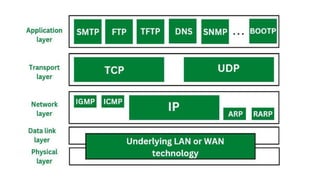
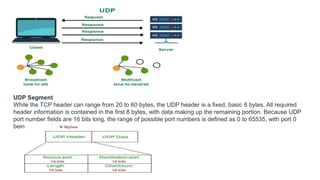
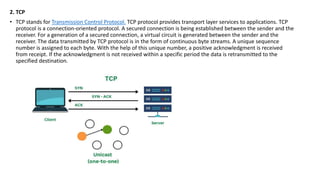
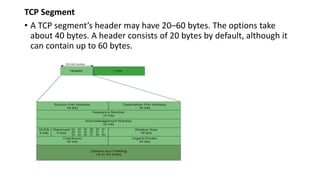
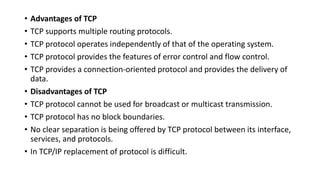
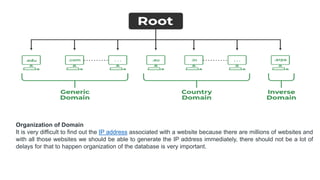
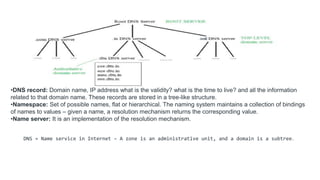
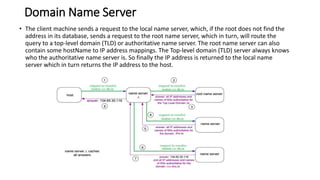
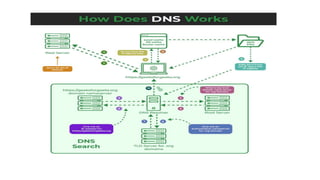
Transport protocols establish reliable communication between machines on a network. They provide services like error control, flow control, and multiplexing. The main transport protocols are TCP and UDP. TCP is connection-oriented and provides reliable, ordered delivery. UDP is connectionless and faster but unreliable. Both protocols use port numbers to identify sending and receiving processes and segment packet headers with fields like source/destination port and sequence numbers. DNS is an application layer protocol that maps domain names to IP addresses, enabling human-friendly web addresses. It uses a hierarchical system of root, TLD, and authoritative name servers to resolve names.