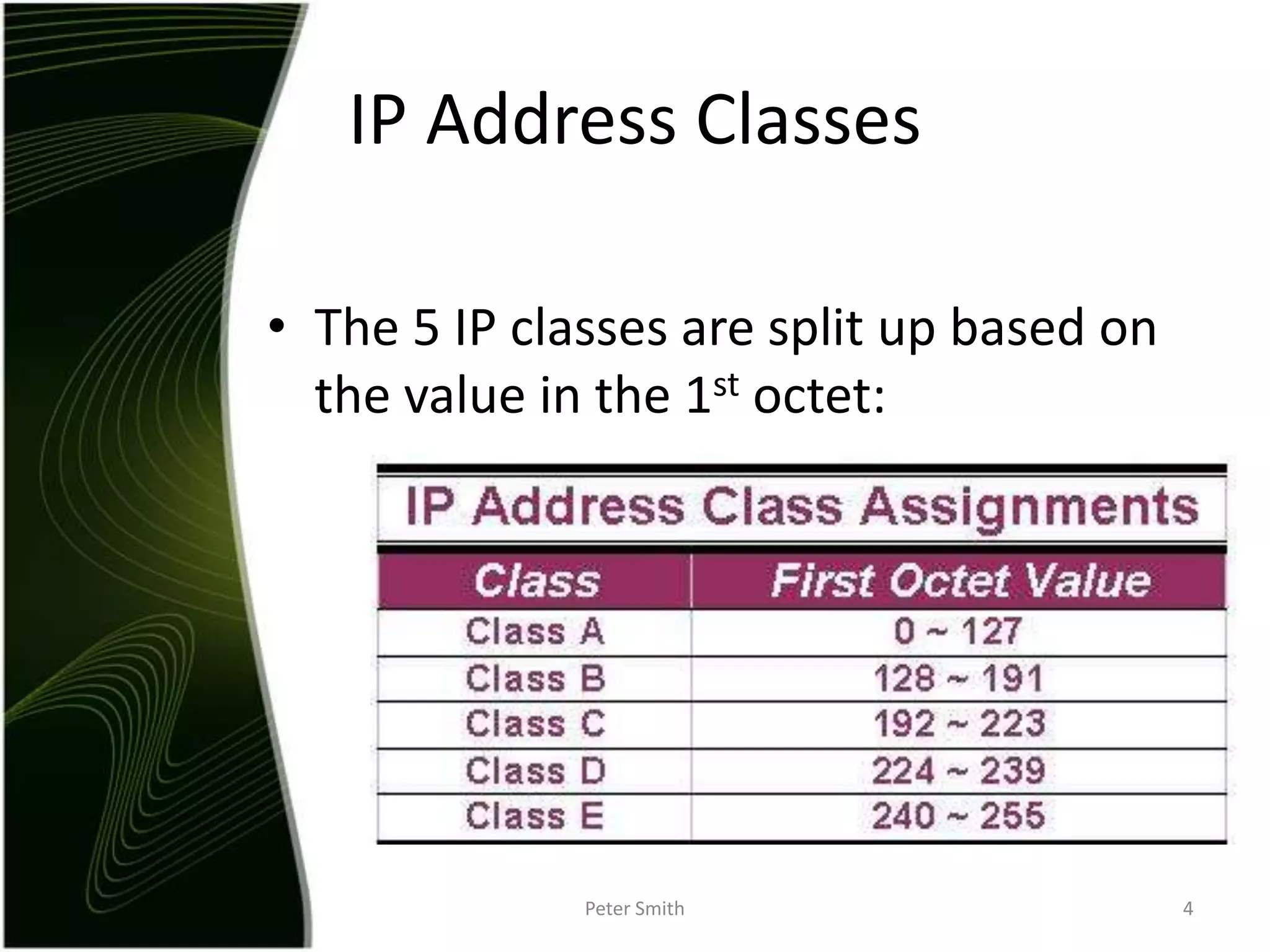
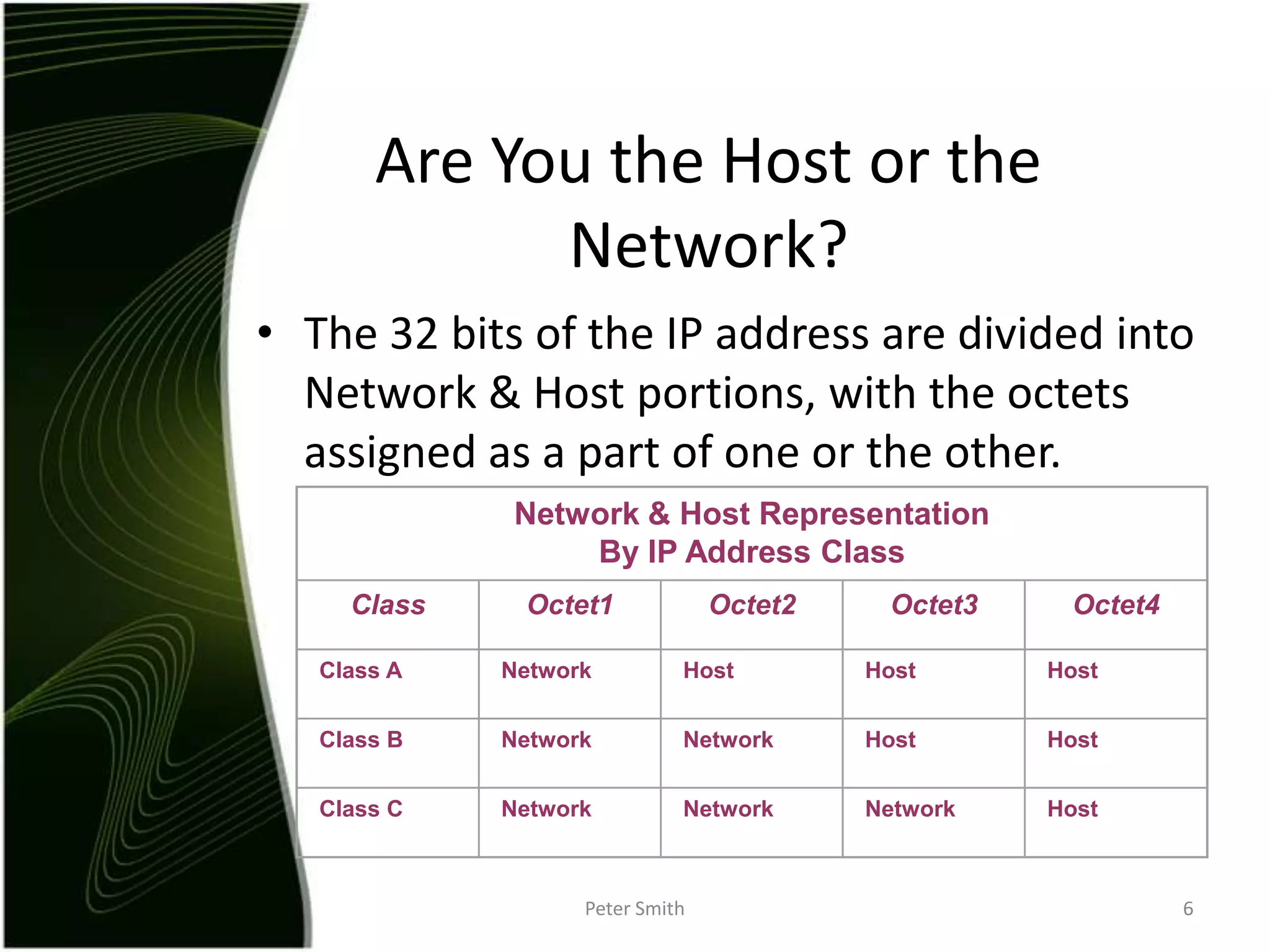
