Embed presentation
Downloaded 81 times

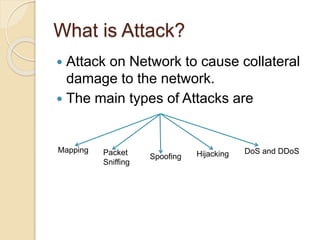

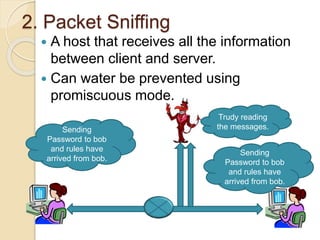


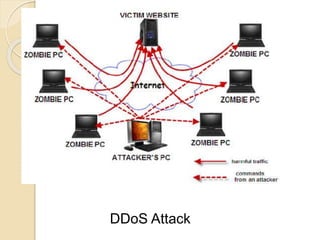

This document discusses various types of network attacks and countermeasures. It describes mapping to study a victim's network before attacking, packet sniffing where a host can read unencrypted communication, spoofing where an attacker takes a target's IP address to remain anonymous, and DoS/DDoS attacks which aim to overload services and bring them down. Hijacking combines different attack techniques to disrupt an entire network. The document provides details on each attack method and their techniques.







