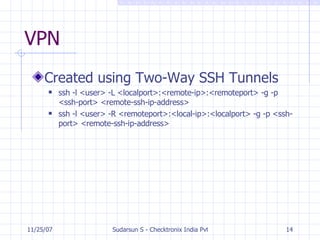
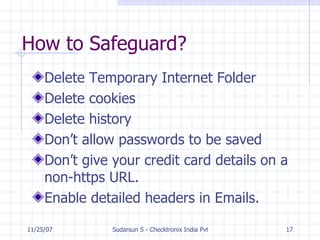
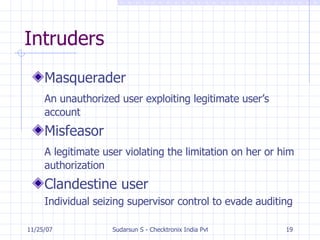
The document discusses various topics related to practical network security including security threats, data security, private communication over public channels, security services, applications that provide security like VPNs and firewalls, types of intruders, intrusion detection, and references for further information. It addresses confidentiality, authenticity, integrity, and non-repudiation as security services and discusses tools like firewalls, intrusion detection, and spam filters that can help safeguard networks.
![Practical Network Security Sudarsun S Checktronix India Pvt Ltd Chennai 600034 [email_address]](https://image.slidesharecdn.com/net-sec-1196005564233590-3/75/Net-Sec-1-2048.jpg)