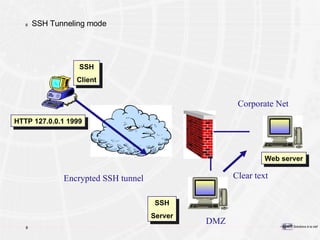
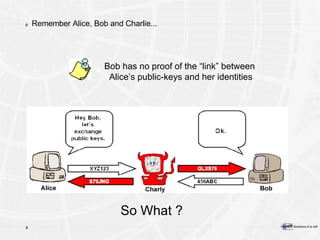
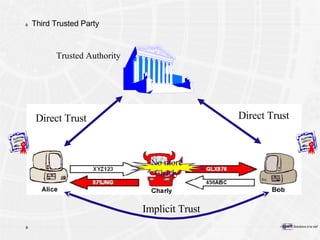
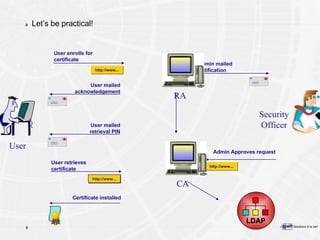
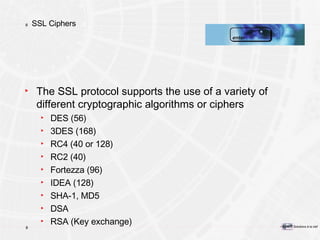
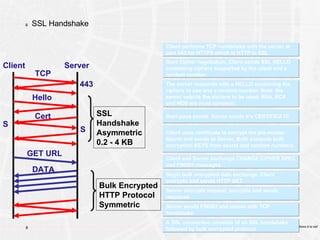
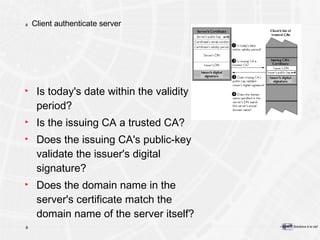
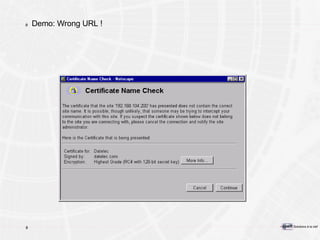
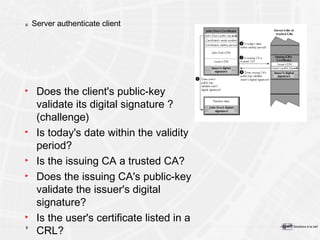
The document provides an overview of a course on PKI (Public Key Infrastructure) technology. It outlines the topics that will be covered over two days, including secret key cryptography algorithms like AES and RSA, digital certificates, certificate authorities, and practical PKI applications like S/MIME, SSL, and IPSEC. The objectives of the course are to understand cryptographic fundamentals, public key infrastructure elements and how they interact, and why PKI is useful for enabling e-commerce and enhancing security.



































































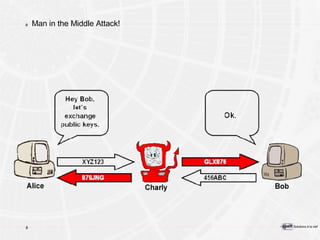



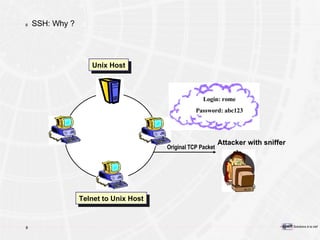
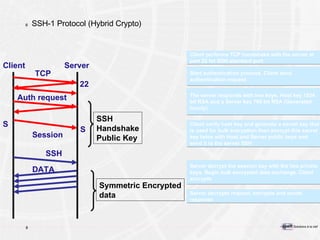


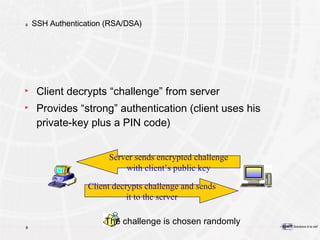
























































![Pour plus d’informations e-Xpert Solutions SA Sylvain Maret Route de Pré-Marais 29 CH-1233 Bernex / Genève +41 22 727 05 55 [email_address]](https://image.slidesharecdn.com/introductiontopkitechnology-090502145056-phpapp02/85/Introduction-To-PKI-Technology-192-320.jpg)