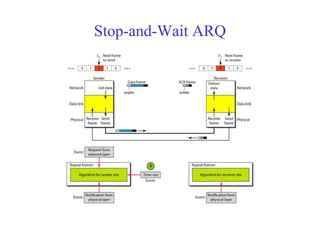
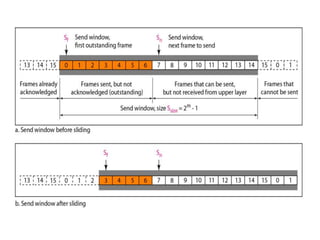
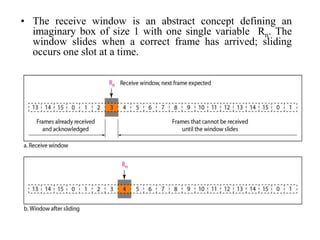
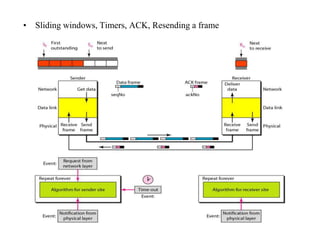
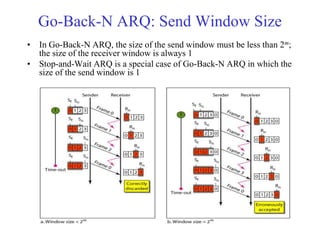
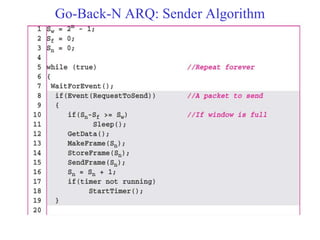
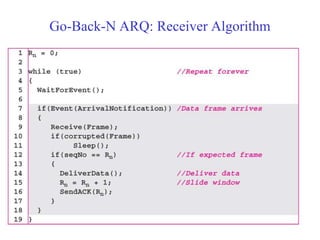
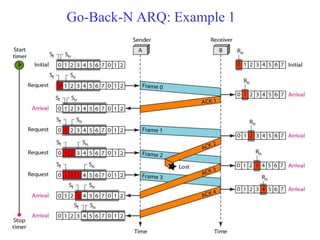
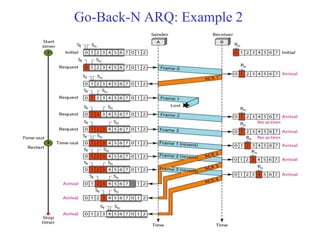
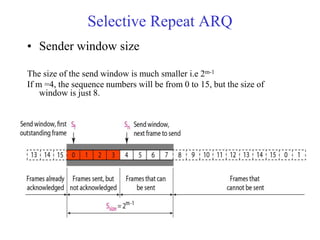
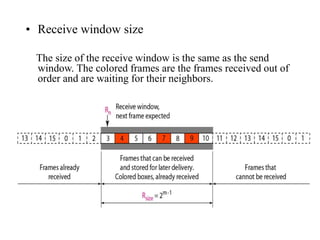
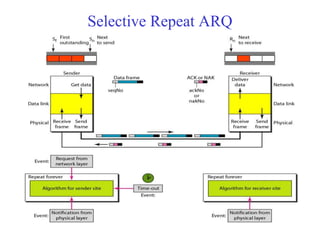
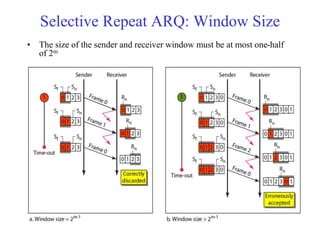
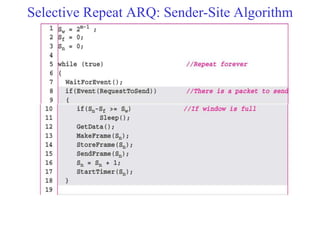
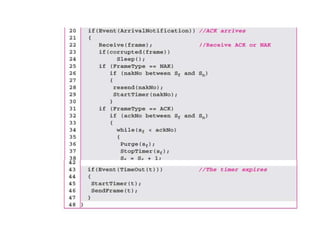
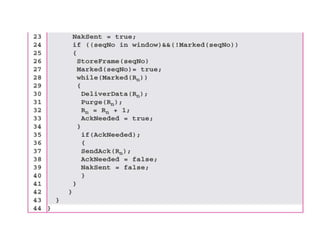
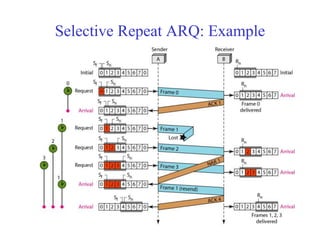
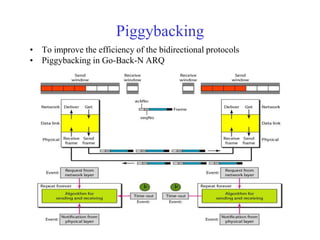
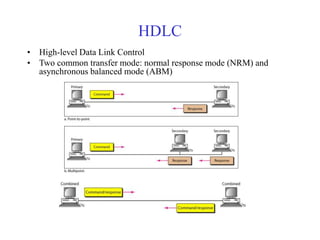
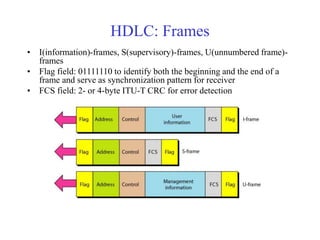
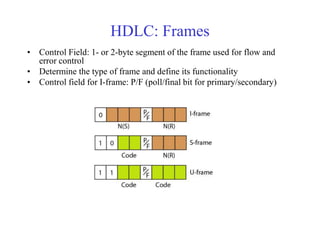
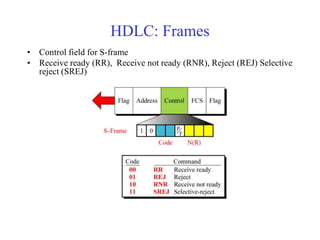
