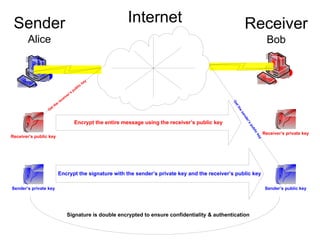
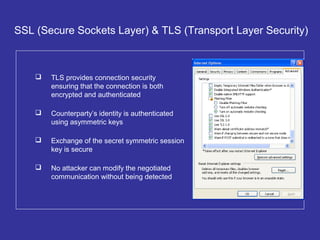
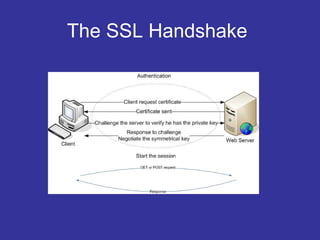
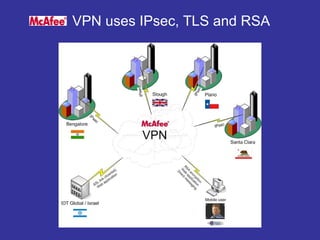
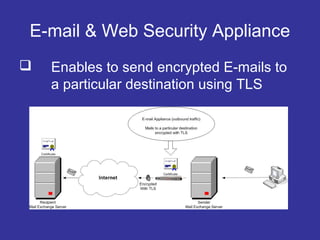
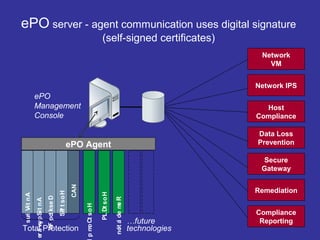
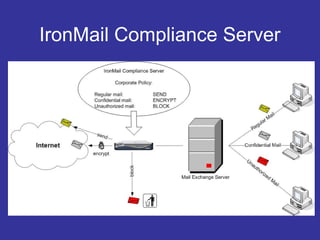
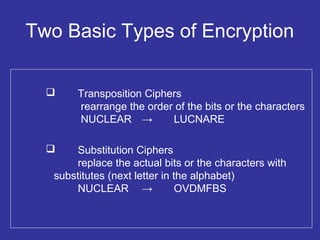
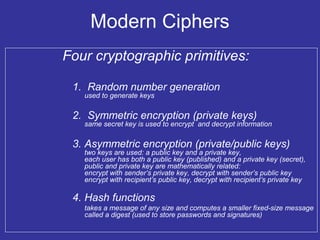
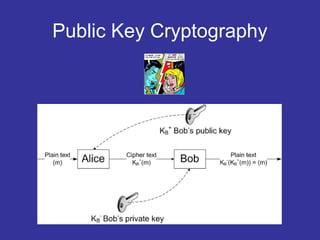
Encryption transforms plain text into cipher text using encryption algorithms and keys to provide confidentiality, integrity, and authenticity of messages. Modern encryption uses both symmetric encryption with private keys and asymmetric encryption with public/private key pairs. Transport Layer Security (TLS) and Secure Sockets Layer (SSL) provide encrypted communication over the internet using technologies like digital certificates, the Diffie-Hellman key exchange, and algorithms like RSA and AES.










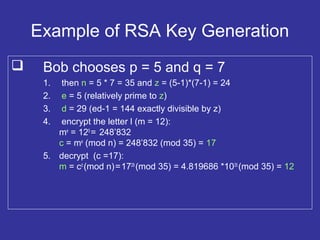
![RSA Algorithm For Key Generation
Based on large prime numbers:
1. Choose two large prime numbers p, q
2. Compute n = pq and z = (p - 1)(q - 1)
3. Choose e (e < n) that has no common factors with z
(e and z are relatively prime)
4. Choose d such that ed – 1 is exactly divisible by z
i.e. ed (mod z) = 1
5. Public key KB
+
is (n,e) ; private key KB
-
is (n,d)
6. Encrypt m with c = me
(mod n)
7. Decrypt c as m = cd
(mod n)
This works because:
m = [me
(mod n)]d
(mod n)](https://image.slidesharecdn.com/5a7709f7-b7db-4267-896b-778bd224b15b-160411080113/85/What-is-Encryption-18-320.jpg)