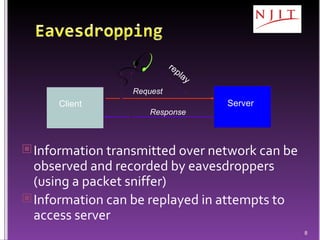
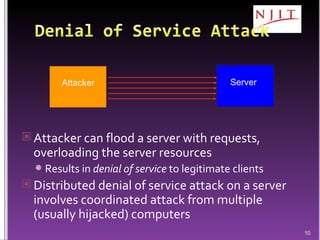
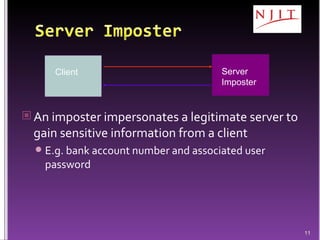
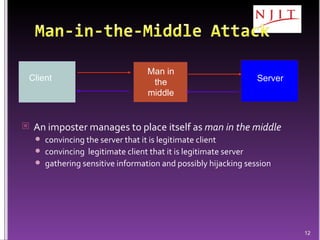
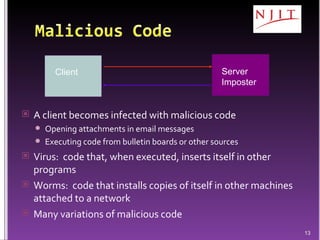
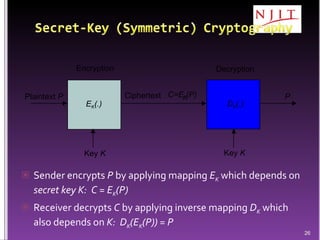
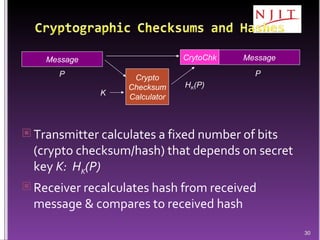
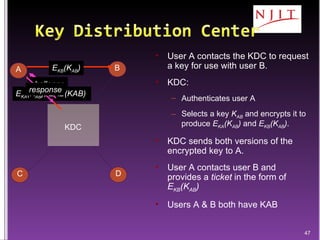
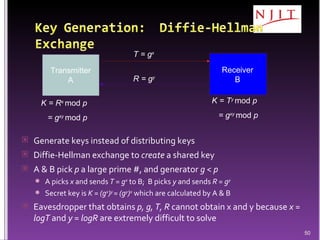
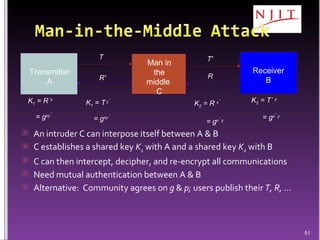
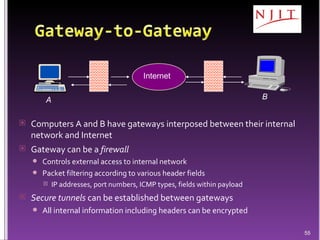
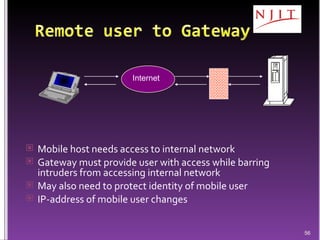
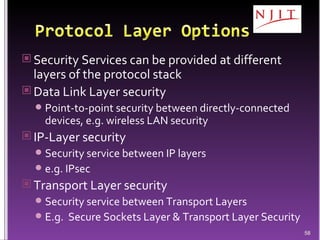
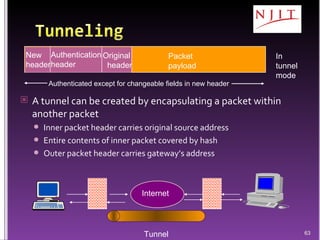
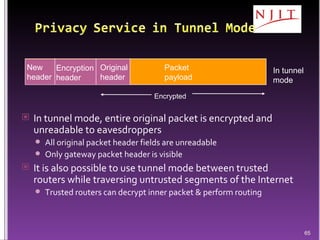
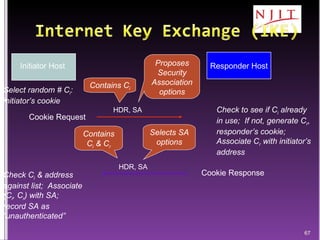
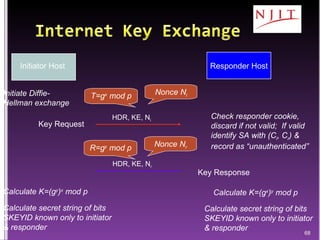
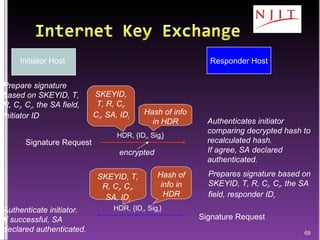
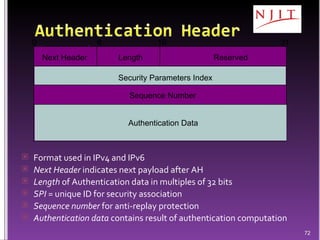
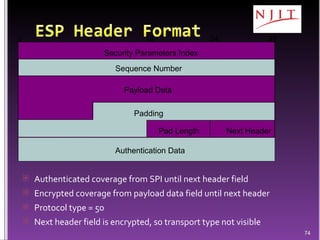
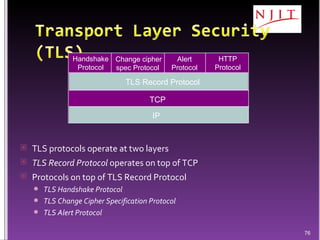
The document discusses network security threats and techniques. It begins by noting the importance of being prepared for attacks. It then describes various network security threats like eavesdropping, man-in-the-middle attacks, denial of service attacks, and malware. It also discusses network security requirements and various countermeasures like encryption, firewalls, and intrusion detection. Cryptographic techniques like public key cryptography, digital signatures, and key distribution protocols are explained as ways to provide security services over networks.























































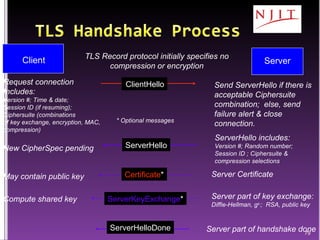
