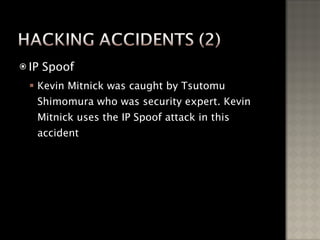
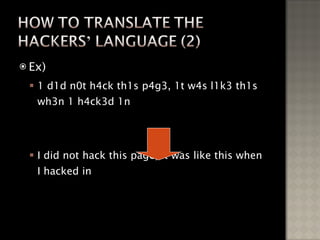
The document discusses the history and types of hacking, including famous hacking incidents. It provides information on how hackers operate after gaining access to systems, including installing backdoors and hiding their activities. The document also discusses how to protect against hackers by patching security holes, encrypting data, and monitoring networks with firewalls and intrusion detection systems.
![Taeho Oh http://postech.edu/~ohhara [email_address]](https://image.slidesharecdn.com/seminar-1-090519000947-phpapp01/85/Hacker-1-320.jpg)