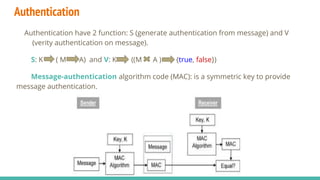
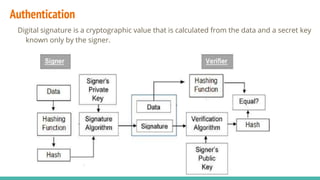
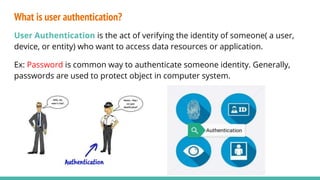
Security involves protecting systems, networks, programs and data from unauthorized access and modification. This is achieved through techniques like cryptography, authentication, firewalls, antivirus software and implementing security policies and defenses. Some common security threats include viruses, worms, hacking, denial of service attacks and password vulnerabilities. Different levels of computer security classification (A, B, C, D) provide increasing levels of protection and access control based on sensitivity of the data and systems.