![Client’s part of key agreement: Diffie-Hellman g y ; RSA, random #s Change Cipher protocol message notifies server that subsequent records protected under new CipherSpec & keys Server changes CipherSpec Hash using new CipherSpec; allows server to verify change in Cipherspec Compute shared key Verify CipherSpec Client Server ClientKeyExchange [ChangeCipherSpec] Finished](https://image.slidesharecdn.com/note11-090518040248-phpapp02/85/Network-Security-80-320.jpg)
![Notify client that subsequent records protected under new CipherSpec & keys Client changes CipherSpec Hash using new CipherSpec; Client verifies new CipherSpec TLS Record protocol encapsulates application-layer messages Privacy through secret key cryptography Reliability through MAC Fragmentation of application messages into blocks for compression/encryption Decompression/Decryption/Verification/Reassembly Client Server Application Data [ChangeCipherSpec] Finished](https://image.slidesharecdn.com/note11-090518040248-phpapp02/85/Network-Security-81-320.jpg)
![Server requests certificate if client needs to be authenticated Client sends suitable certificate If server finds certificate unacceptable; server can send fatal failure alert message & close connection Client prepares digital signature based on messages sent using its private key Server verifies client has private key Client Server ClientHello ServerHello Certificate* ServerKeyExchange* CertificateRequest ServerHelloDone Certificate* ClientKeyExchange CertificateVerify* [ChangeCipherSpec] Finished Application Data [ChangeCipherSpec] Finished](https://image.slidesharecdn.com/note11-090518040248-phpapp02/85/Network-Security-82-320.jpg)