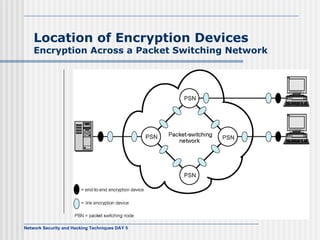
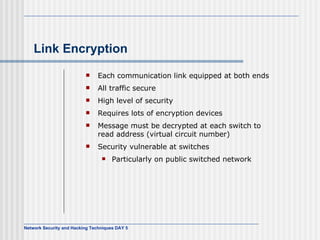
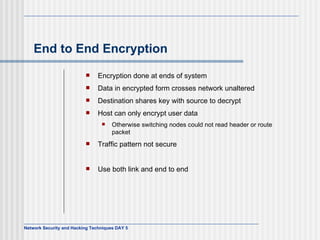
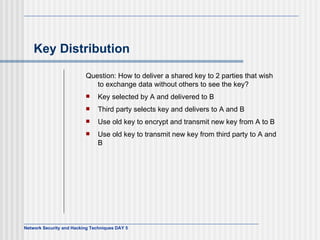
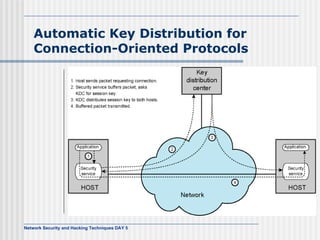
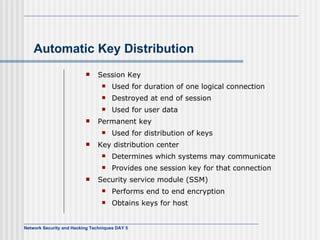
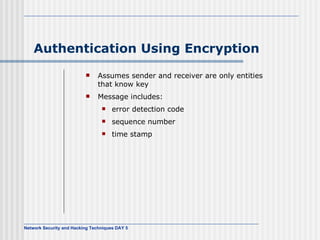
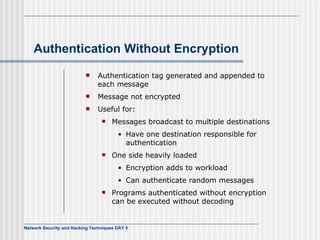
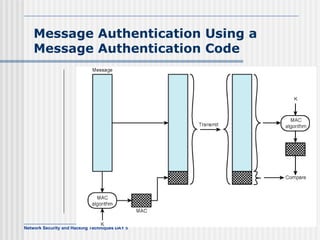
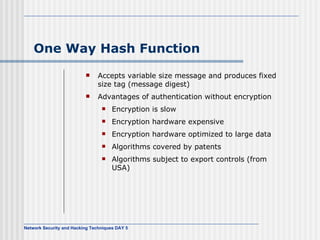
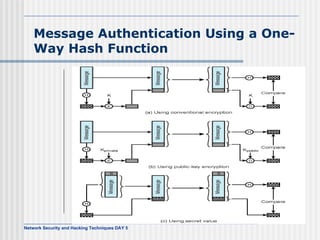
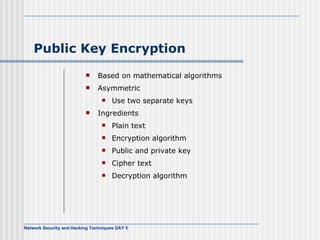
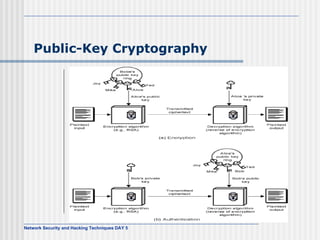
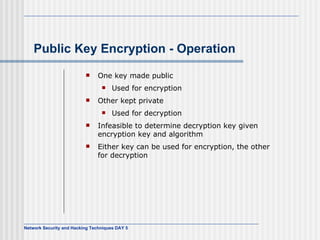
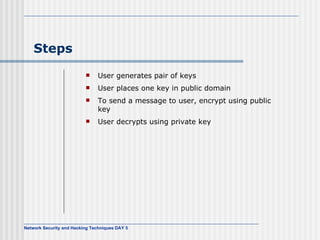
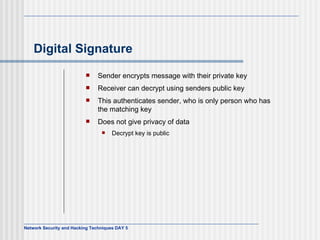
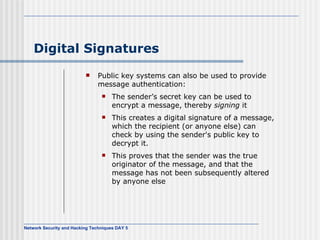
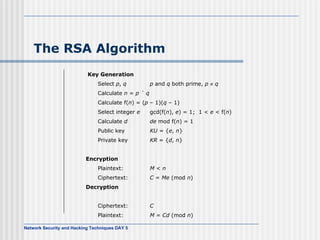
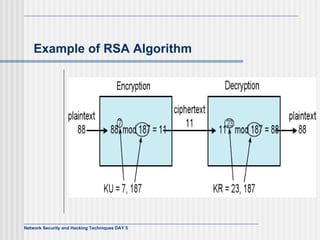
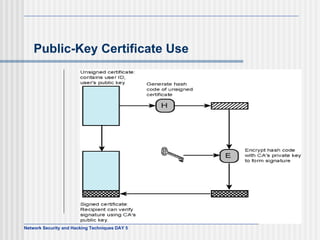
