The document discusses the history and concepts of cryptography, especially in the context of e-commerce. It explains how cryptography evolved from ancient times to modern applications. Symmetric and asymmetric encryption methods are described, including how public/private key pairs work. Digital signatures are introduced as a way to provide authentication, integrity, and non-repudiation for electronic transactions.
![Cryptography & E-Commerce Keeping your Secrets secret! © University of Glamorgan SLIDE “ Some simple yet secure cipher, easily acquired and easily read, should be introduced by which messages might to all intents and purposes be ‘sealed’ to any person but the recipient” Quarterly Review 1853, [The Victorian Internet, Tom Standage]](https://image.slidesharecdn.com/cryptographyande-commerceupdated-120215201600-phpapp01/75/Cryptography-and-E-Commerce-1-2048.jpg)

![Why use Cryptography? Three possible worries facing an e-commerce customer are; If I transmit a credit card number over the internet – can people other then the recipient read it? If I agree to pay £400 for goods – can this information be captured and changed? I am buying something from company X is it really company X? This raise three important Information Security issues : Confidentiality : protecting information from unauthorised disclosure; Integrity: protecting information from unauthorised modification, and ensuring that information is accurate and complete; Authentication – Ensuring the person you are making the transaction with who they say they are? We need to look at these in more depth… © University of Glamorgan SLIDE [Chan et al]](https://image.slidesharecdn.com/cryptographyande-commerceupdated-120215201600-phpapp01/75/Cryptography-and-E-Commerce-3-2048.jpg)







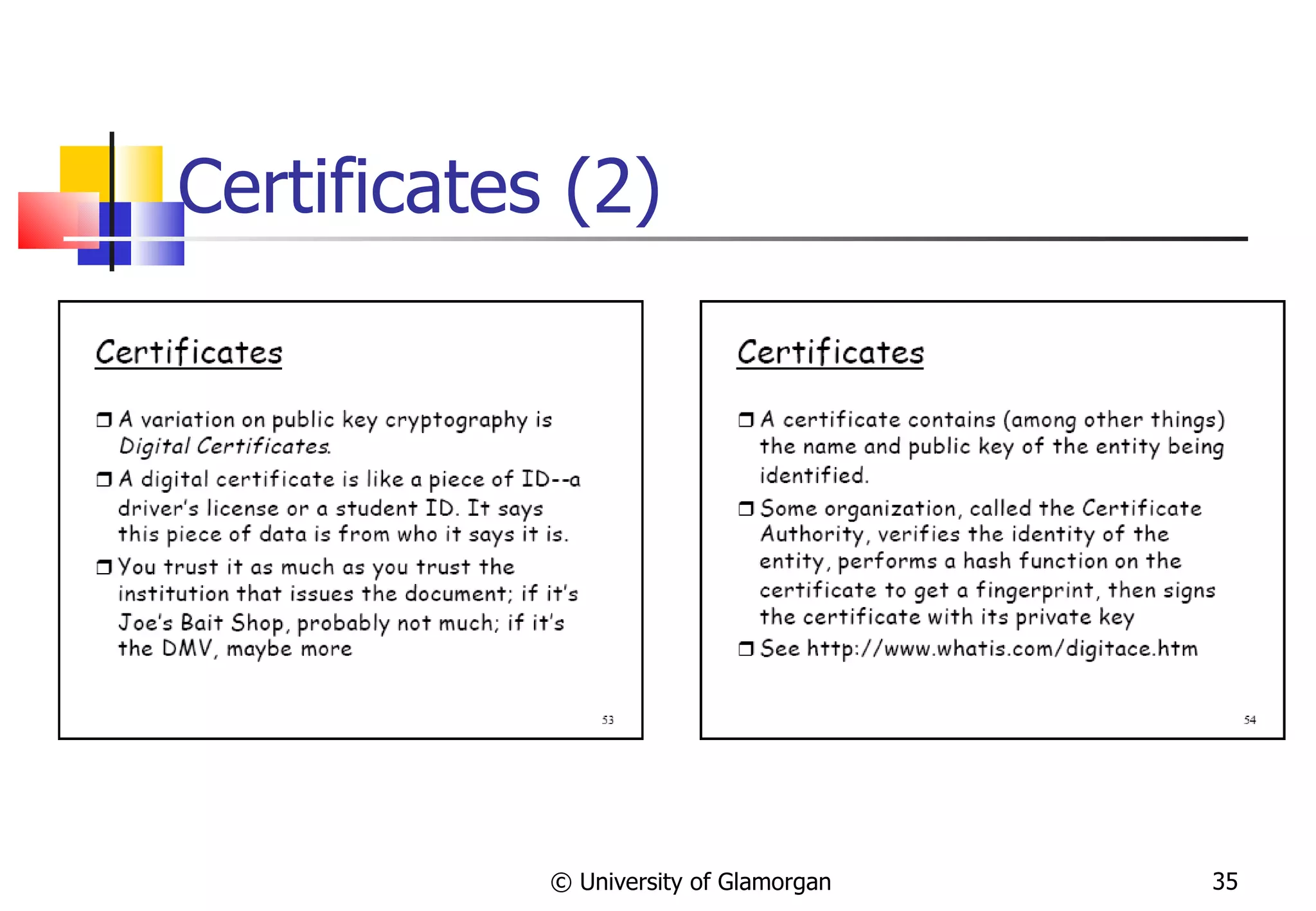
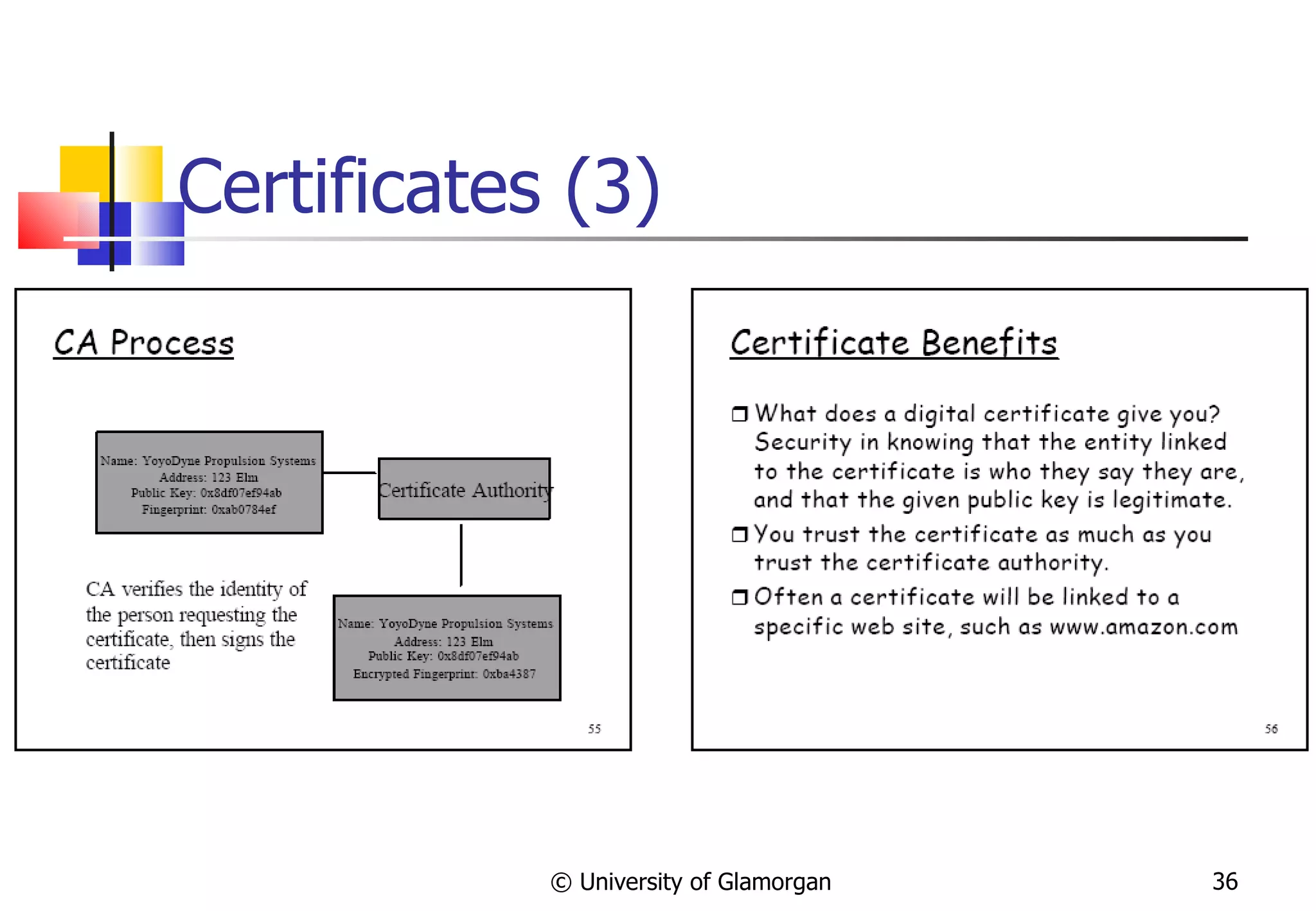
![Digital Signatures A digital signature is a protocol that produces the same effect as a real signature: it is a mark that only the sender can make, but other people can easily recognize as belonging to the sender. Just like read signatures, a digital signature is used to confirm agreement to a message. Digital signatures must meet two primary conditions: Unforgeable: If person P signs a message M with a signature S ( P , M ) it is impossible for anyone else to produce the pair [ M , S ( P , M )]. Authentic: If a person R receives the pair [ M , S ( P , M )] purportedly from P , R can check that the signature is really