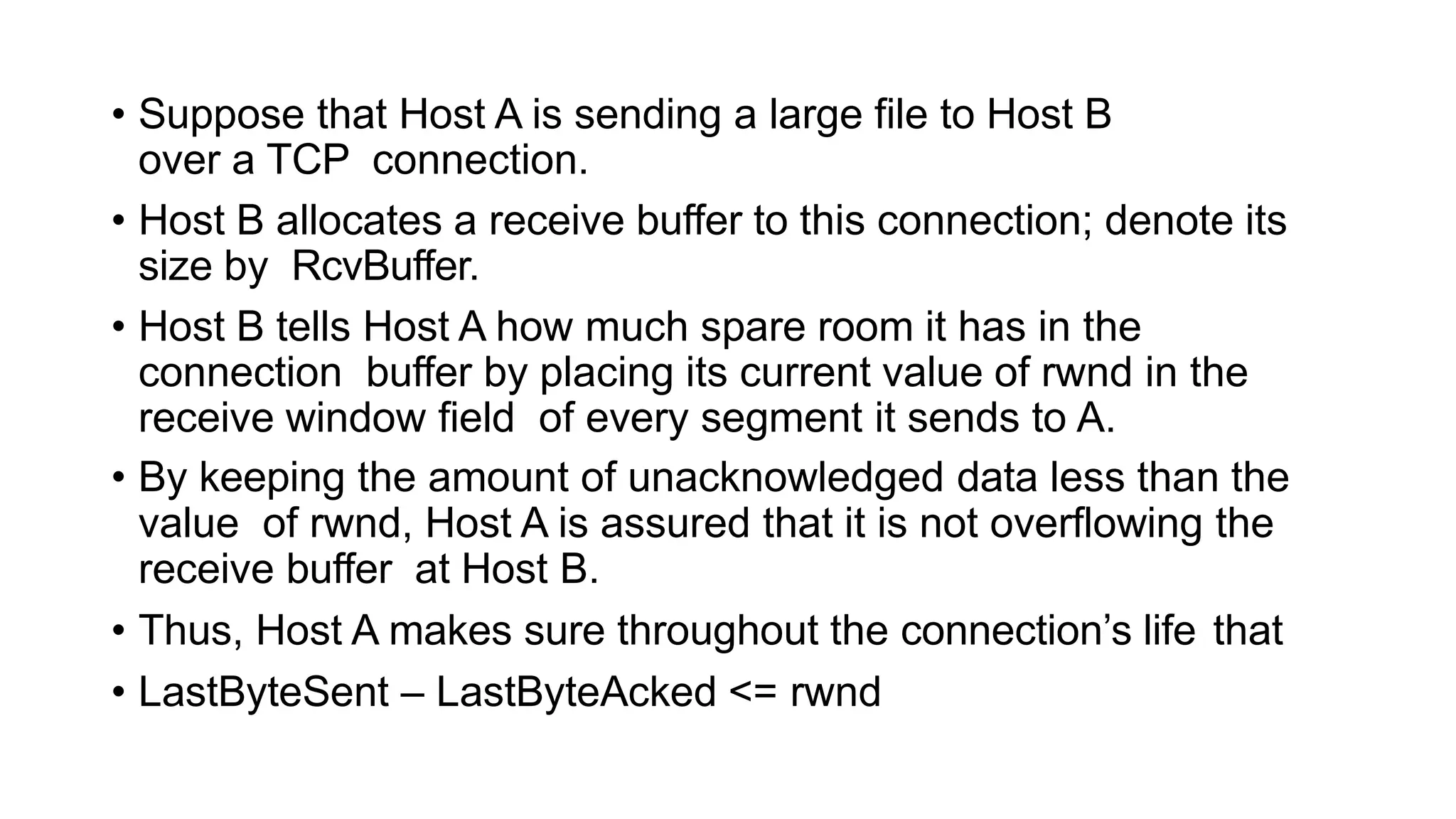
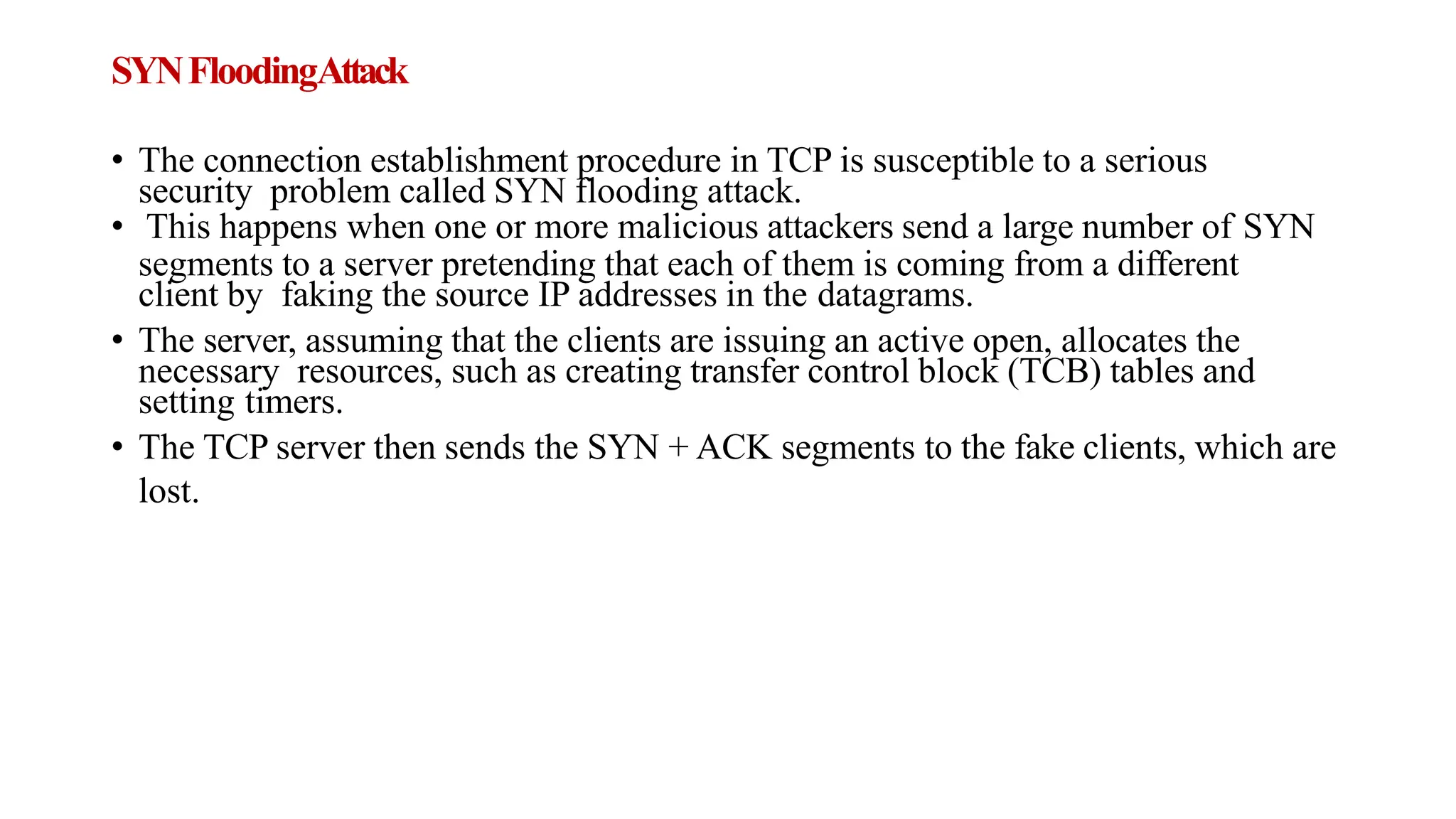
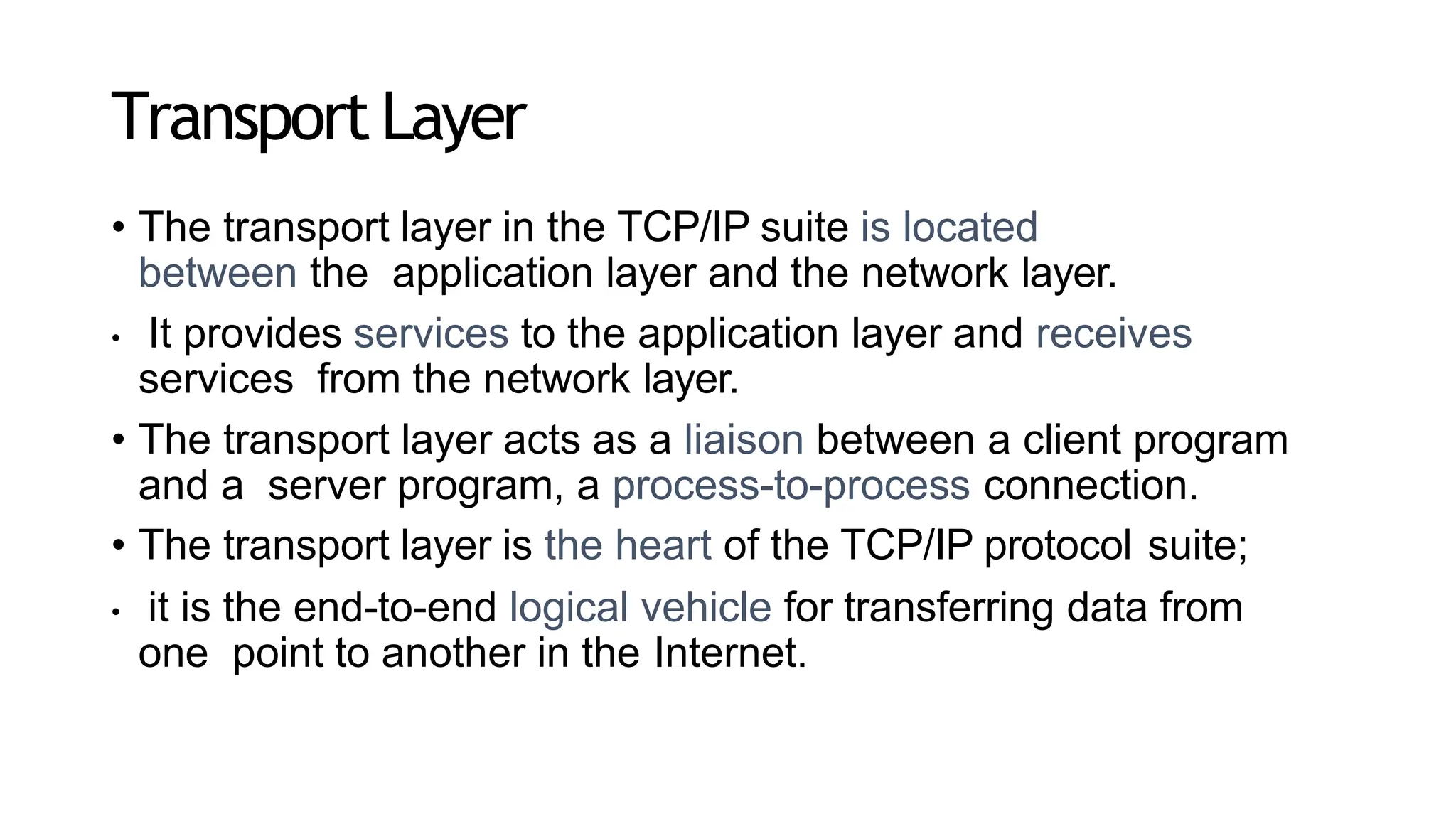
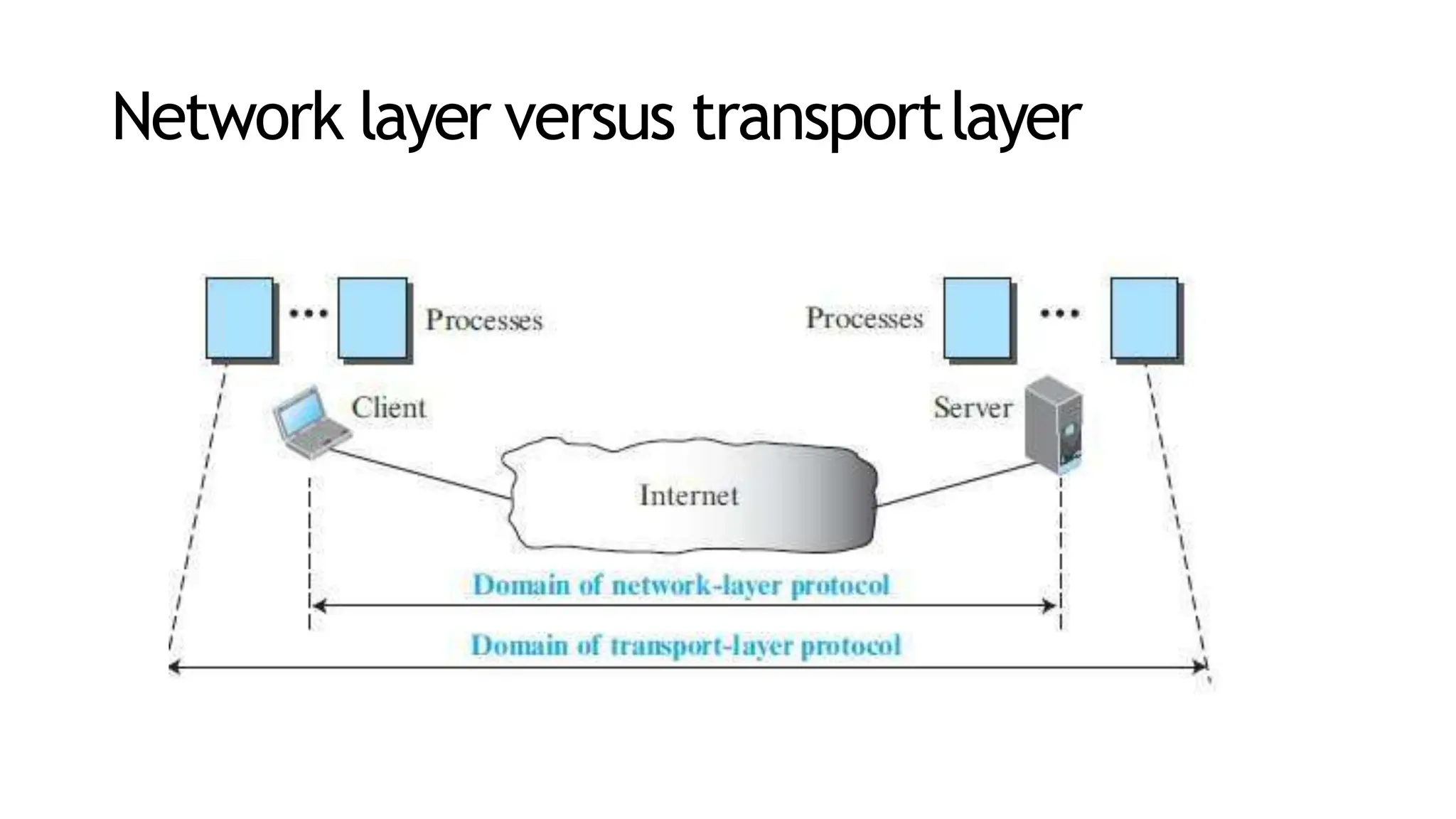
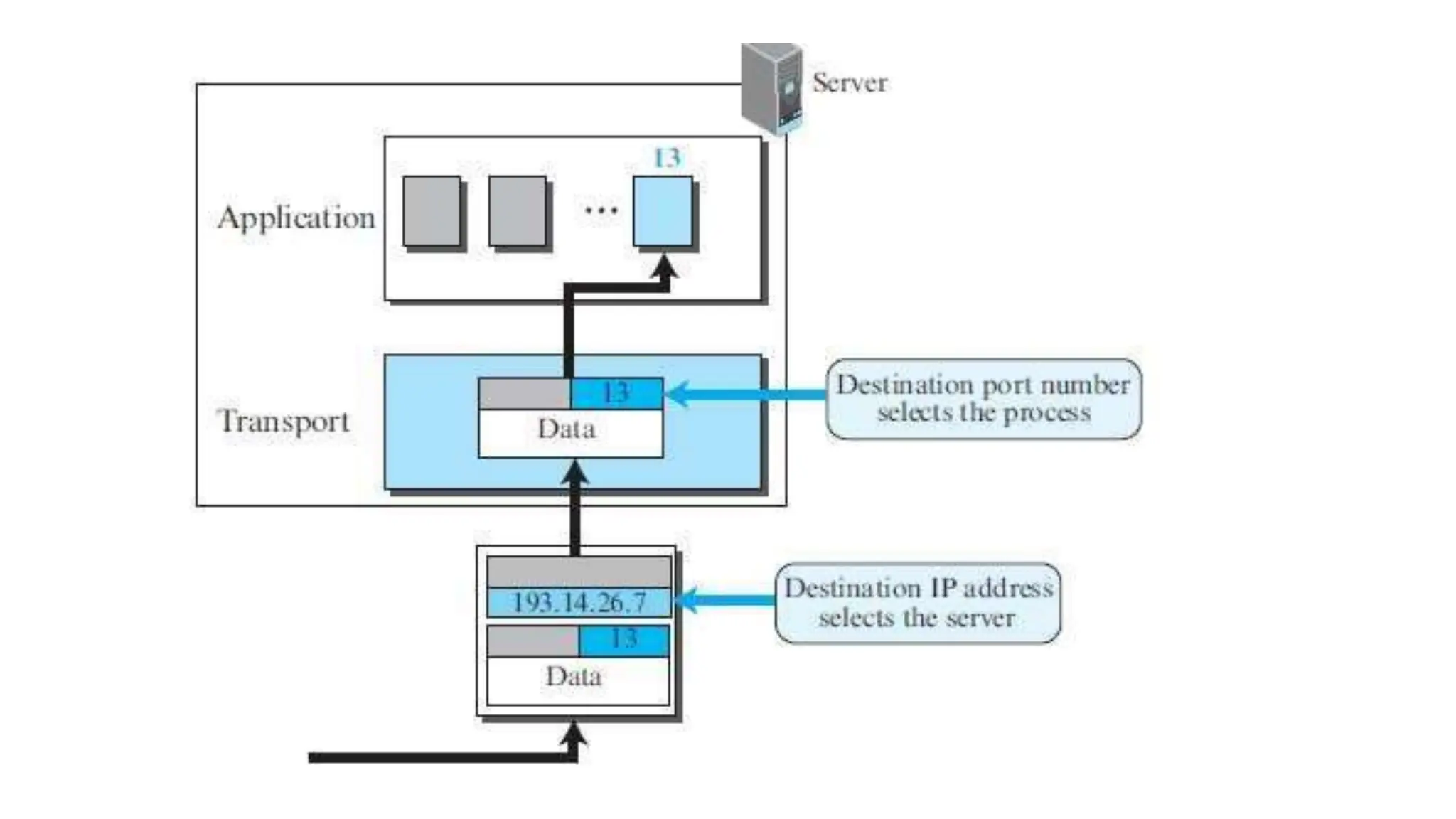
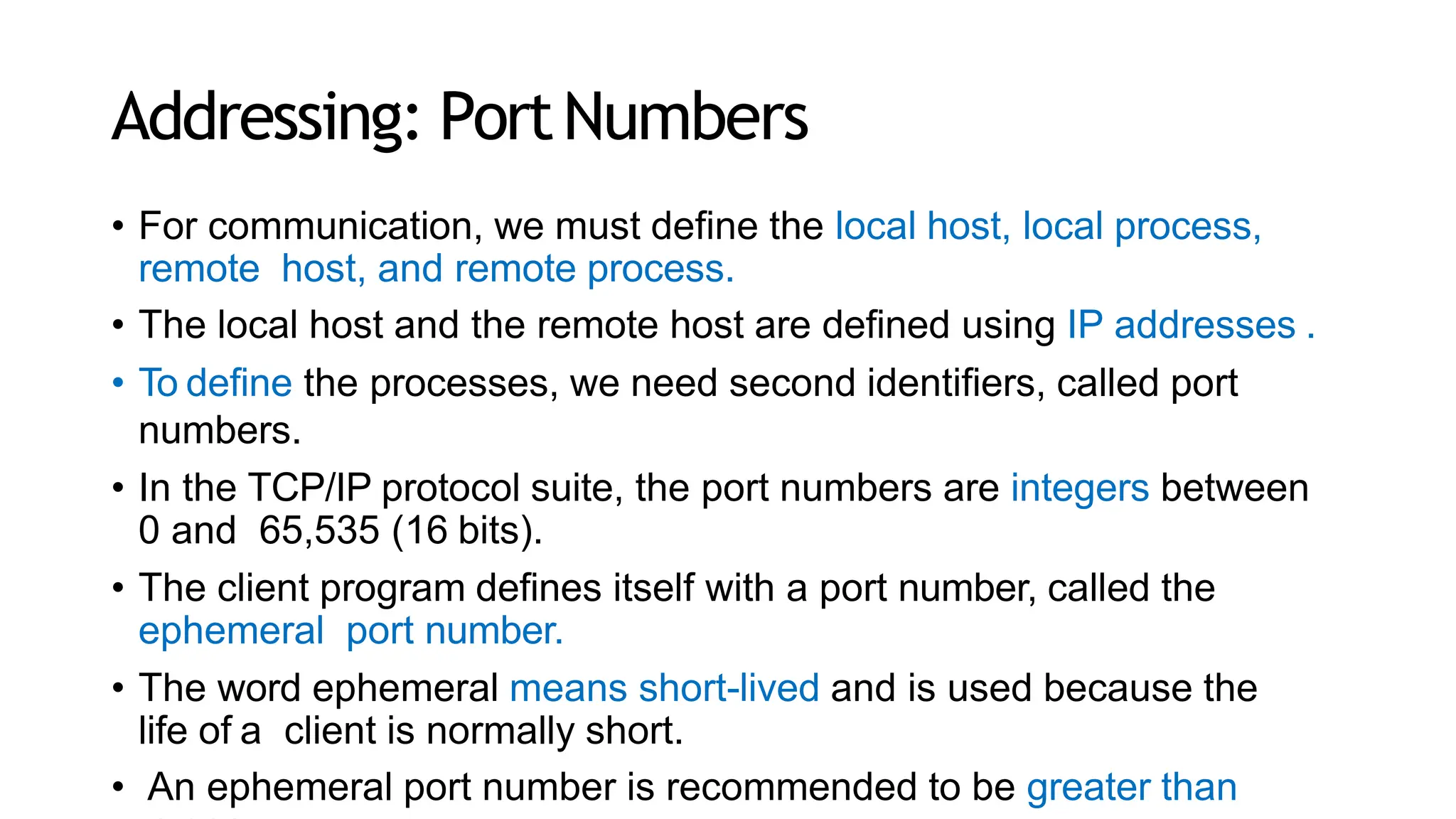
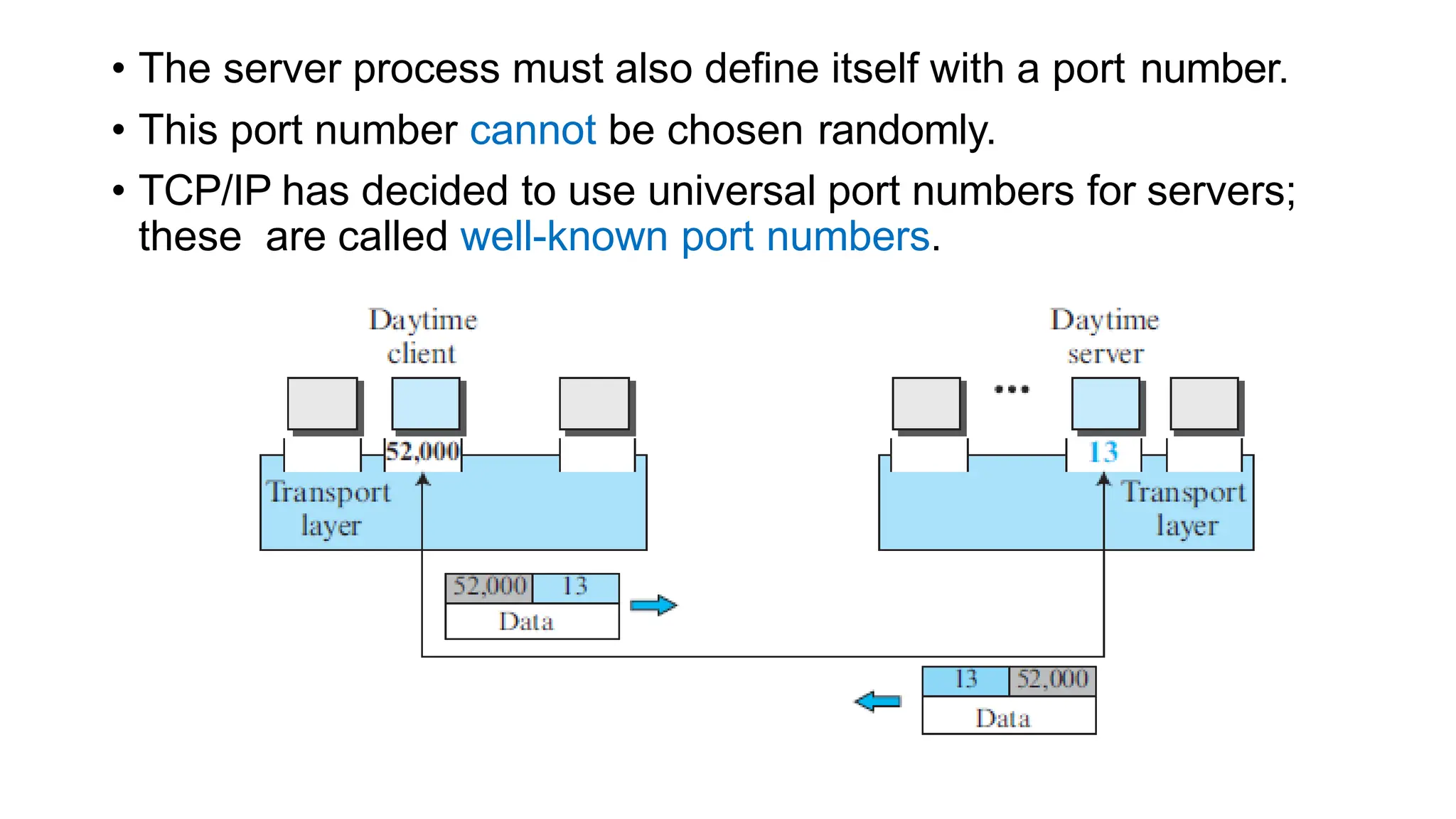
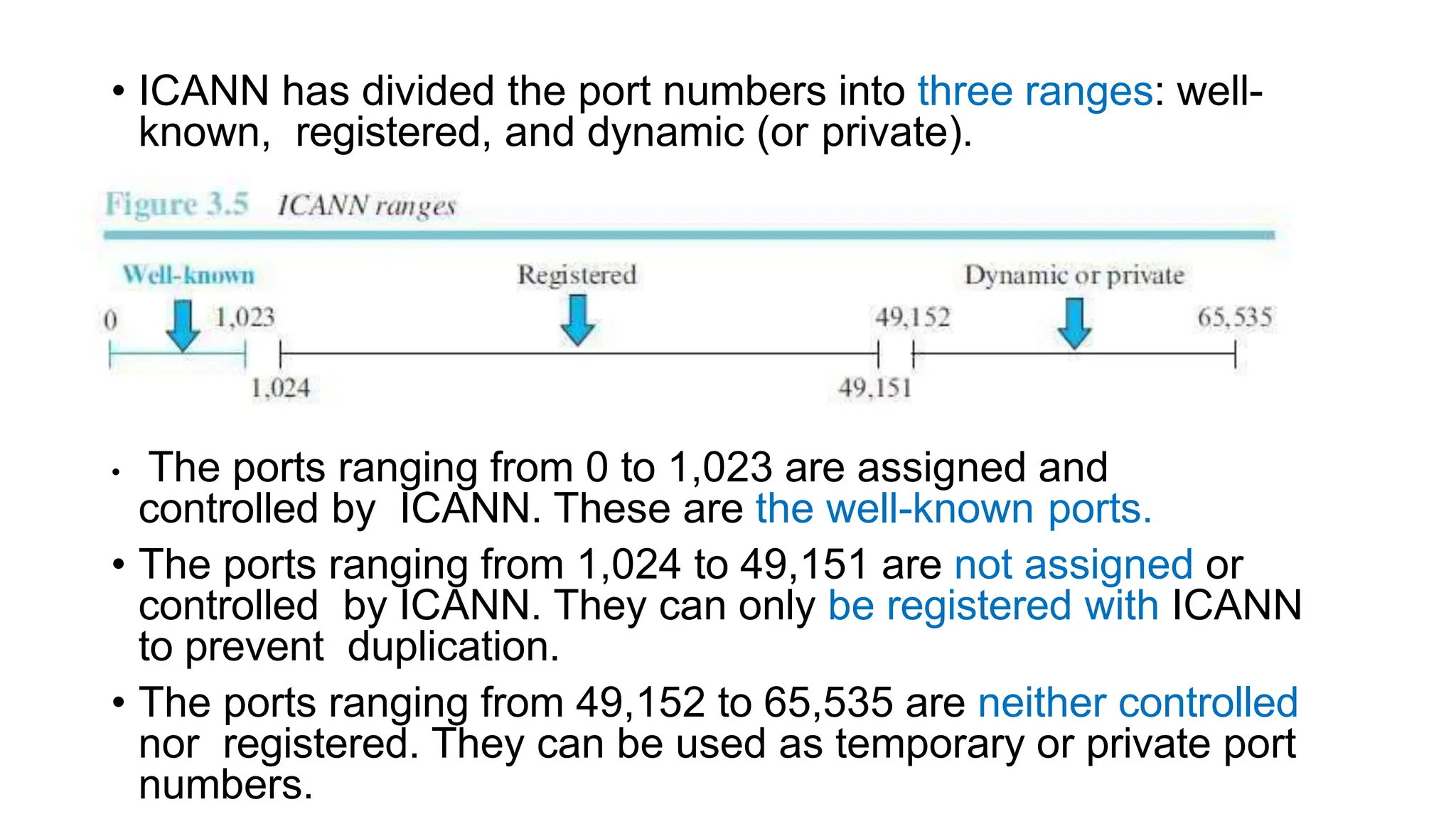
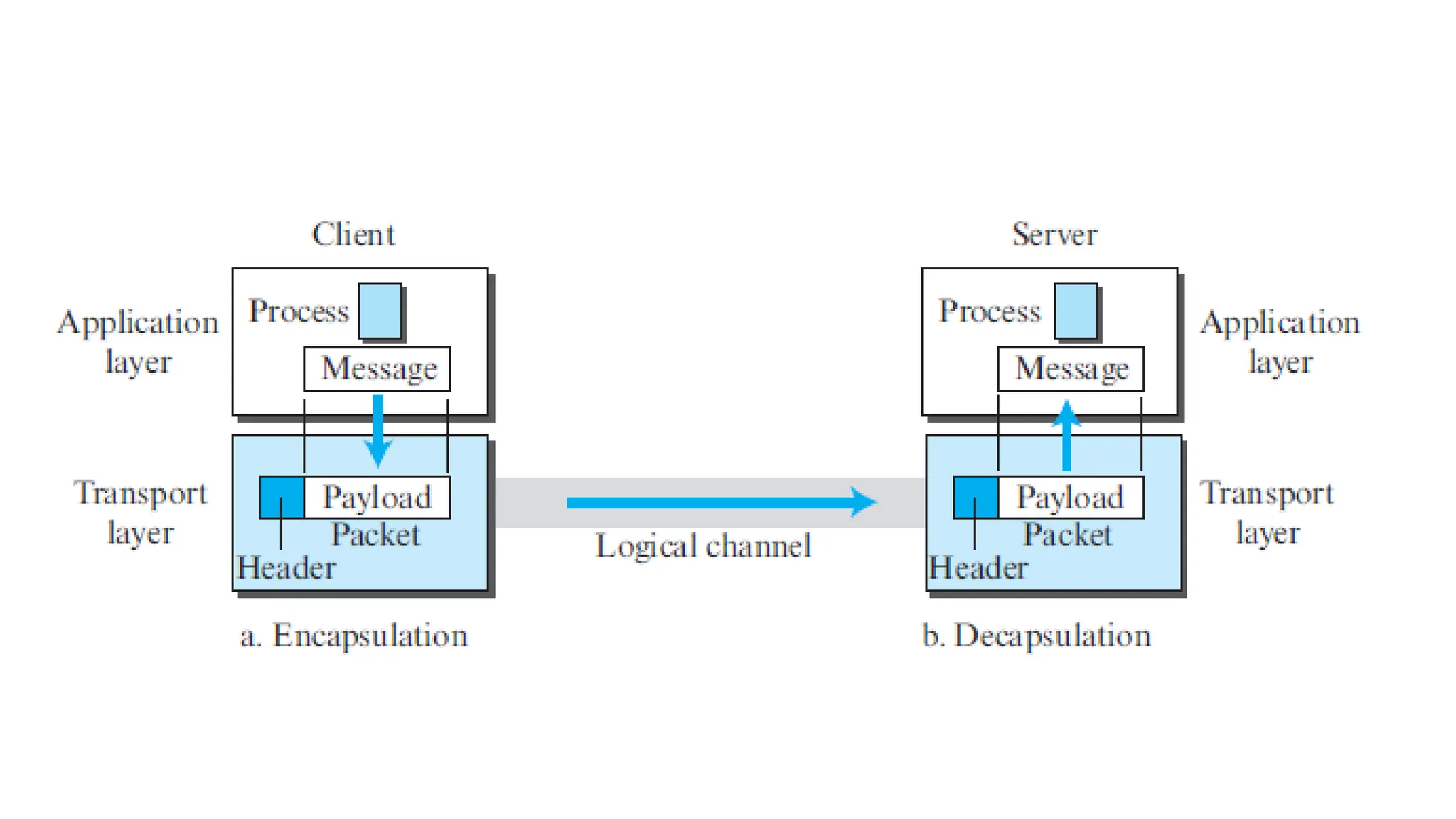
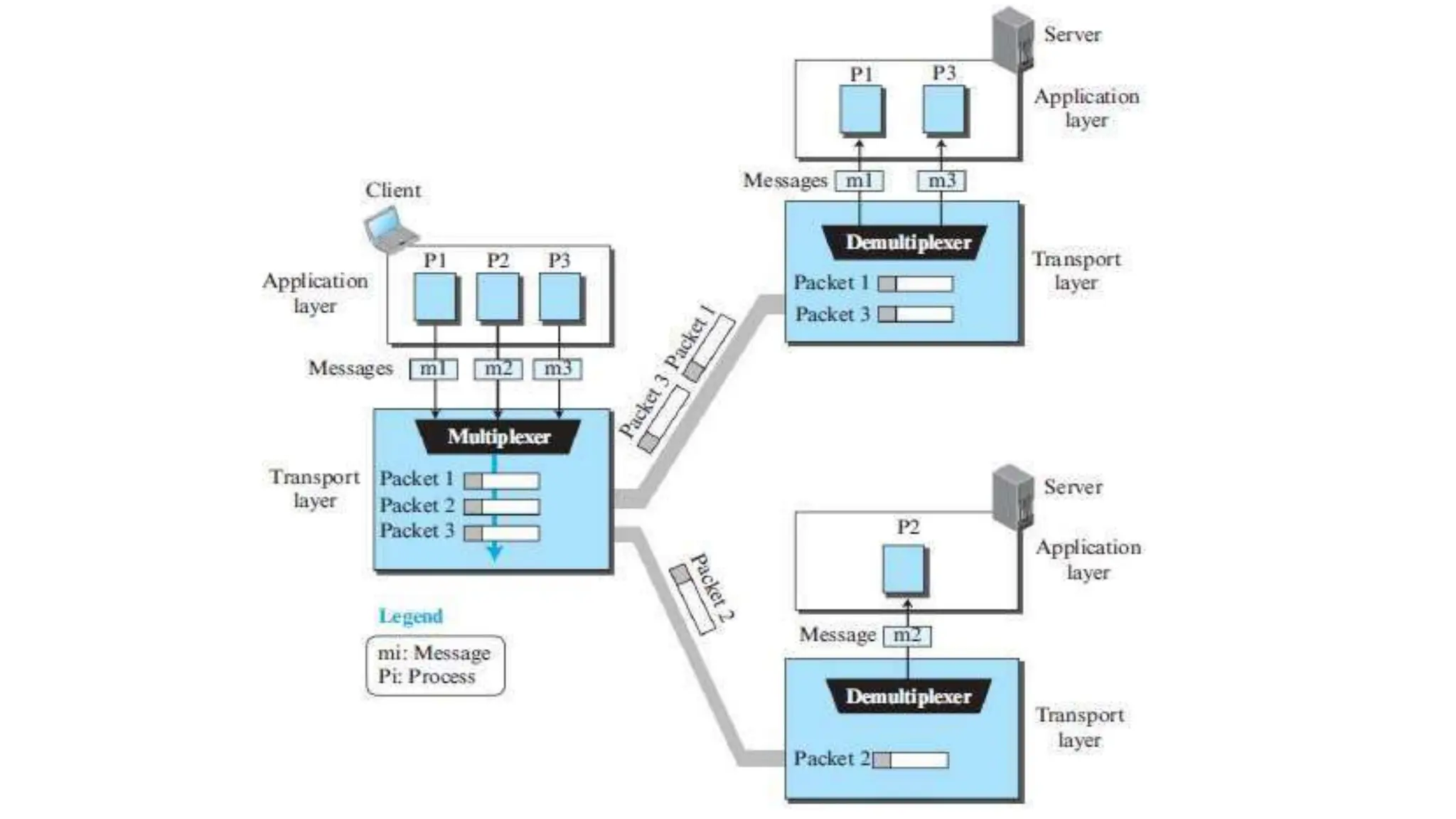
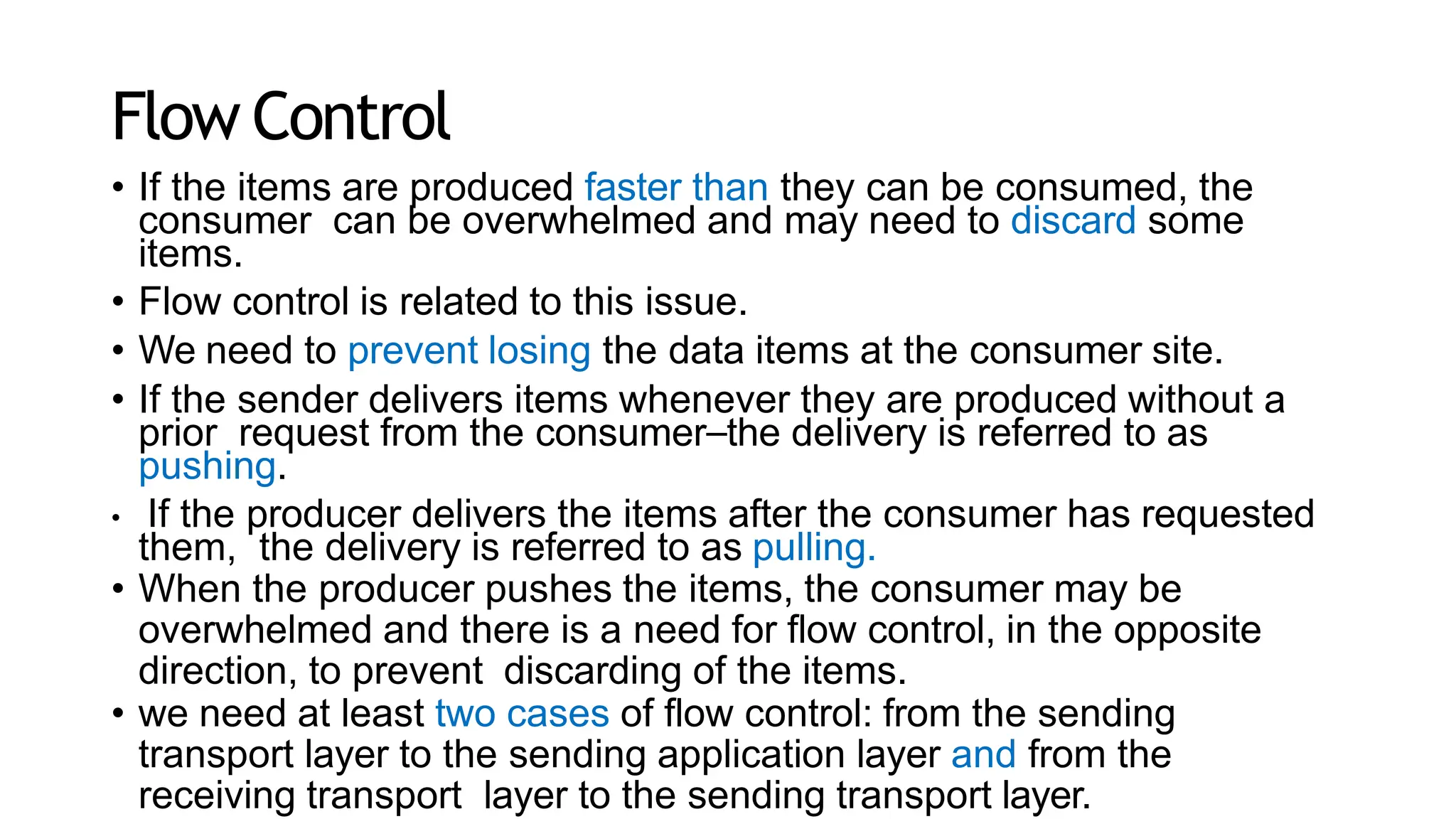