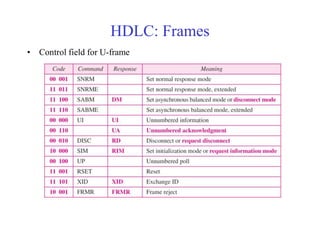
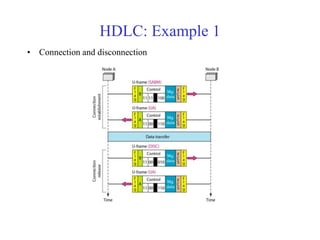
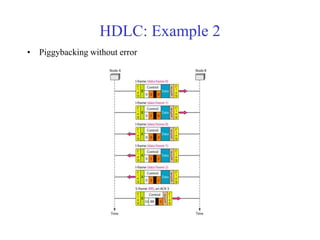
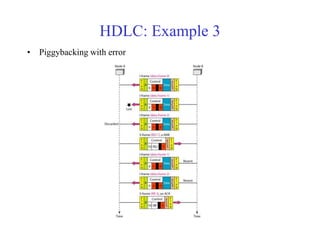
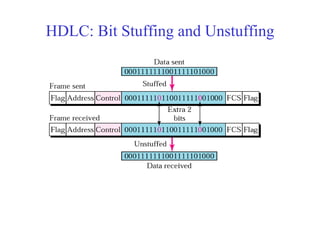
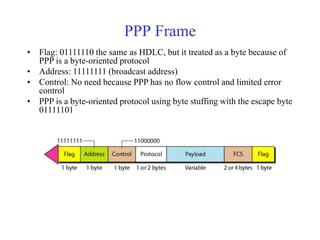
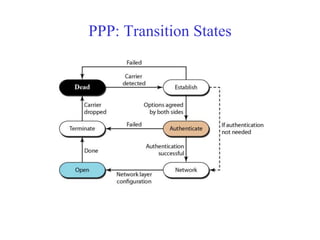
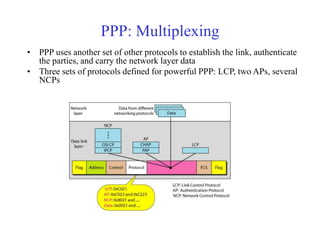
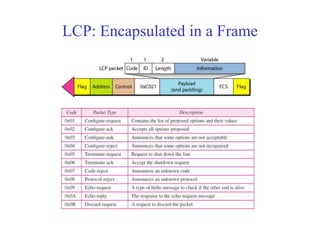
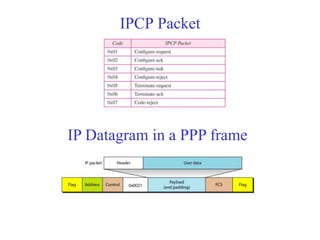
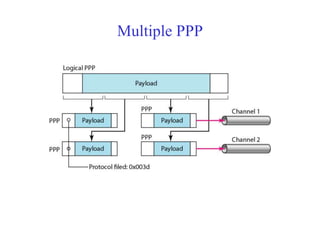
Data link control involves framing data, flow and error control, and common protocols like HDLC and PPP. Framing involves adding source/destination addresses to frames for transmission. Flow control restricts how much data the sender sends before waiting for acknowledgment. Error control uses techniques like automatic repeat request to retransmit lost data frames. HDLC and PPP are protocols that define frame formats and control procedures for point-to-point links.