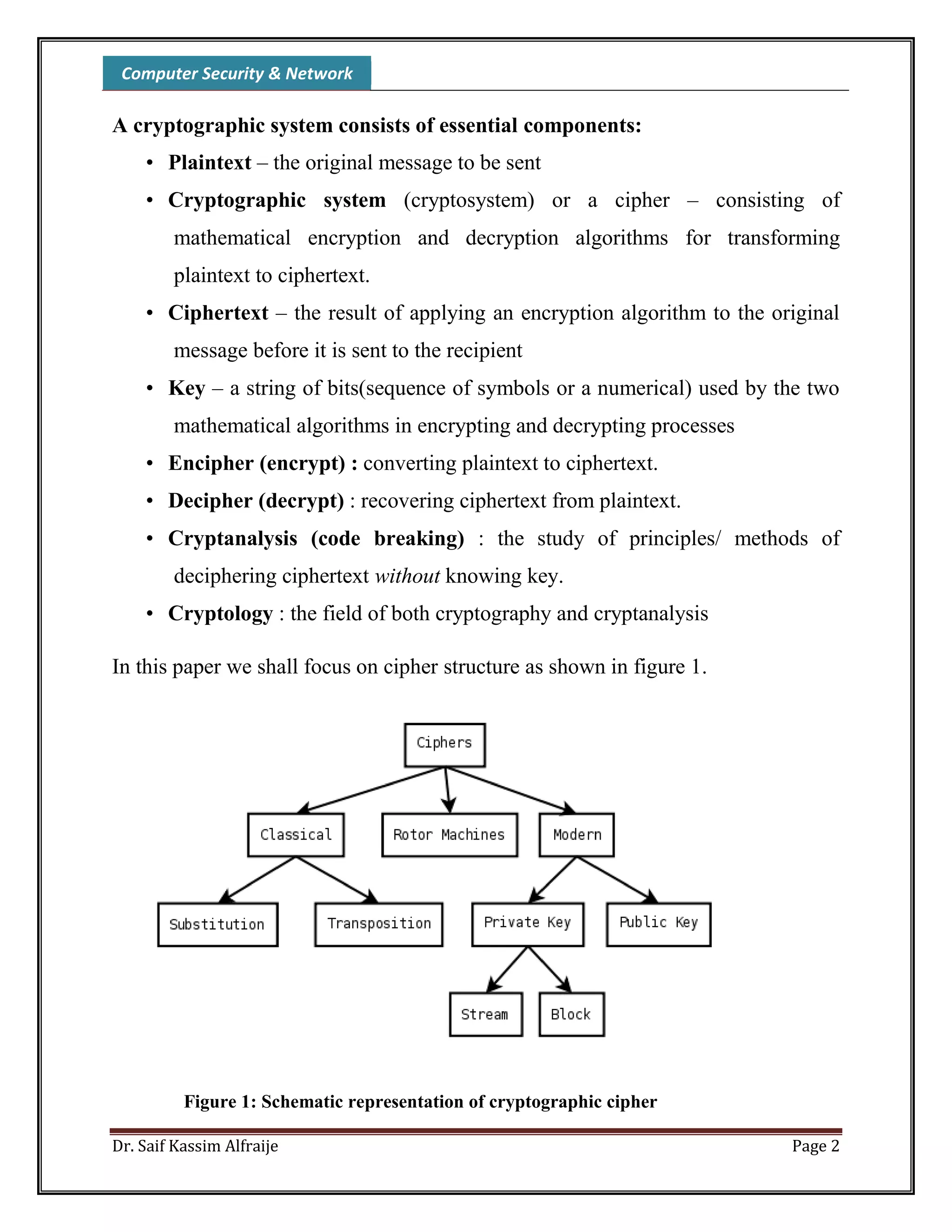
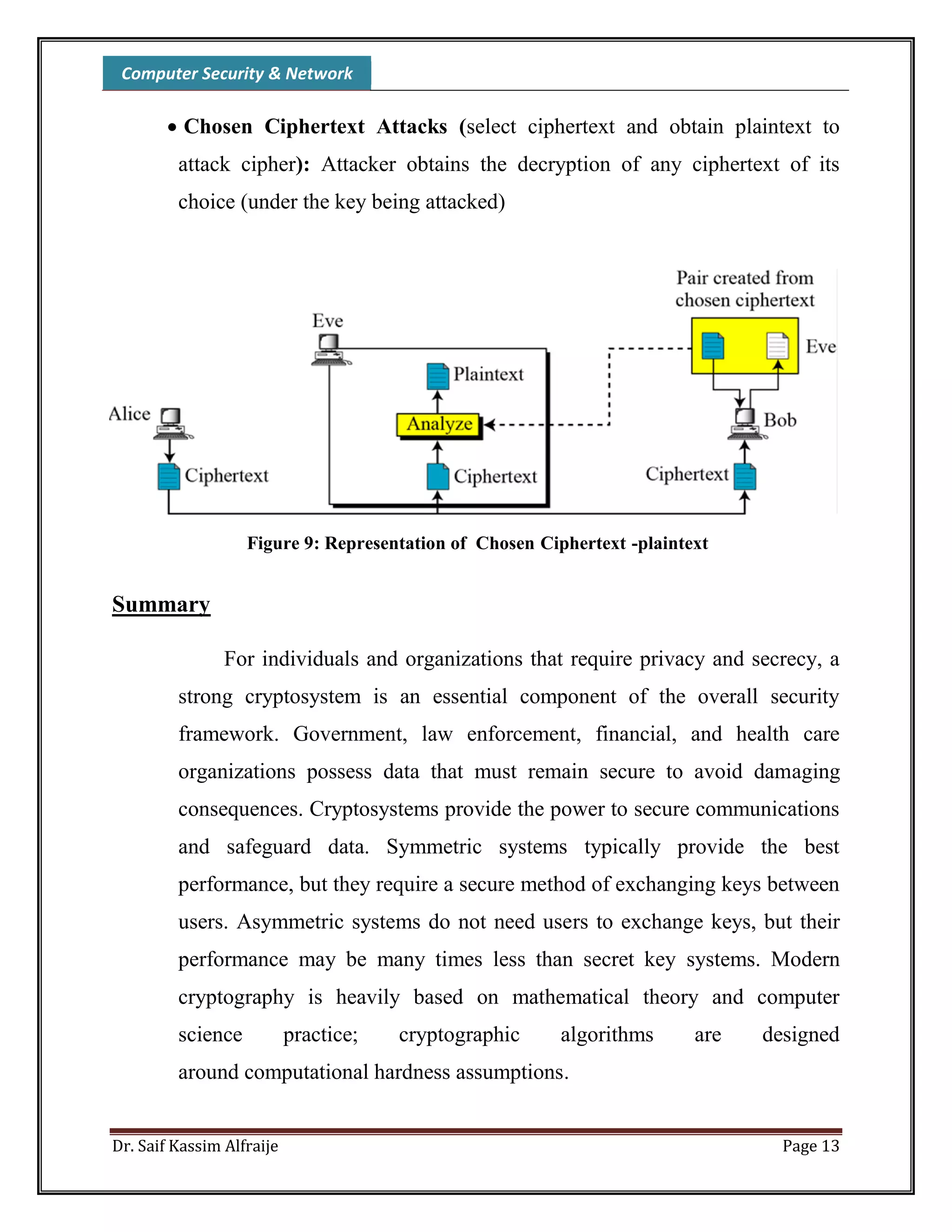
This document discusses computer security and network cryptography. It begins by explaining how organizations can use cryptosystems like symmetric and asymmetric encryption to protect data. Symmetric encryption is faster but requires secure key exchange, while asymmetric encryption uses public and private key pairs. The document then defines cryptography terminology and components like plaintext, ciphertext, encryption, decryption, and cryptanalysis. It describes techniques like substitution and transposition ciphers. The rest of the document discusses encryption models, algorithms, and cryptanalysis methods like ciphertext-only and known-plaintext attacks.