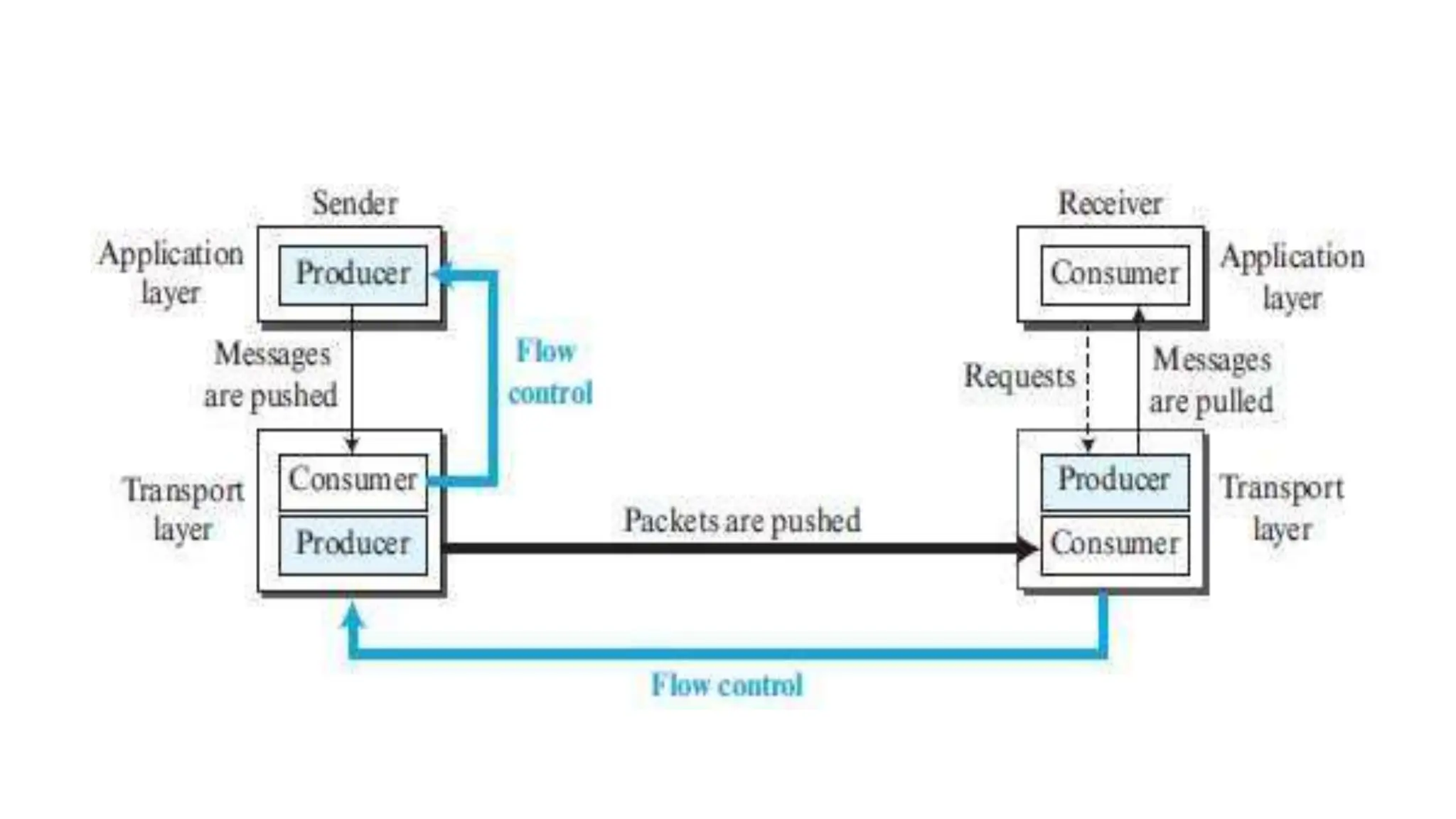
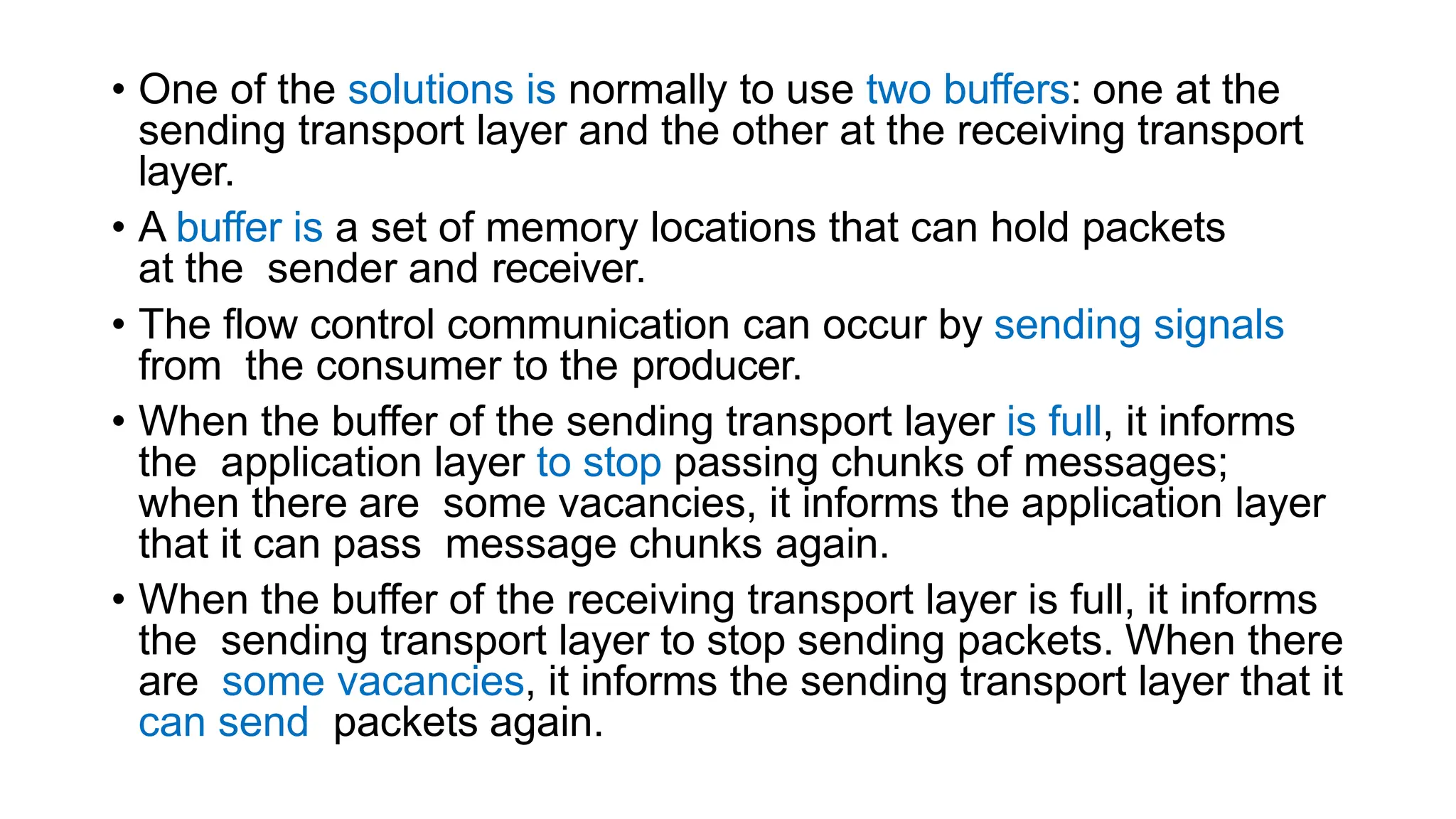
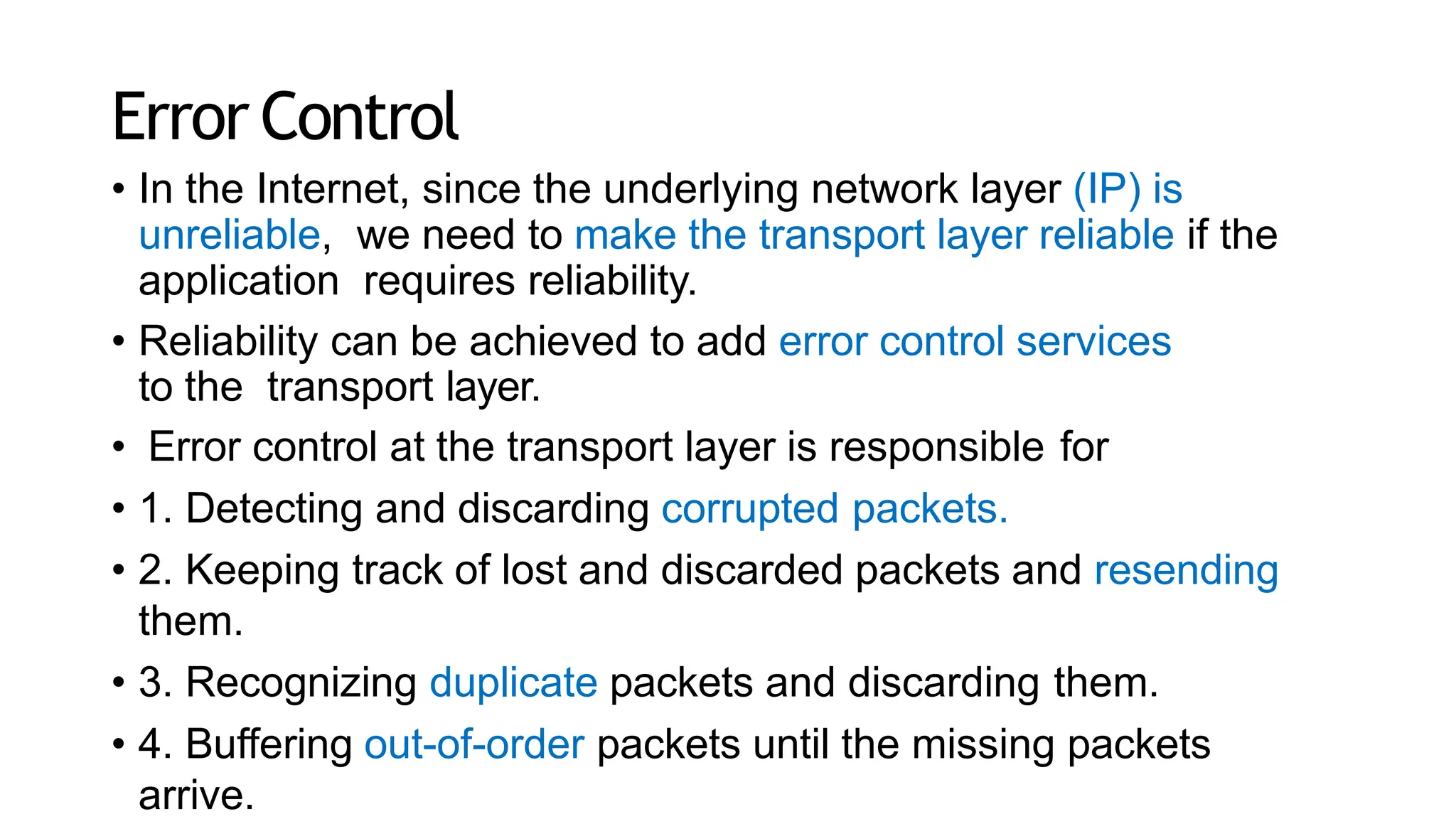
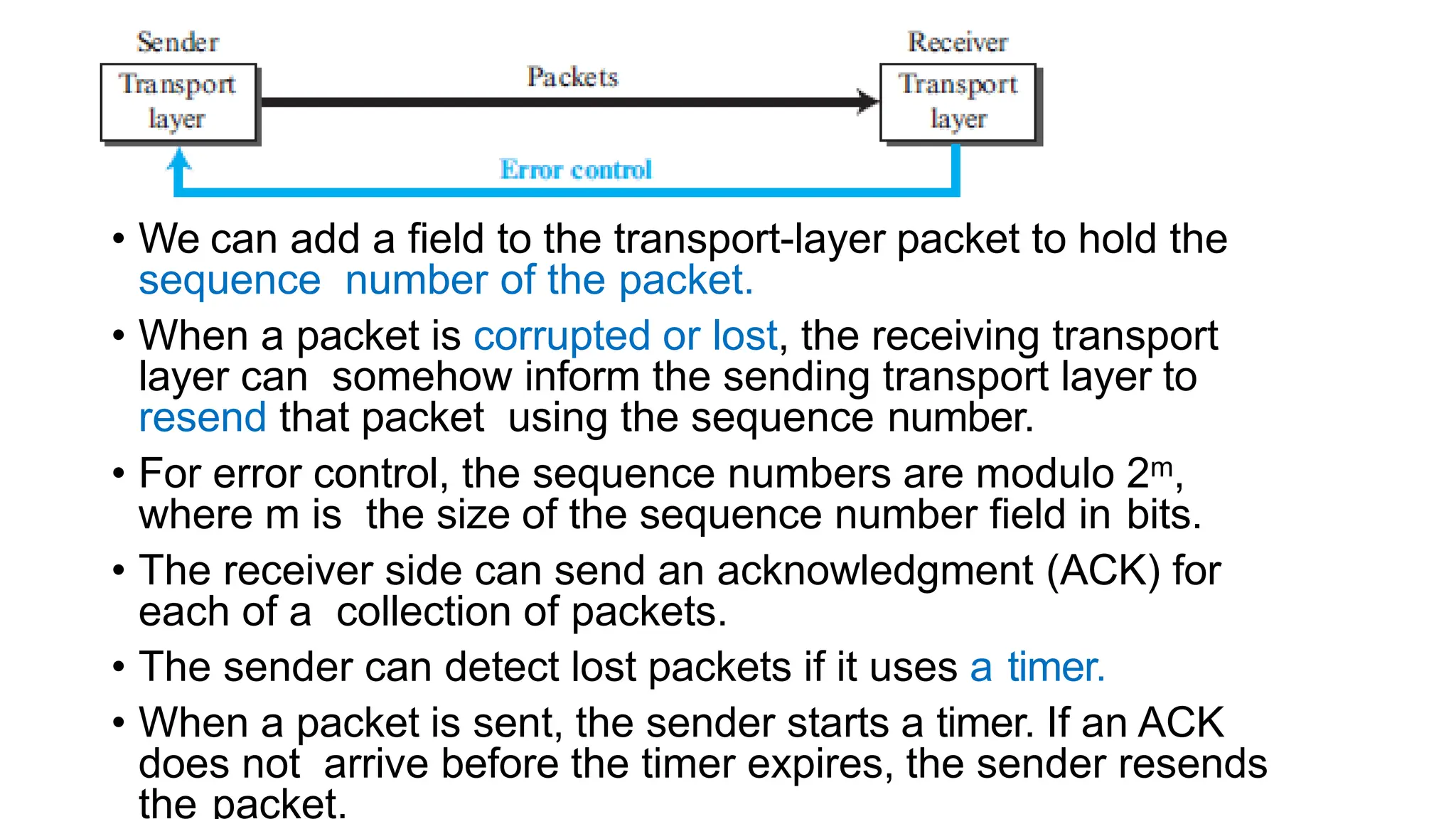
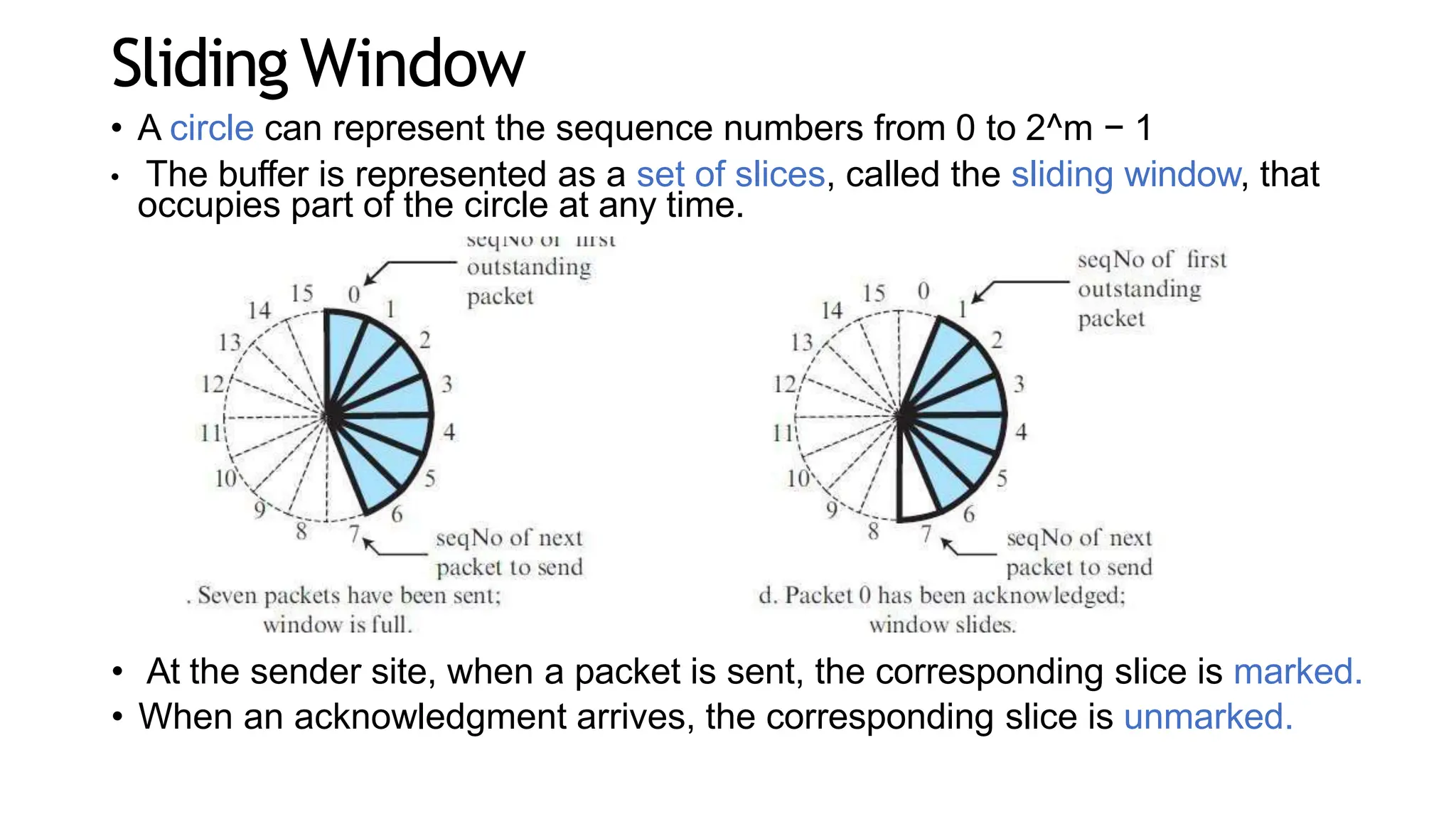
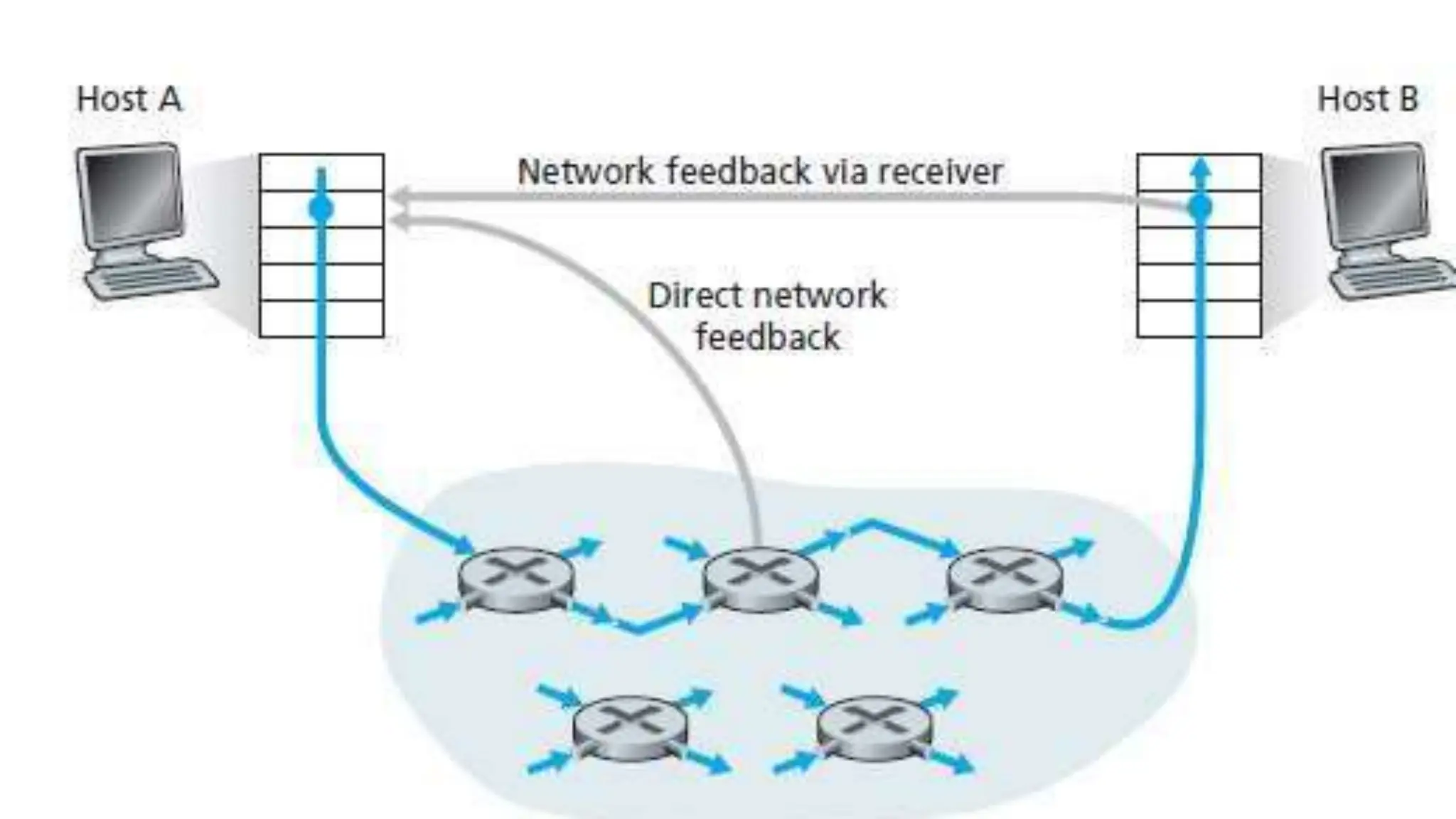
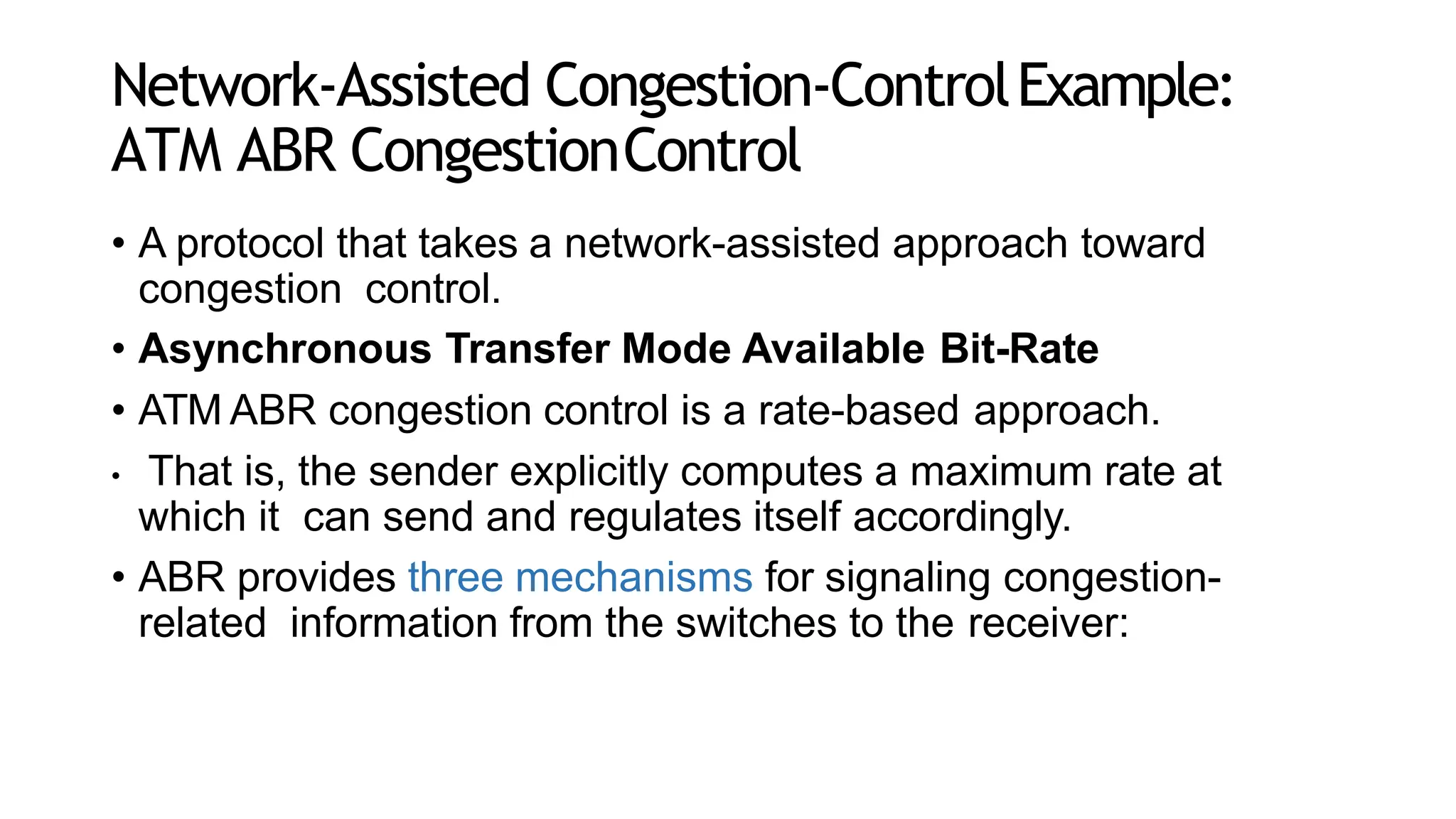
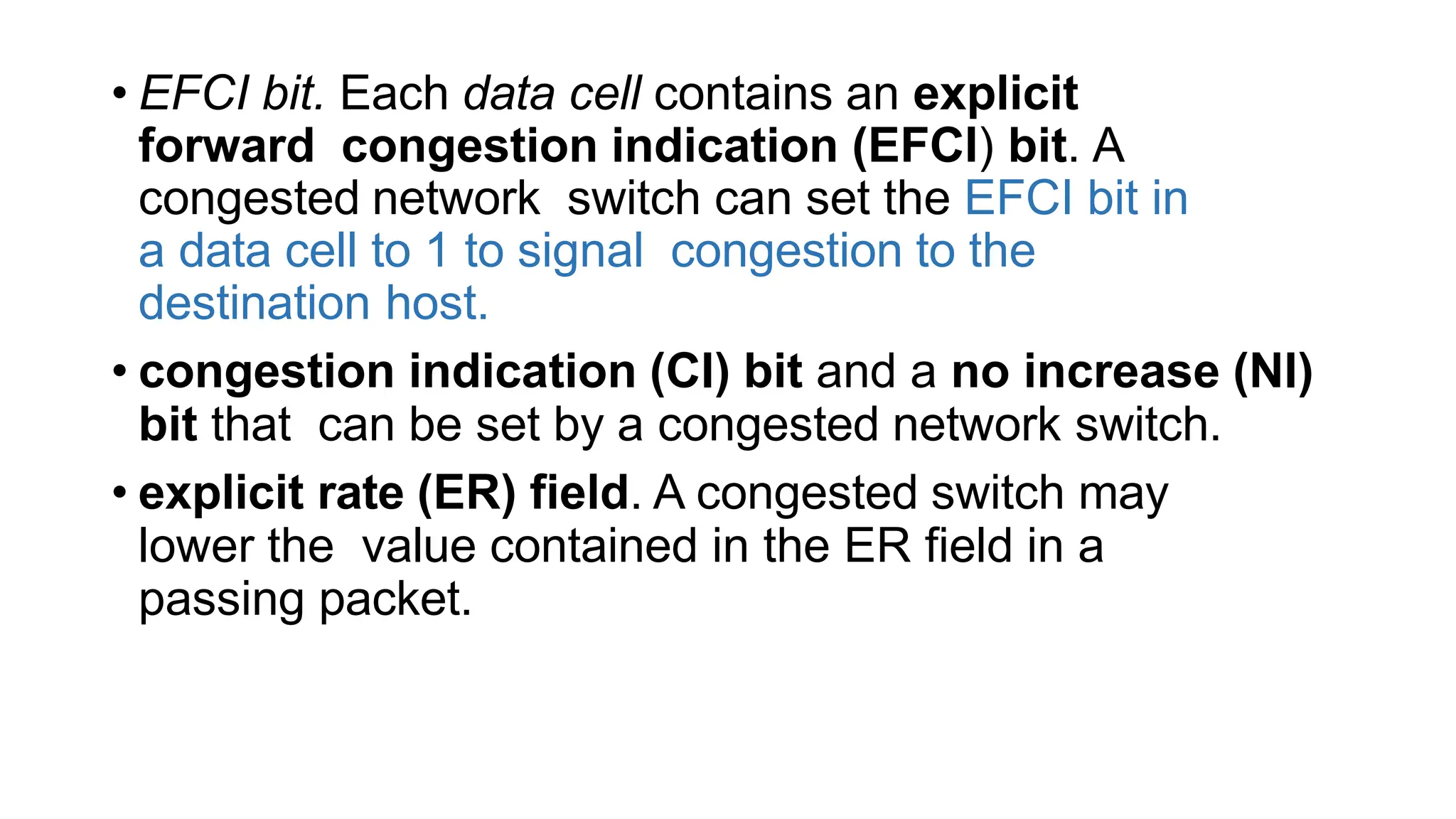
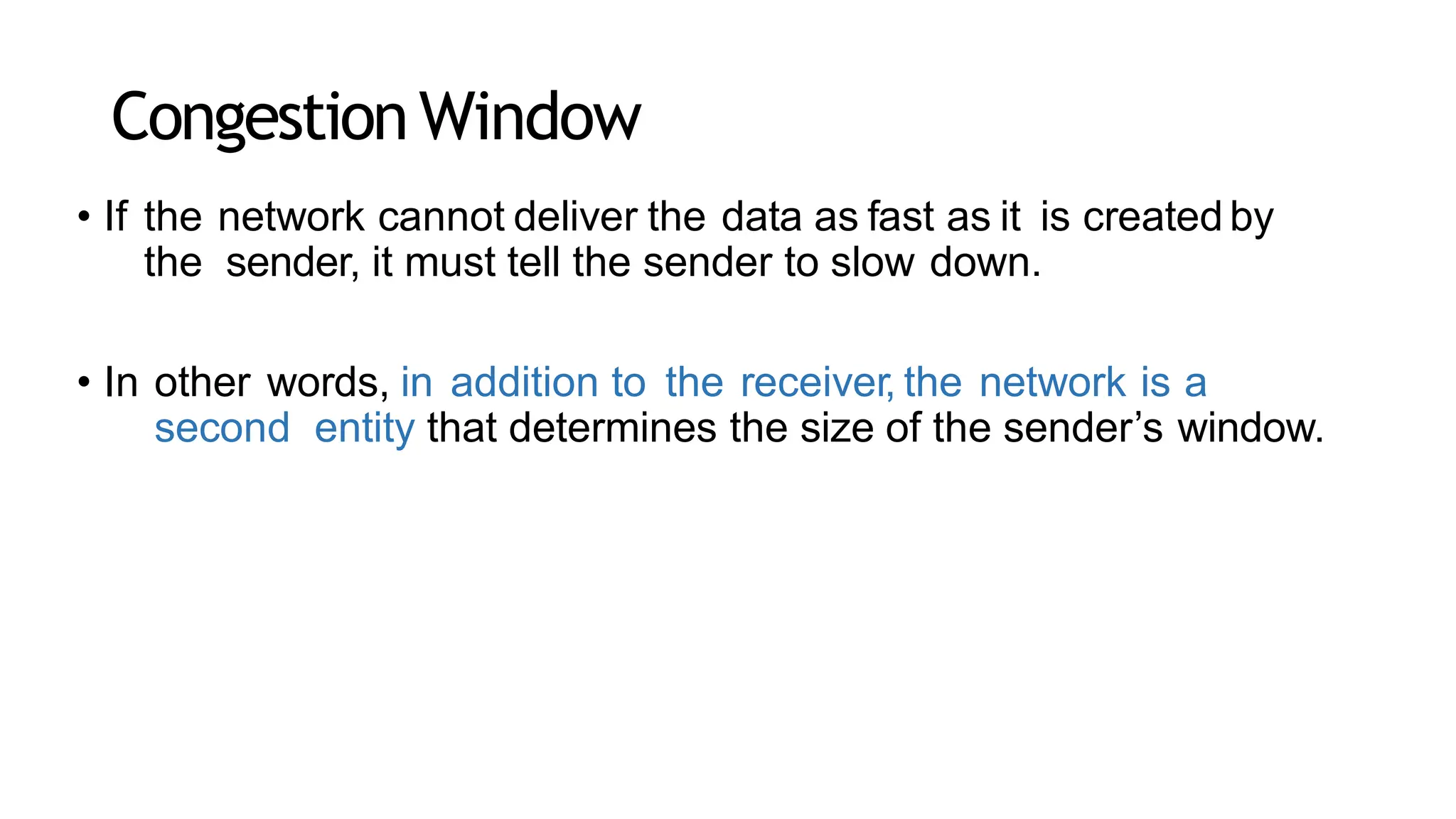
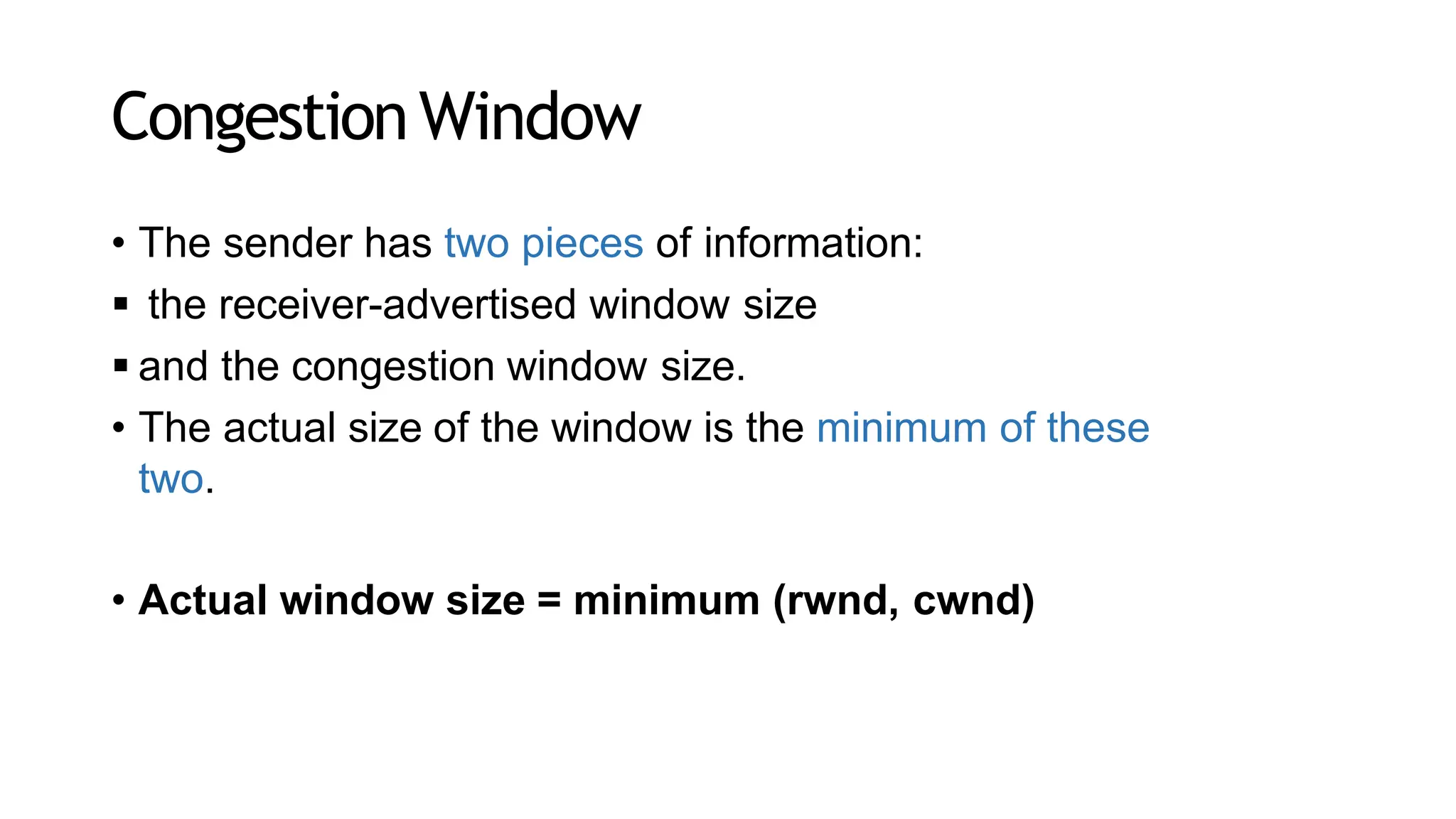
