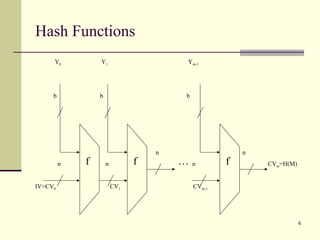
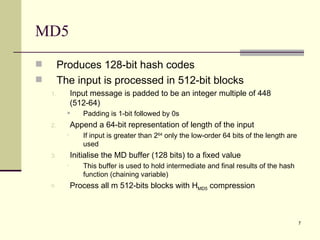
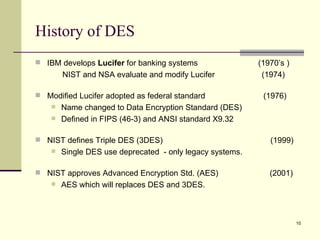
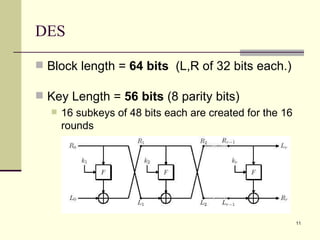
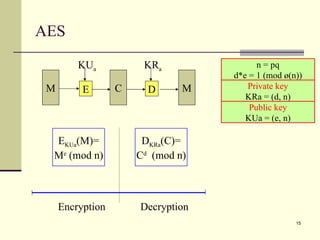
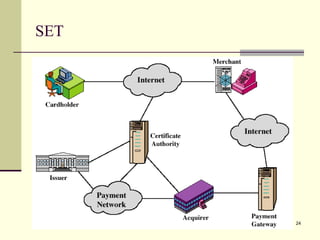
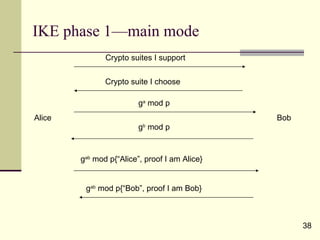
The document discusses various topics related to security in e-commerce including cryptography mechanisms like symmetric and asymmetric encryption, hashing functions, and encryption algorithms like DES, AES, and RSA. It also covers security protocols like SSL/TLS, SET, S/MIME, and SSH. IPSec and its components AH, ESP and IKE are explained. The IKE phases including phase 1 for mutual authentication and phase 2 for establishing session keys are summarized.