from P . Only P could have created this signature, and the signature is firmly attached to M . Two additional requirements are also desirable: Not alterable : After being transmitted, M cannot be changed by R or an interceptor . Not reusable : A previous message presented will be instantly detected by R . © University of Glamorgan WEB SLIDE 011110100101101](https://image.slidesharecdn.com/cryptographyande-commerceupdated-120215201600-phpapp01/75/Cryptography-and-E-Commerce-21-2048.jpg)
![Symmetric Key Digital Signatures © University of Glamorgan S sends sealed M to Arbiter SENDER K S M ARBITER Arbiter retrieves plaintext M from S M K S M K R S M Arbiter seals [ Message received from Sender E ( M , K S ), Identify of Sender S , and copy of plaintext M ] and sends all to R RECIPIENT WEB SLIDE 1 2 3](https://image.slidesharecdn.com/cryptographyande-commerceupdated-120215201600-phpapp01/75/Cryptography-and-E-Commerce-23-2048.jpg)
![Digital Signatures and Timestamps In order to stop a message that has been signed using a digital signature from being reused, we need to make use of timestamps. The protocol is the same as the asymmetric protocol for signing documents except that the message contains a time stamp. e.g. M = [ Message , Time-Stamp ] The timestamp will define when the message was sent. Two messages with the same contents and the same time-stamp will be ignored, thus a message can not be re-used. © University of Glamorgan A PRI M Encrypts message with B PUB and A PRI and then send the message SENDER M Decrypts message with B PRI and A PUB in order to derive M . RECIPIENT B PUB WEB SLIDE 1 2](https://image.slidesharecdn.com/cryptographyande-commerceupdated-120215201600-phpapp01/75/Cryptography-and-E-Commerce-25-2048.jpg)

![The International Context The ECA (2000) in the UK relates to some recent European Directives; The Act aims to implement some aspects of the EU Electronic Signatures Directive (1999/93/EC), which was adopted on 13 December 1999. This was aimed at the legal recognition of electronic signatures in the E.U. The Act also supports the EU E-Commerce Directive, which seeks to remove barriers to the development of electronic commerce in the internal market. The Act also meets the Cryptography Guidelines, published by the Organisation for Economic Co-operation and Development (OECD) (1997) The Act is also compatible with the United Nations Commission on International Trade Law (UNCITRAL) Model Law on Electronic Commerce The UK differs