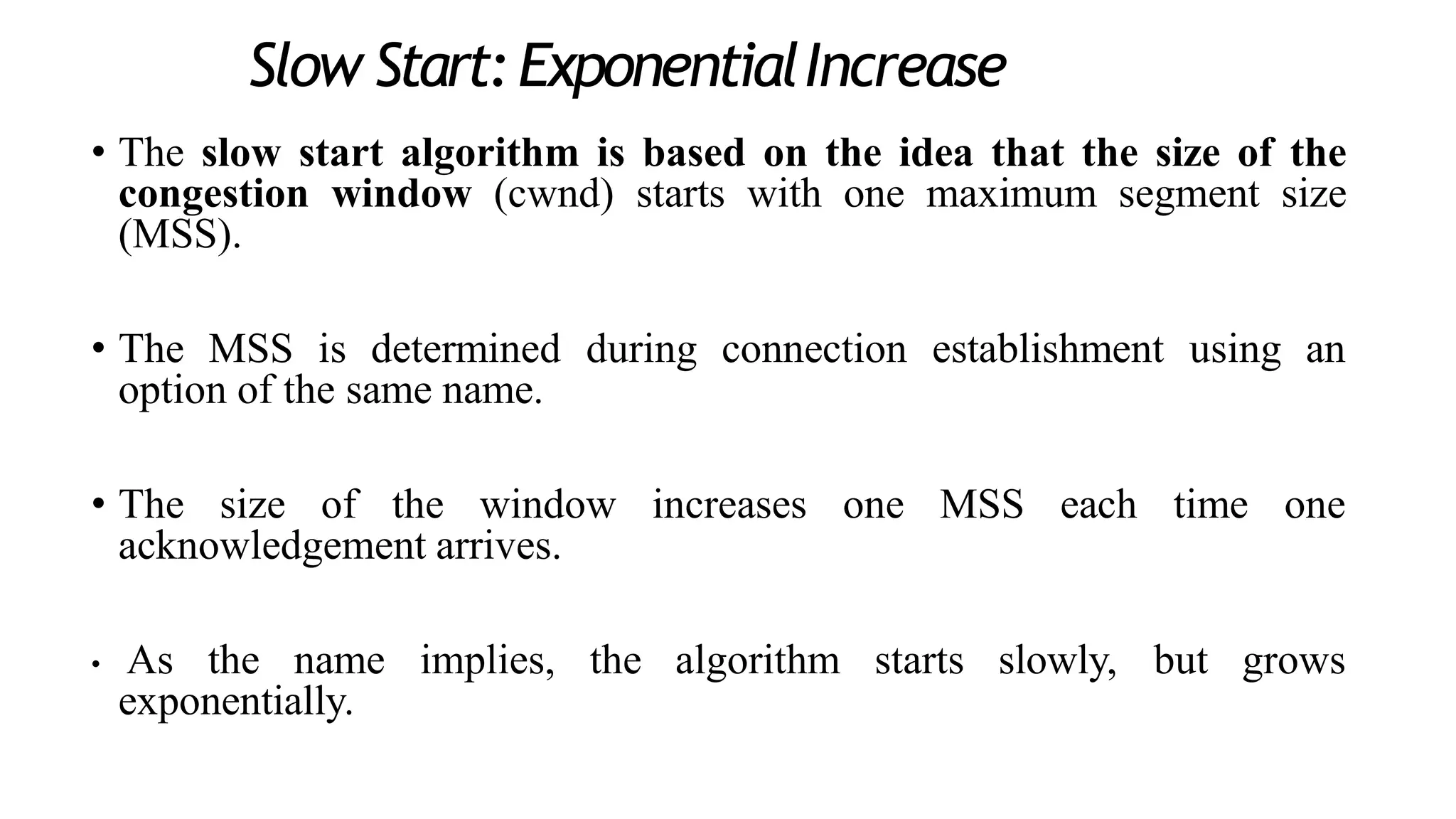
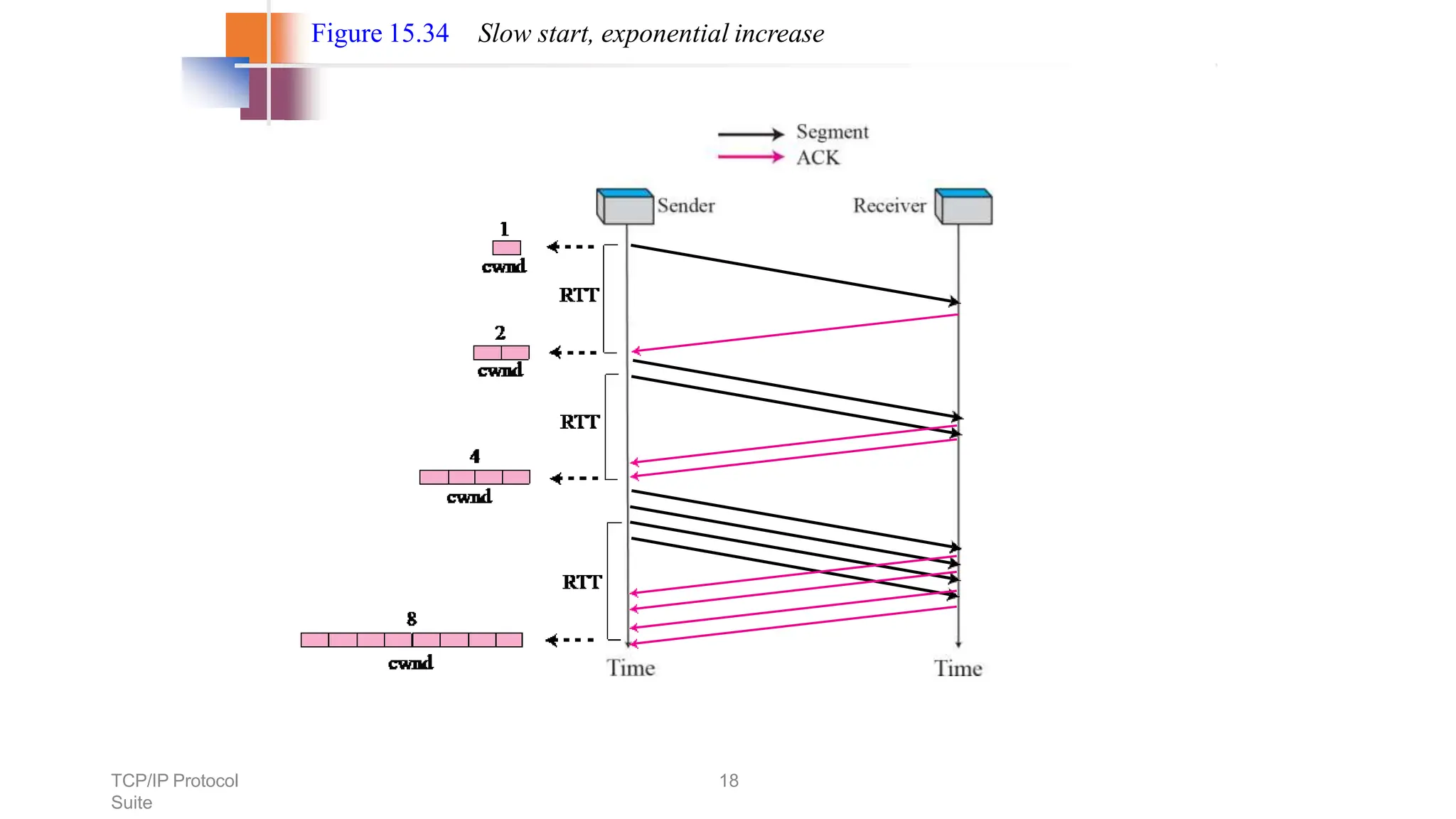
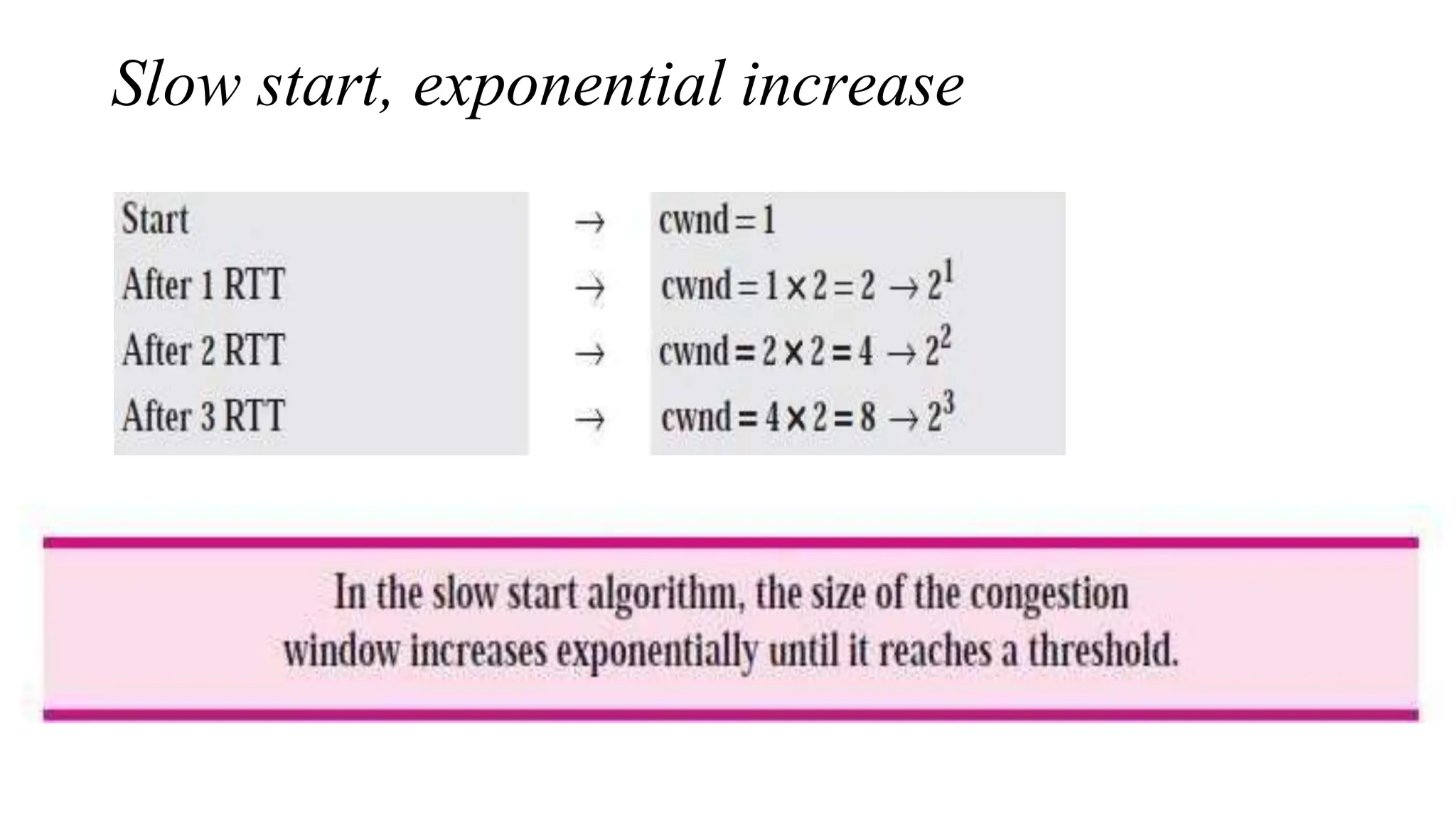
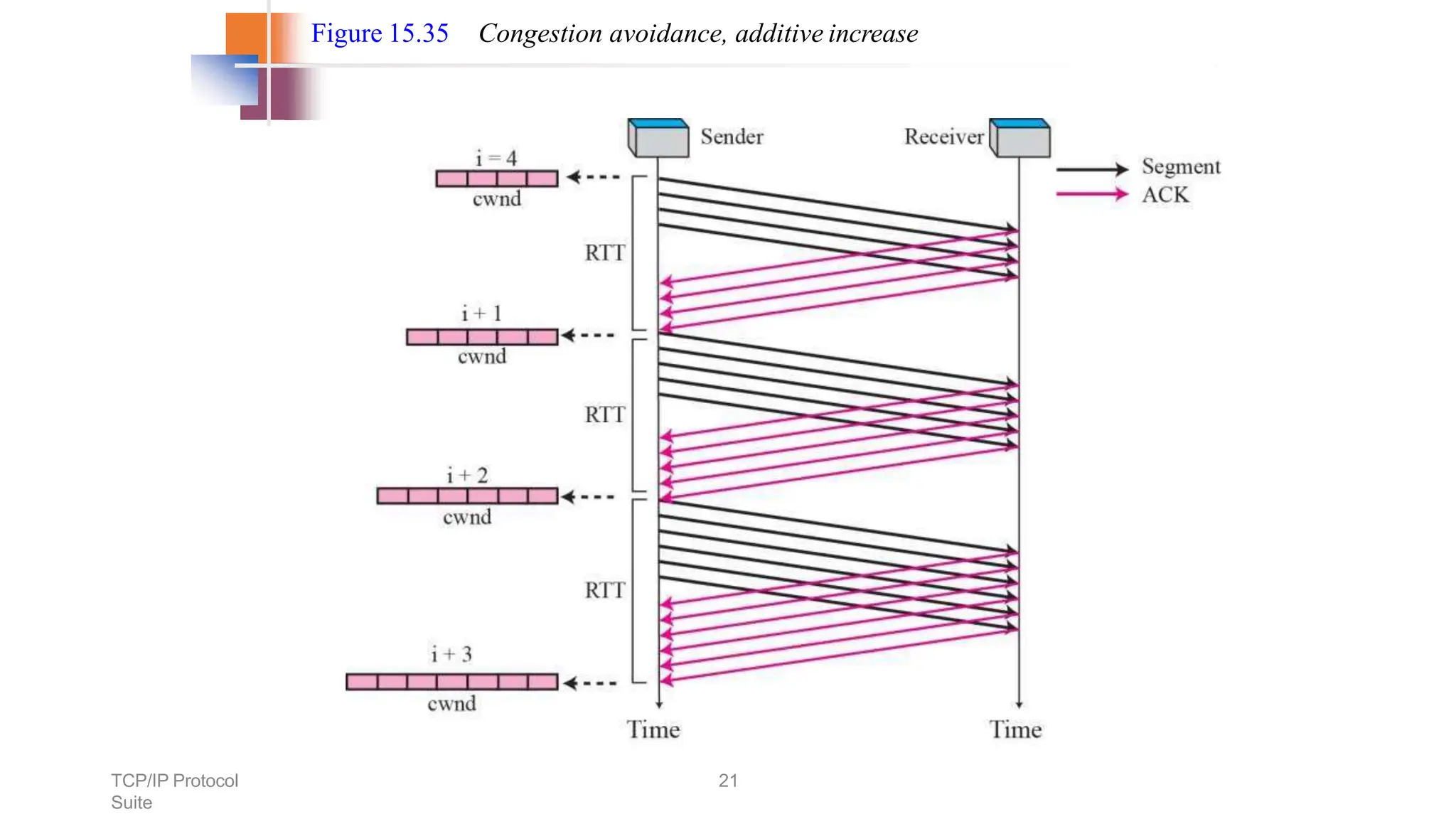
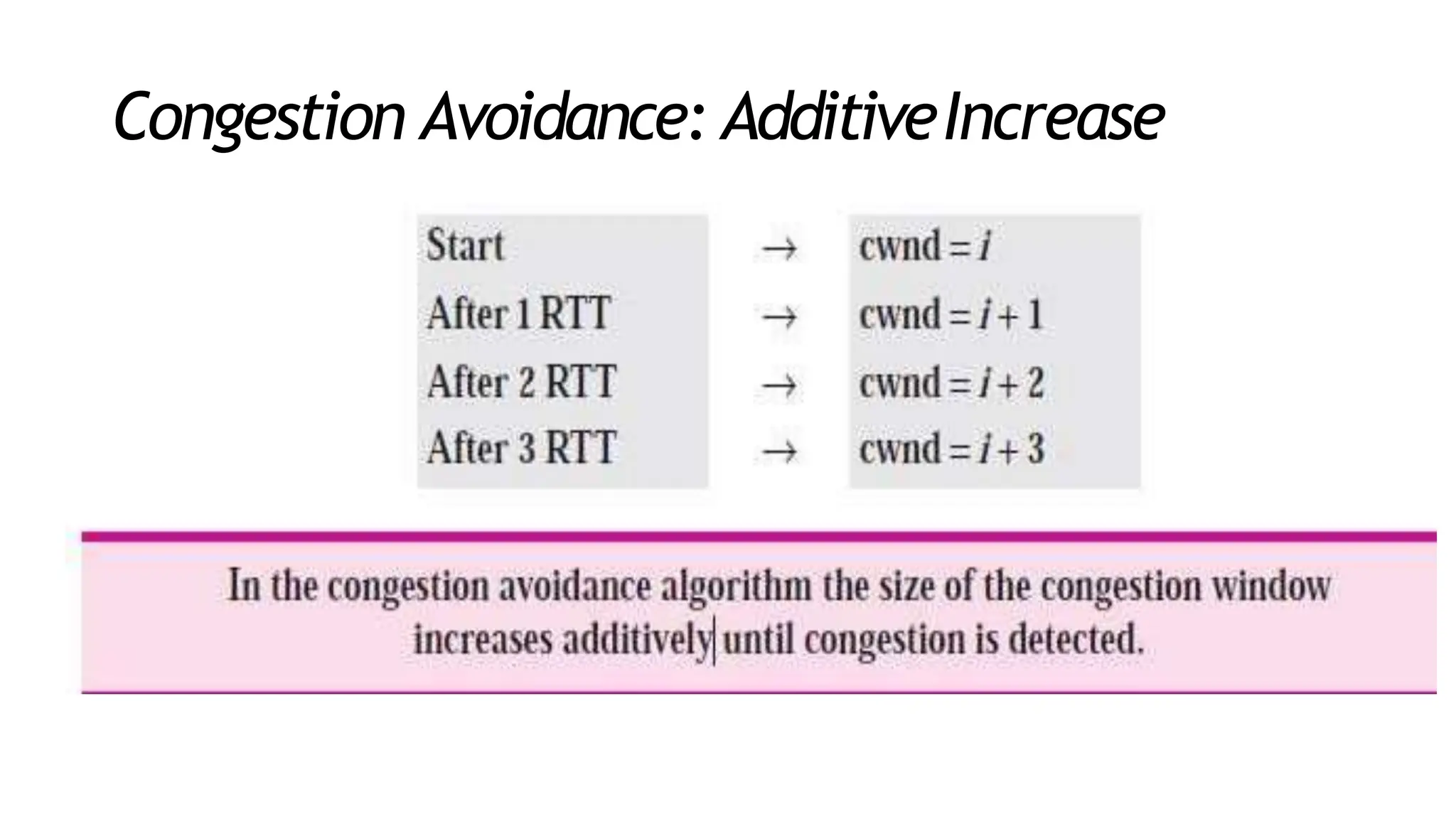
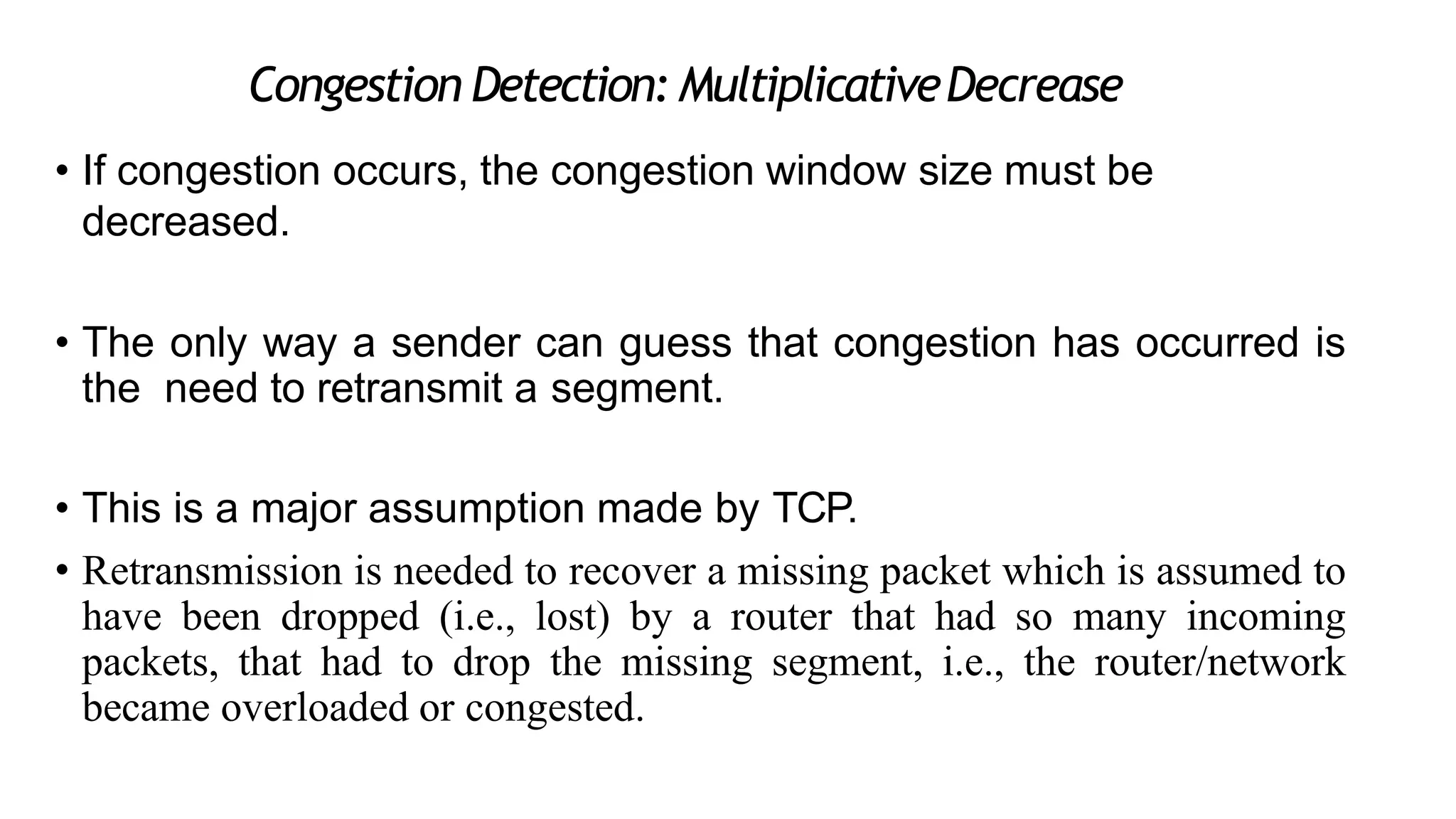
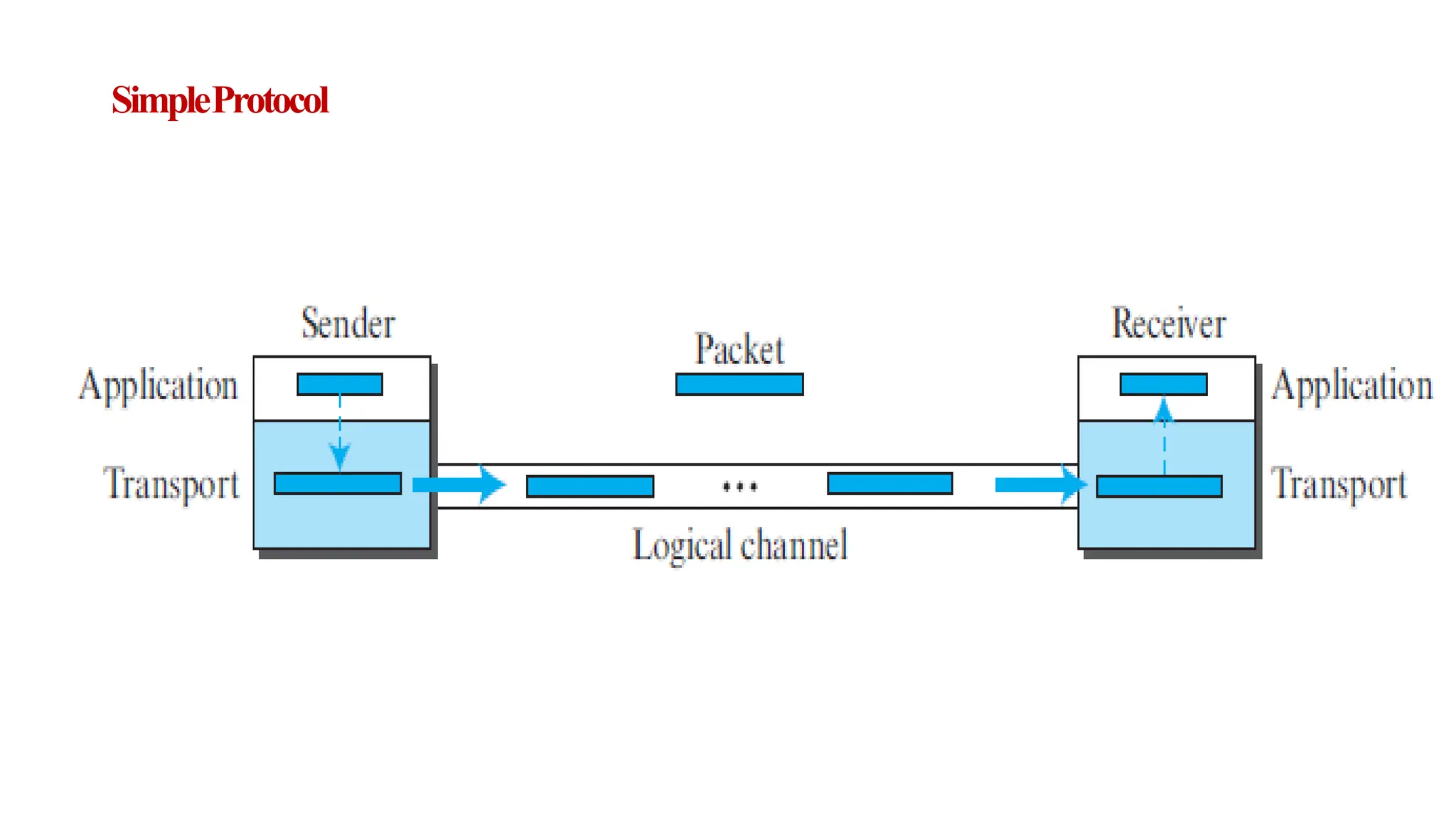
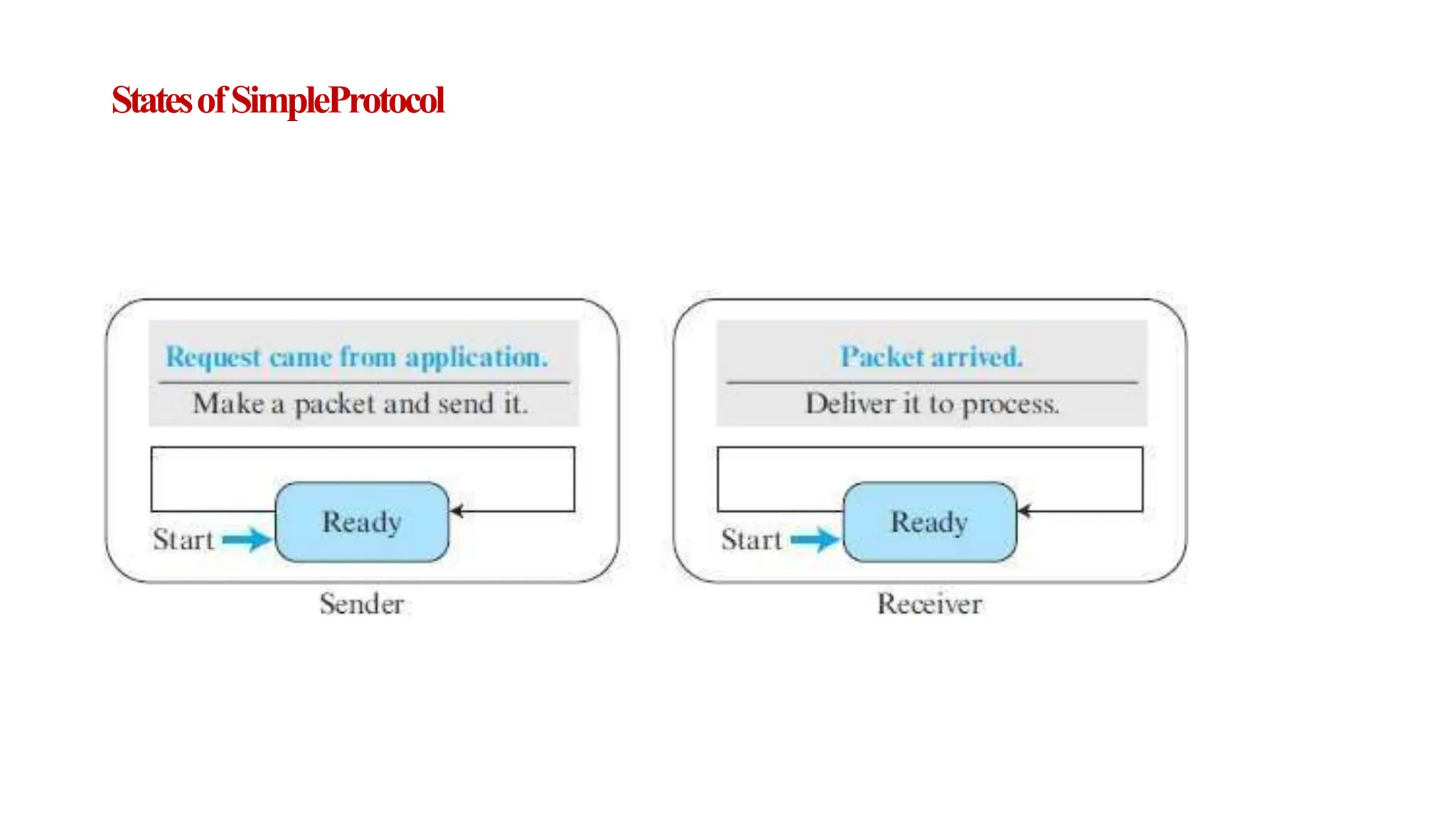
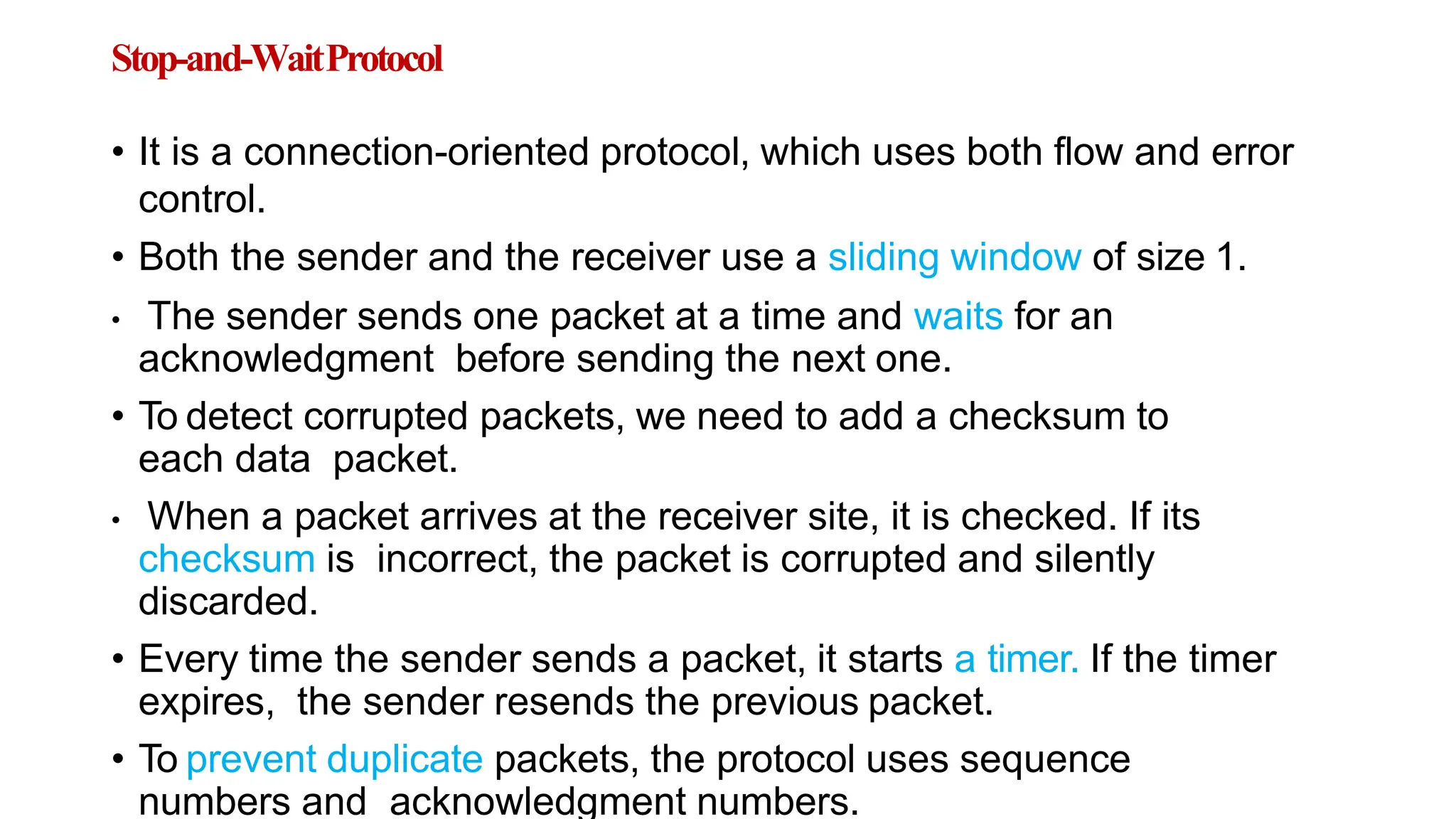
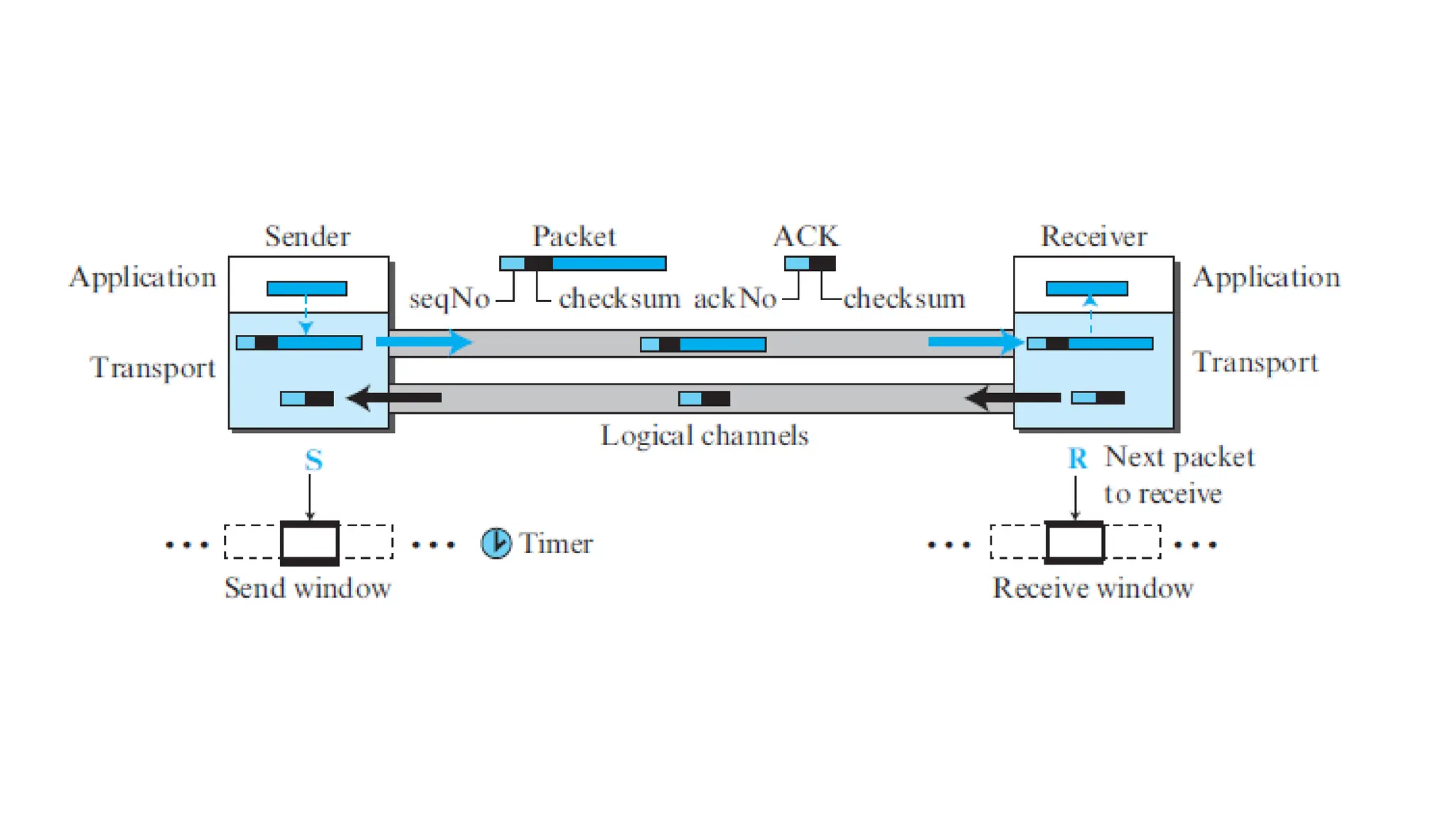
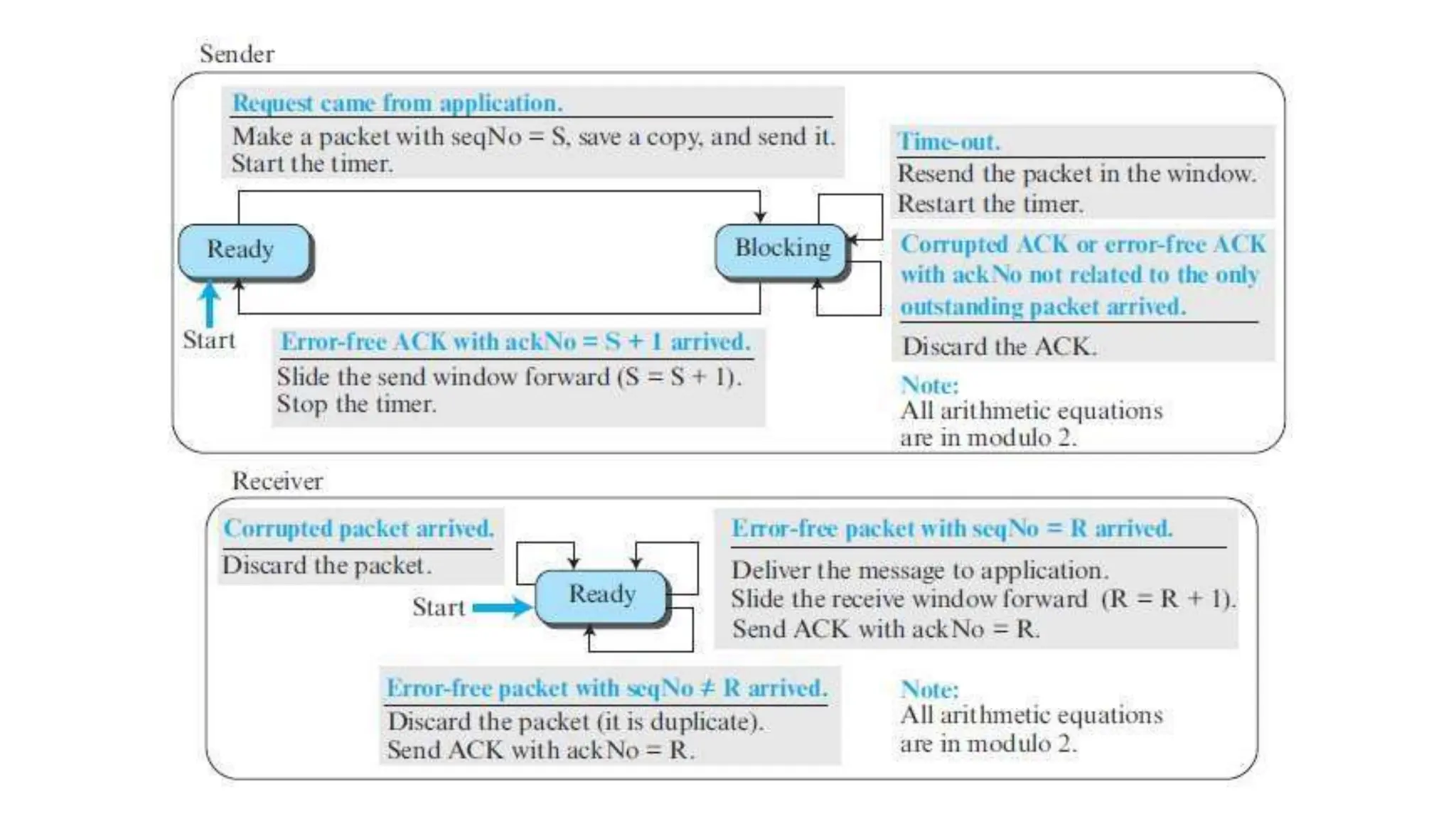