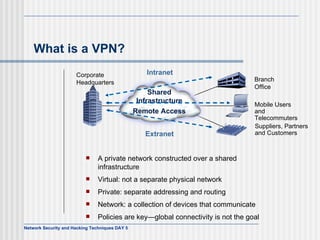
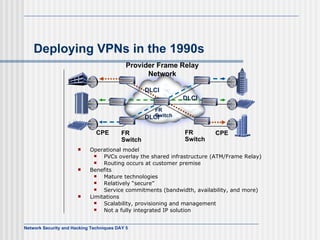
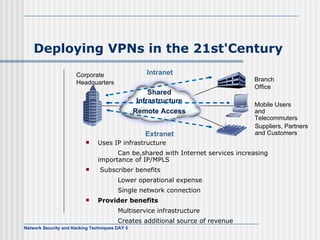
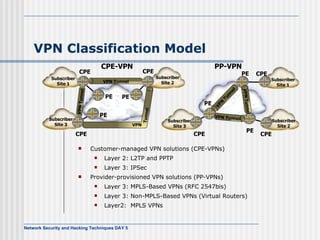
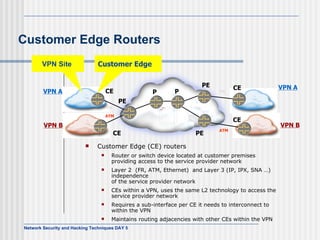
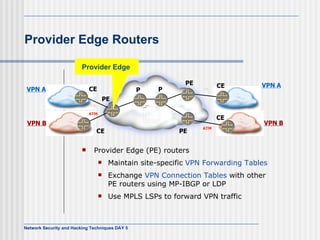
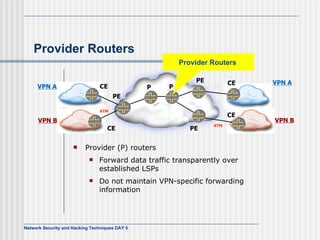
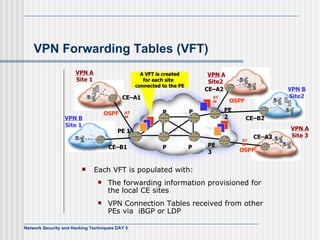
This document discusses network security and honeypot techniques. It provides an overview of honeypots, including their value in learning about blackhat hacking tools and techniques. It describes different types of honeypots, including first and second generation honeypots, and how they aim to gather information while being difficult to detect. The document also briefly mentions honeynets and the Honeynet Project, an organization dedicated to honeypot research.

