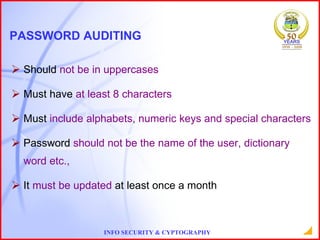
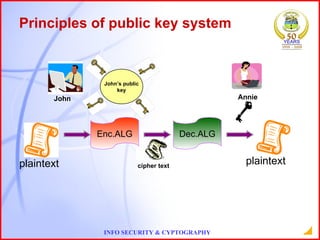
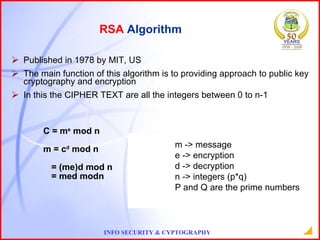
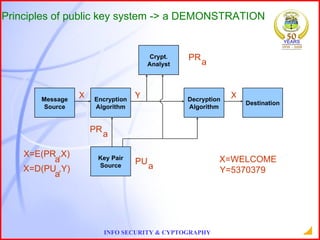
This document provides an overview of information security and cryptography. It discusses objectives of security like avoiding data threats. It also covers topics like password auditing, data security, authentication, encryption, decryption, public and private key cryptography, digital signatures, and the RSA algorithm. It demonstrates an example of encrypting a message using RSA and decrypting the cipher text. The conclusion emphasizes the importance of information security.