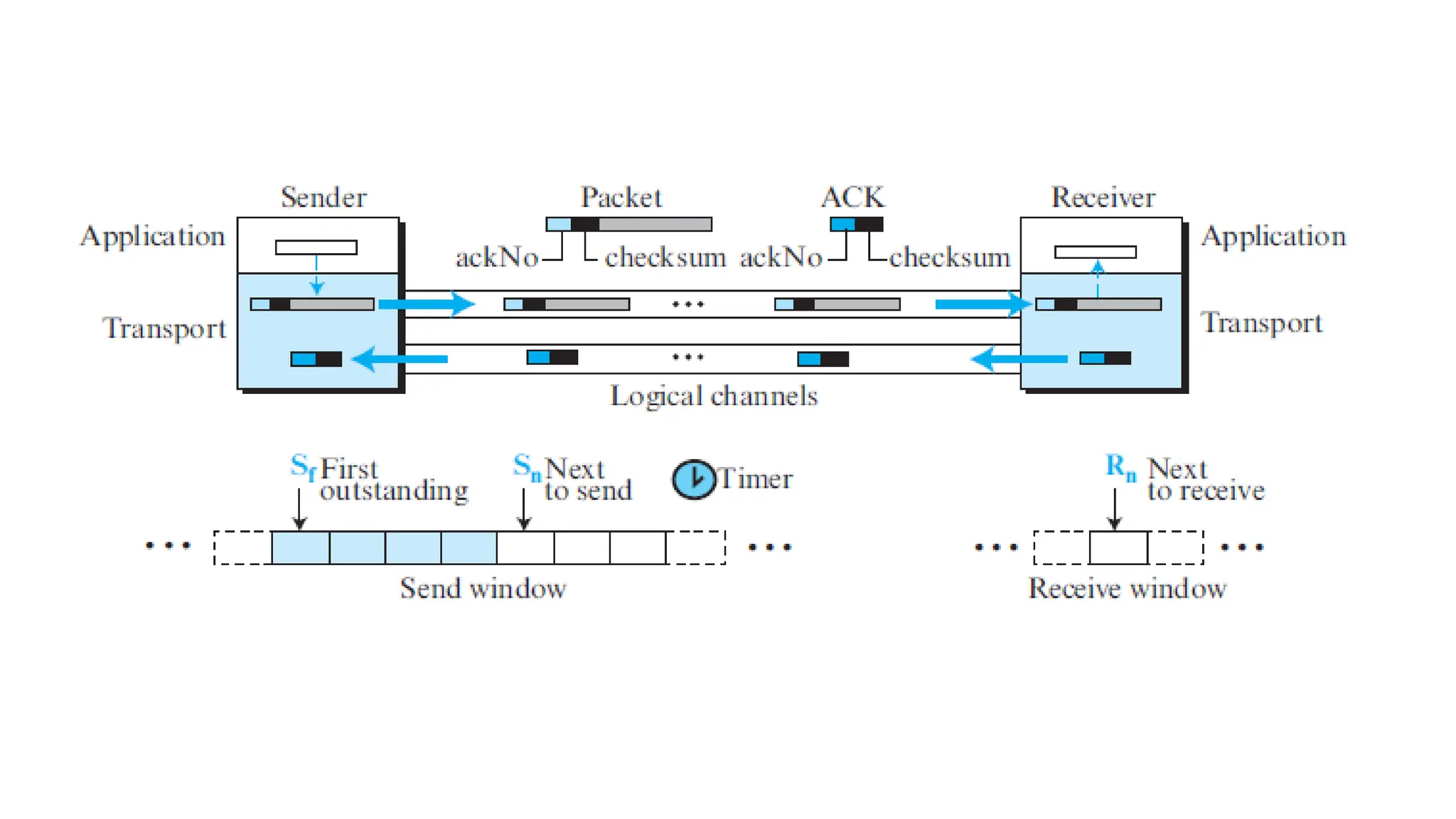
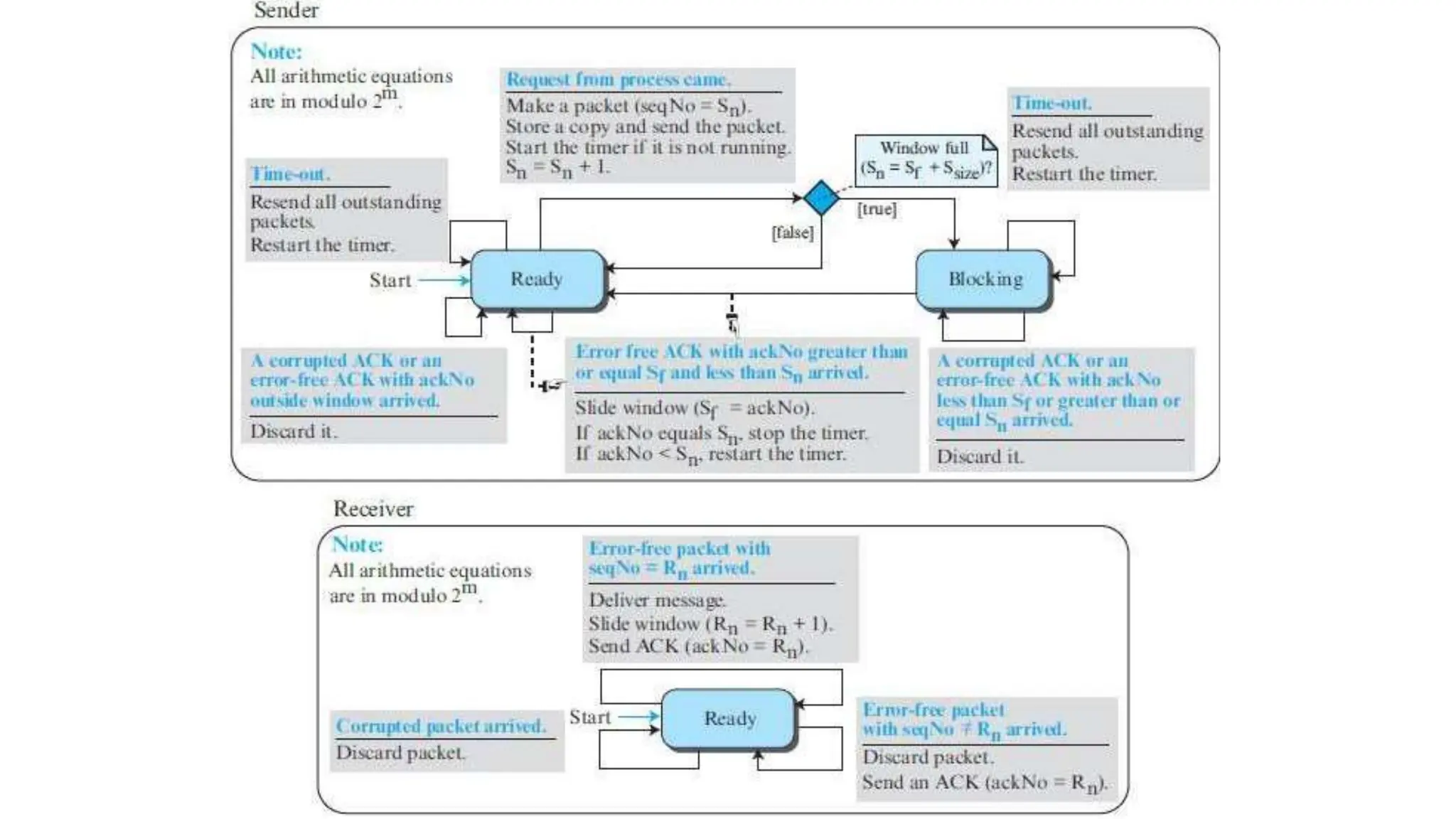
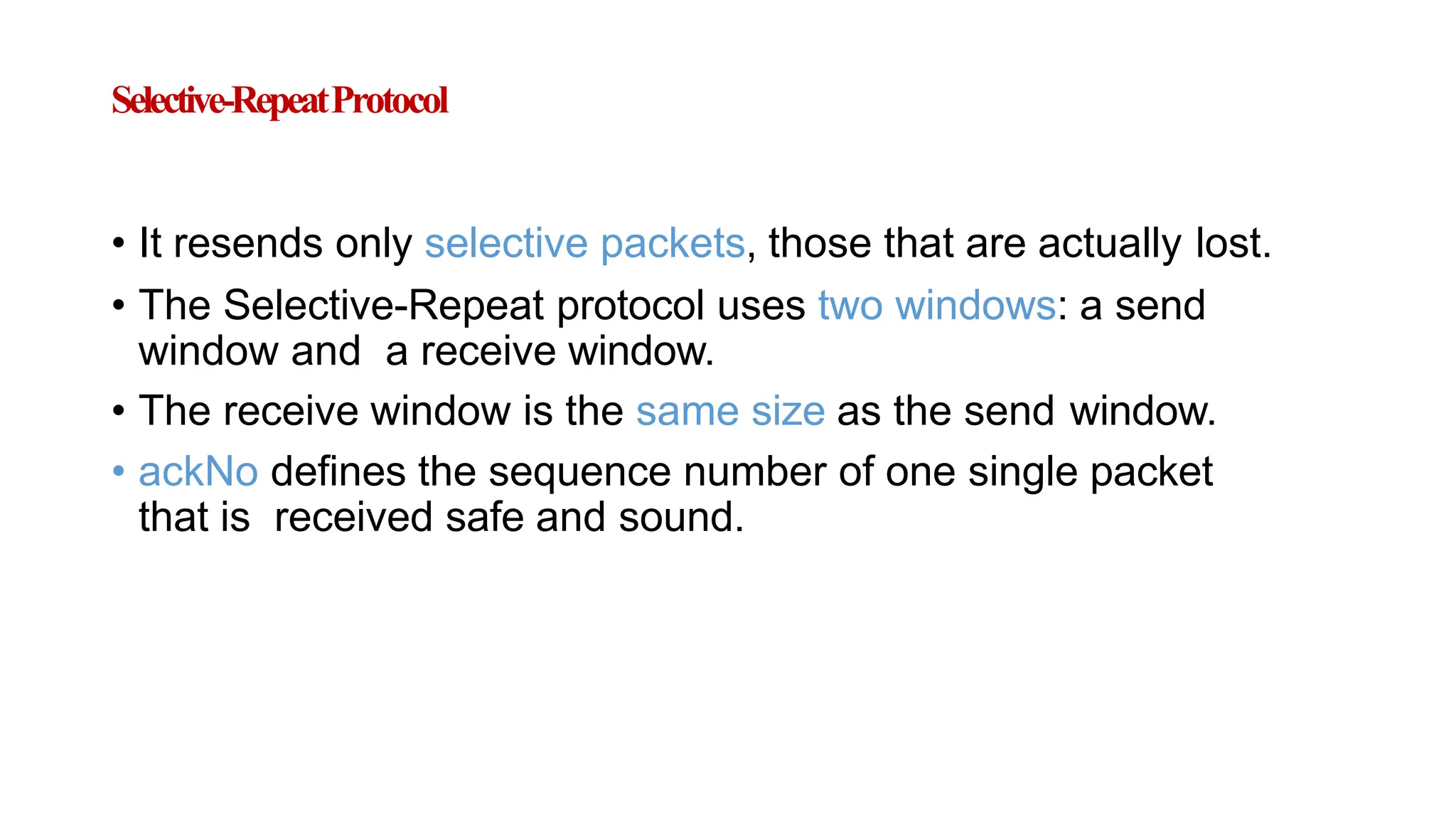
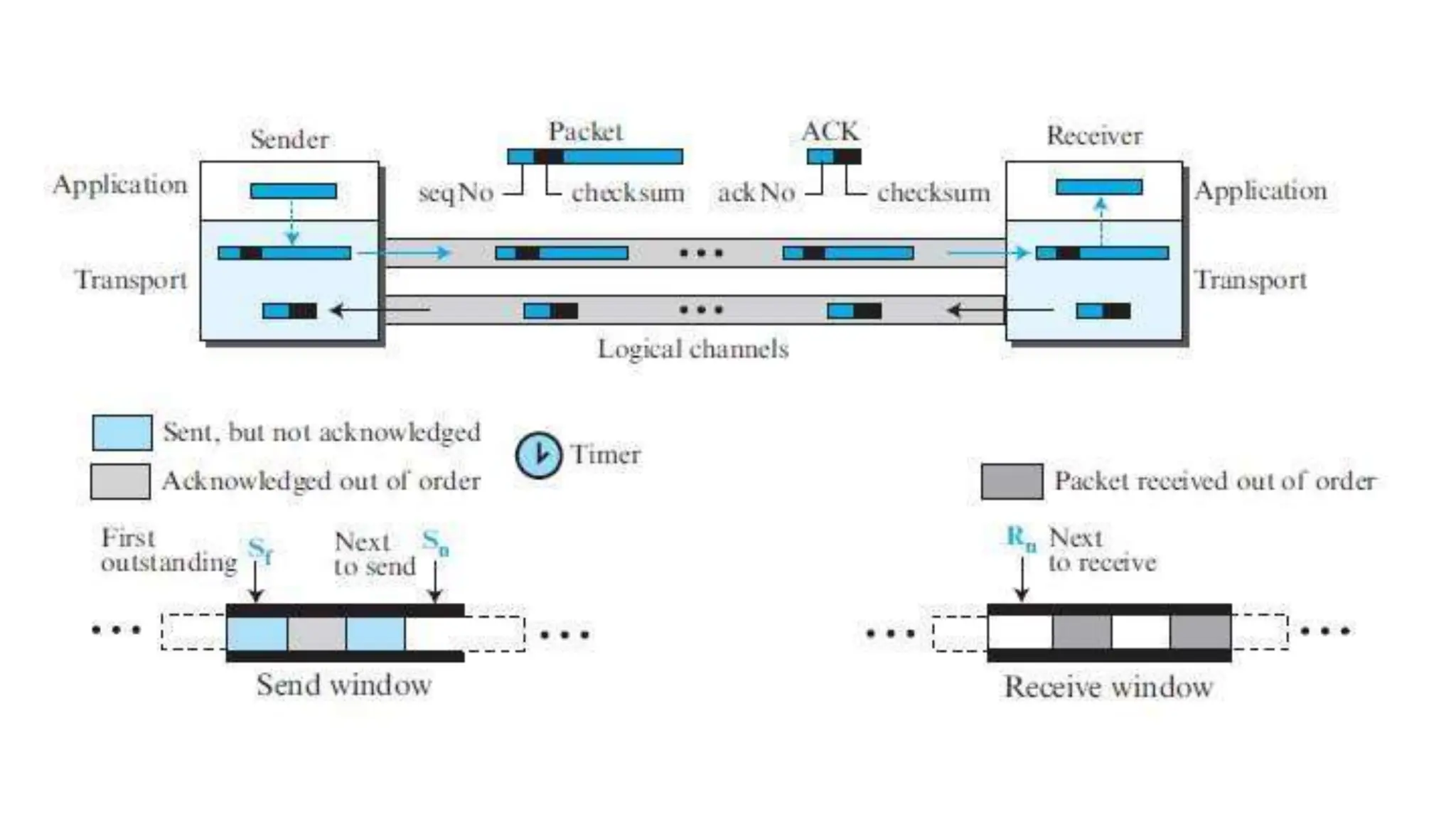
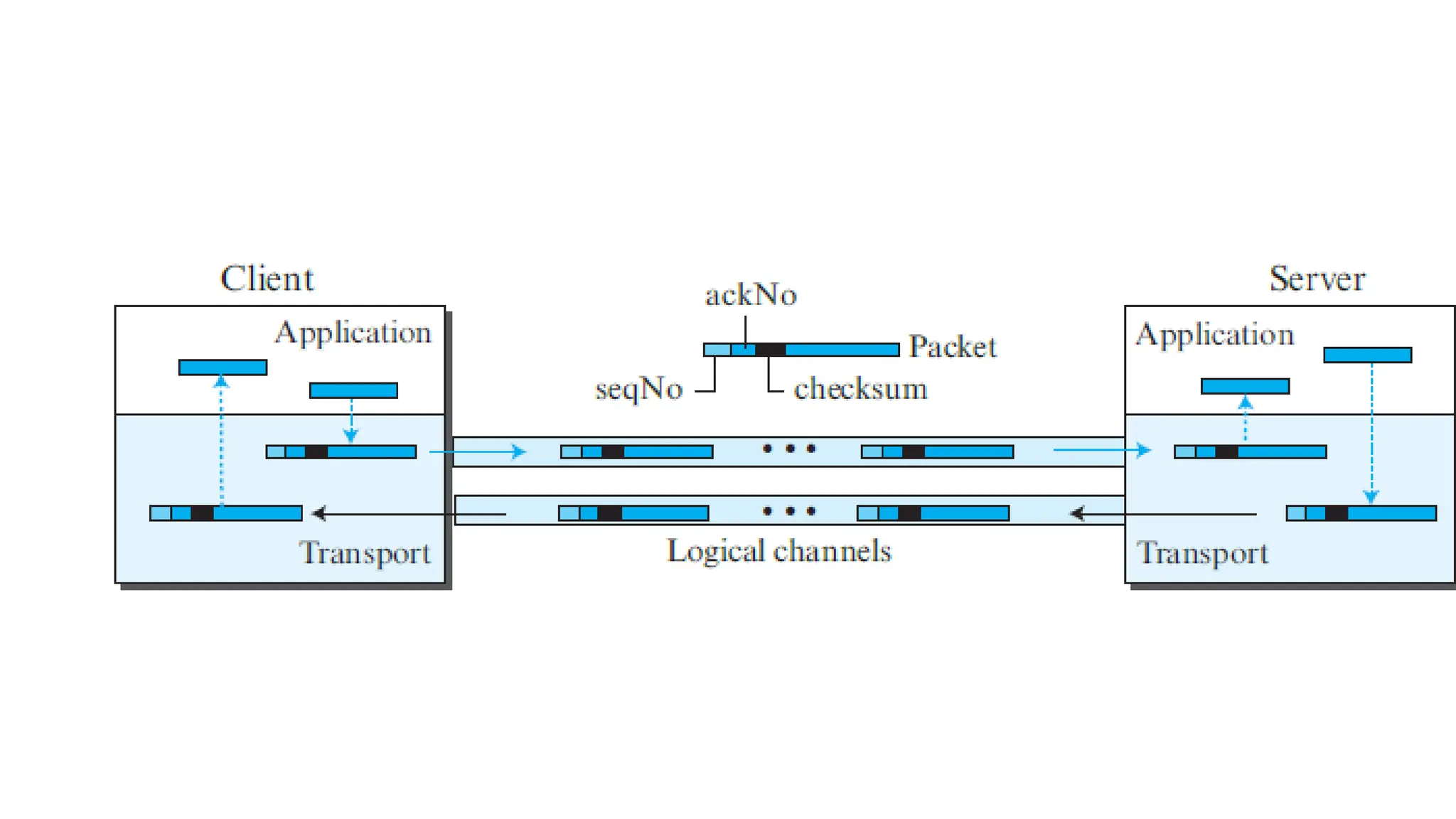
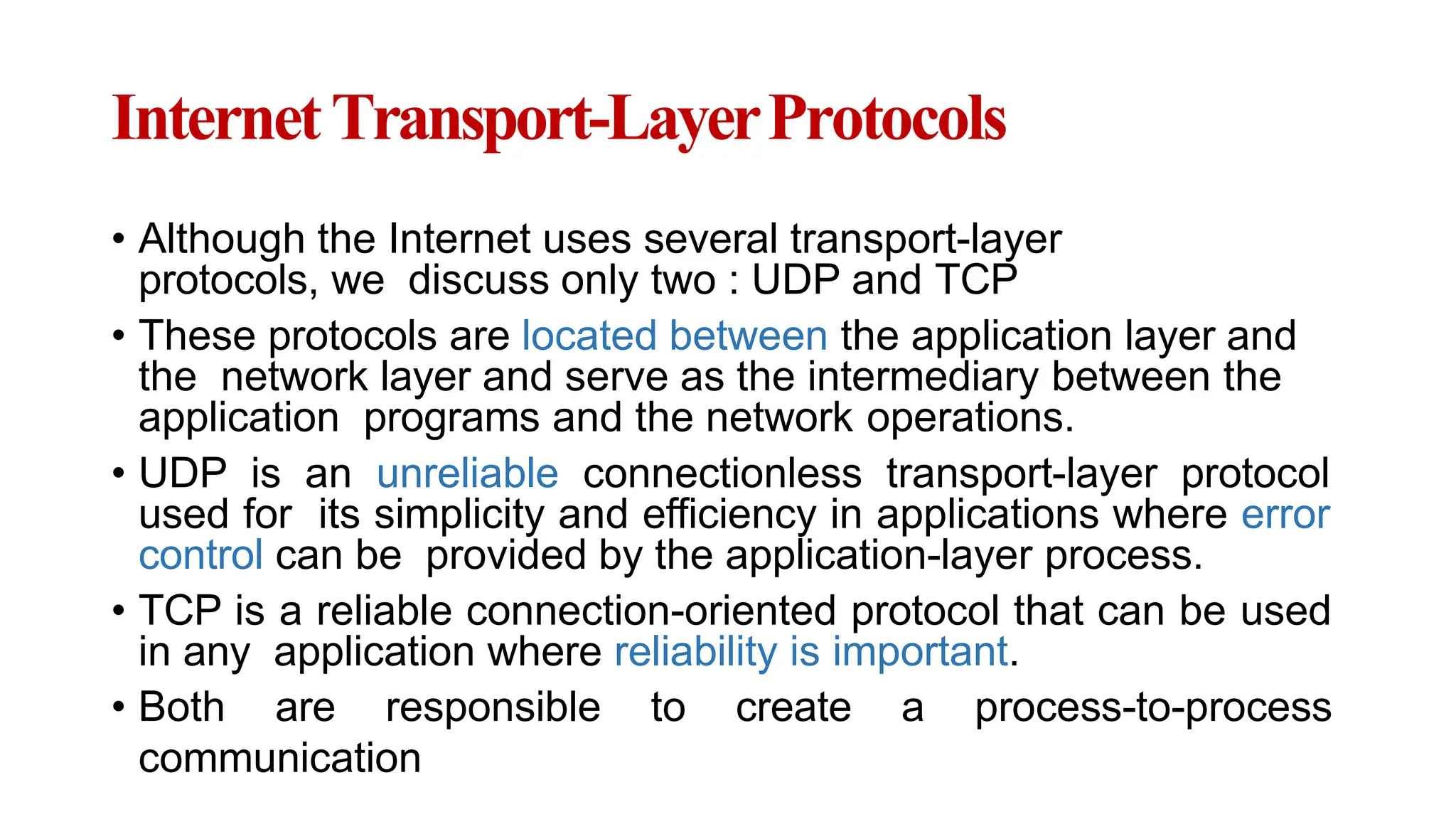
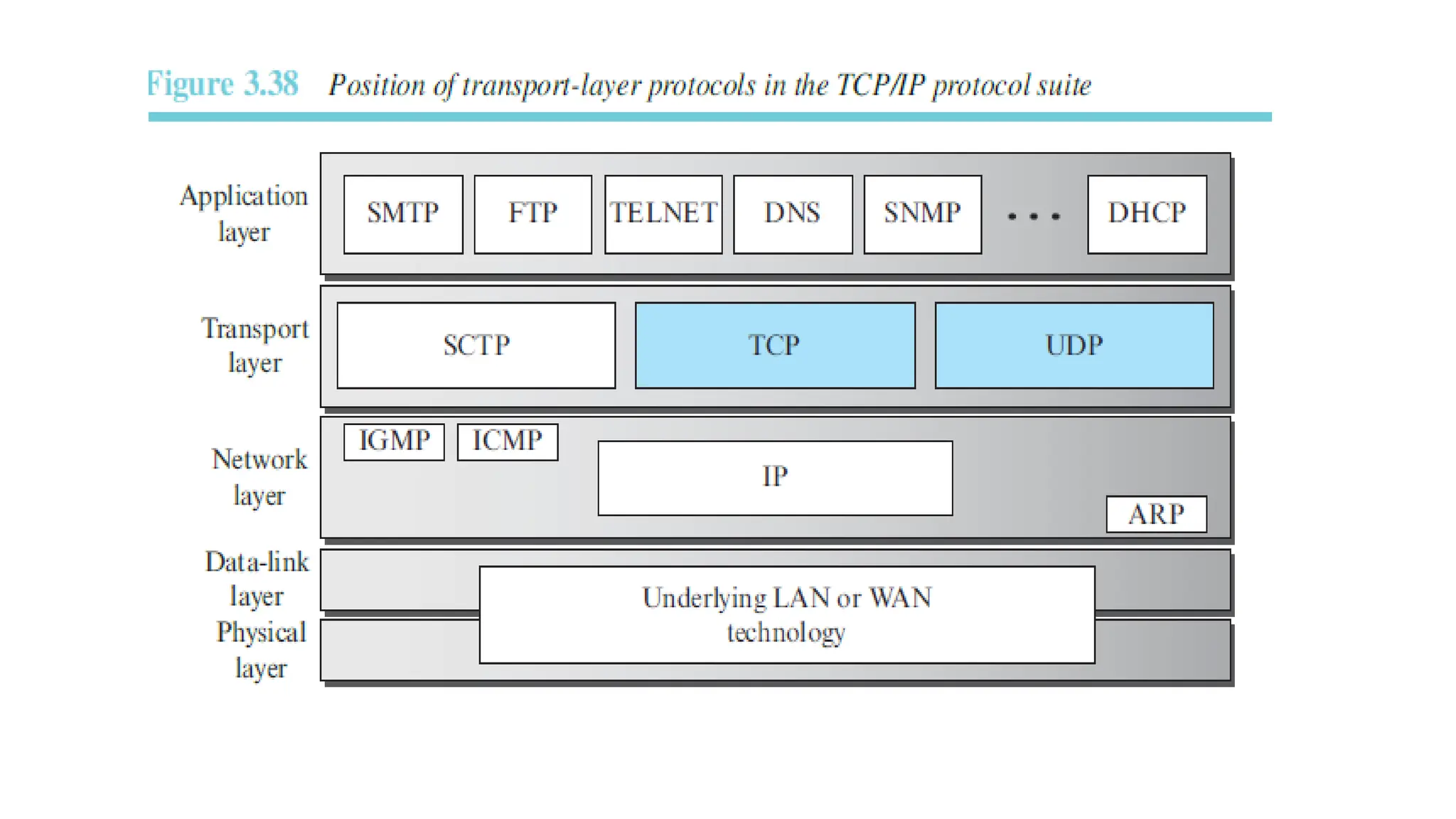
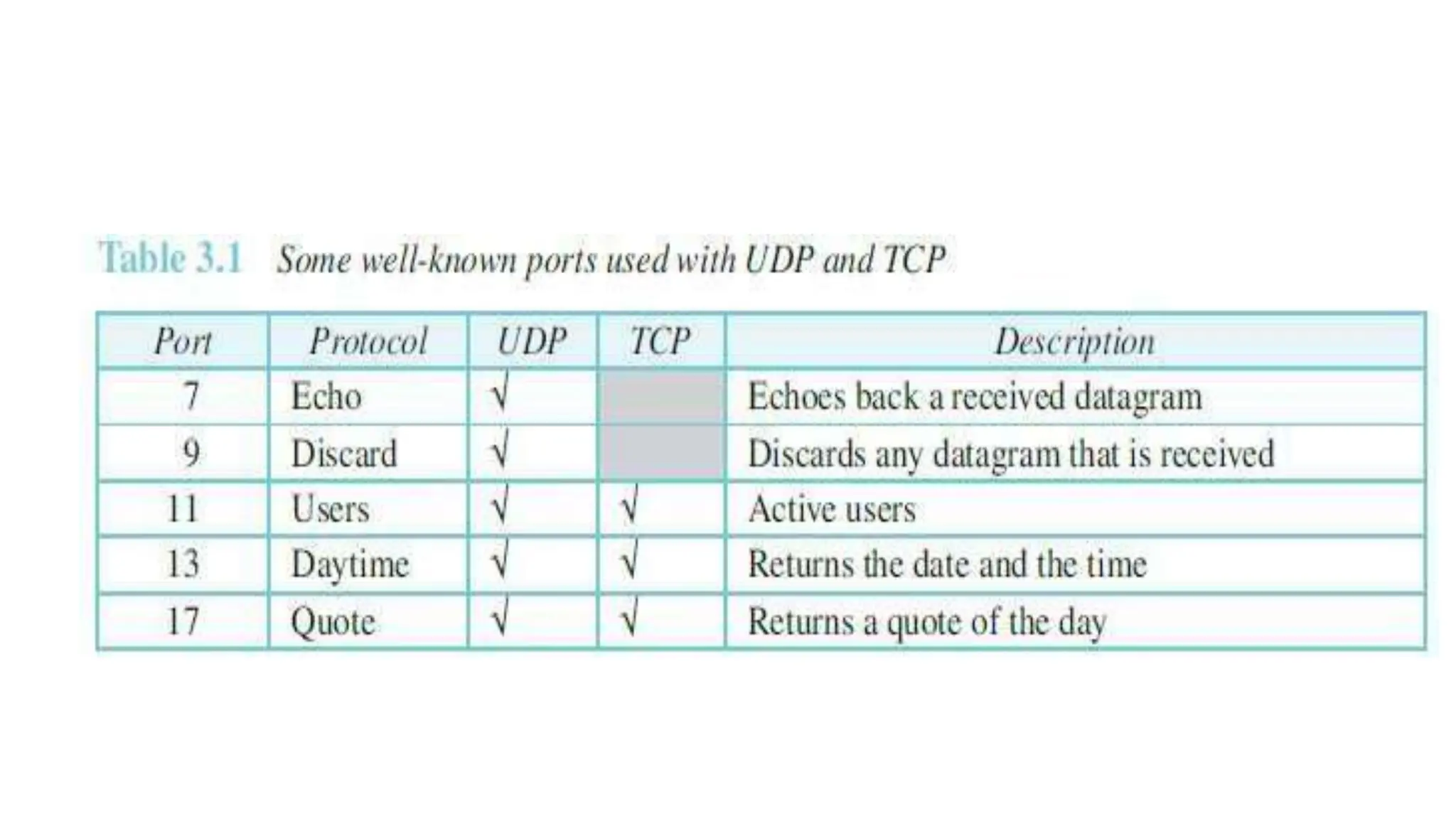
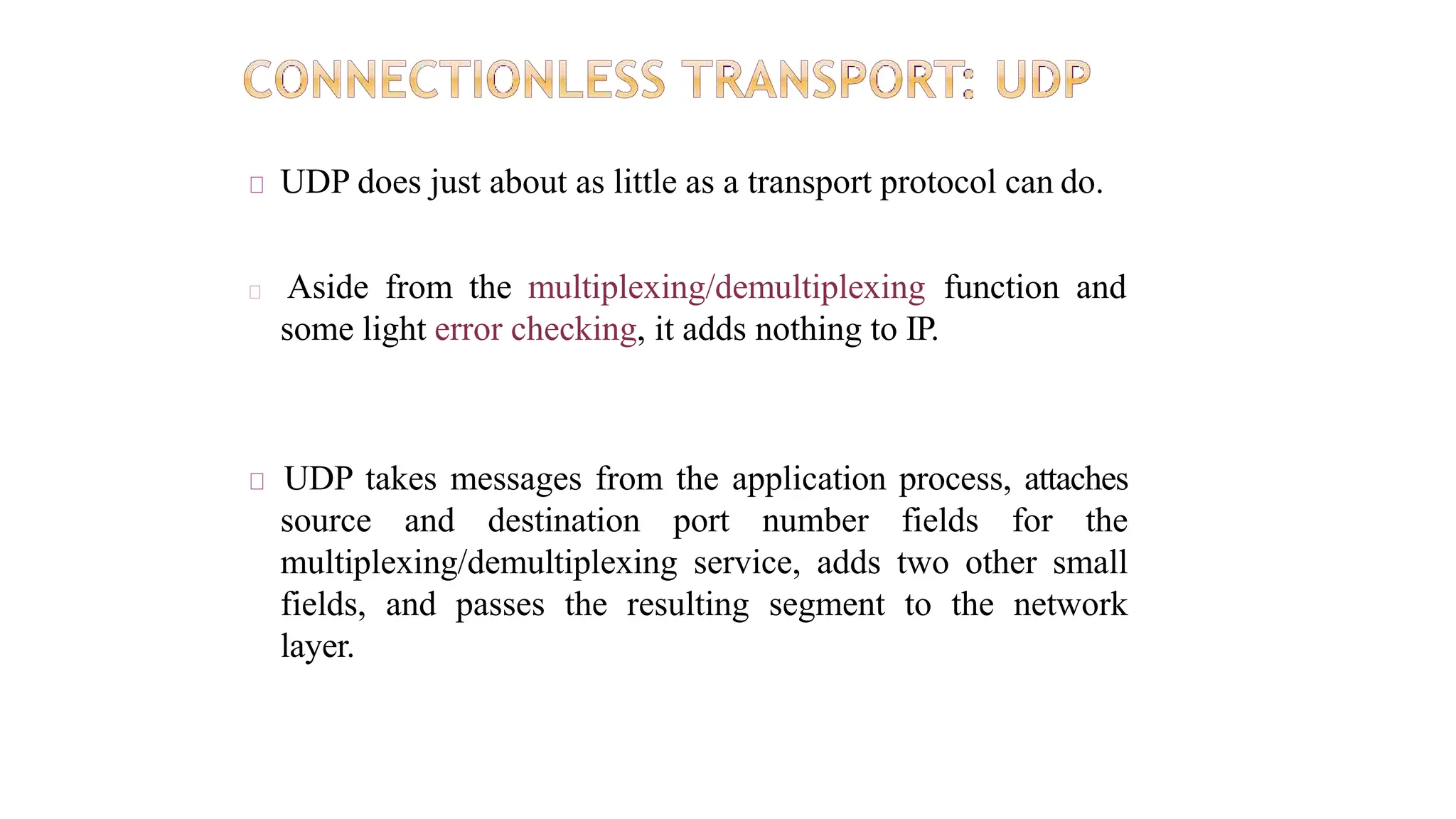
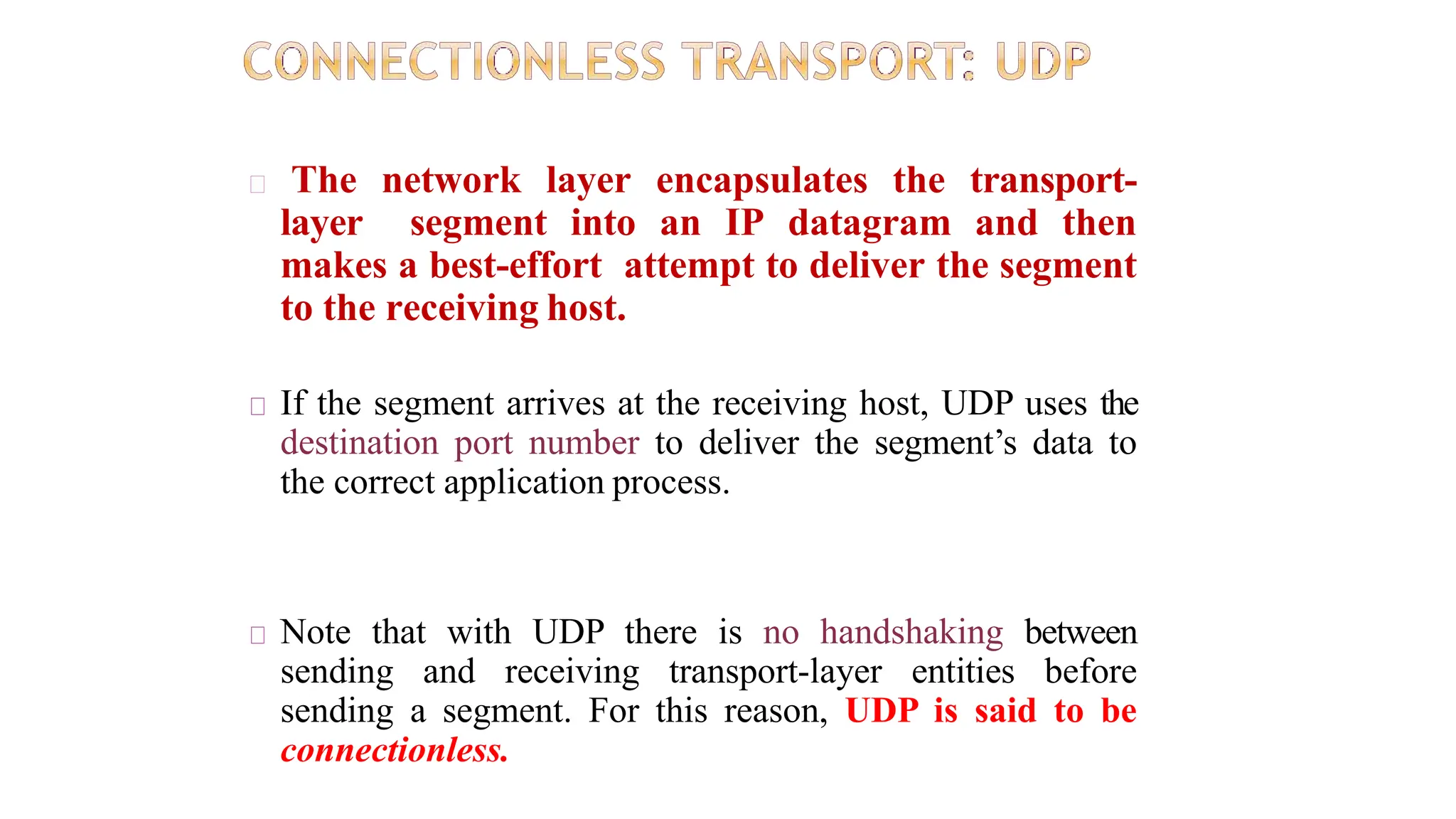
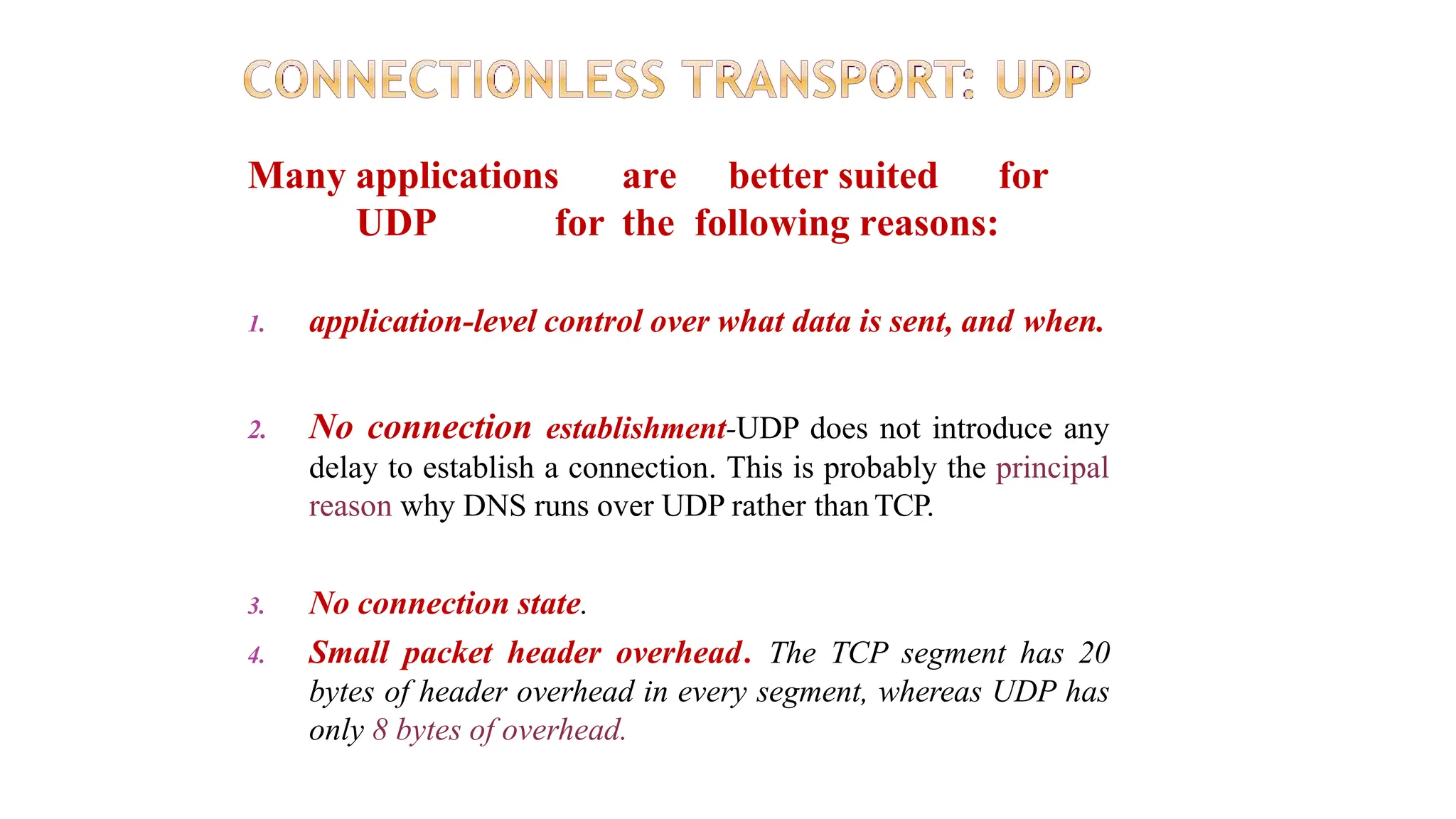