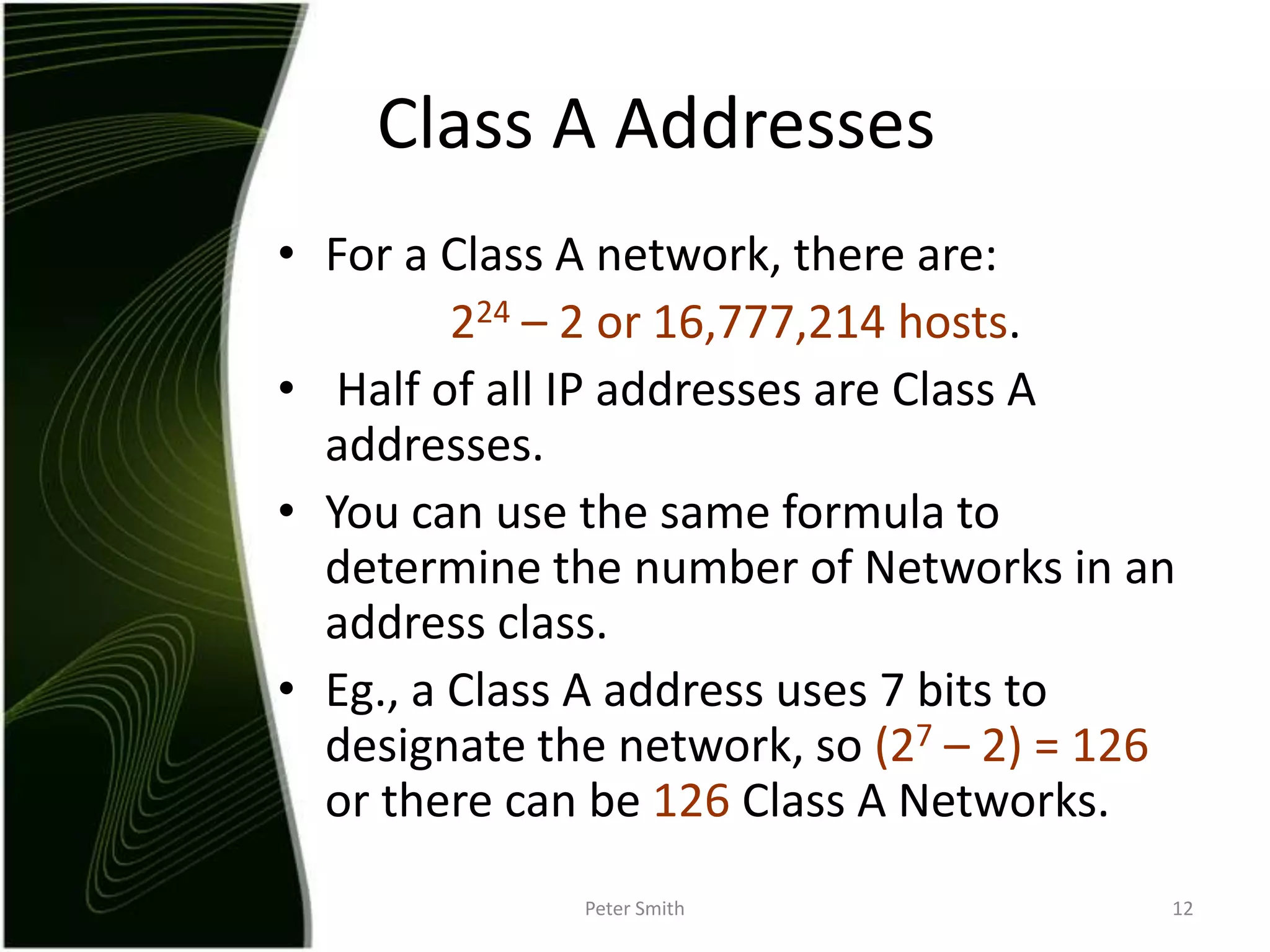
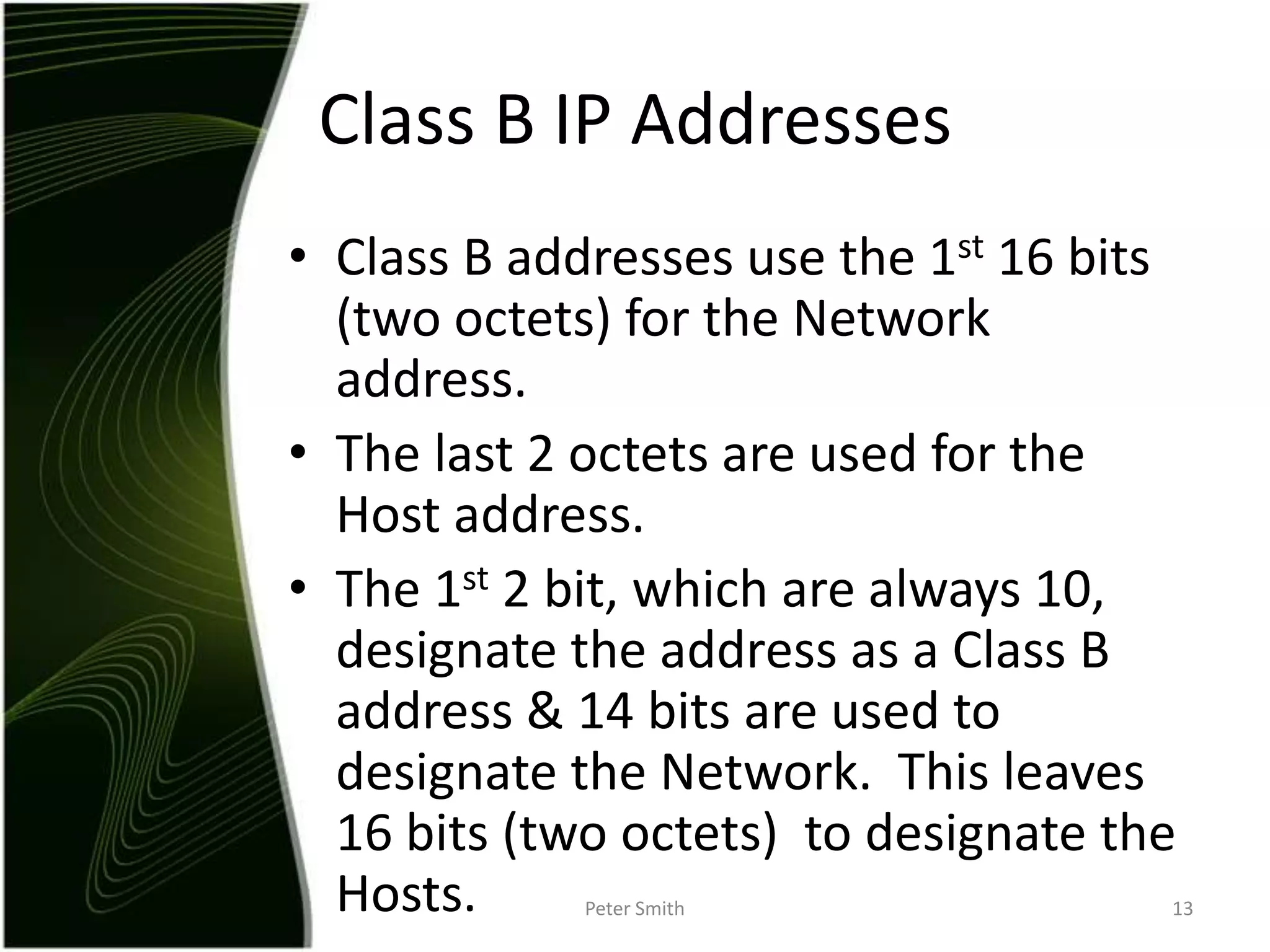
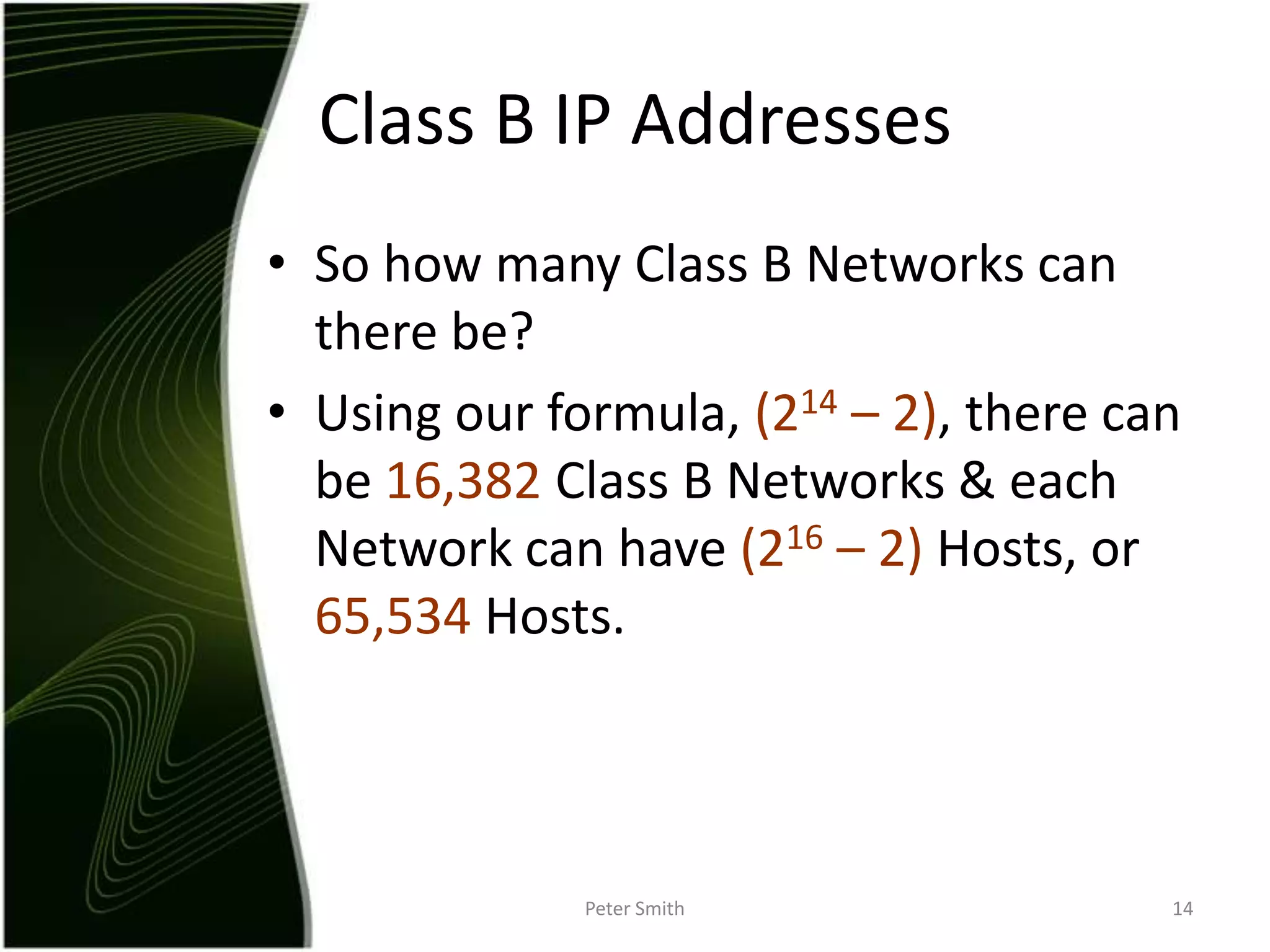
