The document summarizes key topics related to data link control and computer networks, including:
- Announcements about an upcoming midterm exam covering data link control topics.
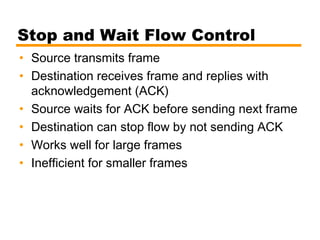
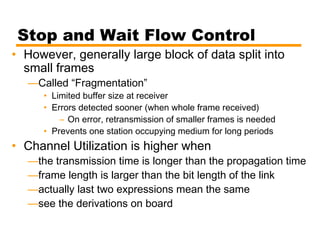
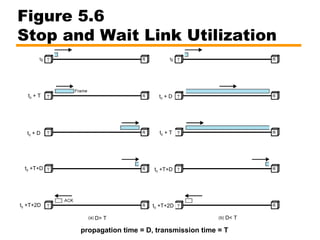
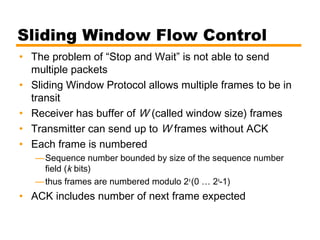
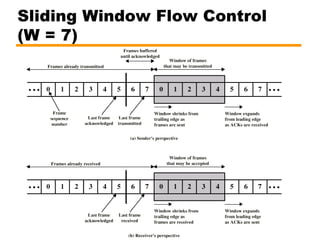
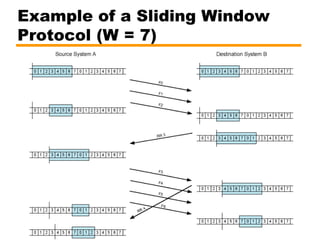
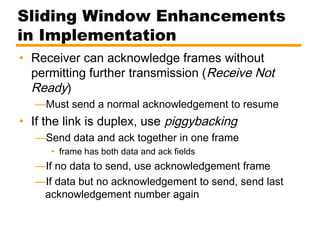
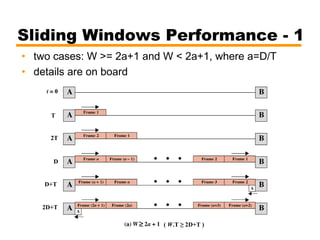
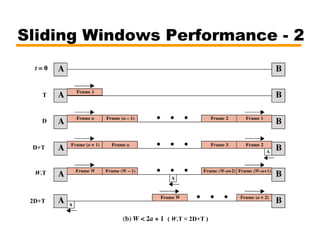
- An overview of different types of flow control mechanisms used in the data link layer, including stop-and-wait and sliding window protocols.
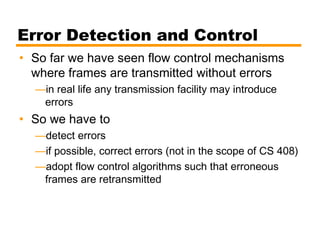
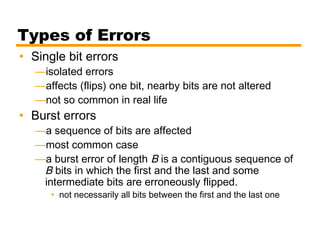
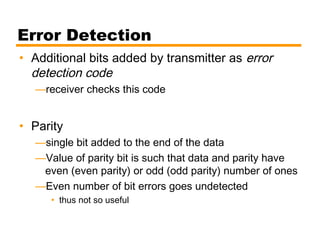
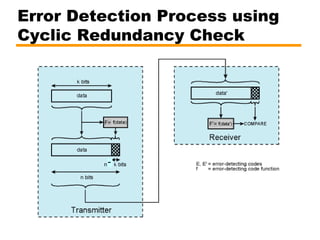
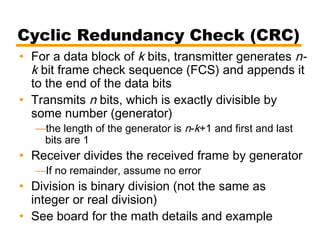
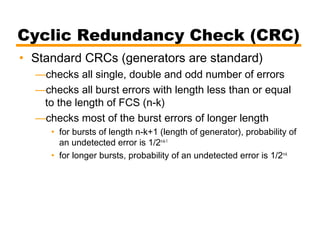
- Details on error detection techniques like parity checking and cyclic redundancy checks (CRCs).