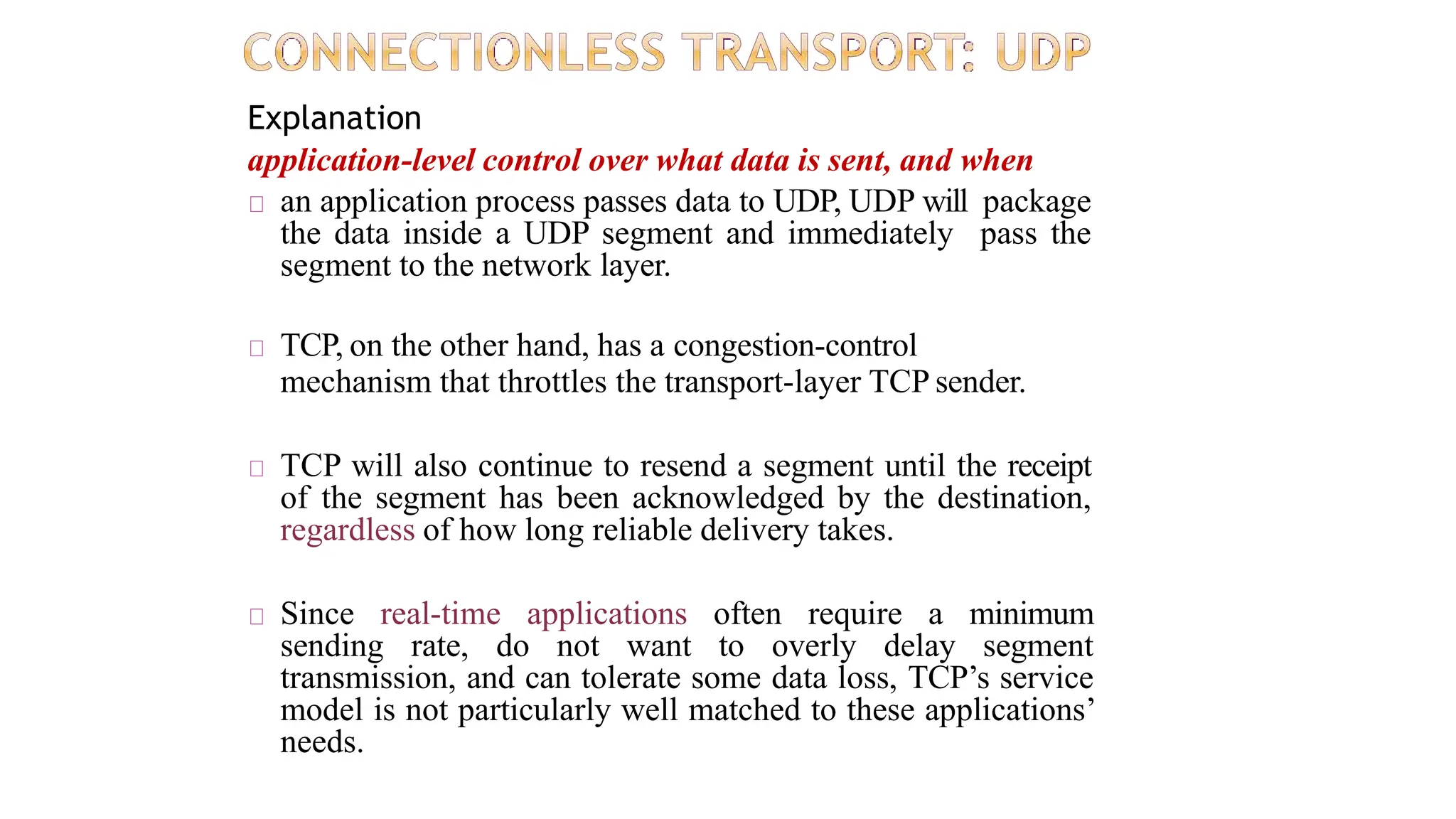
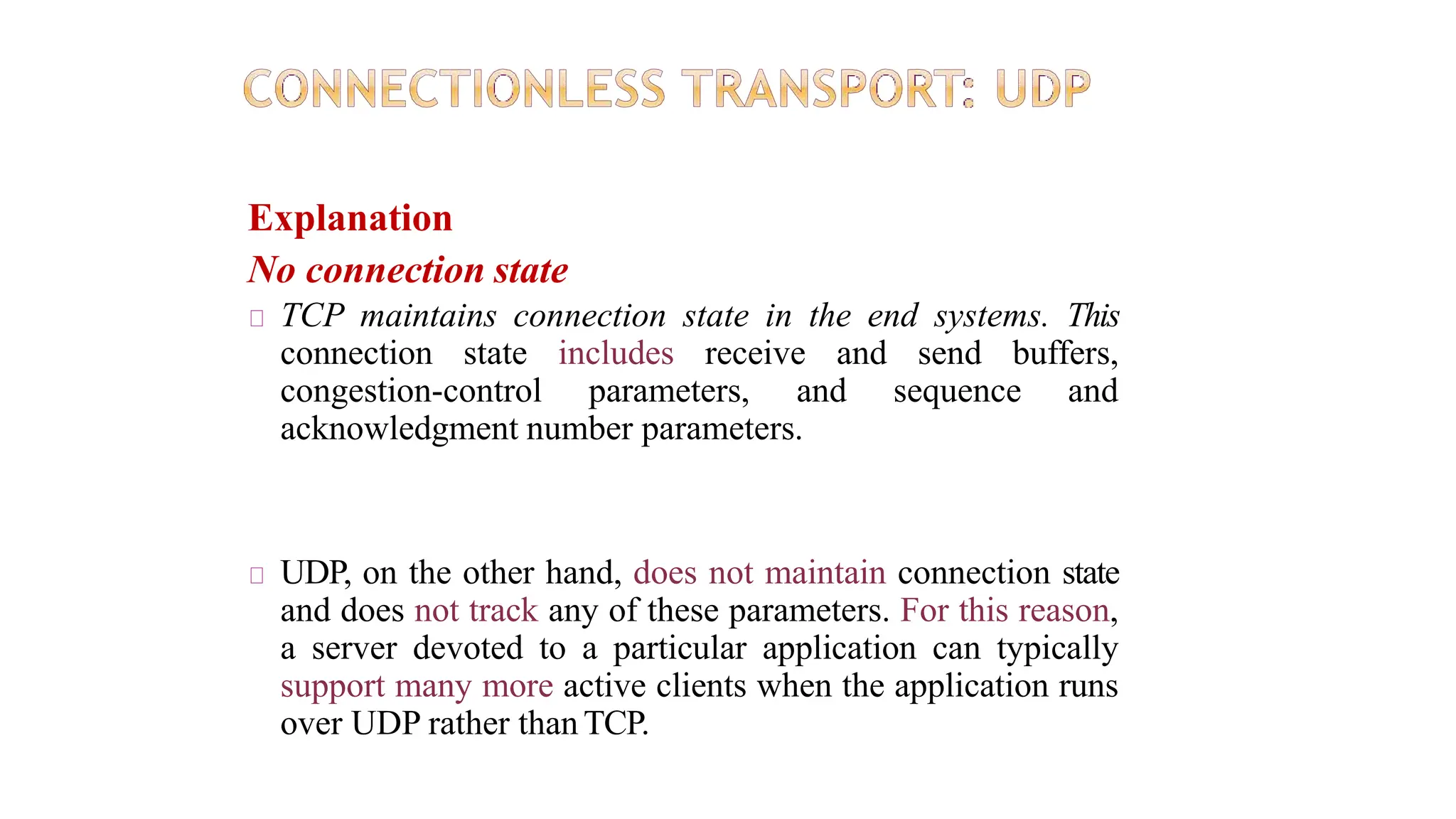
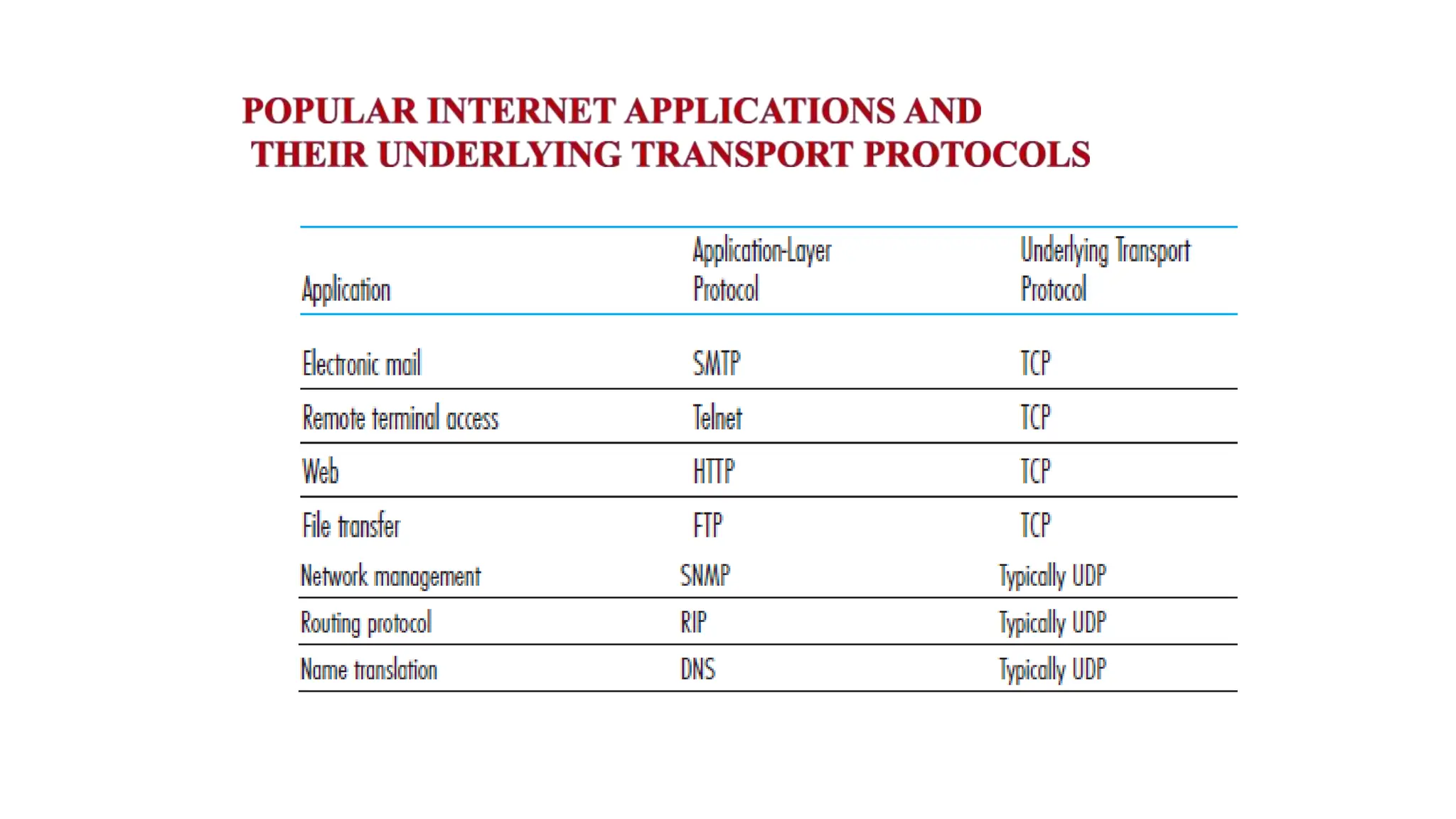
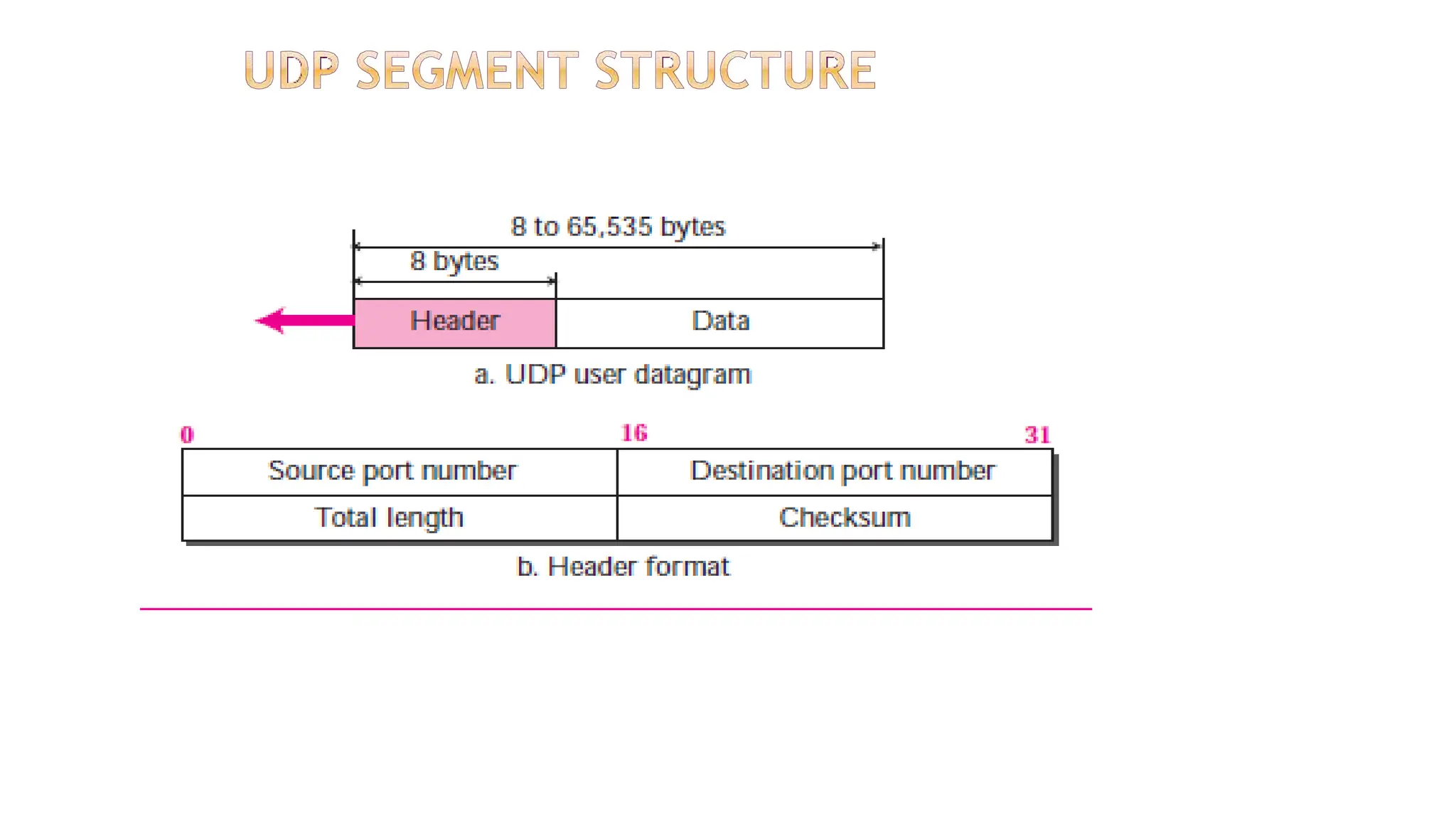
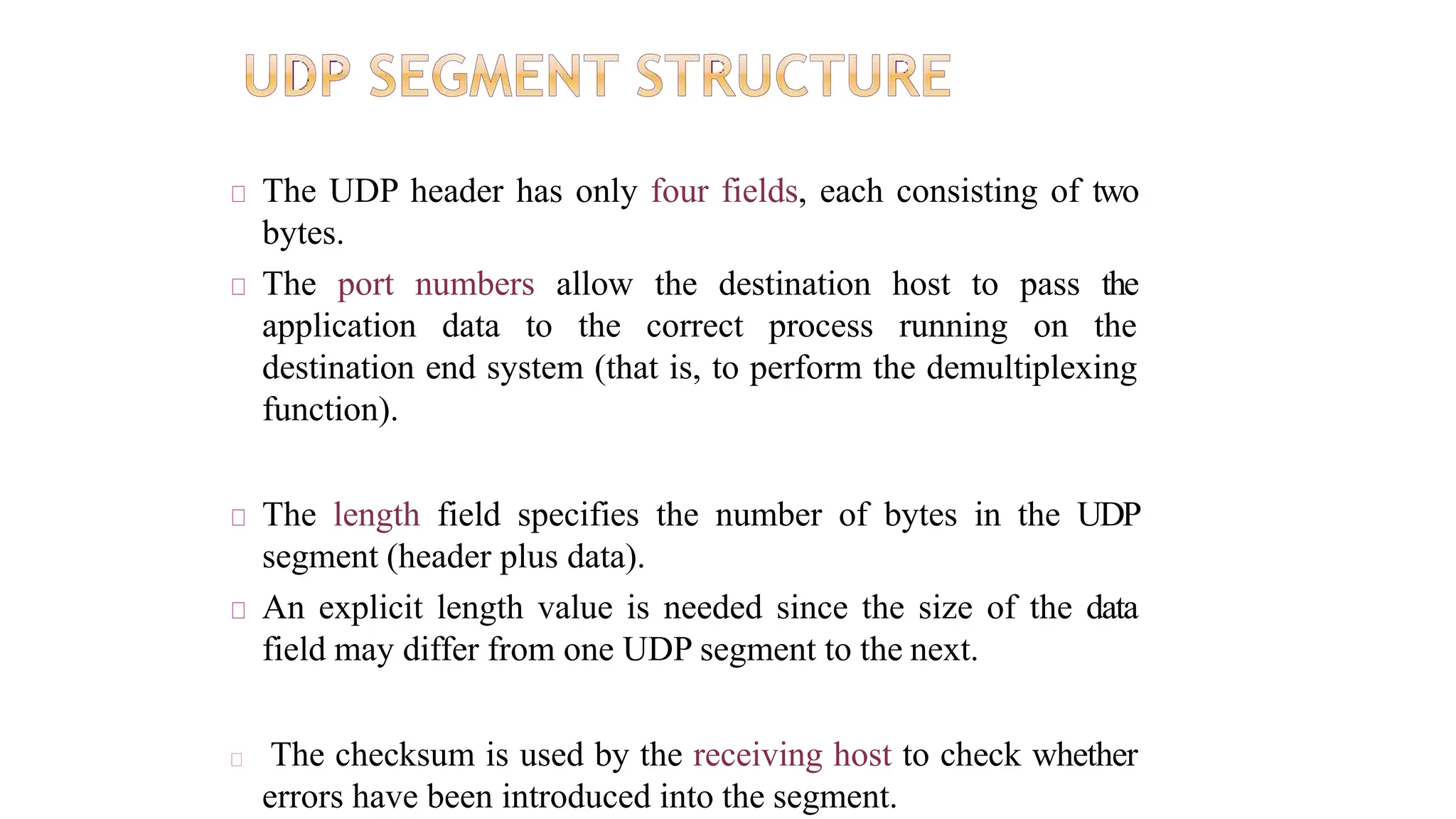
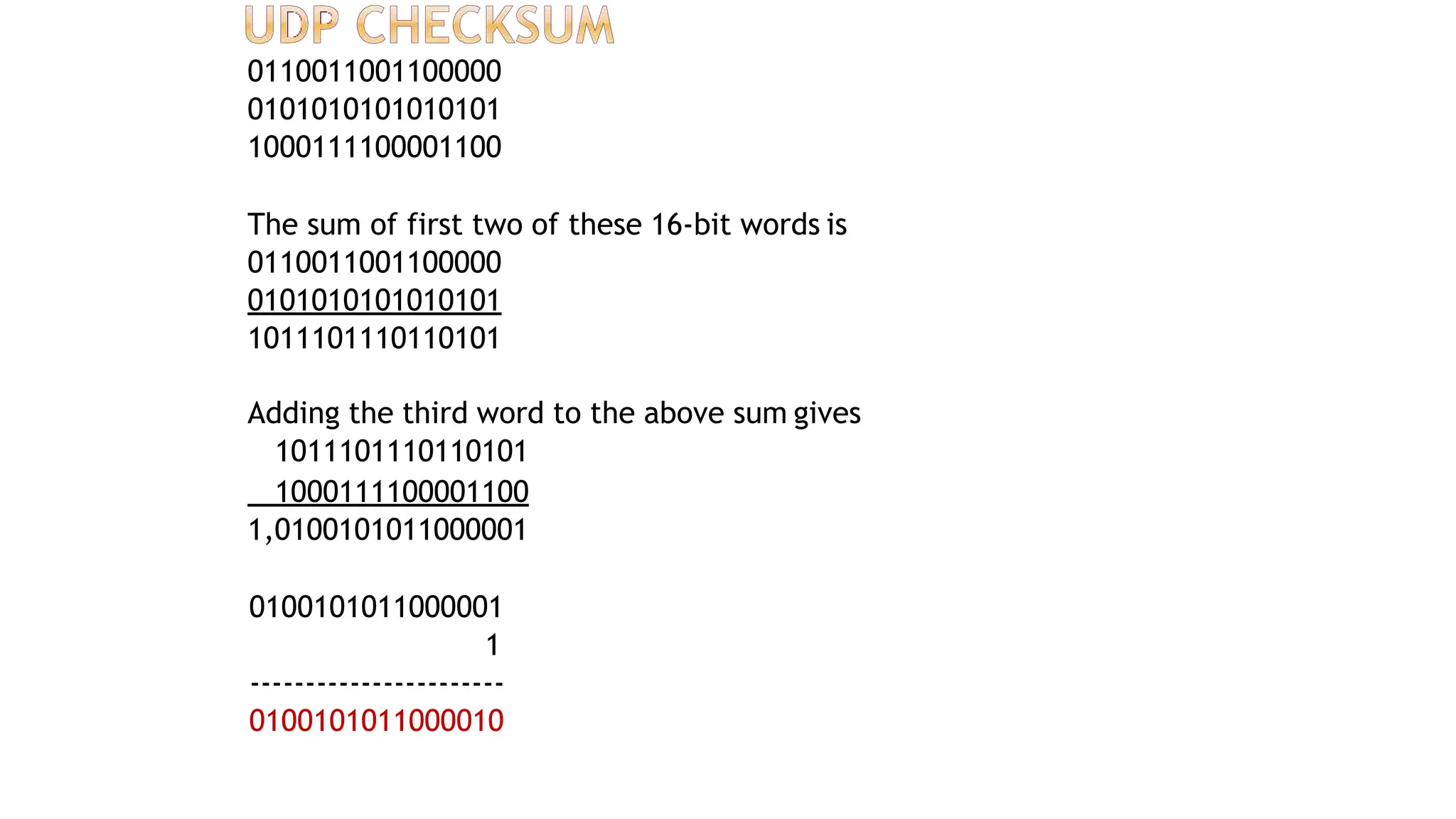
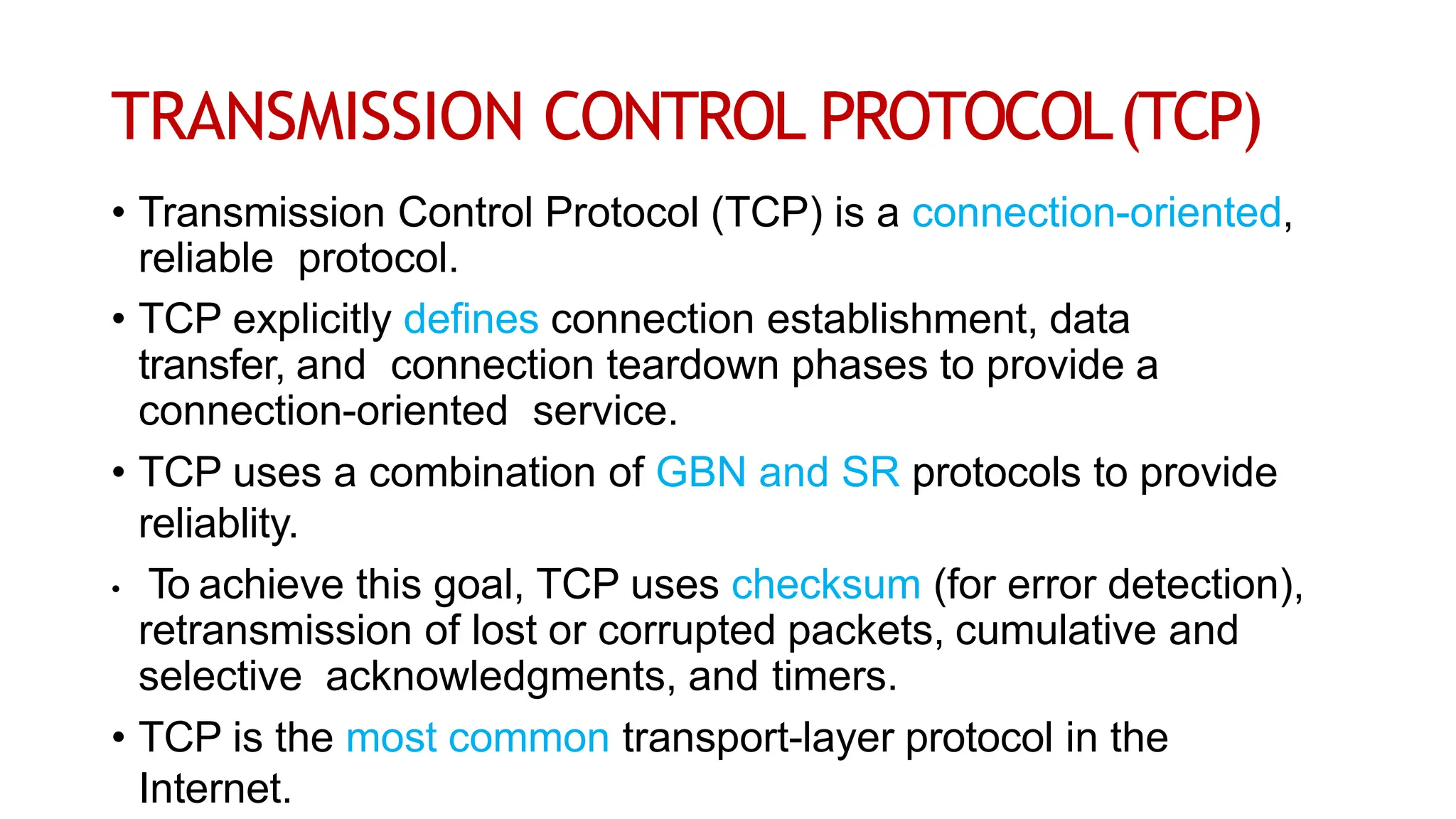
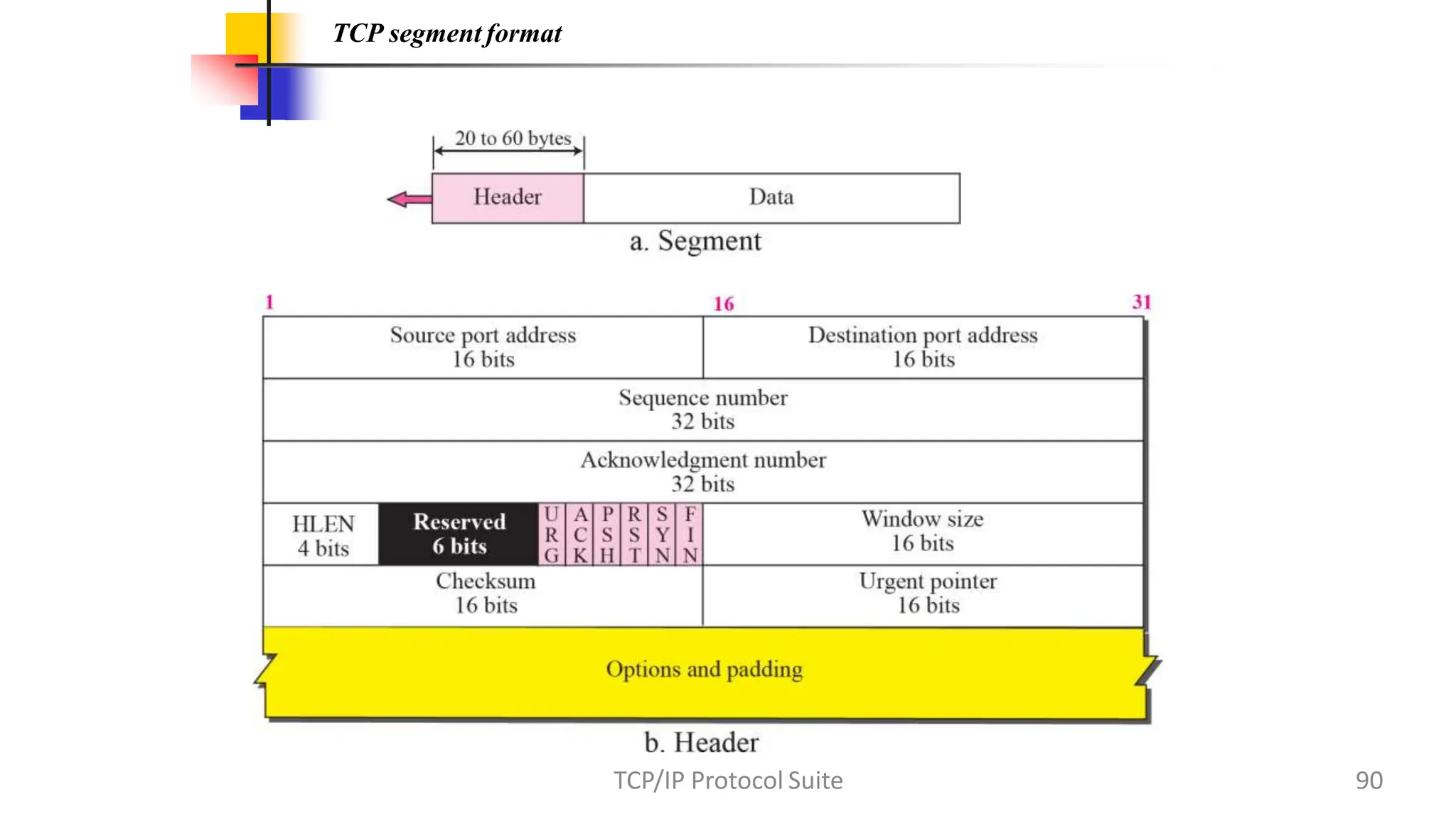
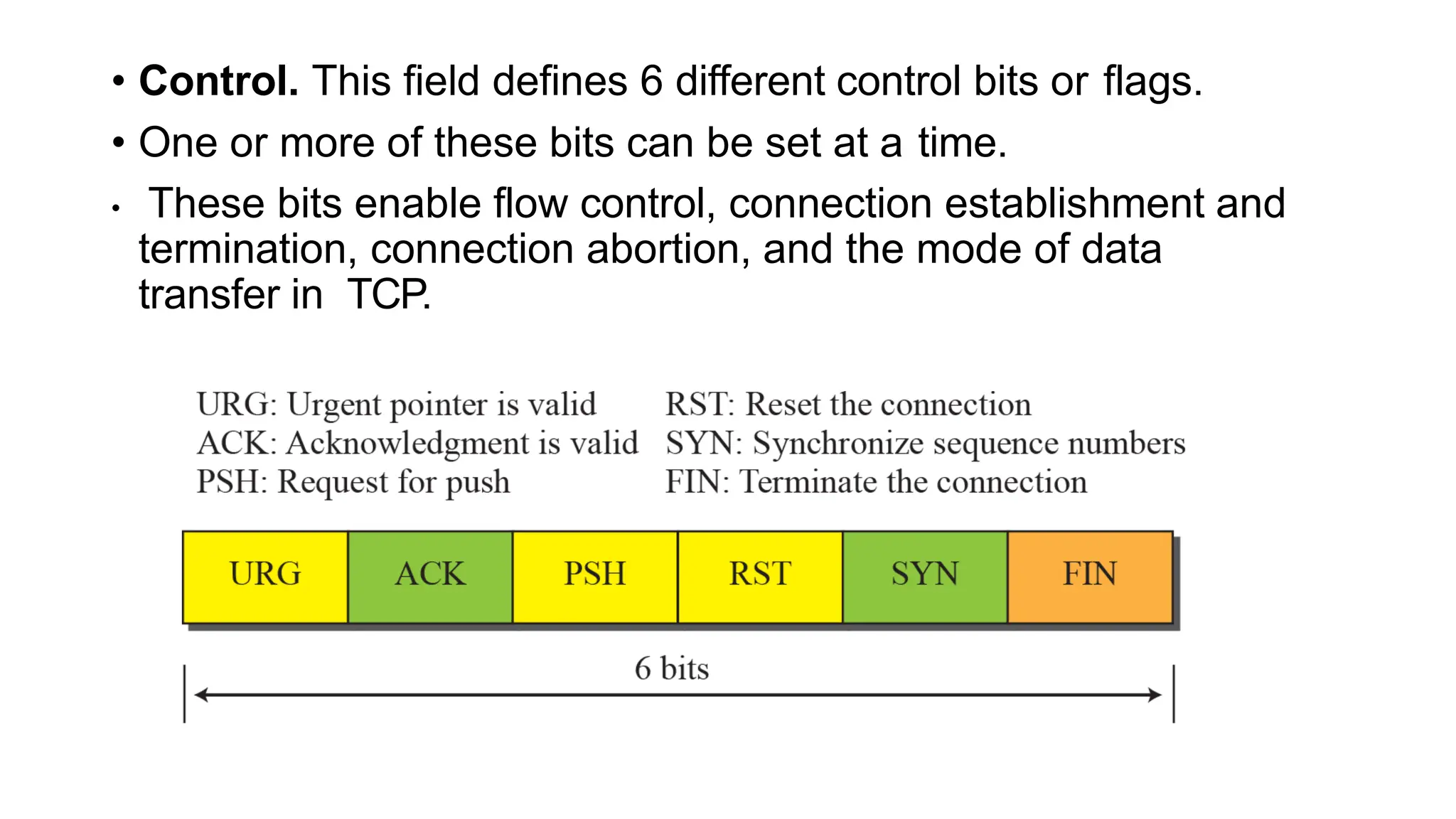
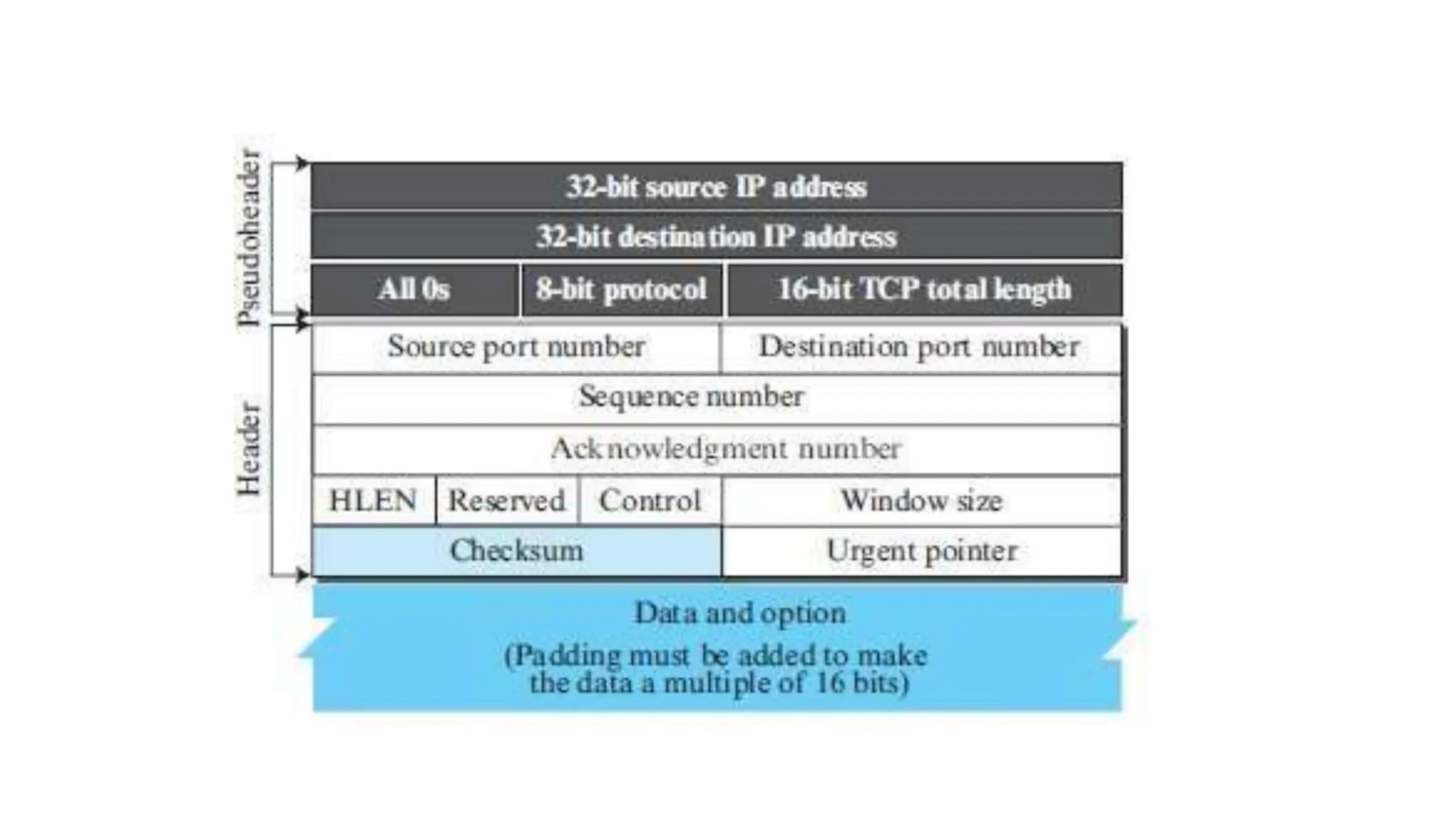
