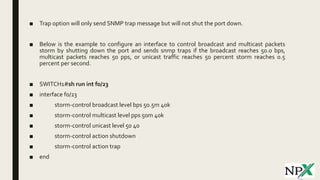
Storm control blocks interfaces from receiving excessive broadcast, multicast, or unicast traffic over a threshold within a time period. When traffic exceeds the rising threshold, the interface is blocked until traffic drops below the falling threshold. Storm control can shut down interfaces or send SNMP traps. It was tested between two switches, with one interface shutting down when unicast traffic exceeded 100 packets per second due to storm control being triggered.