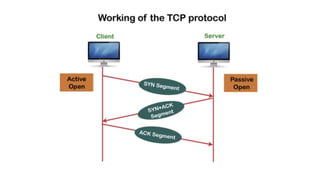
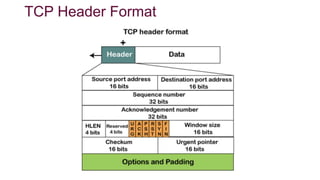
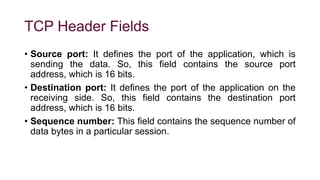
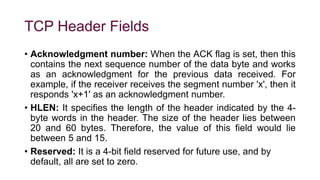
The document provides an overview of the Transmission Control Protocol (TCP), detailing its role as a connection-oriented transport layer protocol that ensures reliable data transmission by dividing data into packets, maintaining order, and using acknowledgment mechanisms. It also discusses TCP's key features, including full duplex communication, stream-oriented transmission, and flow control, alongside its advantages and disadvantages, such as overhead from headers. Additionally, the document outlines the TCP header format and its various fields, including source and destination ports, sequence and acknowledgment numbers, and control flags.