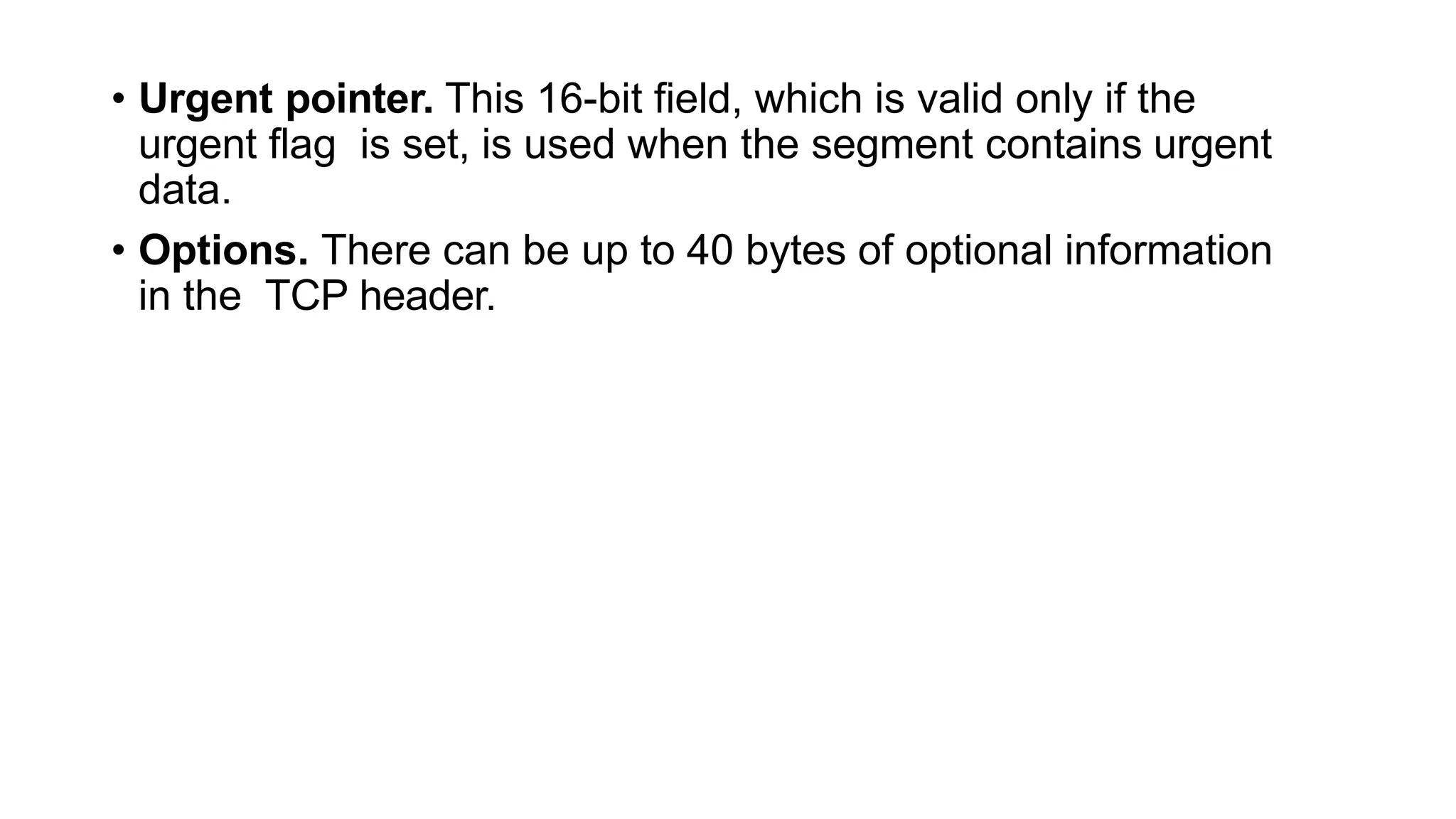
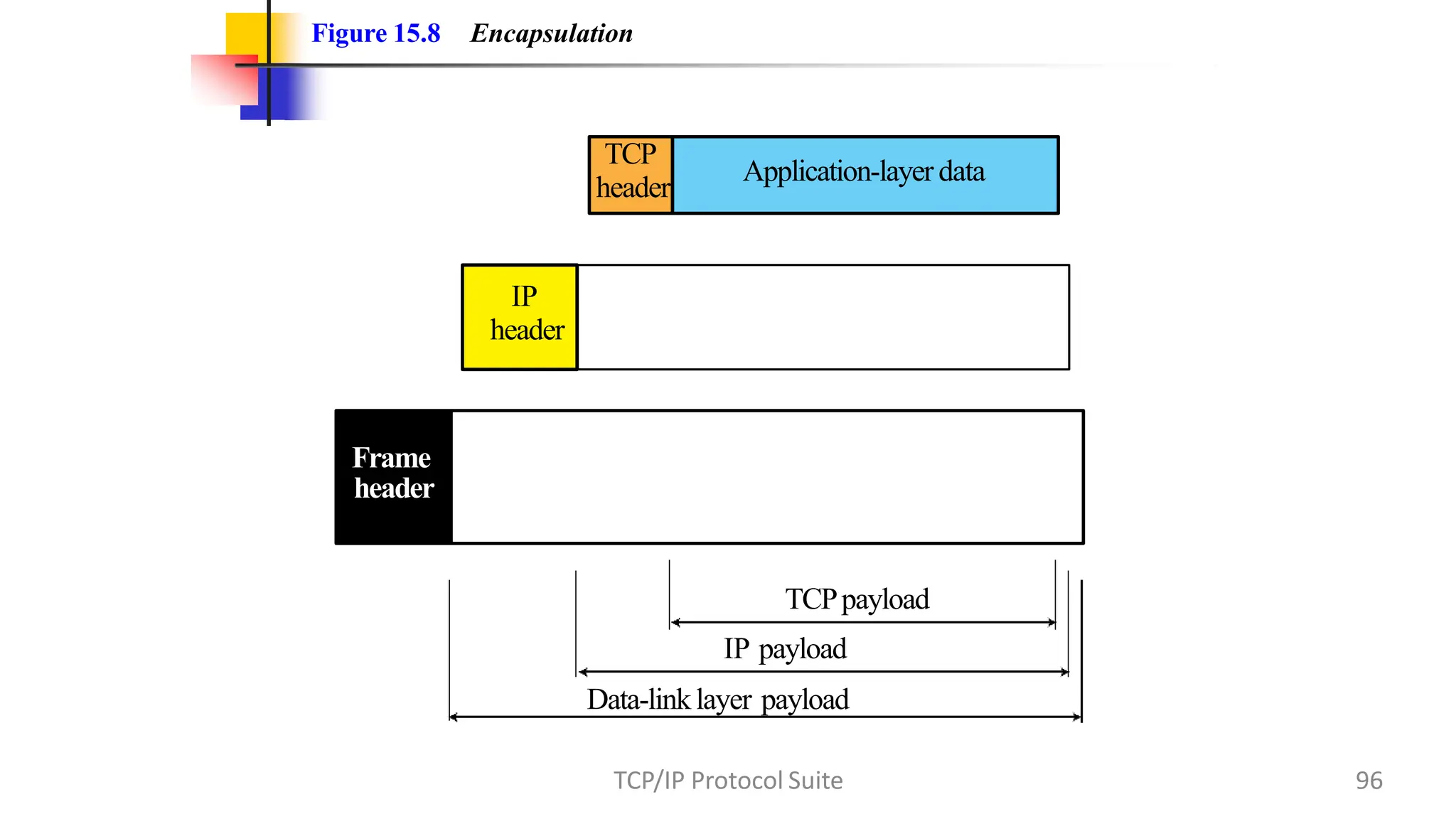
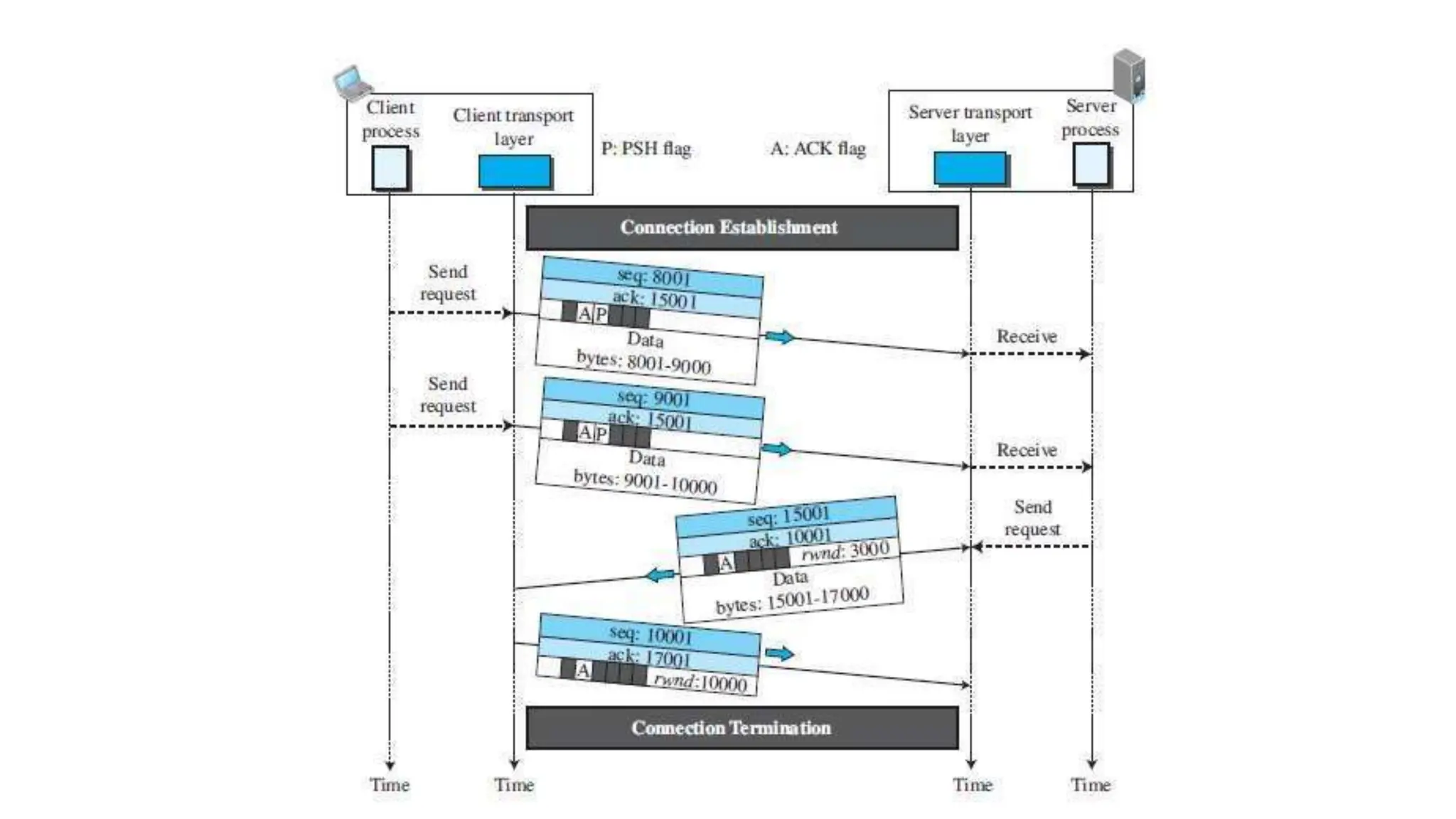
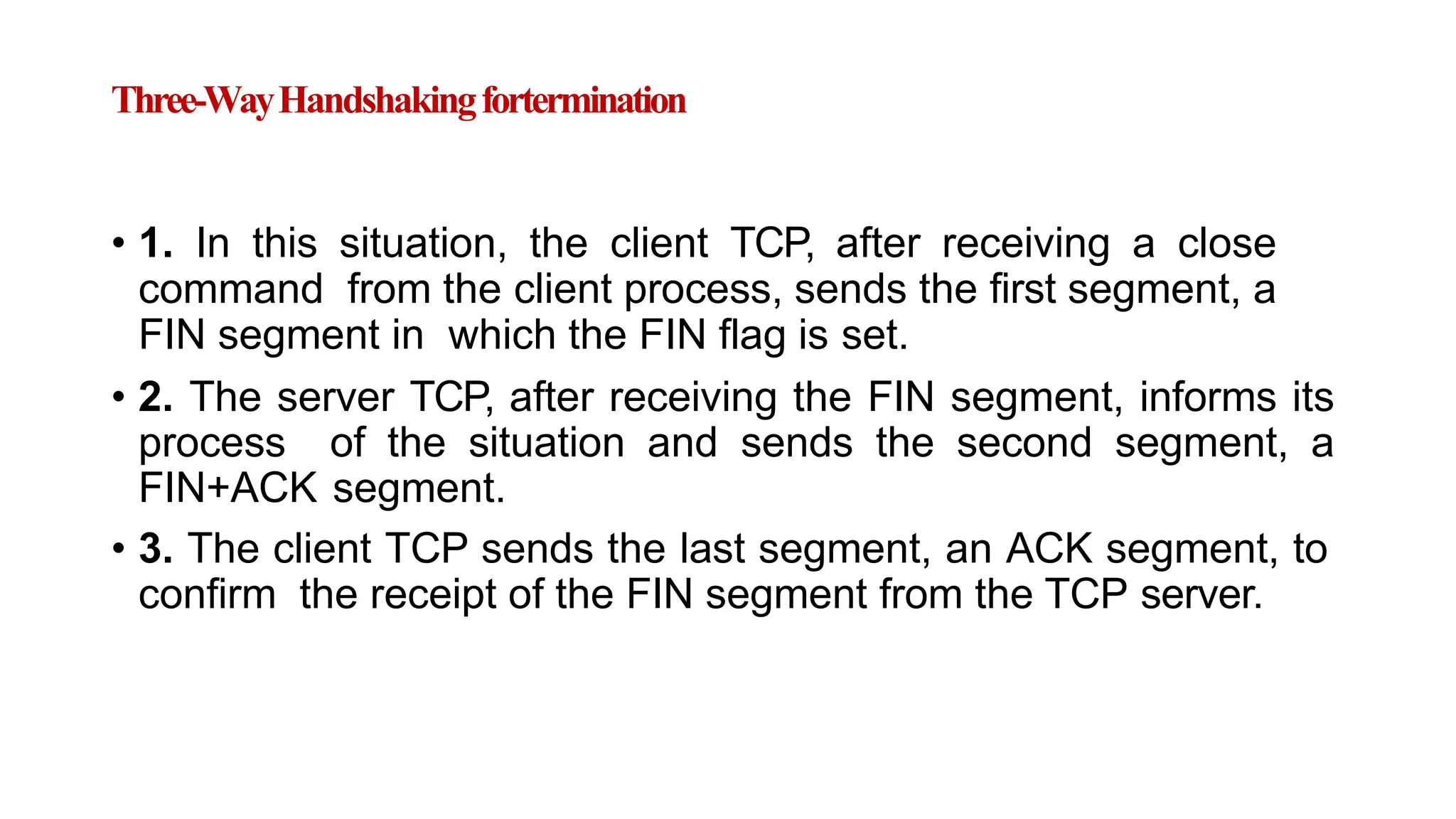
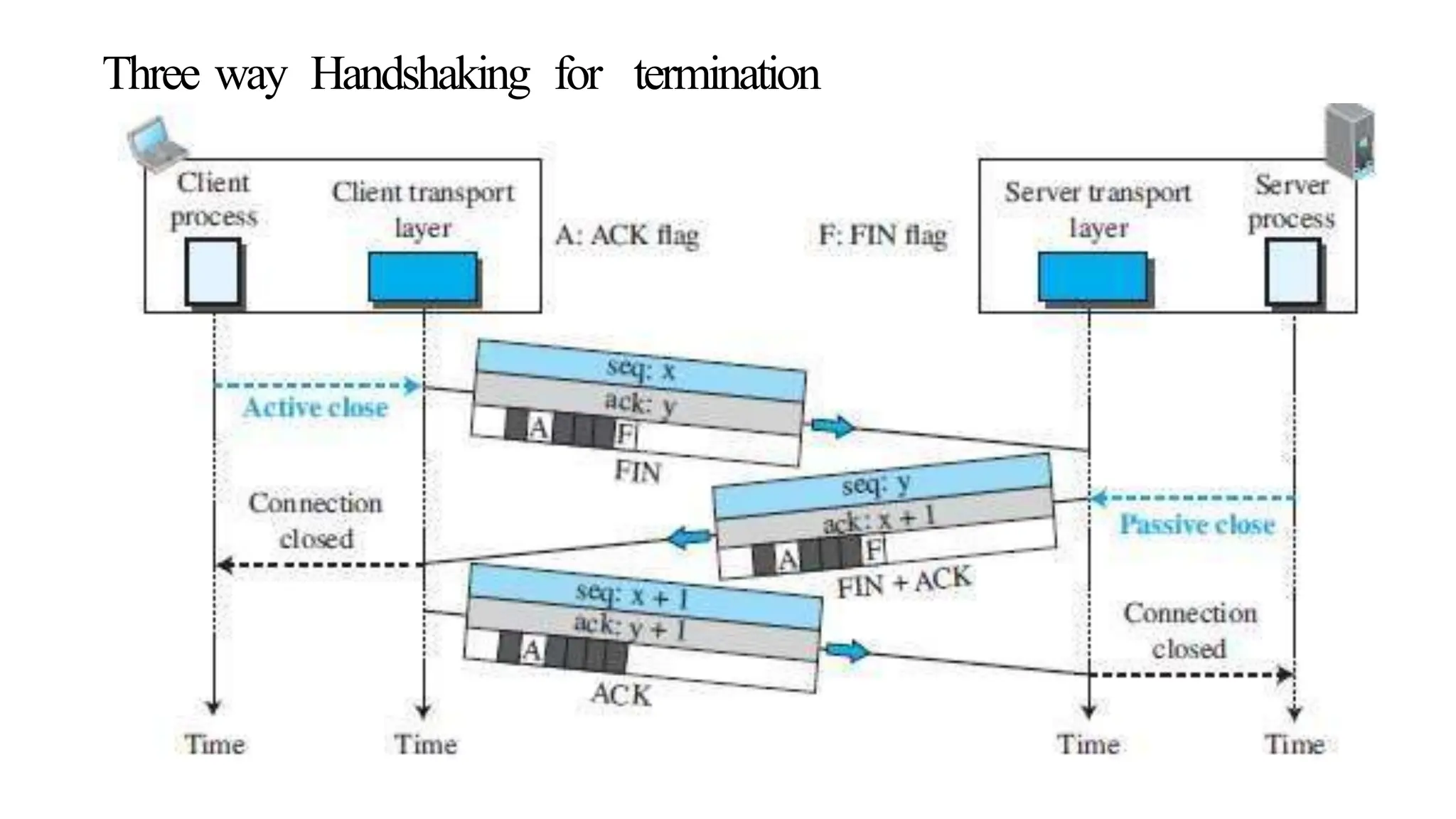
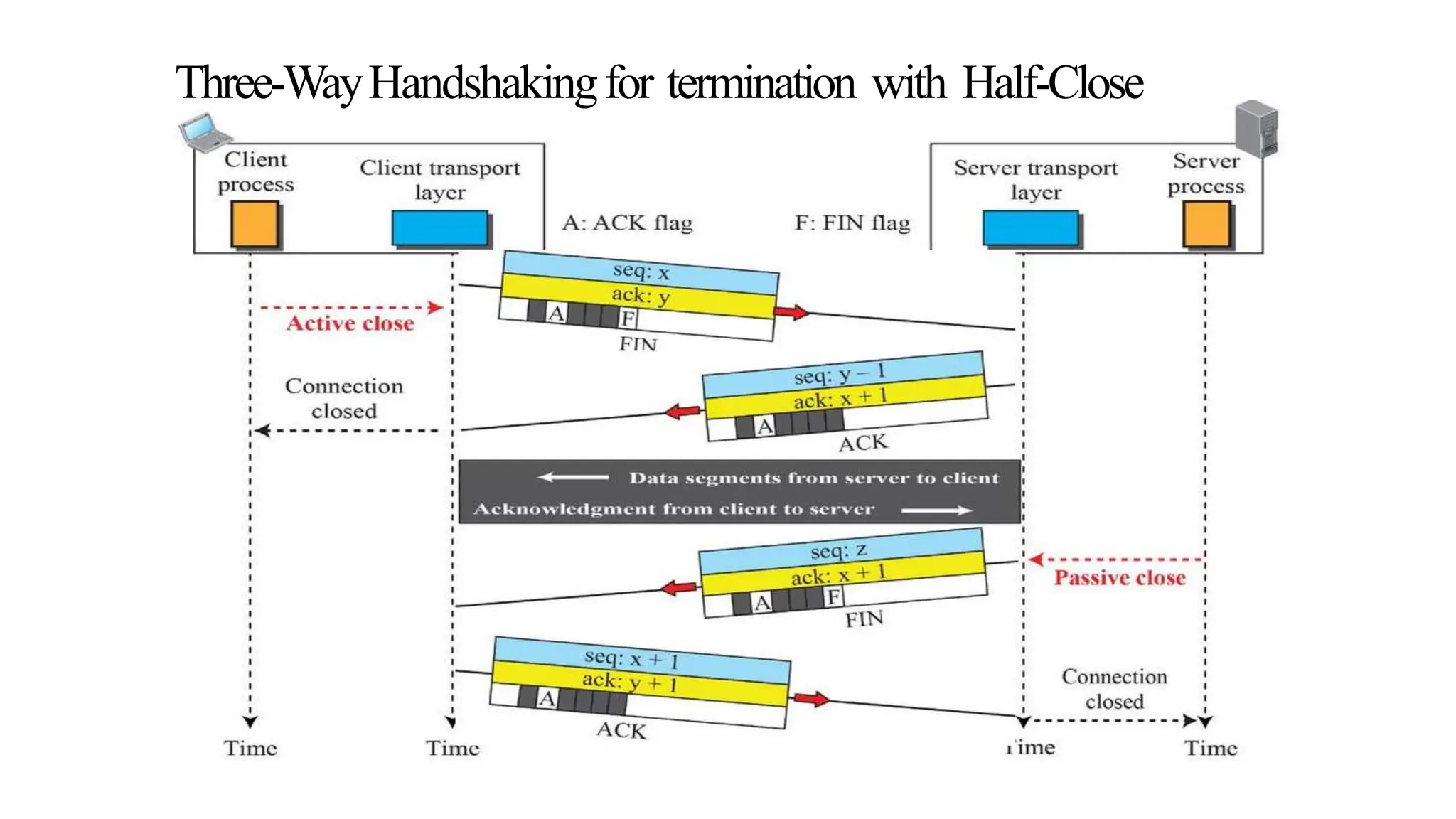
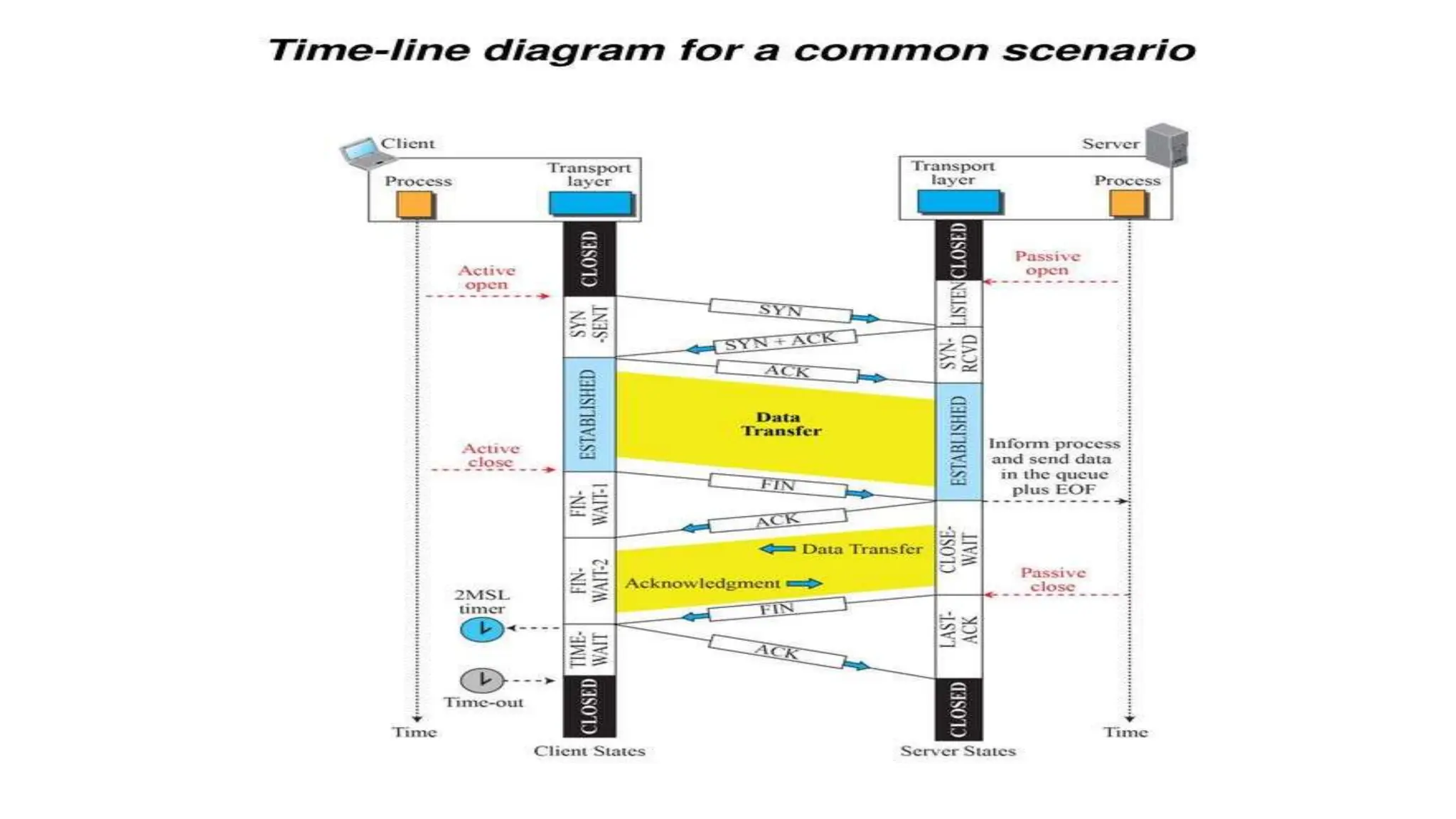
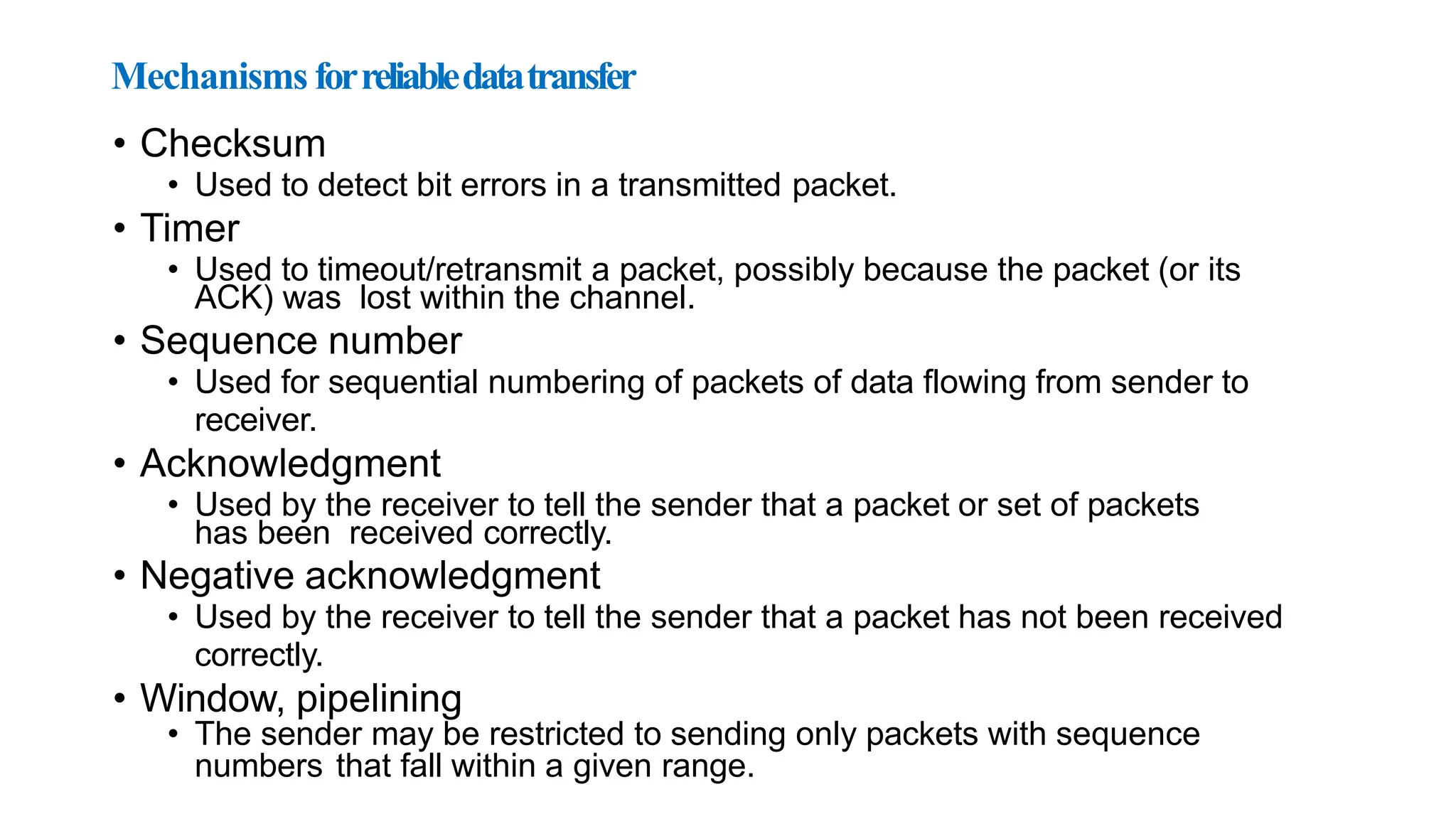
The transport layer provides process-to-process communication between applications on networked devices. It handles addressing