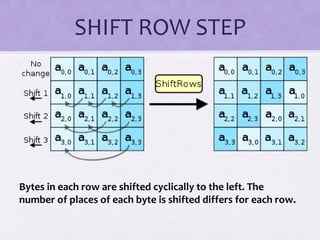
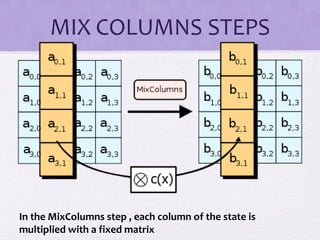
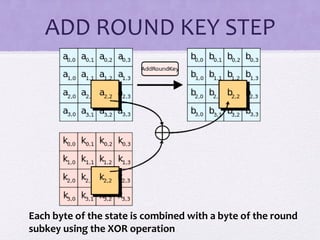
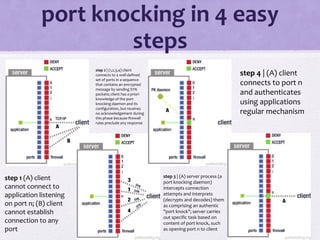
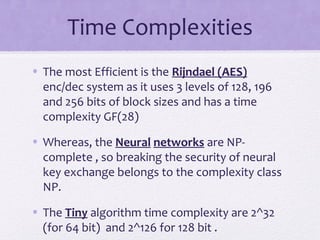
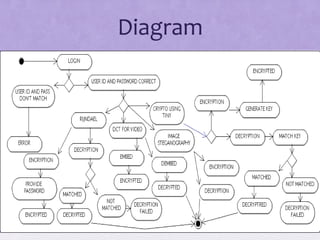
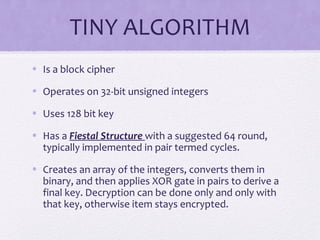
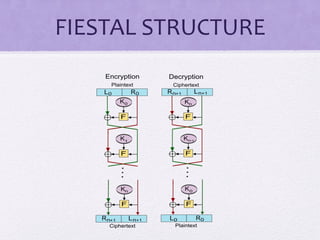
The document discusses various algorithms and techniques in cryptography and network security, highlighting the importance of secure communication in the presence of adversaries. It presents a range of methods including the Tiny algorithm, image and audio steganography, the Rijndael algorithm, and a hybrid port knocking system to enhance security. The proposal aims to combine these techniques to mitigate individual weaknesses and improve the overall security of file sharing.








![SUB BYTES STEP
In the SubBytes step, each byte in the state is replaced with its
entry in a fixed 8-bit lookup table, S;
B[I,j]=S(a[I,j])](https://image.slidesharecdn.com/majorppt-140530022614-phpapp01/85/Cryptography-and-network-security-12-320.jpg)