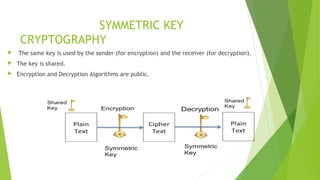
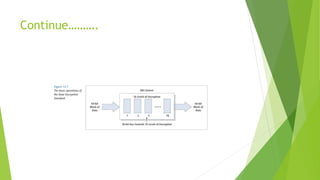
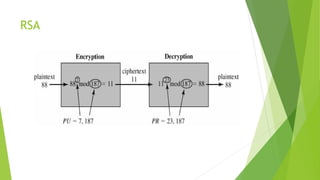
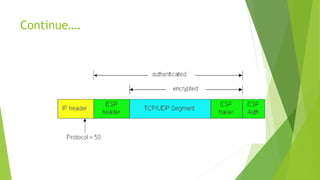
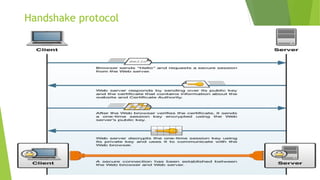
This document provides an overview of network security concepts including cryptography, digital signatures, security at various layers, and firewalls. It discusses cryptography principles like plaintext, ciphertext, and keys. Symmetric and asymmetric key cryptography algorithms are explained along with digital signatures and hashing. Network layer security standards like IPsec and its authentication header and encapsulating security payload are described. Transport layer security including TLS handshake, alert, and cipher protocols is also summarized. The roles and types of firewalls in providing access control between networks are defined.