with port numbers, encapsulation/decapsulation of data, multiplexing/demultiplexing data to the correct processes, flow control to prevent buffer overflows, error control with packet sequencing and acknowledgments, and congestion control to regulate data transmission and avoid overwhelming network switches and routers. Key functions of the transport layer enable reliable data transfer between applications across the internet.






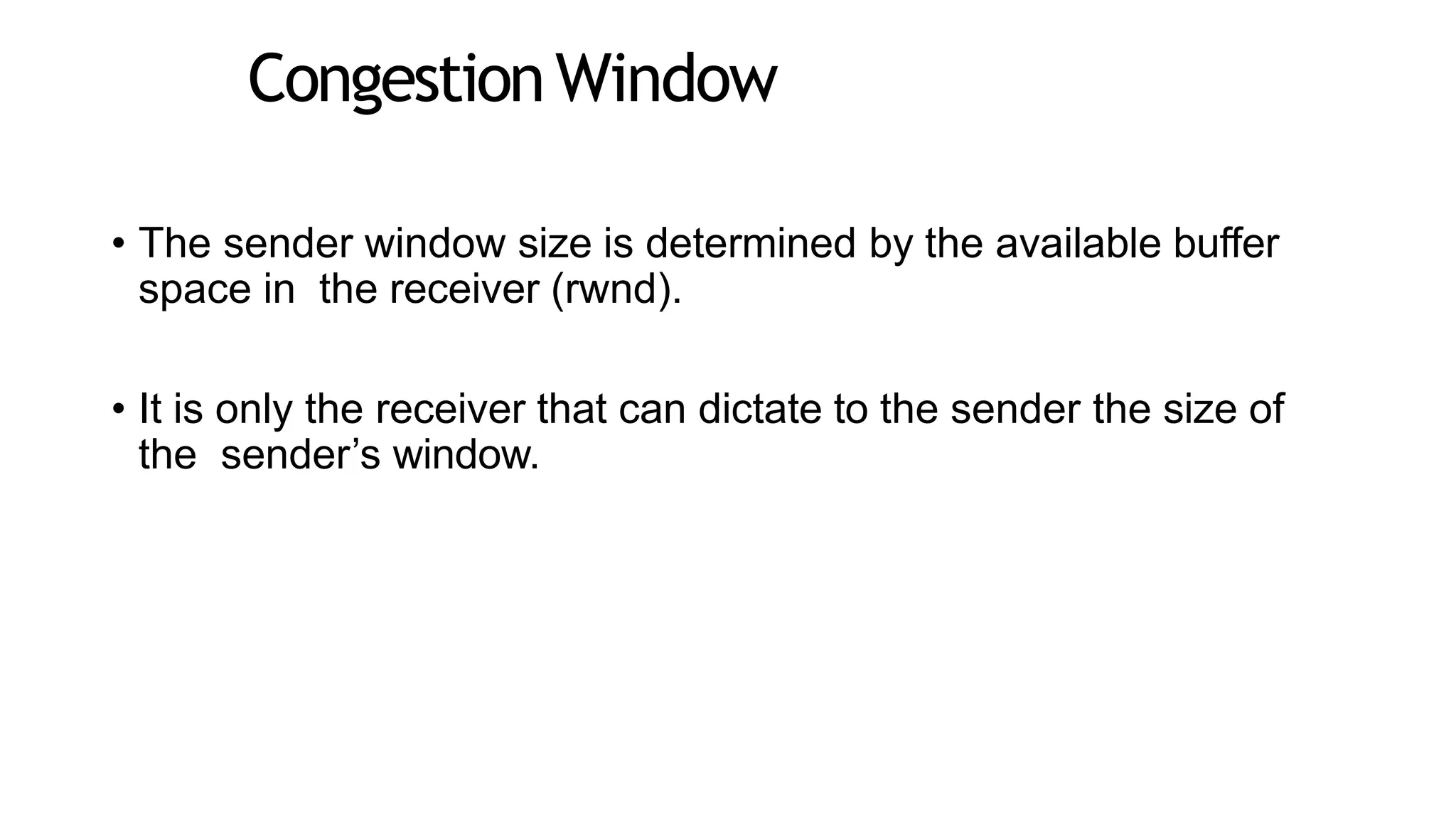



























![• Because TCP is not permitted to overflow the allocated buffer, we
must have
• LastByteRcvd – LastByteRead <= RcvBuffer
• The receive window, denoted rwnd is set to the amount of spare
room in the buffer:
• rwnd = RcvBuffer – [LastByteRcvd – LastByteRead]](https://image.slidesharecdn.com/module2-240414144505-e708ed94/75/Module-2-pptx-sdvsdcdssdfsdf-116-2048.jpg)