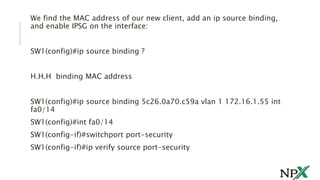
IP Source Guard (IPSG) helps prevent IP spoofing attacks by dropping any traffic that does not match the bindings in the DHCP Snooping database or configured static IP bindings. IPSG creates ACLs dynamically on each port to block unauthorized traffic. It must be enabled on all access ports along with DHCP Snooping to be effective. Static IP/MAC bindings can also be configured for devices not using DHCP.