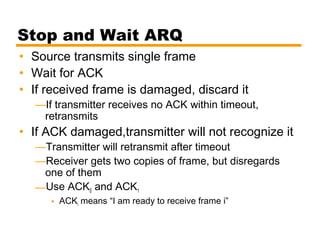
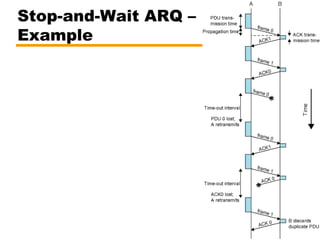
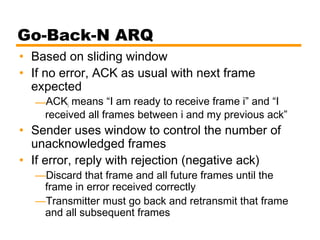
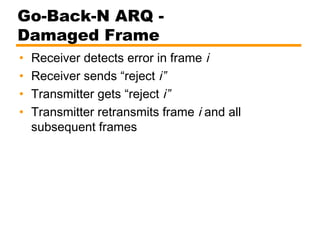
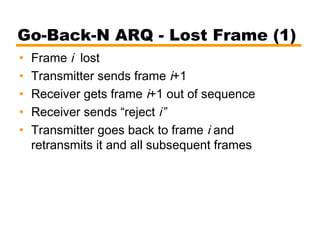
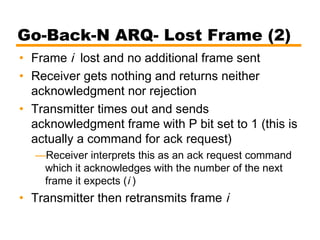
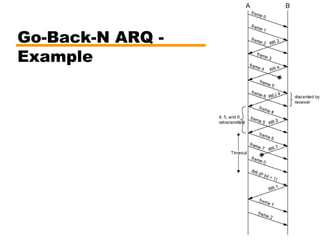
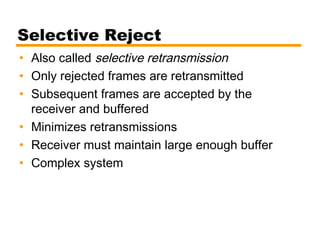
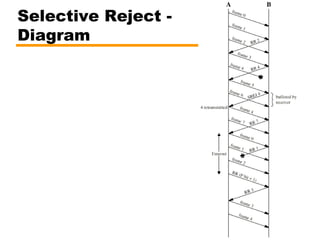
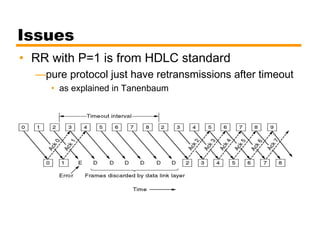
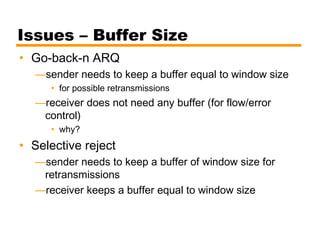
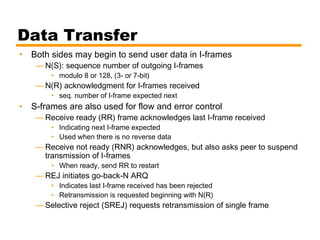
- Automatic repeat request (ARQ) error control mechanisms like stop-and-wait ARQ, go-back-N ARQ, and selective reject ARQ.
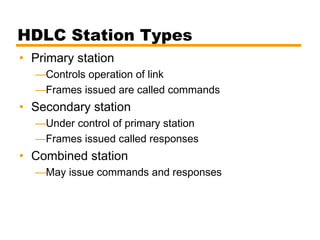
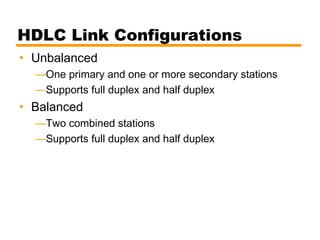
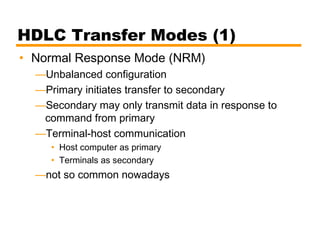
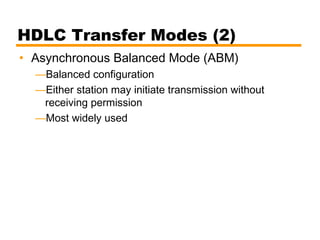
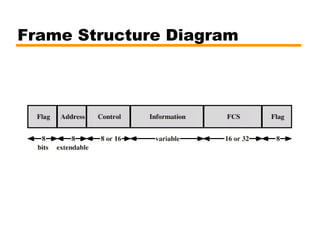
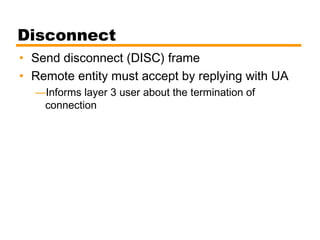
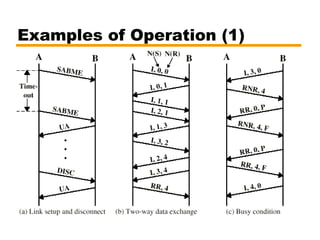
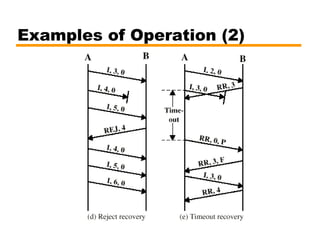
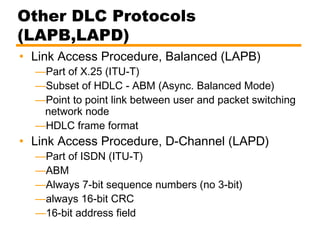
- An introduction to the High Level Data Link Control (HDLC) standard and its use of primary, secondary, and combined station types in different link configurations.