from the global trend of defining as legal, any signature which has a certificate attached as legal binding. Instead it gives electronic signatures the same status as handwritten in English law – evidential method of authenticating a document [Computer Law, Reed and Angel] © University of Glamorgan](https://image.slidesharecdn.com/cryptographyande-commerceupdated-120215201600-phpapp01/75/Cryptography-and-E-Commerce-28-2048.jpg)





![SET Transaction SET currently only supports credit card payments online not debit cards, or stored value payments – other protocols are likely to arise to address these issues. Open standard so a number of implementations have arisen.; Cyber cash supports SET standard RSA Data Security - set compliant software – S/PAY Ultimately not technology or standard itself that will make this a successful protocol but the fact that it is backed by the two largest credit card associations (MasterCard & Visa) © University of Glamorgan 1. Request Transaction 2. Acknowledgement request 3. Purchase order 4. Purchase order verification 5. Customer Payment data 6. Verify customer data 7. Status Query 8. Purchase Status information 9. Request payment 10. Verify payment [Redrawn from Ghosh p132] An overview of the purchase / payment process used by SET (Secure Electronic Transactions) Consumer Bank Vendor](https://image.slidesharecdn.com/cryptographyande-commerceupdated-120215201600-phpapp01/75/Cryptography-and-E-Commerce-39-2048.jpg)
![B2C: SET protocol Authentication uses symmetric key distribution w/o server Digests of the order information - OI - and payment information - PI - are calculated - H[OI] and H[PI] These two are concatenated and signed DS Merchant gets OI, H[PI] & DS - hence can find H[PI] Issuer gets PI, H[OI] & DS - hence can find H[OI] Merchant and issuer can see only info. they should see, but can verify details of the order and payment Suppose some of the information is tampered with. When the DS is decrypted merchant finds a different H[PI] issuer finds a different H[OI] © University of Glamorgan OHP Handout Customer message to Merchant Customer message to Bank M2 Message Digest M1 Message Digest M3 Message Digest Encrypted with Bank Key Only the bank can read it Encrypted with Merchant Key Only the merchant can read it M3=Digest(M1+M2) Dual Customer Signature Encrypted with Private Key](https://image.slidesharecdn.com/cryptographyande-commerceupdated-120215201600-phpapp01/75/Cryptography-and-E-Commerce-40-2048.jpg)