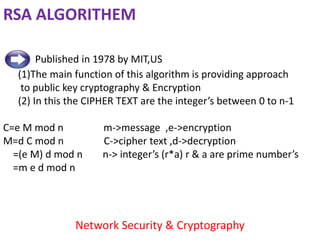
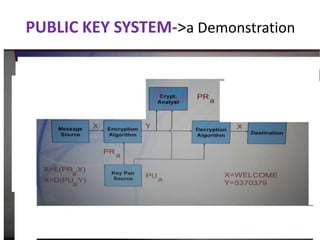
This document summarizes a presentation on network security and cryptography. The presentation covers the objectives of security, password auditing, data security, and authentication. It also discusses encryption, decryption, public and private key cryptography, digital signatures, and the RSA algorithm. The presentation includes a demonstration of a public key system and concludes by emphasizing the importance of securing data through cryptography and network security techniques.