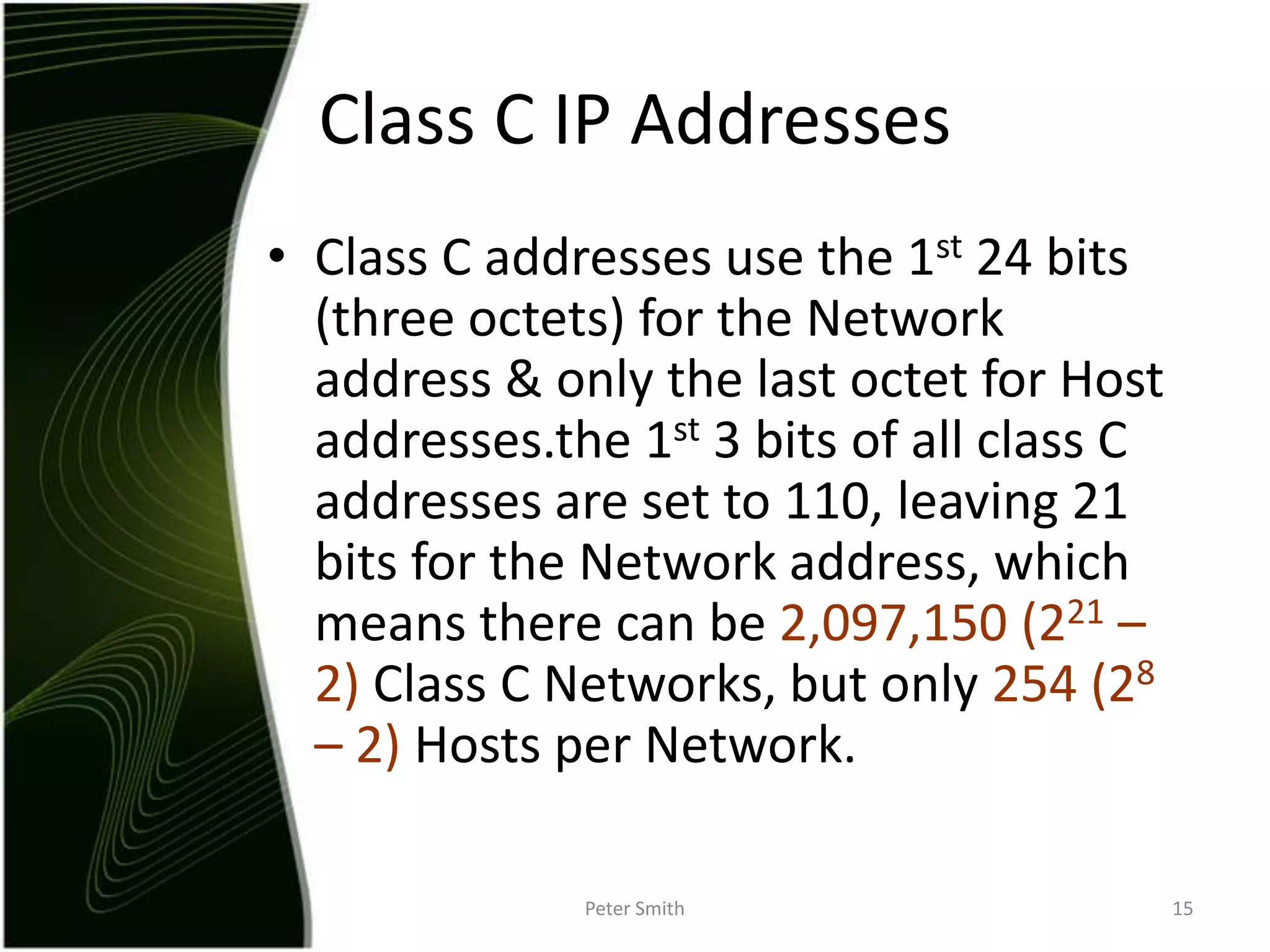
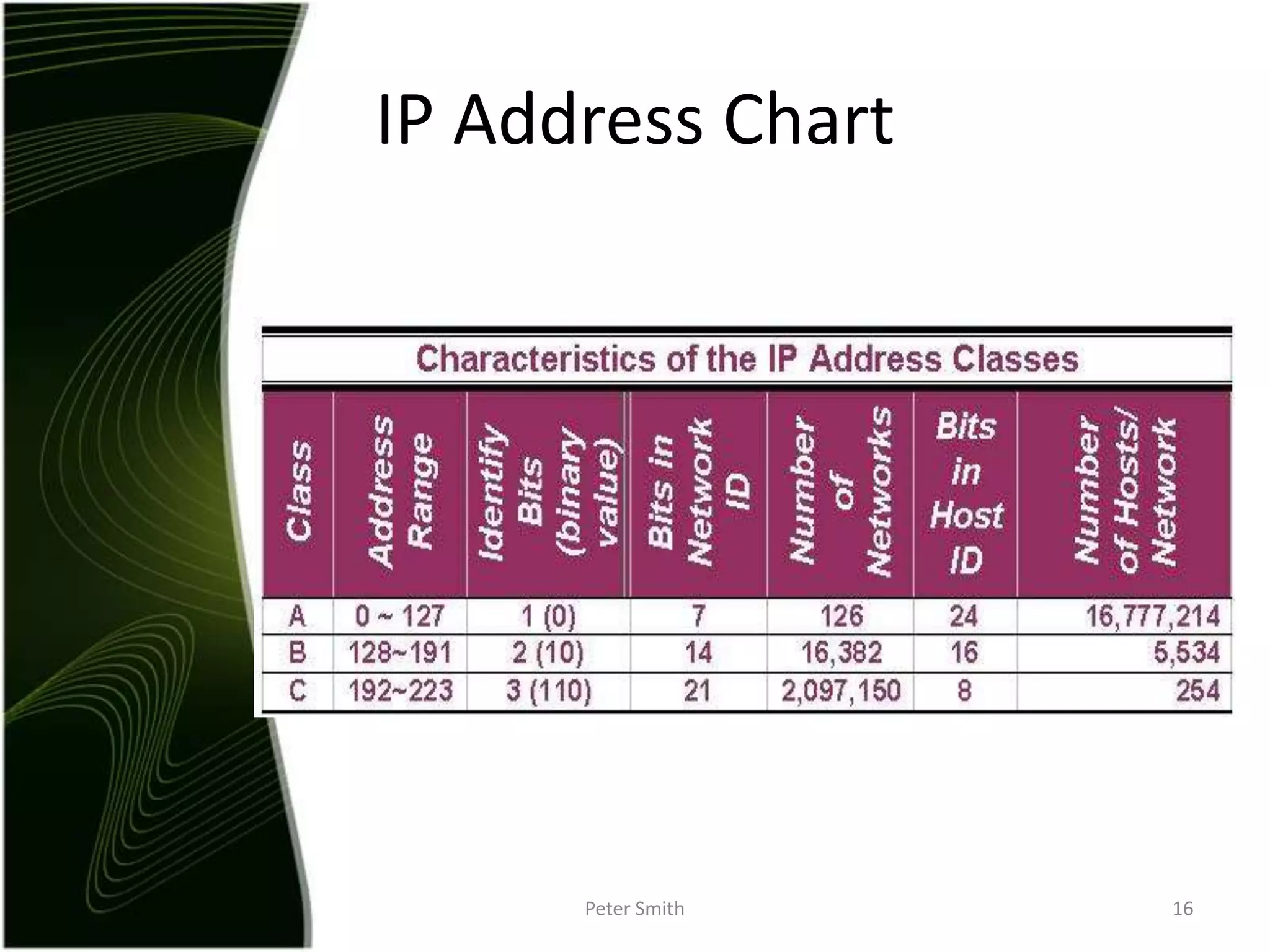