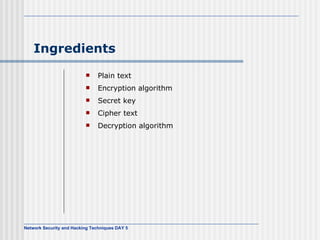
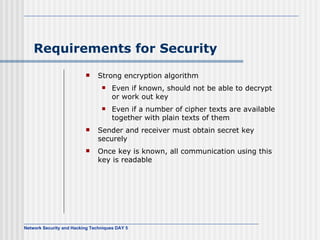
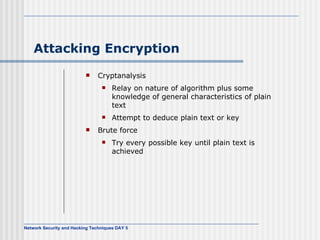
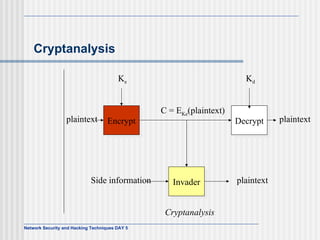

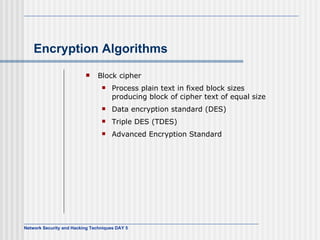
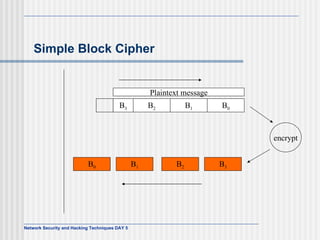
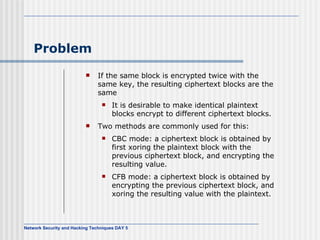
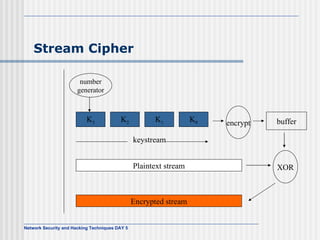
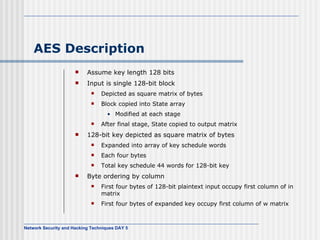
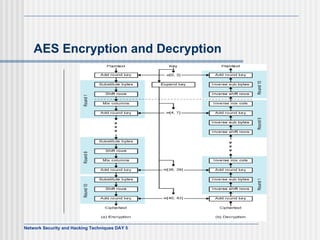
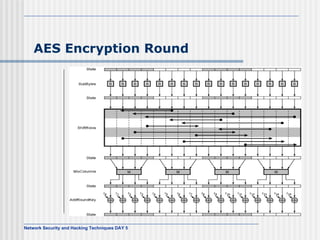
![AES Comments (1) Key expanded into array of forty-four 32-bit words, w[i] Four distinct words (128 bits) serve as round key for each round Four different stages One permutation and three substitution Substitute bytes uses S-box table to perform byte-by-byte substitution of block Shift rows is permutation that performed row by row Mix columns is substitution that alters each byte in column as function of all of bytes in column Add round key is bitwise XOR of current block with portion of expanded key](https://image.slidesharecdn.com/day5-090721102543-phpapp01/85/Day5-32-320.jpg)