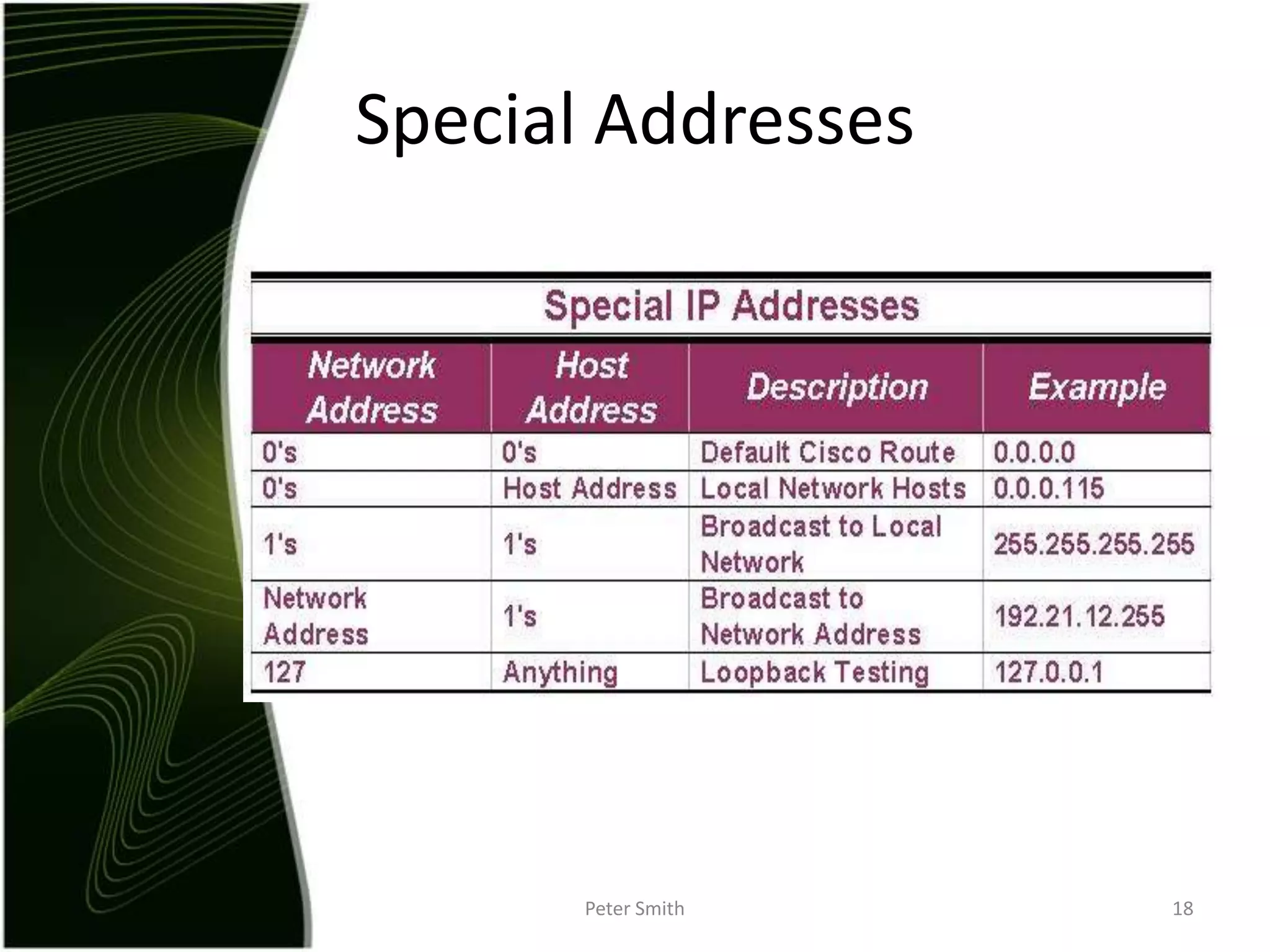
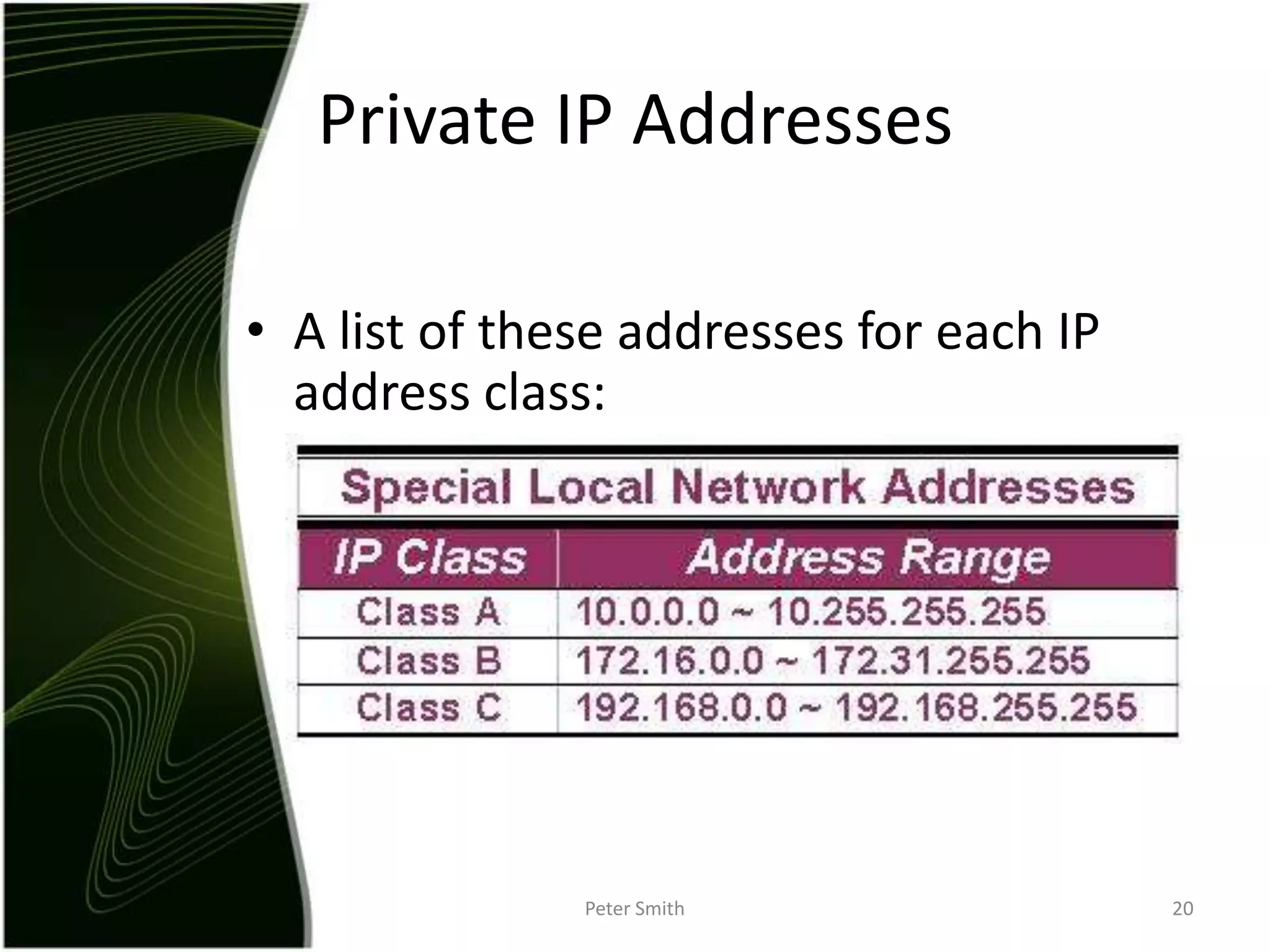
The document discusses IP addressing and the classification of IP addresses. It explains that IP addresses are made up of 4 octets and broken into classes A through E. It provides details on each class, including how many bits are used for the network and host portions and the number of available networks and hosts. Special addresses like private IP addresses that start with 10, 172.16, or 192.168 are also discussed.